Sanrazor: Reducing Redundant Sanitizer Checks in C/C++ Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Red Hat Enterprise Linux 8 Installing, Managing, and Removing User-Space Components
Red Hat Enterprise Linux 8 Installing, managing, and removing user-space components An introduction to AppStream and BaseOS in Red Hat Enterprise Linux 8 Last Updated: 2021-06-25 Red Hat Enterprise Linux 8 Installing, managing, and removing user-space components An introduction to AppStream and BaseOS in Red Hat Enterprise Linux 8 Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -
List of Open Source Components Used by Intel® Deployment Assistant
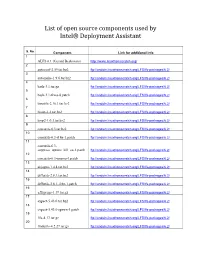
List of open source components used by Intel® Deployment Assistant S. No Component Link for additional info 1 ALFS 6.1 (Gerard Beekmans) http://www.linuxfromscratch.org/ 2 autoconf-2.59.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 3 automake-1.9.6.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 4 bash-3.1.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 5 bash-3.1-fixes-8.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 6 binutils-2.16.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 7 bison-2.2.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 8 bzip2-1.0.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 9 coreutils-6.3.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 10 coreutils-6.3-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 11 coreutils-6.3- suppress_uptime_kill_su-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 12 coreutils-6.3-uname-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 13 dejagnu-1.4.4.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 14 diffutils-2.8.1.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 15 diffutils-2.8.1-i18n-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 16 e2fsprogs-1.39.tar.gz ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 17 expect-5.43.0.tar.bz2 ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ 18 expect-5.43.0-spawn-1.patch ftp://anduin.linuxfromscratch.org/LFS/lfs-packages/6.2/ -

Lossless Compression of Internal Files in Parallel Reservoir Simulation
Lossless Compression of Internal Files in Parallel Reservoir Simulation Suha Kayum Marcin Rogowski Florian Mannuss 9/26/2019 Outline • I/O Challenges in Reservoir Simulation • Evaluation of Compression Algorithms on Reservoir Simulation Data • Real-world application - Constraints - Algorithm - Results • Conclusions 2 Challenge Reservoir simulation 1 3 Reservoir Simulation • Largest field in the world are represented as 50 million – 1 billion grid block models • Each runs takes hours on 500-5000 cores • Calibrating the model requires 100s of runs and sophisticated methods • “History matched” model is only a beginning 4 Files in Reservoir Simulation • Internal Files • Input / Output Files - Interact with pre- & post-processing tools Date Restart/Checkpoint Files 5 Reservoir Simulation in Saudi Aramco • 100’000+ simulations annually • The largest simulation of 10 billion cells • Currently multiple machines in TOP500 • Petabytes of storage required 600x • Resources are Finite • File Compression is one solution 50x 6 Compression algorithm evaluation 2 7 Compression ratio Tested a number of algorithms on a GRID restart file for two models 4 - Model A – 77.3 million active grid blocks 3.5 - Model K – 8.7 million active grid blocks 3 - 15.6 GB and 7.2 GB respectively 2.5 2 Compression ratio is between 1.5 1 compression ratio compression - From 2.27 for snappy (Model A) 0.5 0 - Up to 3.5 for bzip2 -9 (Model K) Model A Model K lz4 snappy gzip -1 gzip -9 bzip2 -1 bzip2 -9 8 Compression speed • LZ4 and Snappy significantly outperformed other algorithms -

The Ark Handbook
The Ark Handbook Matt Johnston Henrique Pinto Ragnar Thomsen The Ark Handbook 2 Contents 1 Introduction 5 2 Using Ark 6 2.1 Opening Archives . .6 2.1.1 Archive Operations . .6 2.1.2 Archive Comments . .6 2.2 Working with Files . .7 2.2.1 Editing Files . .7 2.3 Extracting Files . .7 2.3.1 The Extract dialog . .8 2.4 Creating Archives and Adding Files . .8 2.4.1 Compression . .9 2.4.2 Password Protection . .9 2.4.3 Multi-volume Archive . 10 3 Using Ark in the Filemanager 11 4 Advanced Batch Mode 12 5 Credits and License 13 Abstract Ark is an archive manager by KDE. The Ark Handbook Chapter 1 Introduction Ark is a program for viewing, extracting, creating and modifying archives. Ark can handle vari- ous archive formats such as tar, gzip, bzip2, zip, rar, 7zip, xz, rpm, cab, deb, xar and AppImage (support for certain archive formats depends on the appropriate command-line programs being installed). In order to successfully use Ark, you need KDE Frameworks 5. The library libarchive version 3.1 or above is needed to handle most archive types, including tar, compressed tar, rpm, deb and cab archives. To handle other file formats, you need the appropriate command line programs, such as zipinfo, zip, unzip, rar, unrar, 7z, lsar, unar and lrzip. 5 The Ark Handbook Chapter 2 Using Ark 2.1 Opening Archives To open an archive in Ark, choose Open... (Ctrl+O) from the Archive menu. You can also open archive files by dragging and dropping from Dolphin. -

Troubleshooting Guide
Java Platform, Standard Edition Troubleshooting Guide Release 9 E61074-05 October 2017 Java Platform, Standard Edition Troubleshooting Guide, Release 9 E61074-05 Copyright © 1995, 2017, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -

Bzip2 and Libbzip2, Version 1.0.8 a Program and Library for Data Compression
bzip2 and libbzip2, version 1.0.8 A program and library for data compression Julian Seward, https://sourceware.org/bzip2/ bzip2 and libbzip2, version 1.0.8: A program and library for data compression by Julian Seward Version 1.0.8 of 13 July 2019 Copyright© 1996-2019 Julian Seward This program, bzip2, the associated library libbzip2, and all documentation, are copyright © 1996-2019 Julian Seward. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met: • Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. • The origin of this software must not be misrepresented; you must not claim that you wrote the original software. If you use this software in a product, an acknowledgment in the product documentation would be appreciated but is not required. • Altered source versions must be plainly marked as such, and must not be misrepresented as being the original software. • The name of the author may not be used to endorse or promote products derived from this software without specific prior written permission. THIS SOFTWARE IS PROVIDED BY THE AUTHOR "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DIS- CLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. -

Working with Compressed Archives
Working with compressed archives Archiving a collection of files or folders means creating a single file that groups together those files and directories. Archiving does not manipulate the size of files. They are added to the archive as they are. Compressing a file means shrinking the size of the file. There are software for archiving only, other for compressing only and (as you would expect) other that have the ability to archive and compress. This document will show you how to use a windows application called 7-zip (seven zip) to work with compressed archives. 7-zip integrates in the context menu that pops-up up whenever you right-click your mouse on a selection1. In this how-to we will look in the application interface and how we manipulate archives, their compression and contents. 1. Click the 'start' button and type '7-zip' 2. When the search brings up '7-zip File Manager' (as the best match) press 'Enter' 3. The application will startup and you will be presented with the 7-zip manager interface 4. The program integrates both archiving, de/compression and file-management operations. a. The main area of the window provides a list of the files of the active directory. When not viewing the contents of an archive, the application acts like a file browser window. You can open folders to see their contents by just double-clicking on them b. Above the main area you have an address-like bar showing the name of the active directory (currently c:\ADG.Becom). You can use the 'back' icon on the far left to navigate back from where you are and go one directory up. -

Licensing Information User Manual Release 8.0 E65472-04
Oracle® Communications Calendar Server Licensing Information User Manual Release 8.0 E65472-04 March 2021 Copyright © 2000, 2021, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are “commercial computer software” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. Government. -

Gzip, Bzip2 and Tar EXPERT PACKING
LINUXUSER Command Line: gzip, bzip2, tar gzip, bzip2 and tar EXPERT PACKING A short command is all it takes to pack your data or extract it from an archive. BY HEIKE JURZIK rchiving provides many bene- fits: packed and compressed Afiles occupy less space on your disk and require less bandwidth on the Internet. Linux has both GUI-based pro- grams, such as File Roller or Ark, and www.sxc.hu command-line tools for creating and un- packing various archive types. This arti- cle examines some shell tools for ar- chiving files and demonstrates the kind of expert packing that clever combina- tained by the packing process. If you A gzip file can be unpacked using either tions of Linux commands offer the com- prefer to use a different extension, you gunzip or gzip -d. If the tool discovers a mand line user. can set the -S (suffix) flag to specify your file of the same name in the working di- own instead. For example, the command rectory, it prompts you to make sure that Nicely Packed with “gzip” you know you are overwriting this file: The gzip (GNU Zip) program is the de- gzip -S .z image.bmp fault packer on Linux. Gzip compresses $ gunzip screenie.jpg.gz simple files, but it does not create com- creates a compressed file titled image. gunzip: screenie.jpg U plete directory archives. In its simplest bmp.z. form, the gzip command looks like this: The size of the compressed file de- Listing 1: Compression pends on the distribution of identical Compared gzip file strings in the original file. -

Deduplicating Compressed Contents in Cloud Storage Environment
Deduplicating Compressed Contents in Cloud Storage Environment Zhichao Yan, Hong Jiang Yujuan Tan* Hao Luo University of Texas Arlington Chongqing University University of Nebraska Lincoln [email protected] [email protected] [email protected] [email protected] Corresponding Author Abstract Data compression and deduplication are two common approaches to increasing storage efficiency in the cloud environment. Both users and cloud service providers have economic incentives to compress their data before storing it in the cloud. However, our analysis indicates that compressed packages of different data and differ- ently compressed packages of the same data are usual- ly fundamentally different from one another even when they share a large amount of redundant data. Existing data deduplication systems cannot detect redundant data among them. We propose the X-Ray Dedup approach to extract from these packages the unique metadata, such as the “checksum” and “file length” information, and use it as the compressed file’s content signature to help detect and remove file level data redundancy. X-Ray Dedup is shown by our evaluations to be capable of breaking in the boundaries of compressed packages and significantly Figure 1: A user scenario on cloud storage environment reducing compressed packages’ size requirements, thus further optimizing storage space in the cloud. will generate different compressed data of the same con- tents that render fingerprint-based redundancy identifi- cation difficult. Third, very similar but different digital 1 Introduction contents (e.g., files or data streams), which would other- wise present excellent deduplication opportunities, will Due to the information explosion [1, 3], data reduc- become fundamentally distinct compressed packages af- tion technologies such as compression and deduplica- ter applying even the same compression algorithm. -

Zip Plugin 1.1 Read and Write Zip Archives with Hollywood
Zip Plugin 1.1 Read and write zip archives with Hollywood Andreas Falkenhahn i Table of Contents 1 General information::::::::::::::::::::::::::::: 1 1.1 Introduction :::::::::::::::::::::::::::::::::::::::::::::::::::: 1 1.2 Terms and conditions ::::::::::::::::::::::::::::::::::::::::::: 1 1.3 Requirements::::::::::::::::::::::::::::::::::::::::::::::::::: 2 1.4 Installation ::::::::::::::::::::::::::::::::::::::::::::::::::::: 2 2 About zip.hwp ::::::::::::::::::::::::::::::::::: 3 2.1 Credits ::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 3 2.2 Frequently asked questions:::::::::::::::::::::::::::::::::::::: 3 2.3 Known issues ::::::::::::::::::::::::::::::::::::::::::::::::::: 3 2.4 Future:::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 3 2.5 History ::::::::::::::::::::::::::::::::::::::::::::::::::::::::: 3 3 Usage ::::::::::::::::::::::::::::::::::::::::::::: 5 3.1 Activating the plugin ::::::::::::::::::::::::::::::::::::::::::: 5 3.2 Zip archives as directories::::::::::::::::::::::::::::::::::::::: 5 3.3 Extracting files ::::::::::::::::::::::::::::::::::::::::::::::::: 6 3.4 Zip archive basics::::::::::::::::::::::::::::::::::::::::::::::: 6 3.5 Creating zip archives ::::::::::::::::::::::::::::::::::::::::::: 7 3.6 Linking files :::::::::::::::::::::::::::::::::::::::::::::::::::: 7 4 Function reference::::::::::::::::::::::::::::::: 9 4.1 zip.AddDirectory ::::::::::::::::::::::::::::::::::::::::::::::: 9 4.2 zip.AddFile::::::::::::::::::::::::::::::::::::::::::::::::::::: 9 4.3 zip.CloseArchive::::::::::::::::::::::::::::::::::::::::::::::: -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae