PARSEC3.0: a Multicore Benchmark Suite with Network Stacks and SPLASH-2X
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On Invariant Synthesis for Parametric Systems
On Invariant Synthesis for Parametric Systems Dennis Peuter and Viorica Sofronie-Stokkermans Universit¨at Koblenz-Landau, Koblenz, Germany {dpeuter,sofronie}@uni-koblenz.de May 30, 2019 Abstract We study possibilities for automated invariant generation in parametric systems. We use (a refinement of) an algorithm for symbol elimination in theory extensions to devise a method for iteratively strengthening certain classes of safety properties to obtain invariants of the system. We identify conditions under which the method is correct and complete, and situations in which the method is guaranteed to terminate. We illustrate the ideas on various examples. 1 Introduction In the verification of parametric systems it is important to show that a certain property holds for all states reachable from the initial state. One way to solve such problems is to identify an inductive invariant which entails the property to be proved. Finding suitable inductive invariants is non-trivial – the problem is undecidable in general; solutions have been proposed for specific cases, as discussed in what follows. In [Kap06], Kapur proposes methods for invariant generation in theories such as Presburger arithmetic, real closed fields, and for polynomial equations and inequations with solutions in an algebraically closed field. The main idea is to use templates for the invariant (polynomials with undetermined coefficients), and solve constraints for all paths and initial values to determine the coefficients. A similar idea was used by Beyer et al. [BHMR07] for constraints in linear real or rational arithmetic; it is shown that if an invariant is expressible with a given template, then it will be computed. Symbol elimination has been used for interpolation and invariant generation in many papers. -

What I Wish I Knew When Learning Haskell
What I Wish I Knew When Learning Haskell Stephen Diehl 2 Version This is the fifth major draft of this document since 2009. All versions of this text are freely available onmywebsite: 1. HTML Version http://dev.stephendiehl.com/hask/index.html 2. PDF Version http://dev.stephendiehl.com/hask/tutorial.pdf 3. EPUB Version http://dev.stephendiehl.com/hask/tutorial.epub 4. Kindle Version http://dev.stephendiehl.com/hask/tutorial.mobi Pull requests are always accepted for fixes and additional content. The only way this document will stayupto date and accurate through the kindness of readers like you and community patches and pull requests on Github. https://github.com/sdiehl/wiwinwlh Publish Date: March 3, 2020 Git Commit: 77482103ff953a8f189a050c4271919846a56612 Author This text is authored by Stephen Diehl. 1. Web: www.stephendiehl.com 2. Twitter: https://twitter.com/smdiehl 3. Github: https://github.com/sdiehl Special thanks to Erik Aker for copyediting assistance. Copyright © 20092020 Stephen Diehl This code included in the text is dedicated to the public domain. You can copy, modify, distribute and perform thecode, even for commercial purposes, all without asking permission. You may distribute this text in its full form freely, but may not reauthor or sublicense this work. Any reproductions of major portions of the text must include attribution. The software is provided ”as is”, without warranty of any kind, express or implied, including But not limitedtothe warranties of merchantability, fitness for a particular purpose and noninfringement. In no event shall the authorsor copyright holders be liable for any claim, damages or other liability, whether in an action of contract, tort or otherwise, Arising from, out of or in connection with the software or the use or other dealings in the software. -

Commonspad Ocaml Library Programmer’S Manual
Commonspad OCaml Library Programmer’s manual Yoann Padioleau [email protected] December 29, 2009 Copyright c 2009 Yoann Padioleau. Permission is granted to copy, distribute and/or modify this doc- ument under the terms of the GNU Free Documentation License, Version 1.3. 1 Short Contents 1 Introduction 4 I Common 7 2 Overview 8 3 Basic 14 4 Basic types 31 5 Collection 46 6 Misc 61 II OCommon 66 7 Overview 67 8 Ocollection 68 9 Oset 71 10 Oassoc 73 11 Osequence 74 12 Oarray 75 13 Ograph 77 14 Odb 81 2 III Extra Common 82 15 Interface 84 16 Concurrency 89 17 Distribution 90 18 Graphic 91 19 OpenGL 92 20 GUI 93 21 ParserCombinators 94 22 Backtrace 100 23 Glimpse 101 24 Regexp 103 25 Sexp and binio 104 26 Python 105 Conclusion 106 A Indexes 107 B References 108 3 Contents 1 Introduction 4 1.1 Features . 4 1.2 Copyright . 5 1.3 Source organization . 6 1.4 API organization . 6 1.5 Acknowledgements . 6 I Common 7 2 Overview 8 3 Basic 14 3.1 Pervasive types and operators . 14 3.2 Debugging, logging . 15 3.3 Profiling . 17 3.4 Testing . 18 3.5 Persitence . 20 3.6 Counter . 21 3.7 Stringof . 21 3.8 Macro . 22 3.9 Composition and control . 22 3.10 Concurrency . 24 3.11 Error management . 24 3.12 Environment . 25 3.13 Arguments . 28 3.14 Equality . 29 4 Basic types 31 4.1 Bool . 31 4.2 Char . 31 4.3 Num . -
![Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 Jcorley[At]Westga.Edu](https://docslib.b-cdn.net/cover/5279/jonathan-corley-university-of-west-georgia-1601-maple-street-carrollton-ga-30118-jcorley-at-westga-edu-915279.webp)
Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 Jcorley[At]Westga.Edu
Jonathan Corley University of West Georgia 1601 Maple Street Carrollton, GA 30118 jcorley[at]westga.edu Research Interests CS Education and Outreach, Software Engineering Education Ph.D. in Computer Science, August 2016 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. Jeff Gray Committee: Dr. Jeffrey Carver, Dr. Randy Smith, Dr. Susan Vrbsky, Dr. Eugene Syriani M.S. in Computer Science, May 2012 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. Nicholas Kraft B.S. in Computer Science, May 2009 University of Alabama, Tuscaloosa, AL, USA Honors & Awards Outstanding Graduate Researcher, University of Alabama Department of CS, 2016 President of the University of Alabama chapter of Upsilon Pi Epsilon (UPE), 2015 and 2014 UPE is an international honor society for the computing and information disciplines. 1st place, MODELS ACM Student Research Competition Graduate, 2014. Valencia, Spain University of Alabama College of Engineering Outstanding Service by a Graduate Student, 2014 Outstanding ACM Graduate Award, University of Alabama Department of CS, 2013 Vice-President of the University of Alabama chapter of Upsilon Pi Epsilon, 2013 Inducted into the University of Alabama chapter of Upsilon Pi Epsilon, 2011 Publications Refereed Journal and Book Chapter Jonathan Corley, Brian Eddy, Eugene Syriani, and Jeff Gray “Efficient and Scalable Omniscient Debugging for Model Transformations” In Ghosh, S., Li, J. (Eds.) Software Quality Journal Special Issue on Program Debugging: Research, Practice and Challenges. No. 1, January 2017, pp. 7-48 Jonathan Corley, Eugene Syriani, Huseyin Ergin, and Simon Van Mierlo “Cloud-based Multi- View Modeling Environments” In Cruz, A.M., Paiva, S. (Eds.) Modern Software Engineering Methodologies for Mobile and Cloud Environments, IGI Global. -

The Glasgow Haskell Compiler User's Guide, Version 4.08
The Glasgow Haskell Compiler User's Guide, Version 4.08 The GHC Team The Glasgow Haskell Compiler User's Guide, Version 4.08 by The GHC Team Table of Contents The Glasgow Haskell Compiler License ........................................................................................... 9 1. Introduction to GHC ....................................................................................................................10 1.1. The (batch) compilation system components.....................................................................10 1.2. What really happens when I “compile” a Haskell program? .............................................11 1.3. Meta-information: Web sites, mailing lists, etc. ................................................................11 1.4. GHC version numbering policy .........................................................................................12 1.5. Release notes for version 4.08 (July 2000) ........................................................................13 1.5.1. User-visible compiler changes...............................................................................13 1.5.2. User-visible library changes ..................................................................................14 1.5.3. Internal changes.....................................................................................................14 2. Installing from binary distributions............................................................................................16 2.1. Installing on Unix-a-likes...................................................................................................16 -

Jonathan Corley Research Interests Education Honors & Awards Refereed Journal and Book Chapter
Jonathan Corley University of Alabama 342 H.M. Comer Hall corle001[at]crimson.ua.edu Tuscaloosa, AL 35487-0290 http://corle001.students.cs.ua.edu Research Interests Software Engineering, Model-Driven Engineering, CS Education and Outreach Education Ph.D. in Computer Science, expected August 2016 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. J. Gray M.S. in Computer Science, May 2012 University of Alabama, Tuscaloosa, AL, USA Advisor: Dr. N. Kraft B.S. in Computer Science, May 2009 University of Alabama, Tuscaloosa, AL, USA Honors & Awards Outstanding Graduate Researcher, University of Alabama Department of CS, 2016 1st place, MODELS ACM Student Research Competition Graduate, 2014. Valencia, Spain University of Alabama College of Engineering Outstanding Service by a Graduate Student, 2014 Outstanding ACM Graduate Award, University of Alabama Department of CS, 2013 2nd place, ACM midSE, Graduate: PhD presentation, 2013. Gatlinburg, TN, USA President of the University of Alabama chapter of Upsilon Pi Epsilon (UPE), 2015 and 2014 UPE is an international honor society for the computing and information disciplines. Vice-President of the University of Alabama chapter of Upsilon Pi Epsilon, 2013 Inducted into the University of Alabama chapter of Upsilon Pi Epsilon, 2011 Refereed Journal and Book Chapter Jonathan Corley, Brian Eddy, Eugene Syriani, and Jeff Gray (2016) “Efficient and Scalable Omniscient Debugging for Model Transformations” In Ghosh, S., Li, J. (Eds.) Software Quality Special Issue on Program Debugging: Research, Practice and Challenges. Jonathan Corley, Eugene Syriani, Huseyin Ergin, and Simon Van Mierlo (2016) “Cloud-based Multi-View Modeling Environments” In Cruz, A.M., Paiva, S. (Eds.) Modern Software Engineering Methodologies for Mobile and Cloud Environments, IGI Global. -

Haskell Quick Syntax Reference
Haskell Quick Syntax Reference A Pocket Guide to the Language, APIs, and Library — Stefania Loredana Nita Marius Mihailescu www.allitebooks.com Haskell Quick Syntax Reference A Pocket Guide to the Language, APIs, and Library Stefania Loredana Nita Marius Mihailescu www.allitebooks.com Haskell Quick Syntax Reference: A Pocket Guide to the Language, APIs, and Library Stefania Loredana Nita Marius Mihailescu Bucharest, Romania Bucharest, Romania ISBN-13 (pbk): 978-1-4842-4506-4 ISBN-13 (electronic): 978-1-4842-4507-1 https://doi.org/10.1007/978-1-4842-4507-1 Copyright © 2019 by Stefania Loredana Nita and Marius Mihailescu This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Trademarked names, logos, and images may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, logo, or image we use the names, logos, and images only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. The use in this publication of trade names, trademarks, service marks, and similar terms, even if they are not identified as such, is not to be taken as an expression of opinion as to whether or not they are subject to proprietary rights. -

Pcl: a Robust Monadic Parser Combinator Library for Ocaml
Motivation Basic Monadic Parser Combinators Writing pcl pcl: A Robust Monadic Parser Combinator Library for OCaml Chris Casinghino [email protected] OCaml Summer Project Meeting Chris Casinghino pcl: A Robust Monadic Parser Combinator Library for OCaml Motivation Basic Monadic Parser Combinators Writing pcl Outline 1 Motivation 2 Basic Monadic Parser Combinators What Is A Parser? Building Bigger Parsers 3 Writing pcl Chris Casinghino pcl: A Robust Monadic Parser Combinator Library for OCaml Motivation Basic Monadic Parser Combinators Writing pcl Outline 1 Motivation 2 Basic Monadic Parser Combinators What Is A Parser? Building Bigger Parsers 3 Writing pcl Chris Casinghino pcl: A Robust Monadic Parser Combinator Library for OCaml Motivation Basic Monadic Parser Combinators Writing pcl Benefits of Parser Combinators Parsers are specified directly in target language. No need to learn seperate grammar specification language. Parser may be modified on the fly, no seperate building process. Parsers are typechecked. Easy to extend set of available combinators. Lexer and parser may be written with the same tool. Chris Casinghino pcl: A Robust Monadic Parser Combinator Library for OCaml Motivation Basic Monadic Parser Combinators Writing pcl Parsec: Parser Combinators for Haskell Parsec is a popular monadic parser combinator library for Haskell. Parsec has been around for years, and is widely used. Large combinator library, including parsers for lexing, expressions, etc. Expressive error reporting, efficient. pcl is, in large part, a port of Parsec -

The Λ Abroad a Functional Approach to Software Components
The ¸ Abroad A Functional Approach To Software Components Een functionele benadering van software componenten (met een samenvatting in het Nederlands) Proefschrift ter verkrijging van de graad van doctor aan de Universiteit Utrecht op gezag van de Rector Magni¯cus, Prof. dr W.H. Gispen, ingevolge het besluit van het College voor Promoties in het openbaar te verdedigen op dinsdag 4 november 2003 des middags te 12.45 uur door Daniel Johannes Pieter Leijen geboren op 7 Juli 1973, te Alkmaar promotor: Prof. dr S.D. Swierstra, Universiteit Utrecht. co-promotor: dr H.J.M. Meijer, Microsoft Research. The work in this thesis has been carried out under the auspices of the research school IPA (Institute for Programming research and Algorithmics), and has been ¯nanced by Ordina. Printed by Febodruk 2003. Cover illustration shows the heavily cratered surface of the planet Mercury, photographed by the mariner 10. ISBN 90-9017528-8 Contents Dankwoord ix 1 Overview 1 2 H/Direct: a binary language interface for Haskell 5 2.1 Introduction ................................ 5 2.2 Background ................................ 6 2.2.1 Using the host or foreign language ............... 7 2.2.2 Using an IDL ........................... 8 2.2.3 Overview ............................. 9 2.3 The Foreign Function Interface ..................... 12 2.3.1 Foreign static import and export ................ 12 2.3.2 Variations on the theme ..................... 13 2.3.3 Stable pointers and foreign objects ............... 14 2.3.4 Dynamic import ......................... 15 2.3.5 Dynamic export ......................... 15 2.3.6 Implementing dynamic export .................. 18 2.3.7 Related work ........................... 19 iv Contents 2.4 Translating IDL to Haskell ...................... -
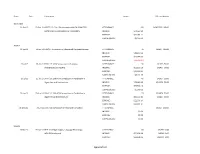
Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 Sigada 100.00 SIGAPP 0.00 SIGPLAN 0.00
Starts Ends Conference Actual SIGs and their % SIGACCESS 21-Oct-13 23-Oct-13 ASSETS '13: The 15th International ACM SIGACCESS ATTENDANCE: 155 SIGACCESS 100.00 Conference on Computers and Accessibility INCOME: $74,697.30 EXPENSE: $64,981.11 SURPLUS/LOSS: $9,716.19 SIGACT 12-Jan-14 14-Jan-14 ITCS'14 : Innovations in Theoretical Computer Science ATTENDANCE: 76 SIGACT 100.00 INCOME: $19,210.00 EXPENSE: $21,744.07 SURPLUS/LOSS: ($2,534.07) 22-Jul-13 24-Jul-13 PODC '13: ACM Symposium on Principles ATTENDANCE: 98 SIGOPS 50.00 of Distributed Computing INCOME: $62,310.50 SIGACT 50.00 EXPENSE: $56,139.24 SURPLUS/LOSS: $6,171.26 23-Jul-13 25-Jul-13 SPAA '13: 25th ACM Symposium on Parallelism in ATTENDANCE: 45 SIGACT 50.00 Algorithms and Architectures INCOME: $45,665.50 SIGARCH 50.00 EXPENSE: $39,586.18 SURPLUS/LOSS: $6,079.32 23-Jun-14 25-Jun-14 SPAA '14: 26th ACM Symposium on Parallelism in ATTENDANCE: 73 SIGARCH 50.00 Algorithms and Architectures INCOME: $36,107.35 SIGACT 50.00 EXPENSE: $22,536.04 SURPLUS/LOSS: $13,571.31 31-May-14 3-Jun-14 STOC '14: Symposium on Theory of Computing ATTENDANCE: SIGACT 100.00 INCOME: $0.00 EXPENSE: $0.00 SURPLUS/LOSS: $0.00 SIGAda 10-Nov-13 14-Nov-13 HILT 2013:High Integrity Language Technology ATTENDANCE: 60 SIGBED 0.00 ACM SIGAda Annual INCOME: $32,696.00 SIGCAS 0.00 EXPENSE: $32,404.66 SIGSOFT 0.00 Appendix C SURPLUS/LOSS: $291.34 SIGCSE 0.00 SIGAda 100.00 SIGAPP 0.00 SIGPLAN 0.00 SIGAI 11-Nov-13 15-Nov-13 ASE '13: ACM/IEEE International Conference on ATTENDANCE: 195 SIGAI 25.00 Automated Software Engineering -

AGERE! at SPLASH 2015 Companion Proceedings
AGERE! at SPLASH 2015 5th International Workshop on Programming based on Actors, Agents, and Decentralized Control Workshop held at ACM SPLASH 2015 26 October 2015 Pittsburgh, PA, USA Companion Proceedings AGERE! is an ACM SIGPLAN workshop Introduction ago, agis, egi, actum, agere latin verb meaning to act, to lead, to do, common root for actors and agents The fundamental turn of software into concurrency and distribution is not only a matter of performance, but also of design and abstraction. It calls for programming paradigms that, compared to current mainstream ones, would allow us to think about, design, develop, execute, debug, and profile – more naturally – systems exhibiting dif- ferent degrees of concurrency, asynchrony, and physical distribution. To this purpose, the AGERE! workshop is aimed at focusing on programming systems, languages and applications based on actors, agents and other programming paradigms promoting a decentralized-control mindset in solving problems and developing software. The work- shop is designed to cover both the theory and the practice of design and programming, bringing together researchers working on the models, languages and technologies, and practitioners developing real-world systems and applications. This volume contains the work-in-progress and short papers accepted and presented at the 5th edition of the AGERE! workshop, not included in the formal proceedings available on the ACM Digital Library. Acknowledgment The organizing committee would like to thank all program committee members, au- thors and participants. Thank you to ACM and SPLASH organizers for their support. We look forward to a productive workshop. 3 Committee Program Committee Gul Agha, University of Illinois at Urbana-Champaign Sylvan Clebsch, Imperial College London Rem Collier, University College Dublin Travis Desell, University of North Dakota Amal El Fallah Seghrouchni, LIP6 Univ. -

Languageext Documentation Release Latest
LanguageExt Documentation Release latest March 31, 2016 Contents 1 C# Functional Language Extensions3 1.1 Introduction...............................................3 1.1.1 Getting started.........................................4 1.1.2 Features.............................................5 1.2 Poor tuple support............................................5 1.3 Null reference problem..........................................6 1.4 Option..................................................6 1.4.1 Option monad - gasp! Not the M word!............................9 1.5 if( arg == null ) throw new ArgumentNullException(“arg”)....................... 10 1.6 Lack of lambda and expression inference................................ 12 1.7 Void isn’t a real type........................................... 12 1.8 Mutable lists and dictionaries...................................... 13 1.8.1 Lists............................................... 13 1.8.2 List pattern matching...................................... 14 1.8.3 Maps.............................................. 15 1.8.4 Map transformers........................................ 17 1.9 The awful out parameter........................................ 18 2 ‘Erlang like’ concurrency 21 2.1 Distributed................................................ 22 2.2 How?................................................... 22 2.3 Functions if you want them....................................... 23 2.4 Classes if you want them......................................... 25 2.5 Publish system.............................................