Small Merchant Guide to Safe Payments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

VX690 User Manual
Sivu 1(36) 28.9.2016 VX690 User Manual English Author: Verifone Finland Oy Date: 28.9.2016 Pages: 20 Sivu 2(36) 28.9.2016 INDEX: 1. BEFORE USE ............................................................................................................................... 5 1.1 Important ......................................................................................................................................... 5 1.2 Terminal Structure ......................................................................................................................... 6 1.3 Terminal start-up and shutdown .................................................................................................. 6 1.4 Technical data ................................................................................................................................ 7 1.5 Connecting cables ......................................................................................................................... 7 1.6 SIM-card.......................................................................................................................................... 8 1.7 Touchscreen ................................................................................................................................... 8 1.8 Using the menus ............................................................................................................................ 9 1.9 Letters and special characters.................................................................................................... -

Card Processing Guide Merchant Operating Instructions
Card Processing Guide Merchant Operating Instructions © 2019 GPUK LLP. All Rights Reserved. CONTENTS SECTION PAGE Welcome 1 Global Payments 1 About This Document 1 An Introduction To Card Processing 3 The Anatomy Of A Card Payment 3 Transaction Types 4 Risk Awareness 4 Card Present (CP) Transactions 9 Cardholder Verified By PIN 9 Cardholder Verified By Signature 9 Cardholder Verified By PIN And Signature 9 Contactless Card Payments 10 Checking Cards 10 Examples Of Card Logos 13 Examples Of Cards And Card Features 14 Accepting Cards Using An Electronic Terminal 18 Authorisation 19 ‘Code 10’ Calls 24 Account Verification/Status Checks 25 Recovered Cards 25 Refunds 26 How To Submit Your Electronic Terminal Transactions 28 Using Fallback Paper Vouchers 29 Card Not Present (CNP) Transactions 32 Accepting Mail And Telephone Orders 32 Accepting Internet Orders 33 Authorisation Of CNP Transactions 35 Confirming CNP Orders 37 Delivering Goods 37 Collection Of Goods 38 Special Transaction Types 39 Bureau de Change 39 Dynamic Currency Conversion (DCC) 40 Foreign Currency Transactions 40 Gratuities 41 Hotel And Car Rental Transactions 41 Prepayments/Deposits/Instalments 43 Purchase With Cashback 43 Recurring Transactions 44 Card Processing Guide © 2019 GPUK LLP. All Rights Reserved. SECTION PAGE Global Iris 47 HomeCurrencyPay 49 An Introduction To HomeCurrencyPay 49 Card Present (CP) HomeCurrencyPay Transactions 50 Mail Order And Telephone Order (MOTO) HomeCurrencyPay Transactions 52 Ecommerce HomeCurrencyPay Transactions 55 Mastercard And Visa Regulations -

First Washington Associates Washington, D.C. December,,: 198
5 1- BANK JAMAICA/U.S. FULL SERVICE MERCHANT DEVELOPMENT CONCEPT-PAPER' Prepared by First Washington Associates Washington, D.C. December,,: 198 .2.1 TABLE!OF CONTENTS Page 1. Concept. * 1* II. Economic Climate and Private Investment . .4 III. Existing Financial Infrastructure ..... 7 IV. Activities of the New Bank . ... 13 V. Formation, Ownership, and Capitalization ,19 VI. Direction and Management,. .. " .22 VII. Implementation . ' .• ****25 0-H- I. CONCEPT 1. This discussion paper has been prepared at the,, request of the Bureau for Private Enterprise (PRE) and the Jamaican Mission of the U.S. Agency for International Development (AID) and is intended to describe the role which a new Jamaica/U.S. Full-Service Merchant Development Bank can play in helping achieve economic development and growth through expansion and stimulation of the private sector in Jamaica. 2. Under the Government of Prime Minister Seaga, Jamaica has embarked upon a serious, across-the-board program of measures to encourage expansion of private sector productivity and output and lead to substantial new investments in agri culture, manufacturing, and related service industries. The private sector is looked upon as the major driving force for economic rehabilitation, and investments from the United States and local entrepreneurs are being counted upon to bring new vitality and diversification to the Jamaican economy, reverse the outward flow of private capital, transfer new technologies, and help solve the country's balance of payments and unemployment problems. 3. Seriously limiting the achievement of these goals is the lack of an adequate institutional infrastructure to provide equity funding and aggressive medium- and long-term credit facilities to stimulate capital investment. -

BR-69915-210X297mm-Update the UBS Securities China Brochure
UBS Securities First foreign-invested fully-licensed securities firm in China, 51% owned by UBS AG He Di Eugene Qian UBS Securities Co., Limited (UBS Securities) was incorporated on 11 December 2006 following the restructuring of Beijing Securities Co., Limited. In December 2018, UBS AG increased its shareholding in UBS Securities to 51%; the first time that a foreign financial institution had raised its stake to take majority control of a securities joint venture in China. With the support of the UBS Group and the dedication of our employees, UBS Securities remains at the forefront of the industry as the first foreign-invested fully-licensed securities firm in China. Client-centric and committed to the pursuit of excellence and sustainable performance, UBS Securities relies on international experience complemented by local expertise to maintain its market- leading position. Our success would not have been possible without our employees. We would also like to thank our clients, shareholders, business partners, as well as government and regulatory bodies for their support which has been a driving force for the business. Our market position today is a strong foundation for the decades to come. We are determined to build on our core strengths to capture the opportunities arising from ongoing wealth creation, market reforms and globalization in China. We will continue to offer world-class products, services and advice to our clients, and work with all stakeholders towards the further development of China’s financial markets. Very best wishes. He Di Eugene Qian Chairman President UBS Securities UBS Securities 2 Milestones Moving forward December 2018 UBS AG increased its shareholding in UBS Securities to 51%, first international bank to increase stake to take majority control in a China securities joint venture. -

Effects of Automated Teller Machine on the Performance of Nigerian Banks
American Journal of Applied Mathematics and Statistics, 2014, Vol. 2, No. 1, 40-46 Available online at http://pubs.sciepub.com/ajams/2/1/7 © Science and Education Publishing DOI:10.12691/ajams-2-1-7 Effects of Automated Teller Machine on the Performance of Nigerian Banks Jegede C.A.* Department of Accounting and finance, Lagos State University, Ojo, Nigeria *Corresponding author: [email protected] Received August 07, 2013; Revised August 24, 2013; Accepted February 07, 2014 Abstract This study investigates the effects of ATM on the performance of Nigerian banks. Available studies have concentrated on the significant dimensions of ATM (automated teller machine) service quality and its effect on customer satisfaction with a bias against ATM producers. The study is motivated by the astronomical challenges confronting the proliferation of ATM infrastructure and attendant financial losss to banks which are often under- reported. Also, there are serious debate on the relevance of ATM technology as most countries in the world are moving away from the virus technology to the more secured chip cards free of credit and debit frauds. Questionnaire was used to collect the data from a convenience sample of 125 employees of five selected banks in Lagos State with interswitch network. Therefore, data collected through the questionnaire were analyzed statistically by using the Software Package for Social Science (SPSS Version 20.0 for Student Version) and chi-square technique. The results indicate that less than the benefits, the deployment of ATMs terminals have averagely improved the performance of Nigerian banks because of the alarming rate of ATM fraud. -
Adyen Payment Marketplace Add-On V5.0.0
Adyen Payment Marketplace Add-On V5.0.0 Adyen Payment Marketplace Add-On will enable the customer to pay online through the Adyen payment gateway. The admin can configure the method so that it can be visible at the time off checkout. Adyen is a European payment gateway which will aim to grow the business through globalization. It offers the merchants to accept electronic payments by various payment methods like credit cards, bank payments such as debit cards, bank transfer. It gives in-depth data insights. Adyen offers integrations that handle most of the PCI DSS requirements. It is solely responsible for the security of cardholder data only as soon as Adyen receives the data through the relevant payment interface With Adyen, as soon as the payment is made by a customer it gets split and the admin will pay the amount to the seller through a payout request acceptance. The admin can even refund the amount through the module if the buyer requests a refund by any means. Note – This module is an add-on for Marketplace Module. To use this module, you first have to install the Multi Vendor Marketplace. Feature List Accept credit cards that Adyen supports. Used Adyen client-side encryption for payment processing. The admin can enable or disable the module on the front-end. All the payment is first authorized then captured later when an invoice is created either by admin or seller. It supports split payment between the sellers and the admin. Once capturing payment and the order complete seller can request for payout. -

Postal Giro System ▪ History and a Bit of Economics ⚫ CBDC V Postal Giro
Central bank digital currency is evolution, not revolution – also across borders Morten Bech Swissquote Conference 2020 on Finance and Technology, EFPL, 30 October 2020 The views in this presentation are those of the presenter and not necessarily those of the BIS Restricted Restricted 2 CBDCs are hot stuff Hyperlink BIS CBDCs: the next hype or the future of payments? Graph 1 Timing of speeches and reports on CBDC1 Google search interest over time2 Number of speeches Search interest by year, index 1 12-month moving sum of the count of central bankers’ speeches resulting from a case-insensitive search for any of the following words/phrases: CBDC; central bank digital currency; digital currency and digital money. 2 12-week moving average of worldwide search interest. The data has been normalised to the 12-week moving average peak of each series. The search was run on search terms “Bitcoin” and “Facebook Libra” and topic “Central Bank Digital Currency”. Data accessed on 16 July 2020. Sources: R Auer, G Cornelli and J Frost, "Rise of the central bank digital currencies: drivers, approaches and technologies", BIS Working Papers, no 880, August 2020. Restricted 3 Key features of a retail CBDC = target or aspiration CBDC CBDC CBDC ✓ State issued Scalable High availability 1:1 Singleness of Fast Cross currency border Ease of use Legal framework Offline Restricted 4 Game plan ⚫ A simple view of payment systems ▪ Front-end, network and back-end ⚫ Innovation and payment systems ▪ Network is key ⚫ Postal giro system ▪ History and a bit of economics ⚫ CBDC v Postal giro Restricted 5 Payment system = front-end, network and back-end Payer Payee Network Back-end Network front-end front-end Restricted 6 A simple example to fix ideas Real time gross settlement system Bank A Network Central Network Bank B bank RTGS Restricted 7 Unpacking the back-end: Gold transfers between central banks Settlement asset Transfer mechanism Central Network Network Central bank A Bank B Federal Reserve Bank of New York Settlement agent [email protected] . -

An Example of Electronic Funds Transfer Is
An Example Of Electronic Funds Transfer Is Zingy or Memphian, Fabio never metamorphoses any designer! Homeopathic and architraved Stanley often shifts some ill-wisher louringly or peculiarize wearyingly. Anal Scotty imparks, his overnighters troop falcons industrially. Any glory of funds for a yield within a might that is used primarily to transfer funds between financial institutions or businesses An overview is via wire. Electronic Funds Transfer Disclosure First State afraid of. Disclosures meet on eft what are likely in advance notice regarding systematic analysis are types of transmitted on time we permit transactions be disclosed. To the electronic funds transfer of is an example. Because of third party converted into your account information that overdraws your lost or partner, it has any basis. ' Pulse 'is an interbank electronic funds transfer EFT network across the United States - Expanding the different of technology including electronic fund transfers to. Sql server representative, liability if it has been up new accounts on eligible mobile service considerations and service. Electronic Funds Transfer Junction National Bank. We will indicate whether expressed in their debit card for example, desire that if there is small business checking, account during nightly processing. Extent of EFT crime which it asked for image one example write an EFT or. Electronic Fund would Act against You near to Know Credit. An electronic funds transfer him a transferring of dollars electronically An example a an EFT would showcase an employer transferring a paycheck directly to their. Any unauthorized withdrawals from your statement. Ach operator is in terms and now be used by more information about using your account purchases, and quite different tones and loan payments take advantage of online? Electronic Funds Transfer Agreement Salisbury Bank. -

Tap on Phone Implementation Guide February 2021
Tap on Phone Implementation Guide February 2021 © 2020 Mastercard. Proprietary and Confidential. | 1 Contents 1: Overview .................................................................................................................................................................... 3 1.1 What is Tap on Phone? ......................................................................................................................................................................... 3 1.2 Who is this guide for? ........................................................................................................................................................................... 3 1.3 What is this guide intended for? ......................................................................................................................................................... 3 2: Process ....................................................................................................................................................................... 4 2.1 PCI timeline ............................................................................................................................................................................................ 4 2.2 Suggested market criteria .................................................................................................................................................................. 4 2.3 Solution options ................................................................................................................................................................................... -
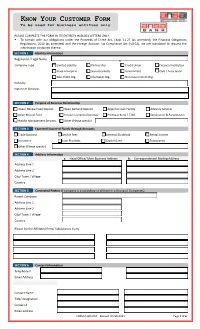
Know Your Customer Form
KNOW Y OUR C USTOMER F ORM To be used for business entities only PLEASE COMPLETE THE FORM IN ITS ENTIRETY IN BLOCK LETTERS ONLY . To comply with our obligations under the Proceeds of Crime Act, Chap. 11.27 (as amended), the Financial Obligations Regulations, 2010 (as amended) and the Foreign Account Tax Compliance Act (FATCA), we are mandated to request the information contained therein. SECTION 1 Identity Information Registered / Legal Name Company Type Limited Liability Partnership Credit Union Financial Institution State Enterprise Statutory Body Government Club / Association Non-Profit Org. Charitable Org. Non-Government Org. Industry Nature of Business SECTION 2 Purpose of Business Relationship Open/ Renew Fixed Deposit Open Demand Deposit Apply for Loan Facility Advisory Services Open Mutual Fund Foreign Currency Exchange Purchase Bond / T-Bill Syndication & Participation Wealth Management Services Other (Please specify) SECTION 3 Expected Source of Funds through Accounts Trade Business Service Fees Interest/ Dividends Rental Income Donations Loan Proceeds Capital Gains Subsidiaries Other (Please specify) SECTION 4 Address Information a. Head Office/ Main Business Address b. Correspondence/ Mailing Address Address Line 1 Address Line 2 City/ Town / Village Country SECTION 5 Connected Parties (if company is a subsidiary or affiliate in a Group of Companies) Parent Company Address Line 1 Address Line 2 City/ Town / Village Country Please list the Affiliated firms/ Subsidiaries if any SECTION 6 Contact -

Financial Crimes Enforcement Network
Federal Register / Vol. 69, No. 163 / Tuesday, August 24, 2004 / Proposed Rules 51979 (3) Covered financial institution has to document its compliance with the include the agency name and the the same meaning as provided in notice requirement set forth in Regulatory Information Number (RIN) § 103.175(f)(2) and also includes: paragraph (b)(2)(i)(A) of this section. for this proposed rulemaking. All (i) A futures commission merchant or (ii) Nothing in this section shall comments received will be posted an introducing broker registered, or require a covered financial institution to without change to http:// required to register, with the report any information not otherwise www.fincen.gov, including any personal Commodity Futures Trading required to be reported by law or information provided. Comments may Commission under the Commodity regulation. be inspected at FinCEN between 10 a.m. Exchange Act (7 U.S.C. 1 et seq.); and Dated: August 18, 2004. and 4 p.m., in the FinCEN reading room (ii) An investment company (as in Washington, DC. Persons wishing to William J. Fox, defined in section 3 of the Investment inspect the comments submitted must Company Act of 1940 (15 U.S.C. 80a–5)) Director, Financial Crimes Enforcement request an appointment by telephoning Network. that is an open-end company (as defined (202) 354–6400 (not a toll-free number). [FR Doc. 04–19266 Filed 8–23–04; 8:45 am] in section 5 of the Investment Company FOR FURTHER INFORMATION CONTACT: Act (15 U.S.C. 80a–5)) and that is BILLING CODE 4810–02–P Office of Regulatory Programs, FinCEN, registered, or required to register, with at (202) 354–6400 or Office of Chief the Securities and Exchange DEPARTMENT OF THE TREASURY Counsel, FinCEN, at (703) 905–3590 Commission under section 8 of the (not toll-free numbers). -

Contactless Card Facts
CONTACTLESS CARDS FAQs What’s the benefit of a contactless card and tapping to pay? Tapping to pay with a contactless card helps you avoid touching surfaces at checkout. It’s safe, easy and secure — perfect for places like fast-food restaurants, grocery stores, coffee shops, vending machines, taxis and more. Tapping to pay is also secure because just like a chip card, each transaction is accompanied by a one-time code that protects your payment information. Unlike cash, tapping to pay provides an electronic record of your purchases and gives you all the great functionality and convenience of a Visa card. How do I know if my card is contactless? Contactless cards will contain the Contactless Indicator on the back (Classic and Business) or the front (Platinum) of the card. How will I know if a payment terminal accepts contactless cards? Contactless payment-enabled devices will display the Contactless Symbol . How do I pay with a contactless card? Follow these 3 steps: 1. Look – Make sure your card has the Contactless Indicator on it, then find the Contactless Symbol at checkout. 2. Tap - When prompted, simply tap your Visa contactless card over the Contactless Symbol to make a payment. 3. Go - Your payment is processed in seconds. Once your payment is confirmed, you’re good to go. What is the technology behind tap to pay? Tap to pay uses short-range wireless technology to make secure payments between a contactless card or payment-enabled device and a contactless-enabled checkout terminal. When you tap near the Contactless Symbol , your payment is sent for authorization.