SQL Injection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Examples of the Electronic Health Record (EHR)
Examples of the Electronic Health Record (EHR) What is Biomedical & Health Informatics? William Hersh Copyright 2020 Oregon Health & Science University Examples of the EHR • Using the Veterans Health Information Systems and Technology Architecture (VistA) • Why VistA? – State-of-the-art EHR that has transformed healthcare in the Veteran’s Health Administration (VHA) (Perlin, 2006; Byrne, 2010) – Not that pretty, but has all of the modern features of the EHR, e.g., clinical decision support (CDS), computerized provider order entry (CPOE), etc. – Distributed under open-source model, unlike most other vendors who do not even allow screen shots to be shown outside their customers’ institutions • Fascinating story (Allen, 2017), but VistA now being phased out in favor of Cerner EHR adopted by Department of Defense (VA, 2017) – https://www.ehrm.va.gov/ WhatIs5 2 1 Some details about VistA • Server written in M (formerly called MUMPS), accessed via command-line interface – Runs in commercial Intersystems Cache (on many platforms) or open-source GT.M (Linux only) • Client (called CPRS) written in Delphi and providers graphical user interface – Only runs on Windows (just about all versions) WhatIs5 3 Logging on to CPRS, the front end to VistA WhatIs5 4 2 Choosing a patient WhatIs5 5 Cover sheet – overview WhatIs5 6 3 Drilling down to details of a problem WhatIs5 7 Details of an allergy WhatIs5 8 4 Viewing vital signs over time WhatIs5 9 More details on problems WhatIs5 10 5 List of active orders WhatIs5 11 Viewing the patient’s notes WhatIs5 12 -

A Cloud Based Patient-Centered Ehealth Record
International Journal on Advances in Life Sciences, vol 7 no 1 & 2, year 2015, http://www.iariajournals.org/life_sciences/ 30 A Cloud Based Patient-Centered eHealth Record Konstantinos Koumaditis, Leonidas Katelaris, and Marinos Themistocleous Department of Digital Systems University of Piraeus Piraeus, Greece e-mail: (konkoum,lkatelaris,mthemist)@unipi.gr Abstract - This research focuses on the Patient-Centered integrated view of citizens health status. The latter is reflected e-Health (PCEH) concept by introducing its importance in EHRs and Personal Health Records (PHRs), which are and demonstrating a multidisciplinary project that being enriched and exploited by different actors and combines advanced technologies. The project links stakeholders (i.e., health and care professionals, citizens, several aspects of PCEH functionality, such as: (a) nutrition experts, hospitals, etc.) in the health ecosystem. homecare telemedicine technologies, (b) e-prescribing, e- Three general PHR models have been proposed [7]: a) the referral, e-learning and (c) state-of-the-art technologies stand-alone model, b) Electronic Health Record (EHR) like cloud computing and Service Oriented Architecture system, and c) the integrated one, which is an interoperable (SOA), will lead to an innovative integrated e-health system providing linkage with a variety of patient platform that delivers many benefits to the society, the information sources, such as EHRs, home diagnostics, economy, the industry and the research community. This insurance claims etc. The main types of health information paper provides insights of the PCEH concept and the supported by PHRs are problem lists, procedures, major current stages of the project. In doing so, we aim to illnesses, provider lists, allergy data, home-monitored data, increase the awareness of this significant work and family history, social history and lifestyle, immunizations, disseminate the knowledge gained so far through our medications and laboratory tests [8, 9]. -
PDF File, 212 KB
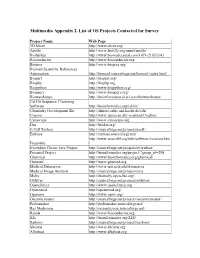
Multimedia Appendix 2. List of OS Projects Contacted for Survey Project Name Web Page 3D Slicer http://www.slicer.org/ Apollo http://www.fruitfly.org/annot/apollo/ Biobuilder http://www.biomedcentral.com/1471-2105/5/43 Bioconductor http://www.bioconductor.org Biojava http://www.biojava.org/ Biomail Scientific References Automation http://biomail.sourceforge.net/biomail/index.html Bioperl http://bioperl.org/ Biophp http://biophp.org Biopython http://www.biopython.org/ Bioquery http://www.bioquery.org/ Biowarehouse http://bioinformatics.ai.sri.com/biowarehouse/ Cd-Hit Sequence Clustering Software http://bioinformatics.org/cd-hit/ Chemistry Development Kit http://almost.cubic.uni-koeln.de/cdk/ Coasim http://www.daimi.au.dk/~mailund/CoaSim/ Cytoscape http://www.cytoscape.org Das http://biodas.org/ E-Cell System http://sourceforge.net/projects/ecell/ Emboss http://emboss.sourceforge.net/ http://www.ensembl.org/info/software/versions.htm Ensemble l Eviewbox Dicom Java Project http://sourceforge.net/projects/eviewbox/ Freemed Project http://bioinformatics.org/project/?group_id=298 Ghemical http://www.bioinformatics.org/ghemical/ Gnumed http://www.gnumed.org Medical Dataserver http://www.mii.ucla.edu/dataserver Medical Image Analysis http://sourceforge.net/projects/mia Moby http://biomoby.open-bio.org/ Olduvai http://sourceforge.net/projects/olduvai/ Openclinica http://www.openclinica.org Openemed http://openemed.org/ Openemr http://www.oemr.org/ Oscarmcmaster http://sourceforge.net/projects/oscarmcmaster/ Probemaker http://probemaker.sourceforge.net/ -

Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria
Original Article Healthc Inform Res. 2019 April;25(2):89-98. https://doi.org/10.4258/hir.2019.25.2.89 pISSN 2093-3681 • eISSN 2093-369X Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria Saptarshi Purkayastha1, Roshini Allam1, Pallavi Maity1, Judy W. Gichoya2 1Department of BioHealth Informatics, Indiana University–Purdue University Indianapolis, Indianapolis, IN, USA 2Dotter Institute, Oregon Health and Science University, Portland, OR, USA Objectives: Open-source Electronic Health Record (EHR) systems have gained importance. The main aim of our research is to guide organizational choice by comparing the features, functionality, and user-facing system performance of the five most popular open-source EHR systems. Methods: We performed qualitative content analysis with a directed approach on recently published literature (2012–2017) to develop an integrated set of criteria to compare the EHR systems. The functional criteria are an integration of the literature, meaningful use criteria, and the Institute of Medicine’s functional requirements of EHR, whereas the user-facing system performance is based on the time required to perform basic tasks within the EHR system. Results: Based on the Alexa web ranking and Google Trends, the five most popular EHR systems at the time of our study were OSHERA VistA, GNU Health, the Open Medical Record System (OpenMRS), Open Electronic Medical Record (OpenEMR), and OpenEHR. We also found the trends in popularity of the EHR systems and the locations where they were more popular than others. OpenEMR met all the 32 functional criteria, OSHERA VistA met 28, OpenMRS met 12 fully and 11 partially, OpenEHR-based EHR met 10 fully and 3 partially, and GNU Health met the least with only 10 criteria fully and 2 partially. -

Advances in Information Technology 0.Pdf
ADVANCES IN INFORMATION TECHNOLOGY AND COMMUNICATION IN HEALTH Studies in Health Technology and Informatics This book series was started in 1990 to promote research conducted under the auspices of the EC programmes’ Advanced Informatics in Medicine (AIM) and Biomedical and Health Research (BHR) bioengineering branch. A driving aspect of international health informatics is that telecommunication technology, rehabilitative technology, intelligent home technology and many other components are moving together and form one integrated world of information and communication media. The complete series has been accepted in Medline. Volumes from 2005 onwards are available online. Series Editors: Dr. O. Bodenreider, Dr. J.P. Christensen, Prof. G. de Moor, Prof. A. Famili, Dr. U. Fors, Prof. A. Hasman, Prof. E.J.S. Hovenga, Prof. L. Hunter, Dr. I. Iakovidis, Dr. Z. Kolitsi, Mr. O. Le Dour, Dr. A. Lymberis, Prof. J. Mantas, Prof. M.A. Musen, Prof. P.F. Niederer, Prof. A. Pedotti, Prof. O. Rienhoff, Prof. F.H. Roger France, Dr. N. Rossing, Prof. N. Saranummi, Dr. E.R. Siegel and Dr. P. Wilson Volume 143 Recently published in this series Vol. 142. J.D. Westwood, S.W. Westwood, R.S. Haluck, H.M. Hoffman, G.T. Mogel, R. Phillips, R.A. Robb and K.G. Vosburgh (Eds.), Medicine Meets Virtual Reality 17 – NextMed: Design for/the Well Being Vol. 141. E. De Clercq et al. (Eds.), Collaborative Patient Centred eHealth – Proceedings of the HIT@HealthCare 2008 joint event: 25th MIC Congress, 3rd International Congress Sixi, Special ISV-NVKVV Event, 8th Belgian eHealth Symposium Vol. 140. P.H. Dangerfield (Ed.), Research into Spinal Deformities 6 Vol. -

Open Source Et Gestion De L'information Médicale : Aperçu Des Projets Existants
Open source et gestion de l'information médicale : aperçu des projets existants Ateliers CISP Club 2011 – Alexandre BRULET Open Source : bref historique... 1969 : UNIX (Bell Labs°) 1975 : distribué à des universités pour « fins éducatives » avec les codes sources... 1977 : projet BSD 1984 : projet GNU (R. Stallman) (sources partagées) 1985 : Free Software Fondation (cadre légal – licence GPL) 1989 : licence BSD modifiée (open source) 1991 : noyau GNU/Linux ? OS dérivés (NetBSD, FreeBSD, SunOS ...) 1993 : Slackware 1993 : Debian 1994 : Red Hat > 50 OS dérivés > 100 OS dérivés 1998 : MPL (ex : SUSE) > 50 OS dérivés (Knopix, Ubuntu...) (Mandriva, Fedora ...) 1999 : licence Apache UNESCO 2004 : logiciels libres patrimoine de l'humanité (…) > 35 licences libres recensées sur wikipédia (PHP, Cecil, MIT, CPL, W3C, etc.) Open source : un fonctionnement communautaire ● La « pyramide » Linux : développeurs / 'maintainers' / chefs de projet sys USB net (...) L. Torvalds / A. Morton ● Système de «patchs» : publics, signés, discutés, soumis, (approuvés) ● Versions stables régulières et archivées (mirroirs) ● Système de «paquets» permettant la cohérence des OS ● Mode de fonctionnement repris par la plupart des distributions basées sur Linux ainsi que leurs « filles » : Debian → Ubuntu, Slackware → Zenwalk, RedHat → Fedora, etc. ● Idem pour les logiciels (xfce/gnome/kde, OOo, Gimp, Firefox, etc.) Le monde open source : un immense agrégat de communautés... OS OS OS Projets GNU OS OS OS Noyau OS OS OS Noyau OS OS Projets BSD Programme open source Programme propriétaire Système OS d'exploitation Quid des logiciels médicaux ? Petit tour du monde de l'open source médical à partir d'une liste proposée par Wikipédia. 1. Logiciels médicaux francophones : MedinTux ● Petite communauté depuis 2005 (marseille), licence CeCiLL ● DMI cabinet / hôpital - objectif = ergonomie ● Programmes serveurs et clients, consultation web possible. -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Adopting an Open Source Hospital Information System to Manage Healthcare Institutions
LIFE: International Journal of Health and Life-Sciences ISSN 2454-5872 Bouidi et al., 2017 Volume 3 Issue 3, pp. 38-57 Date of Publication: 18th December 2017 DOI-https://dx.doi.org/10.20319/lijhls.2017.33.3857 This paper can be cited as: Bouidi, Y, Azzouzi Idrissi, M & Rais, N. (2017). Adopting an Open Source Hospital Information System to Manage Healthcare Institutions. LIFE: International Journal of Health and Life-Sciences, 3(3), 38-57. This work is licensed under the Creative Commons Attribution-Non Commercial 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc/4.0/ or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042, USA. ADOPTING AN OPEN SOURCE HOSPITAL INFORMATION SYSTEM TO MANAGE HEALTHCARE INSTITUTIONS Youssef Bouidi Laboratory of Informatics, Modeling and Systems (LIMS), University of Sidi Mohamed Ben Abdallah (USMBA), Fez, Morocco [email protected] Mostafa Azzouzi Idrissi Laboratory of Informatics, Modeling and Systems (LIMS), University of Sidi Mohamed Ben Abdallah (USMBA), Fez, Morocco [email protected] Noureddine Rais Laboratory of Informatics, Modeling and Systems (LIMS), University of Sidi Mohamed Ben Abdallah (USMBA), Fez, Morocco [email protected] Abstract Our paper is a comparative study of different Open Source Hospital Information Systems (OSHISs). We chose open source because of problems in healthcare management like budget, resources and computerization. A literature review did not allow us to find a similar comparison, which explains the great interest of our study. Firstly, we retrieved nine OSHISs: MediBoard, OpenEMR, OpenMRS, OpenHospital, HospitalOS, PatientOS, Care2x, MedinTux and HOSxP. -

How to Deploy Infrastructure for E-Health Cloud Applications Master's
MASARYK UNIVERSITY FACULTY OF INFORMATICS E-health cloud specificities: How to deploy infrastructure for e-health cloud applications Master’s Thesis Sokolova Evgeniya Brno, 2017 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Evgeniya Sokolova, December 30, 2016 i Abstract The thesis focuses on eHealth cloud specificities and infrastructure deployment for eHealth cloud applications. The Theoretical background chapter contains fundamental information about cloud computing technologies and eHealth. This chapter also describes differences and similarities between regular and eHealth cloud. The Analysis chapter is focused on the selection of Cloud Management Software and medical application for eHealth cloud, based on comparison analysis. The Implementation part describes the design of eHealth cloud infrastructure to run eHealth cloud application and its implementation process, which also includes system testing and the following discussion regarding implementation results. Keywords Cloud computing, eHealth, eHealth cloud, Cloud Management Software, OpenStack, Electronic Health Records. ii Acknowledgement I would like to express my gratitude to my supervisor Mgr. Kamil Malinka, Ph.D for all his useful comments, remarks and inspiration during my work on this thesis. Furthermore, I would like to thank Mgr. Tomáš Sapák for all his help and consultations. I thank to my family for providing me with unfailing support through the process of writing this thesis. iii TABLE OF CONTENT 1 INTRODUCTION ....................................................................................... 1 1.1 Structure of the thesis ................................................................................... 3 2 THEORETICAL BACKGROUND .......................................................... -

Developing an Emr Training Unit for Nursing and Medical Students
TALLINN UNIVERSITY OF TECHNOLOGY Faculty of Information Technology Department of Health Technologies Lingling Yin 156371YVEM DEVELOPING AN EMR TRAINING UNIT FOR NURSING AND MEDICAL STUDENTS Master’s thesis Supervisor: Peeter Ross, MD, PhD Chair of Healthcare Technology Co-supervisor: Alexander Bejan, M.Sc. Furtwangen University, Germany Academic staff Tallinn 2018 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Tervisetehnoloogiate instituut Lingling Yin 156371YVEM ÕENDUS- JA ARSTITEADUSÕPILASTE EMR SÜSTEEMI TREENINGÜKSUSE VÄLJATÖÖTAMINE Magistritöö Juhendaja: Peeter Ross, MD, PhD Tervishoiutehnoloogia juhataja Kaasjuhendaja: Alexander Bejan, M.Sc. Furtwangeni Ülikool, Saksamaa Akadeemiline personal Tallinn 2018 Author’s declaration of originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Lingling Yin 09.01.2018 3 Abstract The aim of this master thesis is to investigate the feasibility of using Open Source EMR systems in order to teach nursing and medical students EMRS practical skills that are needed in their future job. The thesis consists of two main parts; selecting a suitable Open Source EMRS and developing an instructional unit for training students in order to use the EMRS. The Analytic Hierarchy Process (AHP) was used to select a suitable Open Source EMRS. The training unit uses eLearning, problem-based learning, and case study to optimize the teaching methods. The potential learning objectives are defined by using the Revised Bloom’s Taxonomy method. In the later parts, grading rubrics are created for the evaluation of the students’ learning outcomes, while the quantitative and qualitative data analysis methods are applied to the evaluation of the two questionnaires. -

Free/Open Source Software and Health Care: Benefits and Challenges
International Journal of Innovative Research in Computer Science & Technology (IJIRCST) ISSN: 2347-5552, Volume-3, Issue-3, May 2015 Free/Open Source Software and Health Care: Benefits and Challenges Anu Gupta Abstract— Health care occupies an important place in every of software that would enable users to access source code country. Information technology (IT) can play a vital role to and make modifications [3]. The philosophy of the FSF improve the quality, safety and efficiency of health care. But movement has later been extended by proposing “Open there are several hiccups in wide spread usage of Information Source” concept [4]. Open source software is encouraging technology in health care domain. In such a case Free/Open software companies to release source code for their products Source Software (F/OSS) provides an opportunity that allows [5]. So Free/Open Source Software (F/OSS) is a broad term the entire Internet community to use its combined programming knowledge, creativity and expertise to develop used to embrace software that is developed and released software, which could render benefits to whole community under some sort of Free/Open Source license but all without involving cost and proprietary issues. The current allowing inspection of the software’s source code. paper outlines the general model of F/OSS development and Free/Open source licenses share two characteristics: the highlights the features of few F/OSS products usable in source code has to be made available and license fees are health care. The benefits offered by F/OSS are very nil. The most common license is called GPL (GNU General important in terms of flexibility, no licensing issue, negligible Public License) [6]. -

Report on Existing Open-Source Electronic Medical Records
UCAM-CL-TR-768 Technical Report ISSN 1476-2986 Number 768 Computer Laboratory Report on existing open-source electronic medical records Cecily Morrison, Adona Iosif, Miklos Danka February 2010 15 JJ Thomson Avenue Cambridge CB3 0FD United Kingdom phone +44 1223 763500 http://www.cl.cam.ac.uk/ c 2010 Cecily Morrison, Adona Iosif, Miklos Danka Some figures in this document are best viewed in colour. If you received a black-and-white copy, please consult the online version if necessary. Technical reports published by the University of Cambridge Computer Laboratory are freely available via the Internet: http://www.cl.cam.ac.uk/techreports/ ISSN 1476-2986 INTRODUCTION One of the responsibilities of the World Health Organisation (WHO) is to contain outbreaks of emerging viral disease, such as Ebola or H1N1 (swine flu). To more quickly tackle outbreaks and perhaps even prevent the spread of disease, the WHO organisation needs ways to gain reliable data about diseases as soon as an outbreak is identified as well as to disseminate guidelines of care based on that data. Information Technology (IT) has been considered a good option to do this, although myriad problems of data standards has slowed the process. Recently experts on emerging viral diseases met as part of the EViDence Project to discuss and stipulate what such an IT system might do. This report, an adjunct to that meeting, considers whether there is an existing open-source Clinical Information Systems (CIS) that meets these requirements. EViDence project In October 2009, clinical experts