On Invariant Synthesis for Parametric Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 Jcorley[At]Westga.Edu](https://docslib.b-cdn.net/cover/5279/jonathan-corley-university-of-west-georgia-1601-maple-street-carrollton-ga-30118-jcorley-at-westga-edu-915279.webp)
Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 Jcorley[At]Westga.Edu
Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 jcorley[at]westga.edu Research Interests CS Education and Outreach, Software Engineering Education Ph.D. in Computer Science, August 2016 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. Jeff Gray Committee: Dr. Jeffrey Carver, Dr. Randy Smith, Dr. Susan Vrbsky, Dr. Eugene Syriani M.S. in Computer Science, May 2012 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. Nicholas Kraft B.S. in Computer Science, May 2009 University of Alabama, Tuscaloosa, AL, USA Honors & Awards Outstanding Graduate Researcher, University of Alabama Department of CS, 2016 President of the University of Alabama chapter of Upsilon Pi Epsilon (UPE), 2015 and 2014 UPE is an international honor society for the computing and information disciplines. 1st place, MODELS ACM Student Research Competition Graduate, 2014. Valencia, Spain University of Alabama College of Engineering Outstanding Service by a Graduate Student, 2014 Outstanding ACM Graduate Award, University of Alabama Department of CS, 2013 Vice-President of the University of Alabama chapter of Upsilon Pi Epsilon, 2013 Inducted into the University of Alabama chapter of Upsilon Pi Epsilon, 2011 Publications Refereed Journal and Book Chapter Jonathan Corley, Brian Eddy, Eugene Syriani, and Jeff Gray “Efficient and Scalable Omniscient Debugging for Model Transformations” In Ghosh, S., Li, J. (Eds.) Software Quality Journal Special Issue on Program Debugging: Research, Practice and Challenges. No. 1, January 2017, pp. 7-48 Jonathan Corley, Eugene Syriani, Huseyin Ergin, and Simon Van Mierlo “Cloud-based Multi- View Modeling Environments” In Cruz, A.M., Paiva, S. (Eds.) Modern Software Engineering Methodologies for Mobile and Cloud Environments, IGI Global. -

Jonathan Corley Research Interests Education Honors & Awards Refereed Journal and Book Chapter
Jonathan Corley University of Alabama 342 H.M. Comer Hall corle001[at]crimson.ua.edu Tuscaloosa, AL 35487-0290 http://corle001.students.cs.ua.edu Research Interests Software Engineering, Model-Driven Engineering, CS Education and Outreach Education Ph.D. in Computer Science, expected August 2016 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. J. Gray M.S. in Computer Science, May 2012 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. N. Kraft B.S. in Computer Science, May 2009 University of Alabama, Tuscaloosa, AL, USA Honors & Awards Outstanding Graduate Researcher, University of Alabama Department of CS, 2016 1st place, MODELS ACM Student Research Competition Graduate, 2014. Valencia, Spain University of Alabama College of Engineering Outstanding Service by a Graduate Student, 2014 Outstanding ACM Graduate Award, University of Alabama Department of CS, 2013 2nd place, ACM midSE, Graduate: PhD presentation, 2013. Gatlinburg, TN, USA President of the University of Alabama chapter of Upsilon Pi Epsilon (UPE), 2015 and 2014 UPE is an international honor society for the computing and information disciplines. Vice-President of the University of Alabama chapter of Upsilon Pi Epsilon, 2013 Inducted into the University of Alabama chapter of Upsilon Pi Epsilon, 2011 Refereed Journal and Book Chapter Jonathan Corley, Brian Eddy, Eugene Syriani, and Jeff Gray (2016) “Efficient and Scalable Omniscient Debugging for Model Transformations” In Ghosh, S., Li, J. (Eds.) Software Quality Special Issue on Program Debugging: Research, Practice and Challenges. Jonathan Corley, Eugene Syriani, Huseyin Ergin, and Simon Van Mierlo (2016) “Cloud-based Multi-View Modeling Environments” In Cruz, A.M., Paiva, S. (Eds.) Modern Software Engineering Methodologies for Mobile and Cloud Environments, IGI Global. -
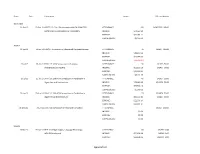
Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 Sigada 100.00 SIGAPP 0.00 SIGPLAN 0.00
Starts Ends Conference Actual SIGs and their % SIGACCESS 21-Oct-13 23-Oct-13 ASSETS '13: The 15th International ACM SIGACCESS ATTENDANCE: 155 SIGACCESS 100.00 Conference on Computers and Accessibility INCOME: $74,697.30 EXPENSE: $64,981.11 SURPLUS/LOSS: $9,716.19 SIGACT 12-Jan-14 14-Jan-14 ITCS'14 : Innovations in Theoretical Computer Science ATTENDANCE: 76 SIGACT 100.00 INCOME: $19,210.00 EXPENSE: $21,744.07 SURPLUS/LOSS: ($2,534.07) 22-Jul-13 24-Jul-13 PODC '13: ACM Symposium on Principles ATTENDANCE: 98 SIGOPS 50.00 of Distributed Computing INCOME: $62,310.50 SIGACT 50.00 EXPENSE: $56,139.24 SURPLUS/LOSS: $6,171.26 23-Jul-13 25-Jul-13 SPAA '13: 25th ACM Symposium on Parallelism in ATTENDANCE: 45 SIGACT 50.00 Algorithms and Architectures INCOME: $45,665.50 SIGARCH 50.00 EXPENSE: $39,586.18 SURPLUS/LOSS: $6,079.32 23-Jun-14 25-Jun-14 SPAA '14: 26th ACM Symposium on Parallelism in ATTENDANCE: 73 SIGARCH 50.00 Algorithms and Architectures INCOME: $36,107.35 SIGACT 50.00 EXPENSE: $22,536.04 SURPLUS/LOSS: $13,571.31 31-May-14 3-Jun-14 STOC '14: Symposium on Theory of Computing ATTENDANCE: SIGACT 100.00 INCOME: $0.00 EXPENSE: $0.00 SURPLUS/LOSS: $0.00 SIGAda 10-Nov-13 14-Nov-13 HILT 2013:High Integrity Language Technology ATTENDANCE: 60 SIGBED 0.00 ACM SIGAda Annual INCOME: $32,696.00 SIGCAS 0.00 EXPENSE: $32,404.66 SIGSOFT 0.00 Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 SIGAda 100.00 SIGAPP 0.00 SIGPLAN 0.00 SIGAI 11-Nov-13 15-Nov-13 ASE '13: ACM/IEEE International Conference on ATTENDANCE: 195 SIGAI 25.00 Automated Software Engineering -

PARSEC3.0: a Multicore Benchmark Suite with Network Stacks and SPLASH-2X
PARSEC3.0: A Multicore Benchmark Suite with Network Stacks and SPLASH-2X Xusheng Zhan1,2, Yungang Bao1, Christian Bienia3, and Kai Li3 1State Key Laboratory of Computer Architecture, ICT, CAS 2University of Chinese Academy of Sciences 3Department of Computer Science, Princeton University Abstract Benchmarks play a very important role in accelerating the development and research of CMP. As one of them, the PARSEC suite continues to be updated and revised over and over again so that it can offer better support for researchers. The former versions of PARSEC have enough workloads to evaluate the property of CMP about CPU, cache and memory, but it lacks of applications based on network stack to assess the performance of CMPs in respect of network. In this work, we introduce PARSEC3.0, a new version of PARSEC suite that implements a user-level network stack and generates three network workloads with this stack to cover network domain. We explore the input sets of splash-2 and expand them to multiple scales, a.k.a, splash-2x. We integrate splash-2 and splash-2x into PARSEC framework so that researchers use these benchmark suite conveniently. Finally, we evaluate the u-TCP/IP stack and new network workloads, and analyze the characterizes of splash-2 and splash-2x. 1. Introduction Benchmarking is a fundamental methodology for computer architecture research. Architects evaluate their new design using benchmark suites that usually consist of multiple programs selected out from a diversity of domains. The PARSEC benchmark suite, containing 13 applications from six emerging domains, has been widely used for evaluating chip multiprocessors (CMPs) systems since it is released in 2008. -

AGERE! at SPLASH 2015 Companion Proceedings
AGERE! at SPLASH 2015 5th International Workshop on Programming based on Actors, Agents, and Decentralized Control Workshop held at ACM SPLASH 2015 26 October 2015 Pittsburgh, PA, USA Companion Proceedings AGERE! is an ACM SIGPLAN workshop Introduction ago, agis, egi, actum, agere latin verb meaning to act, to lead, to do, common root for actors and agents The fundamental turn of software into concurrency and distribution is not only a matter of performance, but also of design and abstraction. It calls for programming paradigms that, compared to current mainstream ones, would allow us to think about, design, develop, execute, debug, and profile – more naturally – systems exhibiting dif- ferent degrees of concurrency, asynchrony, and physical distribution. To this purpose, the AGERE! workshop is aimed at focusing on programming systems, languages and applications based on actors, agents and other programming paradigms promoting a decentralized-control mindset in solving problems and developing software. The work- shop is designed to cover both the theory and the practice of design and programming, bringing together researchers working on the models, languages and technologies, and practitioners developing real-world systems and applications. This volume contains the work-in-progress and short papers accepted and presented at the 5th edition of the AGERE! workshop, not included in the formal proceedings available on the ACM Digital Library. Acknowledgment The organizing committee would like to thank all program committee members, au- thors and participants. Thank you to ACM and SPLASH organizers for their support. We look forward to a productive workshop. 3 Committee Program Committee Gul Agha, University of Illinois at Urbana-Champaign Sylvan Clebsch, Imperial College London Rem Collier, University College Dublin Travis Desell, University of North Dakota Amal El Fallah Seghrouchni, LIP6 Univ. -

The Foundation of Modern Life
click i MAGAZINE 2015, VOLUME II THE FOUNDATION ALSO IN THIS ISSUE: OF New Engineering-Based College of Medicine 16 MODERN Illinois Funded by Google on Two Initiatives 18 LIFE. CS Welcomes Three New Faculty 32 High School Students Plunge into CS 42 Department of Computer Science click! Magazine is produced twice yearly for the friends of got your CS swag? CS @ ILLINOIS to showcase the innovations of our faculty and students, the accomplishments of our alumni, and to inspire our partners and peers in the field of computer science. Department Head: Editorial Board: Rob A. Rutenbar Tom Moone Colin Robertson shop now! my.cs.illinois.edu/buy Associate Department Heads: Rob A. Rutenbar Vikram Adve Laura Schmitt Jeff Erickson Michelle Wellens Lenny Pitt Writers: CS Alumni Advisory Board: Liz Ahlberg Alex Bratton (BS CE ’93) Katie Carr Ira Cohen (BS CS ’81) Robin Kravets Vilas S. Dhar (BS CS ’04, BS LAS BioE ’04) Rick Kubetz William M. Dunn (BS CS ‘86, MS ‘87) Tom Moone Mary Jane Irwin (MS ’75, PhD ’77) Colin Robertson Jennifer A. Mozen (MS CS ’97) Jeff Roley Daniel L. Peterson (BS ’05) Laura Schmitt Peter Tannenwald (BS LAS Math & CS ’85) Michelle Wellens Jill Zmaczinsky (BS CS ’00) Design: Contact us: SURFACE 51 [email protected] 217-333-3426 Computing is not about computers any more. It is about living. Nicholas Negroponte You can read past issues of click! magazine, as well as our monthly e-newsletter at cs.illinois.edu/news 4 CS @ ILLINOIS Department of Computer Science College of Engineering, College of Liberal Arts & Sciences University -

View the Revised S2018 Advance Program
PLAN YOUR EXPERIENCE ADVANCE PROGRAM The 45th International Conference & Exhibition on Computer Graphics and Interactive Techniques TABLE OF CONTENTS SCHEDULE AT A GLANCE ................................................... 3 CURATED CONTENT REASONS TO ATTEND ......................................................... 6 SIGGRAPH 2018 offers several events and sessions that are individually chosen by program chairs to CONFERENCE OVERVIEW ...................................................7 address specific topics in computer graphics and interactive techniques. CONFERENCE SCHEDULE ................................................ 10 Curated content is not selected through the regular APPY HOUR ..........................................................................19 channels of a comprehensive jury. ART GALLERY ......................................................................20 ART PAPERS........................................................................23 INTEREST AREAS SIGGRAPH brings together a wide variety of BUSINESS SYMPOSIUM ...................................................25 professionals who approach computer graphics and COMPUTER ANIMATION FESTIVAL: interactive techniques from different perspectives. ELECTONIC THEATER ........................................................26 Our programs and events align with five broad interest areas (listed below). Use these interest areas to help COMPUTER ANIMATION FESTIVAL: VR THEATER ........ 27 guide you through the content at SIGGRAPH 2018. COURSES .............................................................................28 -

Margaret R. Martonosi
Margaret R. Martonosi Computer Science Bldg, Room 208 Email: [email protected] 35 Olden St. Phone: 609-258-1912 Princeton, NJ 08540 http://www.princeton.edu/~mrm Hugh Trumbull Adams ’35 Professor of Computer Science, Princeton University Assistant Director for Computer and Information Science and Engineering (CISE) at National Science Foundation. (IPA Rotator). Andrew Dickson White Visiting Professor-At-Large, Cornell University Associated faculty, Dept. of Electrical Engineering; Princeton Environmental Institute, Center for Information Technology Policy, Andlinger Center for Energy and the Environment. Research areas: Computer architectures and the hardware/software interface, particularly power-aware computing and mobile networks. HONORS IEEE Fellow. “For contributions to power-efficient computer architecture and systems design” ACM Fellow. “For contributions in power-aware computing” 2016-2022: Andrew Dickson White Visiting Professor-At-Large. Cornell University. Roughly twenty people worldwide are extended this title based on their professional stature and expertise, and are considered full members of the Cornell faculty during their six-year term appointment. 2019 SRC Aristotle Award, for graduate mentoring. 2018 IEEE Computer Society Technical Achievement Award. 2018 IEEE International Conference on High-Performance Computer Architecture Test-of-Time Paper award, honoring the long-term impact of our HPCA-5 (1999) paper entitled “Dynamically Exploiting Narrow Width Operands to Improve Processor Power and Performance” 2017 ACM SenSys Test-of-Time Paper award, honoring the long-term impact of our SenSys 2004 paper entitled “Hardware Design Experiences in ZebraNet”. 2017 ACM SIGMOBILE Test-of-Time Paper Award, honoring the long-term impact of our ASPLOS 2002 paper entitled “Energy-Efficient Computing for Wildlife Tracking: Design Tradeoffs and Early Experiences with ZebraNet”. -

Peter J. Haas
VITA: PETER J. HAAS 7139 Wooded Lake Drive IBM Almaden Research Center San Jose, CA 95120 650 Harry Road (408) 997-7860 San Jose, CA 95120-6099 (408) 927-1702 [email protected] Research Interests Techniques for modelling, simulation, design, and control of complex systems, especially discrete-event stochastic systems, with applications to healthcare, manufacturing, computer, telecommunication, work-flow, and transporta- tion systems. Application of techniques from applied probability and statistics to the design, performance analysis, and control of systems for information management, mining, integration, exploration, and learning. Education Ph.D. (Operations Research) 1986, Stanford University. M.S. (Statistics) 1984, Stanford University. M.S. (Environmental Engineering) 1979, Stanford University. S.B. Magna cum Laude (Engineering and Applied Physics) 1978, Harvard University. Professional Activities Program Chair, Winter Simulation Conference, 2019 ICDE PhD Colloquium Committee, 2015 INFORMS Simulation Society Distinguished Service Award Committee, 2014 Sponsored session organizer, INFORMS National Meeting, 2014 Chair, INFORMS Simulation Society Elections Committee, 2013–2014 President, INFORMS Simulation Society, 2010–2012 Co-Editor, ACM TOMACS, Special Issue in Honor of Donald Iglehart, 2015 Co-Editor, ACM TOMACS, Special Issue on Simulation of Complex Service Systems, 2012 Area Editor, ACM Transactions on Modeling and Computer Simulation (TOMACS), 2004–present Associate Editor, ACM Trans. Database Systems, 2015–present Associate Editor, Operations Research, 1995–present Associate Editor, VLDB Journal, 2007–2013 Invited-Session Organizer, Winter Simulation Conference, 2012; INFORMS National Meeting, 2014 Co-Chair, Third INFORMS Simulation Research Workshop, 2011 Vice President, INFORMS Simulation Society, 2008–2010 Co-Editor, VLDB Journal, Special Issue on Uncertain and Probabilistic Databases, 2008–2009 Member, INFORMS, 1984–present Member, ACM SIGMOD, 2000–present Program Committee, 4th Intl. -

Vita: Peter J
VITA: PETER J. HAAS College of Information and Computer Sciences University of Massachusetts Amherst 140 Governors Drive Amherst, MA 01003-9264 (413) 545-3140 [email protected] Research Interests Application of techniques from applied probability and statistics to the design, performance analysis, and control of systems for information management, mining, integration, exploration, decision support, and learning. Statistical and machine-learning techniques for modeling, simulation, design, and control of complex systems, especially discrete-event stochastic systems, with applications to healthcare, manufacturing, computer, telecommunication, work-flow, and transportation systems. Education Ph.D. (Operations Research) 1986, Stanford University. M.S. (Statistics) 1984, Stanford University. M.S. (Environmental Engineering) 1979, Stanford University. S.B. Magna cum Laude (Engineering and Applied Sciences) 1978, Harvard University. Experience College of Information and Computer Sciences and Deprtment of Mechanical and Industrial Engineering, University of Massachusetts Amherst. Professor, 2017–present Taught graduate course on computer simulation, undergraduate courses on discrete mathematics and probability. Pursuing research on stochastic optimization in database systems, automatic document summarization, genera- tive neural networks for creation and efficient deployment of simulation models, modeling of multiple chronic diseases for decision support, online maintenance of machine-learning models, time-biased sampling for online analytics and machine learning, and reducing training bias in machine learning models. IBM Almaden Research Center, San Jose, CA. Research Staff Member, 1987–2014; Principal Research Staff Mem- ber, 2014–2017. Analytics over massive data With the SystemML team, developed novel compressed linear algebra methods for scalable machine learning. With the Watson division, developed novel methods for principled computation of confidence values for machine-generated hypotheses. -

Engaging with Climate Change: Possible Steps for SIGPLAN
Engaging with Climate Change: Possible Steps for SIGPLAN Preliminary Report of the SIGPLAN Climate Committee Michael Hicks Crista Lopes Benjamin C. Pierce Version 1.2, June 2018 Executive Summary The developing threat of climate change demands an engaged response—not only from policymakers and regulatory agencies, but also from organizations that promote carbon-intensive activities, such as ACM’s Special Interest Group on Programming Languages (SIGPLAN). SIGPLAN’s emphasis on international conferences promotes air travel, a significant and growing contributor to global warming. In view of this — and the concern that many SIGPLAN members have expressed about climate change — SIGPLAN has a clear responsibility to understand and explore ways of reducing the costs of its conference-focused approach to promoting exchange of ideas. This conversation is also timely in view of other emerging concerns about travel, including restrictions on visa rules, infectious disease outbreaks, and questions about fair access for computer scientists from less wealthy regions. Section 1 lays out this argument in more detail. This report aims to begin a conversation among SIGPLAN members about how SIGPLAN might respond to the issue of climate change, focusing on ways to mitigate the climate impact of conferences. We do not advocate specific actions here, but rather aim to lay out as many options as possible, examining their pros and cons in terms of both carbon impact and possible effects on conference culture. The ultimate goal is to build consensus within the community around how best to balance environmental and other harms on one hand with the significant benefits of conferences on the other. -
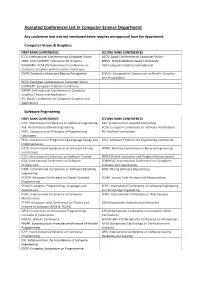
Accepted Conferences List in Computer Science Department
Accepted Conferences List in Computer Science Department Any conference that was not mentioned below requires pre-approval from the department. Computer Vision & Graphics FIRST RANK CONFERENCES SECOND RANK CONFERENCES ICCV: International Conference on Computer Vision ACCV: Asian Conference on Computer Vision I3DG: ACM SIGRAPH Interactive 3D Graphics BMVC: British Machine Vision Conference SIGGRAPH: ACM SIG International Conference on CGI: Computer Graphics International Computer Graphics and Interactive Techniques CVPR: Computer Vision and Pattern Recognition EGPGV: Eurographics Symposium on Parallel Graphics and Visualization ECCV: European Conference on Computer Vision EUROGAP: European Graphics Conference GRAPP: International Conference on Computer Graphics Theory and Application PG: Pacific Conference on Computer Graphics and Applications Software Engineering FIRST RANK CONFERENCES SECOND RANK CONFERENCES ICSE: International Conference on Software Engineering SAC: Symposium on Applied Computing ASE: Automated Software Engineering ECSA: European Conference on Software Architecture POPL: Symposium on Principles of Programming RV: Runtime Verification Languages PLDI: Conference on Programming Language Design and SPLC: Software Product Line Engineering Conference Implementation ISSTA: International Symposium on Software Testing WCRE: Working Conference on Reverse Engineering and Analysis ICST: International Conference on Software Testing PEPM (Partial Evaluation and Program Manipulation) ICSA: International Conference on Software COMPSAC: