Learning to Pivot with Adversarial Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
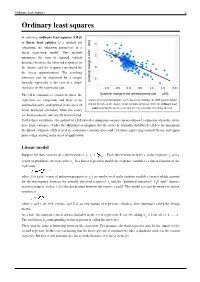
Ordinary Least Squares 1 Ordinary Least Squares
Ordinary least squares 1 Ordinary least squares In statistics, ordinary least squares (OLS) or linear least squares is a method for estimating the unknown parameters in a linear regression model. This method minimizes the sum of squared vertical distances between the observed responses in the dataset and the responses predicted by the linear approximation. The resulting estimator can be expressed by a simple formula, especially in the case of a single regressor on the right-hand side. The OLS estimator is consistent when the regressors are exogenous and there is no Okun's law in macroeconomics states that in an economy the GDP growth should multicollinearity, and optimal in the class of depend linearly on the changes in the unemployment rate. Here the ordinary least squares method is used to construct the regression line describing this law. linear unbiased estimators when the errors are homoscedastic and serially uncorrelated. Under these conditions, the method of OLS provides minimum-variance mean-unbiased estimation when the errors have finite variances. Under the additional assumption that the errors be normally distributed, OLS is the maximum likelihood estimator. OLS is used in economics (econometrics) and electrical engineering (control theory and signal processing), among many areas of application. Linear model Suppose the data consists of n observations { y , x } . Each observation includes a scalar response y and a i i i vector of predictors (or regressors) x . In a linear regression model the response variable is a linear function of the i regressors: where β is a p×1 vector of unknown parameters; ε 's are unobserved scalar random variables (errors) which account i for the discrepancy between the actually observed responses y and the "predicted outcomes" x′ β; and ′ denotes i i matrix transpose, so that x′ β is the dot product between the vectors x and β. -

Quantum State Estimation with Nuisance Parameters 2
Quantum state estimation with nuisance parameters Jun Suzuki E-mail: [email protected] Graduate School of Informatics and Engineering, The University of Electro-Communications, Tokyo, 182-8585 Japan Yuxiang Yang E-mail: [email protected] Institute for Theoretical Physics, ETH Z¨urich, 8093 Z¨urich, Switzerland Masahito Hayashi E-mail: [email protected] Graduate School of Mathematics, Nagoya University, Nagoya, 464-8602, Japan Shenzhen Institute for Quantum Science and Engineering, Southern University of Science and Technology, Shenzhen, 518055, China Center for Quantum Computing, Peng Cheng Laboratory, Shenzhen 518000, China Centre for Quantum Technologies, National University of Singapore, 117542, Singapore Abstract. In parameter estimation, nuisance parameters refer to parameters that are not of interest but nevertheless affect the precision of estimating other parameters of interest. For instance, the strength of noises in a probe can be regarded as a nuisance parameter. Despite its long history in classical statistics, the nuisance parameter problem in quantum estimation remains largely unexplored. The goal of this article is to provide a systematic review of quantum estimation in the presence of nuisance parameters, and to supply those who work in quantum tomography and quantum arXiv:1911.02790v3 [quant-ph] 29 Jun 2020 metrology with tools to tackle relevant problems. After an introduction to the nuisance parameter and quantum estimation theory, we explicitly formulate the problem of quantum state estimation with nuisance parameters. We extend quantum Cram´er-Rao bounds to the nuisance parameter case and provide a parameter orthogonalization tool to separate the nuisance parameters from the parameters of interest. In particular, we put more focus on the case of one-parameter estimation in the presence of nuisance parameters, as it is most frequently encountered in practice. -

Nearly Optimal Tests When a Nuisance Parameter Is Present
Nearly Optimal Tests when a Nuisance Parameter is Present Under the Null Hypothesis Graham Elliott Ulrich K. Müller Mark W. Watson UCSD Princeton University Princeton University and NBER January 2012 (Revised July 2013) Abstract This paper considers nonstandard hypothesis testing problems that involve a nui- sance parameter. We establish an upper bound on the weighted average power of all valid tests, and develop a numerical algorithm that determines a feasible test with power close to the bound. The approach is illustrated in six applications: inference about a linear regression coe¢ cient when the sign of a control coe¢ cient is known; small sample inference about the di¤erence in means from two independent Gaussian sam- ples from populations with potentially di¤erent variances; inference about the break date in structural break models with moderate break magnitude; predictability tests when the regressor is highly persistent; inference about an interval identi…ed parame- ter; and inference about a linear regression coe¢ cient when the necessity of a control is in doubt. JEL classi…cation: C12; C21; C22 Keywords: Least favorable distribution, composite hypothesis, maximin tests This research was funded in part by NSF grant SES-0751056 (Müller). The paper supersedes the corresponding sections of the previous working papers "Low-Frequency Robust Cointegration Testing" and "Pre and Post Break Parameter Inference" by the same set of authors. We thank Lars Hansen, Andriy Norets, Andres Santos, two referees, the participants of the AMES 2011 meeting at Korea University, of the 2011 Greater New York Metropolitan Econometrics Colloquium, and of a workshop at USC for helpful comments. -

Composite Hypothesis, Nuisance Parameters’
Practical Statistics – part II ‘Composite hypothesis, Nuisance Parameters’ W. Verkerke (NIKHEF) Wouter Verkerke, NIKHEF Summary of yesterday, plan for today • Start with basics, gradually build up to complexity of Statistical tests with simple hypotheses for counting data “What do we mean with probabilities” Statistical tests with simple hypotheses for distributions “p-values” “Optimal event selection & Hypothesis testing as basis for event selection machine learning” Composite hypotheses (with parameters) for distributions “Confidence intervals, Maximum Likelihood” Statistical inference with nuisance parameters “Fitting the background” Response functions and subsidiary measurements “Profile Likelihood fits” Introduce concept of composite hypotheses • In most cases in physics, a hypothesis is not “simple”, but “composite” • Composite hypothesis = Any hypothesis which does not specify the population distribution completely • Example: counting experiment with signal and background, that leaves signal expectation unspecified Simple hypothesis ~ s=0 With b=5 s=5 s=10 s=15 Composite hypothesis (My) notation convention: all symbols with ~ are constants Wouter Verkerke, NIKHEF A common convention in the meaning of model parameters • A common convention is to recast signal rate parameters into a normalized form (e.g. w.r.t the Standard Model rate) Simple hypothesis ~ s=0 With b=5 s=5 s=10 s=15 Composite hypothesis ‘Universal’ parameter interpretation makes it easier to work with your models μ=0 no signal Composite hypothesis μ=1 expected signal -

Likelihood Inference in the Presence of Nuisance Parameters N
PHYSTAT2003, SLAC, Stanford, California, September 8-11, 2003 Likelihood Inference in the Presence of Nuisance Parameters N. Reid, D.A.S. Fraser Department of Statistics, University of Toronto, Toronto Canada M5S 3G3 We describe some recent approaches to likelihood based inference in the presence of nuisance parameters. Our approach is based on plotting the likelihood function and the p-value function, using recently developed third order approximations. Orthogonal parameters and adjustments to profile likelihood are also discussed. Connections to classical approaches of conditional and marginal inference are outlined. 1. INTRODUCTION it is defined only up to arbitrary multiples which may depend on y but not on θ. This ensures in particu- We take the view that the most effective form of lar that the likelihood function is invariant to one-to- inference is provided by the observed likelihood func- one transformations of the measurement(s) y. In the tion along with the associated p-value function. In context of independent, identically distributed sam- the case of a scalar parameter the likelihood func- pling, where y = (y1; : : : ; yn) and each yi follows the tion is simply proportional to the density function. model f(y; θ) the likelihood function is proportional The p-value function can be obtained exactly if there to Πf(yi; θ) and the log-likelihood function becomes a is a one-dimensional statistic that measures the pa- sum of independent and identically distributed com- rameter. If not, the p-value can be obtained to a ponents: high order of approximation using recently developed methods of likelihood asymptotics. In the presence `(θ) = `(θ; y) = Σ log f(yi; θ) + a(y): (2) of nuisance parameters, the likelihood function for a ^ (one-dimensional) parameter of interest is obtained The maximum likelihood estimate θ is the value of via an adjustment to the profile likelihood function. -

Exact Statistical Inferences for Functions of Parameters of the Log-Gamma Distribution
UNLV Theses, Dissertations, Professional Papers, and Capstones 5-1-2015 Exact Statistical Inferences for Functions of Parameters of the Log-Gamma Distribution Joseph F. Mcdonald University of Nevada, Las Vegas Follow this and additional works at: https://digitalscholarship.unlv.edu/thesesdissertations Part of the Multivariate Analysis Commons, and the Probability Commons Repository Citation Mcdonald, Joseph F., "Exact Statistical Inferences for Functions of Parameters of the Log-Gamma Distribution" (2015). UNLV Theses, Dissertations, Professional Papers, and Capstones. 2384. http://dx.doi.org/10.34917/7645961 This Dissertation is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Dissertation in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/or on the work itself. This Dissertation has been accepted for inclusion in UNLV Theses, Dissertations, Professional Papers, and Capstones by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. EXACT STATISTICAL INFERENCES FOR FUNCTIONS OF PARAMETERS OF THE LOG-GAMMA DISTRIBUTION by Joseph F. McDonald Bachelor of Science in Secondary Education University of Nevada, Las Vegas 1991 Master of Science in Mathematics University of Nevada, Las Vegas 1993 A dissertation submitted in partial fulfillment of the requirements for the Doctor of Philosophy - Mathematical Sciences Department of Mathematical Sciences College of Sciences The Graduate College University of Nevada, Las Vegas May 2015 We recommend the dissertation prepared under our supervision by Joseph F. -

Confidence Intervals and Nuisance Parameters Common Example
Confidence Intervals and Nuisance Parameters Common Example Interval Estimation in Poisson Sampling with Scale Factor and Background Subtraction The Problem (eg): A “Cut and Count” analysis for a branching fraction B finds n events. ˆ – The background estimate is b ± σb events. – The efficiency and parent sample are estimated to give a scaling factor ˆ f ± σf . How do we determine a (frequency) Confidence Interval? – Assume n is sampled from Poisson, µ = hni = fB + b. ˆ – Assume b is sampled from normal N(b, σb). ˆ – Assume f is sampled from normal N(f, σf ). 1 Frank Porter, March 22, 2005, CITBaBar Example, continued The likelihood function is: 2 2 n −µ 1ˆb−b 1fˆ−f µ e 1 −2 σ −2 σ L(n,ˆb, ˆf; B, b, f) = e b f . n! 2πσbσf µ = hni = fB + b We are interested in the branching fraction B. In particular, would like to summarize data relevant to B, for example, in the form of a confidence interval, without dependence on the uninteresting quantities b and f. b and f are “nuisance parameters”. 2 Frank Porter, March 22, 2005, CITBaBar Interval Estimation in Poisson Sampling (continued) Variety of Approaches – Dealing With the Nuisance Parameters ˆ ˆ Just give n, b ± σb, and f ± σf . – Provides “complete” summary. – Should be done anyway. – But it isn’t a confidence interval. ˆ ˆ Integrate over N(f, σf ) “PDF” for f, N(b, σb) “PDF” for b. (variant: normal assumption in 1/f). – Quasi-Bayesian (uniform prior for f, b (or, eg, for 1/f)). -

Reducing the Sensitivity to Nuisance Parameters in Pseudo-Likelihood Functions
544 The Canadian Journal of Statistics Vol. 42, No. 4, 2014, Pages 544–562 La revue canadienne de statistique Reducing the sensitivity to nuisance parameters in pseudo-likelihood functions Yang NING1*, Kung-Yee LIANG2 and Nancy REID3 1Department of Statistics and Actuarial Science, University of Waterloo, Waterloo, Canada 2Department of Life Sciences and Institute of Genome Sciences, National Yang-Ming University, Taiwan, ROC 3Department of Statistical Science, University of Toronto, Toronto, Canada Key words and phrases: Composite likelihood; higher order inference; invariance; nuisance parameters; pseudo-likelihood. MSC 2010: Primary 62F03; secondary 62F10 Abstract: In a parametric model, parameters are often partitioned into parameters of interest and nuisance parameters. However, as the data structure becomes more complex, inference based on the full likeli- hood may be computationally intractable or sensitive to potential model misspecification. Alternative likelihood-based methods proposed in these settings include pseudo-likelihood and composite likelihood. We propose a simple adjustment to these likelihood functions to reduce the impact of nuisance parameters. The advantages of the modification are illustrated through examples and reinforced through simulations. The adjustment is still novel even if attention is restricted to the profile likelihood. The Canadian Journal of Statistics 42: 544–562; 2014 © 2014 Statistical Society of Canada Resum´ e:´ Les parametres` d’un modele` sont souvent categoris´ es´ comme nuisibles ou d’inter´ et.ˆ A` mesure que la structure des donnees´ devient plus complexe, la vraisemblance peut devenir incalculable ou sensible a` des erreurs de specification.´ La pseudo-vraisemblance et la vraisemblance composite ont et´ epr´ esent´ ees´ comme des solutions dans ces situations. -
![Arxiv:1807.05996V2 [Physics.Data-An] 4 Aug 2018](https://docslib.b-cdn.net/cover/3308/arxiv-1807-05996v2-physics-data-an-4-aug-2018-5263308.webp)
Arxiv:1807.05996V2 [Physics.Data-An] 4 Aug 2018
Lectures on Statistics in Theory: Prelude to Statistics in Practice Robert D. Cousins∗ Dept. of Physics and Astronomy University of California, Los Angeles Los Angeles, California 90095 August 4, 2018 Abstract This is a writeup of lectures on \statistics" that have evolved from the 2009 Hadron Collider Physics Summer School at CERN to the forthcoming 2018 school at Fermilab. The emphasis is on foundations, using simple examples to illustrate the points that are still debated in the professional statistics literature. The three main approaches to interval estimation (Neyman confidence, Bayesian, likelihood ratio) are discussed and compared in detail, with and without nuisance parameters. Hypothesis testing is discussed mainly from the frequentist point of view, with pointers to the Bayesian literature. Various foundational issues are emphasized, including the conditionality principle and the likelihood principle. arXiv:1807.05996v2 [physics.data-an] 4 Aug 2018 ∗[email protected] 1 Contents 1 Introduction 5 2 Preliminaries 6 2.1 Why foundations matter . 6 2.2 Definitions are important . 6 2.3 Key tasks: Important to distinguish . 7 3 Probability 8 3.1 Definitions, Bayes's theorem . 8 3.2 Example of Bayes's theorem using frequentist P . 10 3.3 Example of Bayes's theorem using Bayesian P . 10 3.4 A note re Decisions ................................ 12 3.5 Aside: What is the \whole space"? . 12 4 Probability, probability density, likelihood 12 4.1 Change of observable variable (\metric") x in pdf p(xjµ) . 13 4.2 Change of parameter µ in pdf p(xjµ) ...................... 14 4.3 Probability integral transform . 15 4.4 Bayes's theorem generalized to probability densities . -

P Values and Nuisance Parameters
P Values and Nuisance Parameters Luc Demortier The Rockefeller University, New York, NY 10065, USA Abstract We review the definition and interpretation of p values, describe methods to incorporate systematic uncertainties in their calculation, and briefly discuss a non-regular but common problem caused by nuisance parameters that are unidentified under the null hypothesis. 1 Introduction Statistical theory offers three main paradigms for testing hypotheses: the Bayesian construction of hy- pothesis probabilities, Neyman-Pearson procedures for controlling frequentist error rates, and Fisher's evidential interpretation of tail probabilities. Since practitioners often attempt to combine elements from different approaches, especially the last two, it is useful to illustrate with a couple of examples how they actually address different questions [1]. The first example concerns the selection of a sample of pp¹ collision events for measuring the mass of the top quark. For each event one must decide between two hypotheses, H0 : The event is background, versus H1 : The event contains a top quark. Since the same testing procedure is sequentially repeated on a large number of events, the decision must be made in such a way that the rate of wrong decisions is fully controlled in the long run. Traditionally, this problem is solved with the help of Neyman-Pearson theory, with a terminology adapted to physics goals: the Type-I error rate ® translates to background contamination, and the power of the test to selection efficiency. In principle either hypothesis can be assigned the role of H0 in this procedure. Since only the Type-I error rate is directly adjustable by the investigator (via the size of the critical region), a potentially useful criterion is to define as H0 the hypothesis for which it is deemed more important to control the incorrect rejection probability than the incorrect acceptance probability. -

Stat 5102 Lecture Slides Deck 2
Stat 5102 Lecture Slides Deck 2 Charles J. Geyer School of Statistics University of Minnesota 1 Statistical Inference Statistics is probability done backwards. In probability theory we give you one probability model, also called a probability distribution. Your job is to say something about expectations, probabilities, quantiles, etc. for that distri- bution. In short, given a probability model, describe data from that model. In theoretical statistics, we give you a statistical model, which is a family of probability distributions, and we give you some data assumed to have one of the distributions in the model. Your job is to say something about which distribution that is. In short, given a statistical model and data, infer which distribution in the model is the one for the data. 2 Statistical Models A statistical model is a family of probability distributions. A parametric statistical model is a family of probability distribu- tions specified by a finite set of parameters. Examples: Ber(p), N (µ, σ2), and the like. A nonparametric statistical model is a family of probability dis- tributions too big to be specified by a finite set of parameters. Examples: all probability distributions on R, all continuous sym- metric probability distributions on R, all probability distributions on R having second moments, and the like. 3 Statistical Models and Submodels If M is a statistical model, it is a family of probability distribu- tions. A submodel of a statistical model M is a family of probability distributions that is a subset of M. If M is parametric, then we often specify it by giving the PMF (if the distributions are discrete) or PDF (if the distributions are continuous) { fθ : θ ∈ Θ } where Θ is the parameter space of the model. -

Statistics 1 38
38. Statistics 1 38. STATISTICS Revised September 2015 by G. Cowan (RHUL). This chapter gives an overview of statistical methods used in high-energy physics. In statistics, we are interested in using a given sample of data to make inferences about a probabilistic model, e.g., to assess the model’s validity or to determine the values of its parameters. There are two main approaches to statistical inference, which we may call frequentist and Bayesian. In frequentist statistics, probability is interpreted as the frequency of the outcome of a repeatable experiment. The most important tools in this framework are parameter estimation, covered in Section 38.2, statistical tests, discussed in Section 38.3, and confidence intervals, which are constructed so as to cover the true value of a parameter with a specified probability, as described in Section 38.4.2. Note that in frequentist statistics one does not define a probability for a hypothesis or for the value of a parameter. In Bayesian statistics, the interpretation of probability is more general and includes degree of belief (called subjective probability). One can then speak of a probability density function (p.d.f.) for a parameter, which expresses one’s state of knowledge about where its true value lies. Bayesian methods provide a natural means to include additional information, which in general may be subjective; in fact they require prior probabilities for the hypotheses (or parameters) in question, i.e., the degree of belief about the parameters’ values before carrying out the measurement. Using Bayes’ theorem (Eq. (37.4)), the prior degree of belief is updated by the data from the experiment.