Q2 Consumer Endpoint Protection Apr-Jun 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Ids/Ips
--,.---------------------------------- EO THONG TIN vA TRUYEN THONG CONG HOA xA HOI CHiT NGHIA VII::T NAM DQc qp -T\I' Do - Hl}.nh Phuc S6:'u5J1BTTTT-VNCERT Ha NQi, ngay • V/v Huang dful dam bao an toan thong : /\p C8AJj S:'~~G'lGrf~P CAOSJ Vi~TNAM tin cho cac C6ng/Trang thOng tin di~n t\r 'IAN PliCl,G Dill J,tN"A NO: ~. s6: .2.-.4.6 . T';ProAN CON~ ~PCSYN DEN Ngay:.OLLi.o.1.-1. .' eJ!. Aj0.,t N "'-I. "/I'<'~~""..•••••••••.•Cac Bi), COquan ngang Bi), COquan trvc thui)c C phu. nr~(c)N) iJE N~y:!l1..W~.ILUBND cac tinh, thanh ph5 trvc thui)c Trung uang, Chuy~n:....I(<r... ~~..r••••••••• .............. Th\Ic hi~n chi d:;to cua Thu tuOng Chinh pM v~ vi~c dam bao an toan 17~ong tin cho cac c6ng thong tin di~n tu, dang thai ~S th5ng nh~t v~ ni)i dung va ~ phuang phap quan Iy an t01m thong tin theo yeu cau cua Nghi diM cua Chinh phu s5 4312011/ND-CP ngay 13/612011, Bi) Thong tin va Truy~n thOng hUOng d~n cac co quan nha nuac triSn khai ap d\lng tM li~u "HuOng d~ mi)t s5 bi~n phap ky thu~t co ban dam bao an t01mcho c6ng/trang thong tin di~n ill". Hi li~u nay bao gam mi)t s5 bi~n phap ky thu~t thiSt ySu nh~t nh~m dam bao xay d\Iilg va v~ hanh an toan cac c6ng/trang thOng tin di~n ill va dugc trinh bay trong van ban gui kern theo cong van nay. -

Windows Kernel Hijacking Is Not an Option: Memoryranger Comes to The
WINDOWS KERNEL HIJACKING IS NOT AN OPTION: MEMORYRANGER COMES TO THE RESCUE AGAIN Igor Korkin, PhD Independent Researcher Moscow, Russian Federation [email protected] ABSTRACT The security of a computer system depends on OS kernel protection. It is crucial to reveal and inspect new attacks on kernel data, as these are used by hackers. The purpose of this paper is to continue research into attacks on dynamically allocated data in the Windows OS kernel and demonstrate the capacity of MemoryRanger to prevent these attacks. This paper discusses three new hijacking attacks on kernel data, which are based on bypassing OS security mechanisms. The first two hijacking attacks result in illegal access to files open in exclusive access. The third attack escalates process privileges, without applying token swapping. Although Windows security experts have issued new protection features, access attempts to the dynamically allocated data in the kernel are not fully controlled. MemoryRanger hypervisor is designed to fill this security gap. The updated MemoryRanger prevents these new attacks as well as supporting the Windows 10 1903 x64. Keywords: hypervisor-based protection, Windows kernel, hijacking attacks on memory, memory isolation, Kernel Data Protection. 1. INTRODUCTION the same high privilege level as the OS kernel, and they also include a variety The security of users’ data and of vulnerabilities. Researchers applications depends on the security of consider that “kernel modules (drivers) the OS kernel code and data. Modern introduce additional attack surface, as operating systems include millions of they have full access to the kernel’s lines of code, which makes it address space” (Yitbarek and Austin, impossible to reveal and remediate all 2019). -

Anyconnect および Host Scan のアンチウイルス/アンチスパイウェア
AnyConnect および Host Scan のアンチウイルス/アンチスパイウェア/ファイアウォール サポート表 AnyConnect ポスチャ モジュールにより、AnyConnect Secure Mobility クライアントはホストにインス トールされているオペレーティング システム、およびアンチウイルス、アンチスパイウェア、ファイアウォールの 各ソフトウェアを識別できます。 Host Scan アプリケーションはポスチャ モジュールのコンポーネントに含まれ る、こうした情報を収集するアプリケーションです。 AnyConnect 3.0 より、Host Scan パッケージは AnyConnect Secure Mobility クライアントおよび Cisco Secure Desktop(CSD)の共有コンポーネントになっています。 それ以前は、Host Scan パッケージは CSD を インストールすることによってのみ利用可能になるコンポーネントの 1 つでした。 Host Scan パッケージを CSD から分離したのは、CSD の一部として提供されていたときよりも、ユー ザが頻繁に Host Scan サポート表を更新できるようにするためです。 このサポート表には、ユーザが動的なア クセス ポリシーで使用しているアンチウイルス/アンチスパイウェア/ファイアウォール アプリケーションの製品 名とバージョン情報が記載されています。 シスコでは、Host Scan パッケージに Host Scan アプリケーション、 Host Scan サポート表、および他のコンポーネントを含めて提供しています。 Host Scan サポート表のリスト アンチウイルス アプリケーション総合リスト アンチスパイウェア アプリケーション総合リスト ファイアウォール アプリケーション総合リスト Windows 用アンチウイルス Windows 用アンチスパイウェア Windows 用ファイアウォール Linux 用アンチウイルス Linux 用ファイアウォール Mac OS 用アンチウイルス Mac OS 用アンチスパイウェア Mac OS 用ファイアウォール A B C D E F G H I J K L M N O P Q R S T U V W X Y Z AA AB AC AD AE ファイル データ ファ バージョ データ ファイ データ ファイル データ ファイ エンジンのバー RTP の RTP の 前回のスキャン スキャン/クリー システムのフル アンイン GUI のアク トレイ アイコンの トレイ アイコン 有効期 脅威ログの取 スキャン プログラ フル スキャンの進捗 インストール ディ 一括スキャ メモリ スキャ アンチウイルス製品名 ライブ更新 サービス GUI の表示 のスキャ 有効日の取得 更新の進捗表示 プログラム言語の取得 イル dir の取 市場での別名 ン ルの時刻 のバージョン ルの署名 ジョン チェック 設定 時刻 ニング スキャン ストール ティブ化 表示 の非表示 限 得 ムの実行 表示 レクトリの取得 ン ン 1 ン 得 2 3 360Safe.com 4 360 Antivirus 1.x 9989999898888898 8888 8 9 8 9 9 9 88 5 360杀毒 1.x 9999988898888898 8889 8 8 8 9 9 9 88 6 AEC, spol. s r.o. 7 TrustPort Antivirus 2.x 8888998899888999 9888 8 9 8 9 8 988 8 Agnitum Ltd. -

Leveraging Forticlient with Microsoft Defender: 6 Use Cases
SOLUTION BRIEF Leveraging FortiClient with Microsoft Defender: 6 Use Cases Executive Overview A compromised endpoint can quickly infect an entire enterprise network—which FortiClient Features Include: is why endpoint devices are now a favorite target for cyber criminals. More than an endpoint protection platform that provides automated, next-generation threat nnSecurity Fabric Connector. protection, FortiClient connects endpoints with the Security Fabric. It enables Enables endpoint visibility and endpoint visibility and compliance throughout the Security Fabric architecture. compliance throughout the Combining FortiClient with OS-embedded protection, such as Microsoft Security Fabric architecture. Defender or Microsoft Defender ATP, enhances these capabilities, providing nnVulnerability scanning. an integrated endpoint and network security solution that reinforces enterprise Detects and patches endpoint defenses, reduces complexity, and enhances the end-user experience. vulnerabilities. nn Improving Protection of Endpoint Devices Anti-malware protection. Employs machine learning (ML), FortiClient provides automated threat protection and endpoint vulnerability scanning to help artificial intelligence (AI), and maintain endpoint security hygiene and deliver risk-based visibility across the Fortinet Security cloud-based threat detection Fabric architecture. As a result, organizations can identify and remediate vulnerabilities or in addition to pattern-based compromised hosts across the entire attack surface. malware detection. In some cases, customers may wish to take advantage of certain FortiClient features while nnAnti-exploit engine. Uses leaving existing third-party protections in place. For example, in instances where there are signatureless, behavior-based policies in an organization that require two different antivirus (AV) vendors on an endpoint protection against memory and for governance or compliance reasons, the need for FortiClient alongside a third-party AV fileless attacks; detects exploit solution such as Microsoft Defender is necessitated. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -
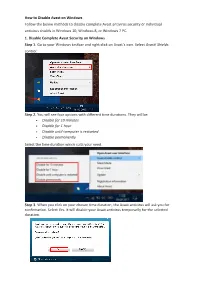
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC
NOT FOR RELEASE, PUBLICATION OR DISTRIBUTION, IN WHOLE OR IN PART, DIRECTLY OR INDIRECTLY, IN, INTO OR FROM ANY JURISDICTION WHERE TO DO SO WOULD CONSTITUTE A VIOLATION OF THE RELEVANT LAWS OR REGULATIONS OF SUCH JURISDICTION FOR IMMEDIATE RELEASE THIS ANNOUNCEMENT CONTAINS INSIDE INFORMATION 10 August 2021 RECOMMENDED MERGER of AVAST PLC with NORTONLIFELOCK INC. to be effected by means of a Scheme of Arrangement under Part 26 of the Companies Act 2006 Summary Further to the announcements made by NortonLifeLock Inc. (“NortonLifeLock”) and Avast plc (“Avast” or the “Company”) on 14 July 2021, the boards of NortonLifeLock and Avast are pleased to announce that they have reached agreement on the terms of a recommended merger of Avast with NortonLifeLock, in the form of a recommended offer by Nitro Bidco Limited (“Bidco”), a wholly- owned subsidiary of NortonLifeLock, for the entire issued and to be issued ordinary share capital of the Company (the “Merger”). It is intended that the Merger will be effected by means of a Court- sanctioned scheme of arrangement under Part 26 of the Companies Act (the “Scheme”). The boards of NortonLifeLock and Avast believe the Merger has compelling strategic logic and represents an attractive opportunity to create a new, industry leading consumer Cyber Safety business, leveraging the established brands, technical expertise and innovation of both groups to deliver substantial benefits to consumers, shareholders and other stakeholders. Under the terms of the Merger, Avast Shareholders will be entitled to receive: for each Avast Share held: USD 7.61 in cash and 0.0302 of a New NortonLifeLock Share in respect of their entire holding of Avast Shares (the “Majority Cash Option”).