Novell Appnotes March 2002
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
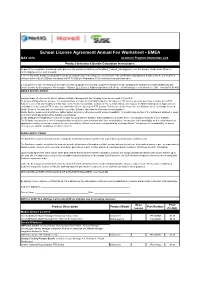
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -

Novell® On-Demand Training
Library of Courses Anywhere, anytime access Updated: April 11, 2011 to valuable training at an incredible price. Novell® On-demand Training * Underlined titles have web links * Red titles are free learning site courses End-User Client Library • SUSE Linux Enterprise Server 10 Fundamentals (3071) First Look: • SUSE Linux Enterprise Server 10 Administration (3072) • SUSE Linux Enterprise Server 10 Advanced • SUSE® Linux Enterprise Desktop 10 Administration (3073) End User: • SUSE Linux Enterprise Server – Networking Services • Novell GroupWise® Client (PDFs) (3074) • Novell Teaming +Conferencing Client • SUSE Linux Enterprise Server – Security (PDFs) (3075) • SUSE Linux Enterprise Desktop 11 Administration (3104) • SUSE Linux Enterprise Desktop 11 Help Desk Administration (8009) • SUSE Linux Enterprise 11 for Solaris Data Center Library: Administration (9061) First Look: • Red Hat 5 to SUSE Linux Enterprise Server 11 Migration Overview • SUSE Linux Enterprise Server 11 • Migrating Red Hat 5 to SUSE Linux Enterprise 11 (8011) • SUSE Linux Enterprise Server 10 • PlateSpin® Workload Management Administration (8008) • SUSE Linux Enterprise Desktop 11 • PlateSpin Forge 2.5 • PlateSpin Recon 3.6 • Business Service Management: Introduction • PlateSpin Recon 3.5 to ITIL (8408) • PlateSpin Migrate 8.1 • Migrating from UNIX to SUSE Linux Enterprise • PlateSpin Migrate 8.0 Server (9052) • Introduction to Novell Cloud Manager (1404) • PlateSpin Recon: Consolidation Assessments and Data Center Management (8415) Quick Fix: • PlateSpin Migrate 8.1: The -

School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link
School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to EMEA_Contract_Admin@Micro Focus.com (for Europe, Middle East, Africa) or contractadmin@Micro Focus.com (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.50 USD per enrollment or $38.00 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.50 plus 2 Additional products ($0.60 ea) = $3.70 total price x enrollment of 1,000 = Annual Fee $3,700. MOBILE DEVICE LICENSE: Upon purchase of a license for ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. -

Brainshare 2010
MessageSolution First in the Market to Offer All-in-One, Integrated Cloud-Based Archiving for Email, File Systems and SharePoint at Novell BrainShare 2010 Salt Lake City, Utah, and Silicon Valley, CA, March 22, 2010 -- MessageSolution, Inc., the global technology leader in email, file systems, and SharePoint on-premise and Software as a Service (SaaS) archiving for electronic discovery, litigation support, compliance, storage management, and email server migrations, announced today that MessageSolution is the first in the market to offer an all-in-one, integrated cloud-based enterprise information archiving (EIA) solution for email, file systems and SharePoint servers at Novell’s BrainShare 2010. As a leading innovator in the live archiving space, MessageSolution is the first on- premise and SaaS archiving provider in the market to archive and stub for all top-ranked email server platforms, including Exchange, Domino, GroupWise, file systems and SharePoint, delivering compliance archiving for all Unix/Linux-based email servers, and file servers for NTFS/NFS/NSS/Netware. MessageSolution Enterprise Migration System helps organizations to migrate between email servers, such as GroupWise or Domino to Exchange bi-directional, and SharePoint or BPOS migration from multiple source systems. MessageSolution is first in the market to perform simultaneous mail server migration, archiving and stubbing all in one streamlined process, to meet clients’ requirements of email server migration and archiving for compliance, server storage management, e-discovery and litigation support. “This offer of SaaS archiving for email, file systems, and SharePoint advances MessageSolution’s leading position in the global technology arena and successfully transforms our on-premise archiving product portfolio for the Software as a Service archiving space,” said Jeff Liang, CTO at MessageSolution, Inc. -

Relevé Des Frais Annuels De L'entente De Licence Destinée À
Relevé des frais annuels de l’entente de licence destinée à l’enseignement primaire et secondaire AOÛT 2016 Les Informations de Programme scolaire Relient DIRECTIVES SUR LA SÉLECTION DE PRODUIT ET LE CALCUL POUR LA SOLUTION GROUPÉE : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Sélectionnez l'une des solutions regroupées ou produits ci-dessous et cochez la case appropriée. Vous pouvez choisir toute combinaison de produits ou de solutions regroupées pour un prix minimal de 2,80 $ par inscription ou de 42 $ par poste de travail. 2. Calculez le prix total en fonction du prix total des produits choisis et calculez les frais annuels en multipliant le nombre d'inscriptions/postes de travail par le prix total. Par exemple : solution 1 au prix de 2,60 $ plus 2 produits additionnels (0,69 $ chaque) = un prix total de 3,98 $ x 1 000 inscriptions = frais annuels de 3 980 $. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). -

Syncsort Incorporated
Novell sagt YES! zu Syncsorts Backup Express Führendes Datensicherungsprodukt erhält Novells „YES! Zertifizierung“ für SUSE LINUX Enterprise Server 9 und Novell Linux Open Enterprise Server Ratingen/ Woodcliff Lake (New Jersey, USA), 03. April 2006 - Wie Syncsort Incorporated heute bekannt gab, hat sein Datensicherungsprodukt Backup Express die YES! Zertifizierung für Novell SUSE® LINUX Enterprise Server 9, Service Pack 1 und Open Enterprise Server (OES) Linux erlangt. Backup Express, das als erstes Programm Datensicherungen für OES- Clusterumgebungen ermöglichte, ist nach wie vor eine der zuverlässigsten Lösungen für Linux auf dem Datensicherungsmarkt. Novell-Kunden stellt Backup Express mehr Sicherungs- und Wiederherstellungsfunktionen für SLES und OES zur Verfügung als jeder andere Softwareanbieter. Backup Express umfasst Sicherungsfunktionen für NSS-Volumes (Novell Storage Services) und NSS-Metadaten in OES- und SLES9-Systemen und ermöglicht es Benutzern, von NetWare gesicherte Daten nach der Migration auf OES LINUX wiederherzustellen. Eine eindrucksvolle Demonstration dieser Funktionalität lieferte Syncsort auf der Novell BrainShare Conference, die im März in Salt Lake City stattfand. Die Tests zur YES!-Zertifizierung sollen Novell-Kunden helfen, unter Hardware- und Softwareprodukten von Drittanbietern diejenigen zu identifizieren, die nachweislich mit den Novell-Produktlinien einschließlich SUSE Linux Enterprise Server und NetWare® kompatibel sind. Die YES! Zertifizierung ist eine angesehene Novell Zertifizierung und gilt weltweit -

Eaton Rapids Public Schools an Unreliable Infrastructure Was Draining the Eaton Rapids Public Schools at a Glance: IT Resources at Eaton Rapids Public Schools
4681136.app 6/21/07 5:46 PM Page 1 Success Story Eaton Rapids Public Schools An unreliable infrastructure was draining the Eaton Rapids Public Schools at a glance: IT resources at Eaton Rapids Public Schools. School district in mid-central Michigan The district eliminated downtime by migrating to Industry: Novell® Open Enterprise Server on SUSE® Linux in Education a clustered environment. Standardizing desktops Location: United States with Novell ZENworks® also reduced desktop Solutions: maintenance time by 50 percent. Novell Open Enterprise Server SUSE Linux Enterprise Server ™ SM Novell Cluster Services Overview with Gracon, a Novell Platinum Partner , Novell Storage Manager Located in mid-central Michigan, Eaton and decided to migrate to Novell Open Novell ZENworks Rapids Public Schools has 3,300 students Enterprise Server on SUSE Linux in a Novell GroupWise and 250 staff. The district recently obtained clustered environment. Results: a $2 million construction bond for technol- – Reduced overall administration time ogy improvements. “We could not have afforded a clustered by 20 percent environment with any other solution” said – Reduced desktop maintenance time Challenge Lyne Roberts, director of Technology and and costs by 50 percent With an aging IT infrastructure, Eaton Rapids Media Services at Eaton Rapids Public – Reduced IT travel time by 75 percent Public Schools was experiencing regular Schools. “With Novell Open Enterprise Server – Created a stable IT infrastructure network downtime. A small IT staff was running on Linux, we have unprecedented despite a 10-percent budget cut rebooting its servers sometimes twice a stability. We hardly even need to go into and without additional IT resources week and facing downtime costs of several our server room anymore.” thousand dollars per incident. -

Relevé Des Frais Annuels De L'entente De Licence Destinée À L
Relevé des frais annuels de l’entente de licence destinée à l’enseignement primaire et secondaire MAI 2016 Les Informations de Programme scolaire Relient DIRECTIVES SUR LA SÉLECTION DE PRODUIT ET LE CALCUL POUR LA SOLUTION GROUPÉE : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Sélectionnez l'une des solutions regroupées ou produits ci-dessous et cochez la case appropriée. Vous pouvez choisir toute combinaison de produits ou de solutions regroupées pour un prix minimal de 2,80 $ par inscription ou de 42 $ par poste de travail. 2. Calculez le prix total en fonction du prix total des produits choisis et calculez les frais annuels en multipliant le nombre d'inscriptions/postes de travail par le prix total. Par exemple : solution 1 au prix de 2,60 $ plus 2 produits additionnels (0,69 $ chaque) = un prix total de 3,98 $ x 1 000 inscriptions = frais annuels de 3 980 $. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). -

Deer Valley Unified School District No
INVITATION FOR BID Material and/or Service: DV16-011 NOVELL SCHOOL LICENSE AGREEMENT Bid Due Date: June 14 ,2016 Time: 11:00 A.M District Contact: Gina Davis Contact Information: 623-445-5109, [email protected] Opening Location: Deer Valley Unified School District No. 97 Purchasing Services 21421 N. 21st Avenue Phoenix, AZ 85027 In accordance with School District Procurement Rules in the Arizona Administrative Code (A.A.C.) promulgated by the State Board of Education pursuant to A.R.S. 15-213, Bids for the material or services specified will be received by the DEER VALLEY UNIFIED SCHOOL DISTRICT NO. 97 at the above specified location until the time and date cited. Bids received by the correct time and date shall be opened and the names of vendors submitting shall be publicly read. All other information contained in the Bid shall remain confidential until award is made. If you need directions to our office, please call 623-445-5101. Bids shall be in the actual possession of the District at the location indicated on or prior to the exact time and date indicated above. Late Bids shall not be considered. Bids must be submitted in a sealed envelope using the District provided label and/or envelope with the solicitation number and Offeror’s name and address clearly indicated on the envelope. All Bids must be written legibly in ink or typewritten. Additional instructions for preparing a Bid are provided herein. When the document is downloaded from our Internet site, it is your responsibility to verify the issuance of an amendment prior to the solicitation date. -

Micro Focus 533370-4 Addn 34
Micro Focus 533370-4 Addn 34 Product Name Manufacturer Vendor Part No Description Unit of Measure State Price Access Management Products NetIQ 873-010505 NetIQ Access Manager 10-Instance License (external use only) EACH $ 423,150.00 Access Management Products NetIQ 873-010507 NetIQ Access Manager 1-Server License (requires prior purchase of 10-Instance - external EACHuse only) $ 48,825.00 Access Management Products NetIQ 873-010813 NetIQ Access Manager 1-User License EACH $ 8.46 Access Management Products NetIQ 873-010815 NetIQ Access Manager 1-User Government-to-Citizen/Business-to-Consumer License EACH $ 1.63 Access Management Products NetIQ 873-010816 NetIQ Access Manager 1-User Inactive License EACH $ 1.63 Access Management Products NetIQ 877-001854 NetIQ Access Manager 1-User 1-Year Renewal Priority Maintenance EACH $ 2.15 Access Management Products NetIQ 877-002900 NetIQ Access Manager 1-User GtoC/BtoC 1-Renewal Priority Maintenance EACH $ 0.40 Access Management Products NetIQ 877-006659 NetIQ Access Manager 1-User Inactive 1-Year Renewal Priority Maintenance EACH $ 0.40 Access Management Products NetIQ 877-007447 NetIQ Access Manager 10-Instance 1-Year Renewal Priority Maintenance (external use only)EACH $ 106,113.00 Access Management Products NetIQ 877-007449 NetIQ Access Manager 1-Instance 1-Year Renewal Priority Maintenance (requires prior purchaseEACH of 10-Instance - external$ use 12,238.80only) Access Management Products NetIQ 874-007113 NetIQ Access Manager 1-User 1-Year Renewal Priority Subscription EACH $ 4.30 Access Management -
NYS Pricelist SEP2013
New York State Price List September 2013 Product Description Part Number Feb 2008 Introductory Introductory Current New York State MSRP MSRP Date MSRP Discount Price NetIQ Access Manager 10‐Instance License (external use only) 873‐010505 N/A $650,000.00 12/30/2010 $650,000.00 $325,000.00 NetIQ Access Manager 1 Server License (requires prior 873‐010507 N/A $75,000.00 12/30/2010 $75,000.00 $37,500.00 NetIQ Access Manager 3.2 1‐User License 873‐010813 N/A $13.00 1/1/2013 $13.00 $6.50 NetIQ Access Manager 3.2 1‐User Government‐to‐ Citizen/Business‐to‐Consumer License 873‐010815 N/A $2.50 1/1/2013 $2.50 $1.25 NetIQ Access Manager 3.2 1‐User Inactive License 873‐010816 N/A $2.50 1/1/2013 $2.50 $1.25 Upgrade NetIQ Access Manager 10‐Instance License (external use only) 873‐010506 N/A $345,000.00 12/30/2010 $345,000.00 $172,500.00 Upgrade NetIQ Access Manager 1 Server License (requires prior purchase of 10‐Instance ‐ external use only) 873‐010508 N/A $39,800.00 12/30/2010 $39,800.00 $19,900.00 Upgrade NetIQ Access Manager 3.2 1‐User License 873‐010814 N/A $6.90 1/1/2013 $6.90 $3.45 NetIQ Access Manager 3.2 1‐User License + 1‐Year Priority Maintenance 877‐007833 N/A $17.00 1/1/2013 $17.00 $8.50 NetIQ Access Manager 3.2 1‐User Government‐to‐ Citizen/Business‐to‐Consumer License + 1‐Year Priority Maintenance 877‐007837 N/A $3.20 1/1/2013 $3.20 $1.60 NetIQ Access Manager 3.2 1‐User Inactive License + 1‐Year Priority Maintenance 877‐007839 N/A $3.20 1/1/2013 $3.20 $1.60 NetIQ Access Manager 10‐Instance License + 1 Year Priority Maintenance (external -

Curriculum Vitae
Curriculum Vitae DR. DAVID A. WILEY, II 204 Highlands Rd Online contact: Hurricane, WV [email protected] 25526-8402 http://davidwiley.org/ +1-801-822-9211 @opencontent TABLE OF CONTENTS Education 3 Experience 4 Publications 8 Peer-Reviewed Articles Published With Student Co-Authors 8 Other Peer-Reviewed Articles 12 Book Chapters 14 Books 16 Editing 17 Other Articles 17 Awarded Grants, Contracts, and Gifts 21 International Presentations 27 National Presentations 32 Consulting and Other Contract Work 48 Press and Media Coverage 50 Honors and Awards 51 Policy 52 Classes Taught 53 Service 55 Service Related to the Dissemination of Research 55 Service within the University 55 Additional Professional Service 56 Other Service 57 Current and Past Professional Affiliations 60 2 EDUCATION Post-doctoral Fellow, Instructional Technology, 2000-2001 Utah State University, Logan, Utah Co-wrote and obtained funding from the National Science Foundation for the grant The Instructional Architect: A System for Discovering, Recommending, and Using Learning Objects PhD, Instructional Psychology and Technology, 2000 Brigham Young University, Provo, Utah Dissertation Title: Learning Object Design and Sequencing Theory B.F.A., Music, 1997 Marshall University, Huntington, West Virginia Vocal performance major with piano minor and emphasis in choral conducting. Senior recital: Die Schöne Mullerin, a cycle of 20 songs with poetry by Wilhelm Muller and music by Franz Schubert. Pre-college Program, Music, 1989 Carnegie Mellon University, Pittsburgh, PA Studied