An Algorithm That Decides PRIMES in Polynomial Time
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Saddle Point Method in Combinatorics Asymptotic Analysis: Successes and Failures (A Personal View)
Pn The number of inversions in permutations Median versus A (A large) for a Luria-Delbruck-like distribution, with parameter A Sum of positions of records in random permutations Merten's theorem for toral automorphisms Representations of numbers as k=−n "k k The q-Catalan numbers A simple case of the Mahonian statistic Asymptotics of the Stirling numbers of the first kind revisited The Saddle point method in combinatorics asymptotic analysis: successes and failures (A personal view) Guy Louchard May 31, 2011 Guy Louchard The Saddle point method in combinatorics asymptotic analysis: successes and failures (A personal view) Pn The number of inversions in permutations Median versus A (A large) for a Luria-Delbruck-like distribution, with parameter A Sum of positions of records in random permutations Merten's theorem for toral automorphisms Representations of numbers as k=−n "k k The q-Catalan numbers A simple case of the Mahonian statistic Asymptotics of the Stirling numbers of the first kind revisited Outline 1 The number of inversions in permutations 2 Median versus A (A large) for a Luria-Delbruck-like distribution, with parameter A 3 Sum of positions of records in random permutations 4 Merten's theorem for toral automorphisms Pn 5 Representations of numbers as k=−n "k k 6 The q-Catalan numbers 7 A simple case of the Mahonian statistic 8 Asymptotics of the Stirling numbers of the first kind revisited Guy Louchard The Saddle point method in combinatorics asymptotic analysis: successes and failures (A personal view) Pn The number of inversions in permutations Median versus A (A large) for a Luria-Delbruck-like distribution, with parameter A Sum of positions of records in random permutations Merten's theorem for toral automorphisms Representations of numbers as k=−n "k k The q-Catalan numbers A simple case of the Mahonian statistic Asymptotics of the Stirling numbers of the first kind revisited The number of inversions in permutations Let a1 ::: an be a permutation of the set f1;:::; ng. -

CS321 Spring 2021
CS321 Spring 2021 Lecture 2 Jan 13 2021 Admin • A1 Due next Saturday Jan 23rd – 11:59PM Course in 4 Sections • Section I: Basics and Sorting • Section II: Hash Tables and Basic Data Structs • Section III: Binary Search Trees • Section IV: Graphs Section I • Sorting methods and Data Structures • Introduction to Heaps and Heap Sort What is Big O notation? • A way to approximately count algorithm operations. • A way to describe the worst case running time of algorithms. • A tool to help improve algorithm performance. • Can be used to measure complexity and memory usage. Bounds on Operations • An algorithm takes some number of ops to complete: • a + b is a single operation, takes 1 op. • Adding up N numbers takes N-1 ops. • O(1) means ‘on order of 1’ operation. • O( c ) means ‘on order of constant’. • O( n) means ‘ on order of N steps’. • O( n2) means ‘ on order of N*N steps’. How Does O(k) = O(1) O(n) = c * n for some c where c*n is always greater than n for some c. O( k ) = c*k O( 1 ) = cc * 1 let ccc = c*k c*k = c*k* 1 therefore O( k ) = c * k * 1 = ccc *1 = O(1) O(n) times for sorting algorithms. Technique O(n) operations O(n) memory use Insertion Sort O(N2) O( 1 ) Bubble Sort O(N2) O(1) Merge Sort N * log(N) O(1) Heap Sort N * log(N) O(1) Quicksort O(N2) O(logN) Memory is in terms of EXTRA memory Primary Notation Types • O(n) = Asymptotic upper bound. -
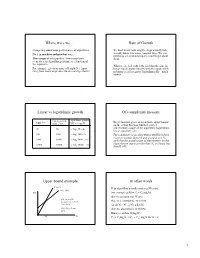
Rate of Growth Linear Vs Logarithmic Growth O() Complexity Measure
Where were we…. Rate of Growth • Comparing worst case performance of algorithms. We don't know how long the steps actually take; we only know it is some constant time. We can • Do it in machine-independent way. just lump all constants together and forget about • Time usage of an algorithm: how many basic them. steps does an algorithm perform, as a function of the input size. What we are left with is the fact that the time in • For example: given an array of length N (=input linear search grows linearly with the input, while size), how many steps does linear search perform? in binary search it grows logarithmically - much slower. Linear vs logarithmic growth O() complexity measure Linear growth: Logarithmic growth: Input size T(N) = c log N Big O notation gives an asymptotic upper bound T(N) = N* c 2 on the actual function which describes 10 10c c log 10 = 4c time/memory usage of the algorithm: logarithmic, 2 linear, quadratic, etc. 100 100c c log2 100 = 7c The complexity of an algorithm is O(f(N)) if there exists a constant factor K and an input size N0 1000 1000c c log2 1000 = 10c such that the actual usage of time/memory by the 10000 10000c c log 10000 = 16c algorithm on inputs greater than N0 is always less 2 than K f(N). Upper bound example In other words f(N)=2N If an algorithm actually makes g(N) steps, t(N)=3+N time (for example g(N) = C1 + C2log2N) there is an input size N' and t(N) is in O(N) because for all N>3, there is a constant K, such that 2N > 3+N for all N > N' , g(N) ≤ K f(N) Here, N0 = 3 and then the algorithm is in O(f(N). -

Asymptotic Analysis for Periodic Structures
ASYMPTOTIC ANALYSIS FOR PERIODIC STRUCTURES A. BENSOUSSAN J.-L. LIONS G. PAPANICOLAOU AMS CHELSEA PUBLISHING American Mathematical Society • Providence, Rhode Island ASYMPTOTIC ANALYSIS FOR PERIODIC STRUCTURES ASYMPTOTIC ANALYSIS FOR PERIODIC STRUCTURES A. BENSOUSSAN J.-L. LIONS G. PAPANICOLAOU AMS CHELSEA PUBLISHING American Mathematical Society • Providence, Rhode Island M THE ATI A CA M L ΤΡΗΤΟΣ ΜΗ N ΕΙΣΙΤΩ S A O C C I I R E E T ΑΓΕΩΜΕ Y M A F O 8 U 88 NDED 1 2010 Mathematics Subject Classification. Primary 80M40, 35B27, 74Q05, 74Q10, 60H10, 60F05. For additional information and updates on this book, visit www.ams.org/bookpages/chel-374 Library of Congress Cataloging-in-Publication Data Bensoussan, Alain. Asymptotic analysis for periodic structures / A. Bensoussan, J.-L. Lions, G. Papanicolaou. p. cm. Originally published: Amsterdam ; New York : North-Holland Pub. Co., 1978. Includes bibliographical references. ISBN 978-0-8218-5324-5 (alk. paper) 1. Boundary value problems—Numerical solutions. 2. Differential equations, Partial— Asymptotic theory. 3. Probabilities. I. Lions, J.-L. (Jacques-Louis), 1928–2001. II. Papani- colaou, George. III. Title. QA379.B45 2011 515.353—dc23 2011029403 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. Republication, systematic copying, or multiple reproduction of any material in this publication is permitted only under license from the American Mathematical Society. -

Definite Integrals in an Asymptotic Setting
A Lost Theorem: Definite Integrals in An Asymptotic Setting Ray Cavalcante and Todor D. Todorov 1 INTRODUCTION We present a simple yet rigorous theory of integration that is based on two axioms rather than on a construction involving Riemann sums. With several examples we demonstrate how to set up integrals in applications of calculus without using Riemann sums. In our axiomatic approach even the proof of the existence of the definite integral (which does use Riemann sums) becomes slightly more elegant than the conventional one. We also discuss an interesting connection between our approach and the history of calculus. The article is written for readers who teach calculus and its applications. It might be accessible to students under a teacher’s supervision and suitable for senior projects on calculus, real analysis, or history of mathematics. Here is a summary of our approach. Let ρ :[a, b] → R be a continuous function and let I :[a, b] × [a, b] → R be the corresponding integral function, defined by y I(x, y)= ρ(t)dt. x Recall that I(x, y) has the following two properties: (A) Additivity: I(x, y)+I (y, z)=I (x, z) for all x, y, z ∈ [a, b]. (B) Asymptotic Property: I(x, x + h)=ρ (x)h + o(h)ash → 0 for all x ∈ [a, b], in the sense that I(x, x + h) − ρ(x)h lim =0. h→0 h In this article we show that properties (A) and (B) are characteristic of the definite integral. More precisely, we show that for a given continuous ρ :[a, b] → R, there is no more than one function I :[a, b]×[a, b] → R with properties (A) and (B). -

Comparing the Heuristic Running Times And
Comparing the heuristic running times and time complexities of integer factorization algorithms Computational Number Theory ! ! ! New Mexico Supercomputing Challenge April 1, 2015 Final Report ! Team 14 Centennial High School ! ! Team Members ! Devon Miller Vincent Huber ! Teacher ! Melody Hagaman ! Mentor ! Christopher Morrison ! ! ! ! ! ! ! ! ! "1 !1 Executive Summary....................................................................................................................3 2 Introduction.................................................................................................................................3 2.1 Motivation......................................................................................................................3 2.2 Public Key Cryptography and RSA Encryption............................................................4 2.3 Integer Factorization......................................................................................................5 ! 2.4 Big-O and L Notation....................................................................................................6 3 Mathematical Procedure............................................................................................................6 3.1 Mathematical Description..............................................................................................6 3.1.1 Dixon’s Algorithm..........................................................................................7 3.1.2 Fermat’s Factorization Method.......................................................................7 -

Introducing Taylor Series and Local Approximations Using a Historical and Semiotic Approach Kouki Rahim, Barry Griffiths
Introducing Taylor Series and Local Approximations using a Historical and Semiotic Approach Kouki Rahim, Barry Griffiths To cite this version: Kouki Rahim, Barry Griffiths. Introducing Taylor Series and Local Approximations using a Historical and Semiotic Approach. IEJME, Modestom LTD, UK, 2019, 15 (2), 10.29333/iejme/6293. hal- 02470240 HAL Id: hal-02470240 https://hal.archives-ouvertes.fr/hal-02470240 Submitted on 7 Feb 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. INTERNATIONAL ELECTRONIC JOURNAL OF MATHEMATICS EDUCATION e-ISSN: 1306-3030. 2020, Vol. 15, No. 2, em0573 OPEN ACCESS https://doi.org/10.29333/iejme/6293 Introducing Taylor Series and Local Approximations using a Historical and Semiotic Approach Rahim Kouki 1, Barry J. Griffiths 2* 1 Département de Mathématique et Informatique, Université de Tunis El Manar, Tunis 2092, TUNISIA 2 Department of Mathematics, University of Central Florida, Orlando, FL 32816-1364, USA * CORRESPONDENCE: [email protected] ABSTRACT In this article we present the results of a qualitative investigation into the teaching and learning of Taylor series and local approximations. In order to perform a comparative analysis, two investigations are conducted: the first is historical and epistemological, concerned with the pedagogical evolution of semantics, syntax and semiotics; the second is a contemporary institutional investigation, devoted to the results of a review of curricula, textbooks and course handouts in Tunisia and the United States. -

An Introduction to Asymptotic Analysis Simon JA Malham
An introduction to asymptotic analysis Simon J.A. Malham Department of Mathematics, Heriot-Watt University Contents Chapter 1. Order notation 5 Chapter 2. Perturbation methods 9 2.1. Regular perturbation problems 9 2.2. Singular perturbation problems 15 Chapter 3. Asymptotic series 21 3.1. Asymptotic vs convergent series 21 3.2. Asymptotic expansions 25 3.3. Properties of asymptotic expansions 26 3.4. Asymptotic expansions of integrals 29 Chapter 4. Laplace integrals 31 4.1. Laplace's method 32 4.2. Watson's lemma 36 Chapter 5. Method of stationary phase 39 Chapter 6. Method of steepest descents 43 Bibliography 49 Appendix A. Notes 51 A.1. Remainder theorem 51 A.2. Taylor series for functions of more than one variable 51 A.3. How to determine the expansion sequence 52 A.4. How to find a suitable rescaling 52 Appendix B. Exam formula sheet 55 3 CHAPTER 1 Order notation The symbols , o and , were first used by E. Landau and P. Du Bois- Reymond and areOdefined as∼ follows. Suppose f(z) and g(z) are functions of the continuous complex variable z defined on some domain C and possess D ⊂ limits as z z0 in . Then we define the following shorthand notation for the relative!propertiesD of these functions in the limit z z . ! 0 Asymptotically bounded: f(z) = (g(z)) as z z ; O ! 0 means that: there exists constants K 0 and δ > 0 such that, for 0 < z z < δ, ≥ j − 0j f(z) K g(z) : j j ≤ j j We say that f(z) is asymptotically bounded by g(z) in magnitude as z z0, or more colloquially, and we say that f(z) is of `order big O' of g(z). -

Big-O Notation
The Growth of Functions and Big-O Notation Introduction Note: \big-O" notation is a generic term that includes the symbols O, Ω, Θ, o, !. Big-O notation allows us to describe the aymptotic growth of a function f(n) without concern for i) constant multiplicative factors, and ii) lower-order additive terms. By asymptotic growth we mean the growth of the function as input variable n gets arbitrarily large. As an example, consider the following code. int sum = 0; for(i=0; i < n; i++) for(j=0; j < n; j++) sum += (i+j)/6; How much CPU time T (n) is required to execute this code as a function of program variable n? Of course, the answer will depend on factors that may be beyond our control and understanding, including the language compiler being used, the hardware of the computer executing the program, the computer's operating system, and the nature and quantity of other programs being run on the computer. However, we can say that the outer for loop iterates n times and, for each of those iterations, the inner loop will also iterate n times for a total of n2 iterations. Moreover, for each iteration will require approximately a constant number c of clock cycles to execture, where the number of clock cycles varies with each system. So rather than say \T (n) is approximately cn2 nanoseconds, for some constant c that will vary from person to person", we instead use big-O notation and write T (n) = Θ(n2) nanoseconds. This conveys that the elapsed CPU time will grow quadratically with respect to the program variable n. -

13.7 Asymptotic Notation
“mcs” — 2015/5/18 — 1:43 — page 528 — #536 13.7 Asymptotic Notation Asymptotic notation is a shorthand used to give a quick measure of the behavior of a function f .n/ as n grows large. For example, the asymptotic notation of ⇠ Definition 13.4.2 is a binary relation indicating that two functions grow at the same rate. There is also a binary relation “little oh” indicating that one function grows at a significantly slower rate than another and “Big Oh” indicating that one function grows not much more rapidly than another. 13.7.1 Little O Definition 13.7.1. For functions f; g R R, with g nonnegative, we say f is W ! asymptotically smaller than g, in symbols, f .x/ o.g.x//; D iff lim f .x/=g.x/ 0: x D !1 For example, 1000x1:9 o.x2/, because 1000x1:9=x2 1000=x0:1 and since 0:1 D D 1:9 2 x goes to infinity with x and 1000 is constant, we have limx 1000x =x !1 D 0. This argument generalizes directly to yield Lemma 13.7.2. xa o.xb/ for all nonnegative constants a<b. D Using the familiar fact that log x<xfor all x>1, we can prove Lemma 13.7.3. log x o.x✏/ for all ✏ >0. D Proof. Choose ✏ >ı>0and let x zı in the inequality log x<x. This implies D log z<zı =ı o.z ✏/ by Lemma 13.7.2: (13.28) D ⌅ b x Corollary 13.7.4. -

Binary Search
UNIT 5B Binary Search 15110 Principles of Computing, 1 Carnegie Mellon University - CORTINA Course Announcements • Sunday’s review sessions at 5‐7pm and 7‐9 pm moved to GHC 4307 • Sample exam available at the SCHEDULE & EXAMS page http://www.cs.cmu.edu/~15110‐f12/schedule.html 15110 Principles of Computing, 2 Carnegie Mellon University - CORTINA 1 This Lecture • A new search technique for arrays called binary search • Application of recursion to binary search • Logarithmic worst‐case complexity 15110 Principles of Computing, 3 Carnegie Mellon University - CORTINA Binary Search • Input: Array A of n unique elements. – The elements are sorted in increasing order. • Result: The index of a specific element called the key or nil if the key is not found. • Algorithm uses two variables lower and upper to indicate the range in the array where the search is being performed. – lower is always one less than the start of the range – upper is always one more than the end of the range 15110 Principles of Computing, 4 Carnegie Mellon University - CORTINA 2 Algorithm 1. Set lower = ‐1. 2. Set upper = the length of the array a 3. Return BinarySearch(list, key, lower, upper). BinSearch(list, key, lower, upper): 1. Return nil if the range is empty. 2. Set mid = the midpoint between lower and upper 3. Return mid if a[mid] is the key you’re looking for. 4. If the key is less than a[mid], return BinarySearch(list,key,lower,mid) Otherwise, return BinarySearch(list,key,mid,upper). 15110 Principles of Computing, 5 Carnegie Mellon University - CORTINA Example -

A Potentially Fast Primality Test
A Potentially Fast Primality Test Tsz-Wo Sze February 20, 2007 1 Introduction In 2002, Agrawal, Kayal and Saxena [3] gave the ¯rst deterministic, polynomial- time primality testing algorithm. The main step was the following. Theorem 1.1. (AKS) Given an integer n > 1, let r be an integer such that 2 ordr(n) > log n. Suppose p (x + a)n ´ xn + a (mod n; xr ¡ 1) for a = 1; ¢ ¢ ¢ ; b Á(r) log nc: (1.1) Then, n has a prime factor · r or n is a prime power. The running time is O(r1:5 log3 n). It can be shown by elementary means that the required r exists in O(log5 n). So the running time is O(log10:5 n). Moreover, by Fouvry's Theorem [8], such r exists in O(log3 n), so the running time becomes O(log7:5 n). In [10], Lenstra and Pomerance showed that the AKS primality test can be improved by replacing the polynomial xr ¡ 1 in equation (1.1) with a specially constructed polynomial f(x), so that the degree of f(x) is O(log2 n). The overall running time of their algorithm is O(log6 n). With an extra input integer a, Berrizbeitia [6] has provided a deterministic primality test with time complexity 2¡ min(k;b2 log log nc)O(log6 n), where 2kjjn¡1 if n ´ 1 (mod 4) and 2kjjn + 1 if n ´ 3 (mod 4). If k ¸ b2 log log nc, this algorithm runs in O(log4 n). The algorithm is also a modi¯cation of AKS by verifying the congruent equation s (1 + mx)n ´ 1 + mxn (mod n; x2 ¡ a) for a ¯xed s and some clever choices of m¡ .¢ The main drawback of this algorithm¡ ¢ is that it requires the Jacobi symbol a = ¡1 if n ´ 1 (mod 4) and a = ¡ ¢ n n 1¡a n = ¡1 if n ´ 3 (mod 4).