Security and Privacy Aspects of Mobile Platforms and Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Toshiba AC100 / Dynabook AZ Board: Compal Paz00 DRAM: 512 Mib MMC: Sdhci@C8000000: 1, Sdhci@C8000600: 0 Loading Environment from MMC
Compal_LA-6352P_PAZ00_AC100.pdf t=0x9babec8cell=0x9babf80 [0,0] Contents: [Dobrica PavlinuÅ¡iÄ's random unstructured stuff] • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (kernel) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (cpuinfo) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (Rooting) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (nvflash) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (fastboot.stock.bin) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (backup) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (Linux) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (links) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (phh 2.6.32 kernel with working suspend and audio) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (mainline kernel) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (u-boot from APX) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (build u-boot) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (build kernel) ◊ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (create initrd with new modules) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (create bootloader file) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (serial port) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (bootstrap debian) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (u-boot over pax, usb filesystem) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (wifi) • Dobrica PavlinuÅ¡iÄ's random unstructured stuff (disk speed) ♦ Dobrica PavlinuÅ¡iÄ's random unstructured stuff (tuhing block size) • Dobrica PavlinuÅ¡iÄ's -

Android (Operating System) 1 Android (Operating System)
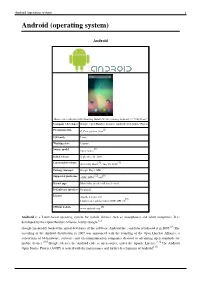
android text PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 11 Sep 2011 07:56:19 UTC Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google, running Android 2.3 "Gingerbread" Company / developer Google Inc, Open Handset Alliance [1] Programmed in C (core), Java (UI), C++ Working state Current [2] [3] Source model Mixed (free and open source software and proprietary software) Initial release 21 October 2008 [4] [4] Latest stable release Tablets: 3.2 (Honeycomb) Phones: 2.3.6 (Gingerbread) / 2 September 2011 Package manager APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Linux kernel (monolithic) Android (operating system) 2 Default user interface Graphical [7] License Apache License 2.0 before 3.0, closed source for 3.0, 3.1 and 3.2: Linux kernel patches under GNU GPL v2 [8] Official website android.com Android is an operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance led by Google.[9] [10] Google purchased the initial developer of the software, Android Inc., in 2005.[11] The unveiling of the Android distribution on 5 November 2007 was announced with the founding of the Open Handset Alliance, a consortium of 84 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[12] [13] [14] [15] Google released most of the Android code under the Apache License, a free software license.[16] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[17] Android consists of a kernel based on the Linux kernel, with middleware, libraries and APIs written in C and application software running on an application framework which includes Java-compatible libraries based on Apache Harmony. -
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google. -

Toshiba Ac100-111
Windows®. Life without Walls™. Toshiba recommends Windows 7. TOSHIBA AC100-111 TOSHIBA AC100 – WEB COMPUTING AT THE SPEED OF NOW. Combining the functionality of a smartphone and the usability of a netbook, the Toshiba AC100 is a thin, light and mobile internet always-connected device that helps you access content from anywhere. Model Part No. List Price exclusive EAN Code incl. VAT Toshiba AC100-111 PDN01E-00600WS4 699 4026203819269 Specification Processor / technology NVIDIA® Tegra™ 250 Mobile Web Processor (1.00 GHz, 333 MHz FSB, 1 MB L2 Cache) Chipset integrated in NVIDIA® Tegra™ 250 Mobile Web Processor Operating system Toshiba Home Menu for Android™ 2.1 (German, French, Italian, English) Display 25.7cm (10.1”) Toshiba TruBrite® WSVGA TFT High Brightness display with 16 : 9 aspect ratio and LED backlighting Maximum number of colors: 16.7 million, high brightness: 200 cd/m2, Resolution: 1,024 x 600 Hard disk 32 GB eMMC (SSD - Solid State Drive ) System memory 512MB (onboard) DDR2 RAM (800 MHz), maximum expandability: 512MB DDR2 RAM Optical drive optional external DVD Super Multi drive (DL) via USB Diskette drive optional external 3.5” Floppy disk drive via USB Graphic adapter Ultra Low-power (ULP) GeForce® Graphics Processing integrated in NVIDIA® Tegra™ 250 Mobile Web Processor Keyboard 86 keys, Euro keys, full-sized matt black keyboard Pointing device Touchpad Wired communication no Wireless communication Ralink® Wireless LAN (802.11b/g/n) and Bluetooth® 2.1 with EDR (Enhanced Data Rate), 3G Mobile Breitband WWAN/3G (HSDPA 7.2Mbps -

TOSHIBA AC100 Il Web Alla Velocità Della Luce
TOSHIBA AC100 Il Web alla velocità della luce Schermo TruBrite® da 10" con retroilluminazione LED Tastiera standard per una digitazione comoda I LED di notifica laterali si illuminano se ricevi una mail Benvenuto nel futuro dei computer ultramobili. In grado di coniugare le funzionalità di uno smartphone con la praticità di un netbook, lo strabiliante Toshiba AC100 è un dispositivo Internet mobile incredibilmente sottile, leggero e sempre connesso che ti consente di accedere e condividere i contenuti Web ovunque ti trovi. L'interfaccia Toshiba Home Menu per Android™ offre all'utente un'esperienza intuitiva e altamente personale, mentre l'ultimissima tecnologia di connettività WiFi o a banda larga mobile* ti consente di accedere a posta elettronica, social network e applicazioni Internet ovunque ti trovi. Grazie all'incredibile durata massima della batteria pari a 8 ore (7 giorni in standby) con funzionalità Instant On, troverai il Toshiba AC100 pronto ogniqualvolta lo desideri, mentre i LED laterali ti avviseranno all'istante quando arrivo di un nuovo messaggio di posta elettronica. Non è uno smartphone. Non è un netbook. È il compagno essenziale per il Web. INTERFACCIA TOSHIBA HOME MENU 7 GIORNI DI DURATA IN STANDBY DESIGN ULTRASOTTILE E LEGGERO Rapido accesso alle tue applicazioni grazie Con massimo 8 ore di durata della batteria Con uno spessore di appena 14 mm nel punto a Toshiba Home Menu con schermate quando il computer è in uso, 7 giorni quando più sottile e un eccezionale case ultraleggero, il personalizzate adatte alle tue abitudini. è in standby con funzionalità Instant On, Toshiba AC100 è il compagno perfetto per il hai accesso al Web ogniqualvolta lo desideri. -

Dokumentation Backup Und Installation Ubuntu 12 Auf Toshiba
Dokumentation Backup und Installation Ubuntu 12 auf Toshiba AC 100V Das folgende How-to habe ich mir aus verschiedenen Quellen im Netz zusammengestellt und beinhaltet wesentlich mehr Hinweise als ich sie selbst benötigt habe. Kurzanleitung: die prinzipielle Abfolge bestand aus – Backup (s. Punkt 1) Quellen: http://ac100.grandou.net/nvflash + http://ac100.grandou.net/backups – dem nvflash setup (s. Punkt 1) – s.u. bis zur 'Note' – der Installation (s. Punkt 2) – s.u. komplett, dauerte auch nur ca. 30 Min. Alles weitere wie ein anderer Desktop oder Programme sowie deren Anpassungen wahlweise! Leider gibt es manche Programme nicht für ARM-PROZESSOREN! Inhalt: 0. Start (just Intro...) 1. Backup (inkl. Verweis auf restore) 2. Installation (inkl. das Danach..) 3. Anpassungen: Ton, Flash, Desktop etc. 4. zusätzliche Programme 5. Troubleshooting super Quellen: http://wiki.informatik.hu- berlin.de/nomads/index.php/Erfahrungsbericht_Toshiba_AC100#Grundlagen_zum_Flashen (http://www.arm-community.de/news/betriebssysteme/162-wie-installiere-ich-ubuntu-1110-auf- meinem-toshiba-ac100) 0. Start recovery/flash mode des netbook: a) Connect a USB-cable between your ac100 (mini-usb) to your PC. Enter the recovery mode by keep pressing CTRL+ESC and power-up the AC100. The AC100 will turn on (check LED) but the display will remain dark. b) Shut down your AC, connect it to your PC with the USB cable. Hold down [CTRL]+[ESC] on your AC and switch it on. Keep [CTRL]+[ESC] pressed for a while! After that, your AC should be on (check power LED) with the display off. Now you are in service mode and you can access it via nvflash. -

(ANTSIT) Final Report To
An investigation of appropriate new technologies to support interactive teaching in Zambian schools (ANTSIT) Final report to DfID A joint report from Aptivate and the Centre for Commonwealth Education (University of Cambridge) Björn Haßler, Sara Hennessy, Tom Lord, Andrew Cross, Alan Jackson, Matthew Simpson 31st March 2011 This is the final report of the ANTSIT project under the New and Emerging Technologies Research programme Phase 1: 2010-2011. This is the low-bandwidth accessible version of the report, containing fewer images. ©2011 Aptivate Text: Licensed under Creative Commons Attribution Only 2.0 UK Images: All rights reserved. (Contact us for reproduction.) Maps: © Google and respective providers. Aptivate The Humanitarian Centre Fenner's Gresham Road Cambridge CB1 2ES http://www.aptivate.org Dr Björn Haßler [email protected] Centre for Commonwealth Education Faculty of Education 184 Hills Road Cambridge CB2 8PQ http://www.educ.cam.ac.uk Dr Sara Hennessy [email protected] This document was formatted in OpenOffice. Paragraphs are left justified as this makes it easier to read for some readers. This document is an output from a project funded by the UK Department for International Development (DFID) for the benefit of developing countries. However, the views expressed and information contained in it are not necessarily those of or endorsed by DFID, which can accept no responsibility for such views or information or for any reliance placed on them. Version 1.0.9 (low bandwidth) 2 Table of Contents 1 Introduction and background .....................................................................................................7 -
Toshiba AC Series AC100 Laptop Part Number - PDN01A-00D01F Anywhere, Anytime Access to Your Life in the Cloud
Toshiba AC Series AC100 Laptop Part Number - PDN01A-00D01F Anywhere, anytime access to your life in the Cloud. This revolutionary thin and light Cloud Computing device gives you affordable access to all your applications, data and content anytime, anywhere. This thin and light device has 10.1” screen and intuitive interface, which gives you easy access to the applications and data you’ve stored in the Cloud. It features a 32GB solid state drive, an NVIDIA processor and a suite of screen tools that give you the power and performance to handle rich content and web-browsing without the compromises of a phone-size interface. General CPU NVIDIA® Tegra T250 Mobile Processor Screen Size 10.1" Widescreen SVGA TFT Active Matrix 200NIT CSV, LED Backlight Display (1024 x 600) Platform Android 2.1 Memory 512MB DDR2 (533MHz) On board (No free slots) Storage 32GB eMMC Flash Storage Audio Intel High Definition Audio Sound Speakers Stereo speaker Sound High quality stereo speakers Webcam Yes Buttons and Pointing Keyboard and Wide TouchPad™ pointing device, 2 Buttons device Power Supply 30W Worldwide AC Adaptor Standard Warranty* 1 Year limited parts and labour warranty Security Kensington® cable lock slot for optional theft protection devices Also included is Dataviz, fring, Evernote, SingleClick Connect, Opera Mobile Browser, and FBREader, Toshiba Home Menu which includes: Toshiba File Manager, Toshiba Power Manager, Software Toshiba Media Player, Screen Capture, Widgets included: Toshiba Ebook, Toshiba YouTube, Toshiba Social Media, Toshiba Memo, Search, -

Getting Slackware ARM on the Toshiba AC100 (Also Know As the Dynabook AZ) Getting Slackware ARM on the Toshiba AC100 (Also Know As the Dynabook AZ)
2021/07/26 12:22 (UTC) 1/11 Getting Slackware ARM on the Toshiba AC100 (also know as the Dynabook AZ) Getting Slackware ARM on the Toshiba AC100 (also know as the Dynabook AZ) When all this started off I was using ARMedslack 13.37 but as of version 14 the official Slackware ARM port changed name to Slackware ARM. Any reference to ARMedslack in this short tutorial refers to the Slackware ARM official port. Preface The Slackware ARM userland can run on almost any ARM based hardware out there and the Toshiba AC100 is no exception to that rule of thumb. The only impediment to going straight ahead is the kernel. I like to work around the problem by borrowing the kernel from some other distribution that has support for the AC100. currently you have 3 options to get reasonable support for the hardware: 2.6.38 kernel patched up for AC100 3.0 kernel patched up for AC100 3.15+ mainstream kernel (untested yet) The 3.1 kernel development got broken on the way and to my understanding is unmaintained. There are several places you can get the binary kernel images or the sources to compile them I generally look for Ubuntu first. Initially I used the Ubuntu kernel version 2.6.38 but over time I upgraded to version 3.0.27. Hardware information Here is some of the information I fetched on my AC100 before going into reflashing it with a different OS The original partition layout These values are relative to my model (10G), other models (even if with the same size EMMC) may have a different layout. -

Toshiba Ac100-Serien / Toshiba Ac100-10D
BÄRBARA DATORER / TOSHIBA / TOSHIBA AC100-SERIEN / TOSHIBA AC100-10D Toshiba AC100-10D Artikelnummer : PDN01E-00801EN5 Processor typ : NVIDIA® Tegra™ 250 Mobile Web-processor klockhastighet : 1.0 GHz Framsidesbuss (Front side bus) : 333 MHz 2:a nivåns cache (2nd level cache) : 1 MB Operativsystem Toshibas startmeny för Android™ 2.1 Designfärg färg : Svart med orangefärgade accenter, strukturmönster och ett svart tangentbord SSD-hårddisk kapacitet : 16 GB Systemminne standard : 512 MB (installerat) maximala expansionsmöjligheter : 512 MB teknik : DDR2 RAM (800 MHz) Skärm storlek : 25,7cm (10,1 tum) typ : Toshiba TruBrite® WSVGA TFT High Brightness-skärm med 16 : 9-format och LED-bakgrundsbelysning intern upplösning : 1 024 × 600 Grafikkort tillverkare : NVIDIA® typ : GeForce®-grafikprocessor med ultralåg strömförbrukning integrerad i NVIDIA® Tegra™ 250 Mobile Web-processorn minnestyp : delad Interna videolägen * INTERNAL_VIDEO_MODES_AVAILABLE * upplösning : 1,024 x 600 Gränssnitt 1 x extern mikrofon 1 x hörlurar (stereo) 1 x integrerad 1,3 megapixels webbkamera med inbyggd mikrofon 1 x HDMI med stöd för signalformatet 1080p 1 x Multikortläsare (med stöd för SD™-kort upp till 2 GB, miniSD™/microSD™-kort med adapter upp till 2 GB, SDHC™-kort upp till 32 GB samt MultiMedia Card™ upp till 2 GB) 1 (höger 1) x USB 2.0 1 (höger 1) x mini-USB Trådlös kommunikation Överensstämmelse : Wi-Fi® Nätverkssupport : 802.11b/g/n Trådlös teknik : Trådlöst LAN Trådlös teknik : Bluetooth® 2.1 + EDR Ljudsystem ljudformat som stöds : 24-bitars stereo högtalare : inbyggd stereohögtalare Tangentbord tangenter : 86 specialfunktioner : fullstort mattsvart tangentbord Pekdon typ : Touch Pad Batteri teknik : litiumjon maximal livslängd : det finns för närvarande inget officiellt benchmark-resultat för batteri Nätadapter inspänning : nätadapter (100/240 V) med automatisk spänningsväljare för global användning utspänning : 19 V utström : 1.58 A Fysiska mått B x D x H : 262,0 x 189,8 x 14,0 (fram) / 21,0 (bak) mm vikt : från 0,87 kg Garanti 2 års inlämningsgaranti. -

Computación a Bajo Coste. Procesamiento Con ARM
Computación a bajo coste. Procesamiento con ARM. V Jornadas de supercomputación y avances en tecnología Noviembre 2012 CollaboraCollabora de un vistazo ● Fundada en 2005 ● Especialistas en Open Source ● Clientes incluyen chip OEMs, vendedores de silicio y fabricantes de tecnologia de consumo ● 80+ ingenieros en Open Source en todo el mundo ● Oficinas centrales en Cambridge, UK ● Oficinas en Montreal, Canada. ● Sociedad de capital privado ¿Qué hace CollaboraCollabora? ● Consultoría que ayuda a maximizar beneficios del Open Source: ● Centrandose en las necesidades del cliente. ● Integrando cambios en la comunidad de Software Libre/Open Source. ● Reutilizando y mejorando las soluciones Open Source existentes. ● Creadores de proyectos: Gstreamer, Telepathy, ... ● Contribuciones: D-Bus, Webkit, Clutter, GTK, Qt, PulseAudio, Wayland, ... ¿Qué hace CollaboraCollabora? ● Experiencia en la pila del nucleo del kernel, ya sea Linux, Android u otros núcleos (también en tiempo real) ● Experiencia en gráficos: X.org, Wayland, aceleradores 3D, 2D, OpenGL(ES), OpenMAX y otros componentes de la interfaz gráfica. ● Experiencia en el sector de empotrados (embedded), para uso industrial, tanto como para terminales móviles. ARM ¿dónde? ARM ¿dónde? ● En vuestros bolsillos... ● terminales móviles ARM ¿dónde? ● En vuestros bolsillos... ● terminales móviles ● Equipos de red, equipos médicos, ¼ ARM ¿dónde? ● En vuestros bolsillos... ● terminales móviles ● Equipos de red, equipos médicos, … ● Smart Phone, Smart TV, In-Vehicle Infotainment, ... ARM ¿dónde? ● En vuestros bolsillos... ● terminales móviles ● Equipos de red, equipos médicos, … ● Smart Phone, Smart TV, In-Vehicle Infotainment, … ● Data centers (servidores de red) ARM Holdings Ltd. ● 1983: Acorn RISC Machine ● 1983-86: Furber & Wilson – ARM1 (ARM2) ● 1990: Advanced RISC Machine ● Acorn RISC Machine ● Apple Computer (hoy en día, Apple Inc.) ● VLSI Technologies ● Acorn Archimedes – Proyecto Apple Newton (PDA) '92 ● 1998: ARM Holdings Ltd. -

Toshiba AC100-117 User Guide Manual Operating Instructions
User’s Manual TOSHIBA AC100 Table of Contents Copyright. v Disclaimer . v Trademarks . v AVC/H.264 License Notice . vi FCC information . vi EU Declaration of Conformity . vii VCCI Class B Information . ix Canadian regulatory information (Canada only) . ix Following information is only valid for EU-member States:. ix Disposing of the TOSHIBA AC100 device and the batteries . x REACH - Compliance Statement . x Following information is only for Turkey: . xi Preface Conventions . xii General Precautions Provide adequate ventilation. xiv Creating a friendly environment . xv Stress injury . xv Heat injury . xv Pressure or impact damage. xvi Mobile phones . xvi Instruction Manual for Safety and Comfort . xvi Chapter 1 Getting Started & Grand Tour Equipment checklist. 1-1 Getting Started . 1-2 Grand Tour . 1-7 Chapter 2 Basic Operations & Home screen Using the Touch Pad . 2-1 Getting to know the TOSHIBA HOME Menu screen . 2-2 User’s Manual ii TOSHIBA AC100 Opening and switching applications . 2-4 Opening the Settings screen. 2-5 Working with menus. 2-5 Monitoring your device’s status . 2-6 Managing Notifications . 2-7 Locking your screen . 2-8 Customizing the Home screen . 2-8 Optimizing battery life . 2-10 Backup/restore settings and applications . 2-10 Factory Reset . 2-11 Chapter 3 Connecting to networks Connecting to mobile networks . 3-1 Connecting to Wi-Fi networks. 3-2 Connecting to Bluetooth devices . 3-4 Chapter 4 Applications & Widgets Alarm Clock. 4-1 Analog clock . 4-2 Browser . 4-2 Calculator . 4-5 Camera . 4-6 Contacts . 4-7 Documents To Go . 4-8 Email .