Game Consoles - Are They Secure?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Computer Game Mods, Modders, Modding, and the Mod Scene
Computer Game Mods, Modders, Modding, and the Mod Scene Walt Scacchi Institute for Software Research and Center for Computer Games and Virtual Worlds University of California, Irvine 92697-3455 USA March 2010 Abstract Computer games have increasingly been the focus of user-led innovations in the form of game mods. This paper examines how different kinds of socio-technical affordances serve to organize the actions of the people who develop and share their game mods. The affordances examined include customization and tailoring mechanisms, software and content copyright licenses, game software infrastructure and development tools, career contingencies and organizational practices of mod teams, and social worlds intersecting the mod scene. Numerous examples will be used to ground this review and highlight how such affordances can organize, facilitate or constrain what can be done. Overall, this study helps to provide a deeper understanding of how a web of associated affordances collectively serve to govern what mods get made, how modding practices emerge and flourish, and how modders and the game industry serve each others' interests, though not always in equivocal terms. Introduction Computer game mods are a leading form of user-led innovation in game design and game play experience. But modded games are not standalone systems, as they require the user to have an originally acquired or authorized copy of the unmodded game. Thus, there are questions of not only who creates what and who owns such modified games, but also whether or how the practice of game modding is controlled or governed by external parties to ultimately exploit the efforts of game modders. -

Nvidia Equity Report
APRIL 2020 NVIDIA EQUITY REPORT By Sanjay Gospodinov Col'23 EQUITY REPORT // APRIL 2020 0 2 NVIDIA REVENUE STREAM NVidia Corp is a technology company based in Santa Clara, Ca with operations worldwide. It is primarily a graphics processing chip manufacturer that makes most of its revenue from the sales of graphics processing units (GPUs), which are used for gaming, professional visualization, and cryptocurrency mining. The Nvidia graphics card, Geforce, is a particularly popular gaming graphics card and as of right now, Nvidia controls 18% of the overall graphics card market and 73% of the discrete GPU market (where the GPU and CPU are separate). Nvidia also produces Quadro, a GPU aimed at professional graphics content designers. They additionally make Tesla (no relation to the car maker), which is a GPU accelerator that runs simulations, deep learning algorithms, and is primarily marketed towards AI data scientists and big data research. Lastly, this segment of NVidia also makes GRID, a product designed for cloud-based streaming. This reportable segment, which almost entirely sells GPUs, makes up 86.7% of Nvidia's revenue. TEGRA SEGMENT AND OPPORTUNITY FOR GROWTH The other reportable segment of Nvidia is Tegra, which combines a GPU and CPU onto one chip. This product is made to support online gaming, entertainment devices, drones, and self-driving cars. This segment of Nvidia's business is relatively new and only produced about 13% of the company's revenue in 2019. However, the opportunity for growth is tremendous here as, in early 2015, Nvidia partnered with Uber to expand in the self-driving car sector. -

UPC Platform Publisher Title Price Available 730865001347
UPC Platform Publisher Title Price Available 730865001347 PlayStation 3 Atlus 3D Dot Game Heroes PS3 $16.00 52 722674110402 PlayStation 3 Namco Bandai Ace Combat: Assault Horizon PS3 $21.00 2 Other 853490002678 PlayStation 3 Air Conflicts: Secret Wars PS3 $14.00 37 Publishers 014633098587 PlayStation 3 Electronic Arts Alice: Madness Returns PS3 $16.50 60 Aliens Colonial Marines 010086690682 PlayStation 3 Sega $47.50 100+ (Portuguese) PS3 Aliens Colonial Marines (Spanish) 010086690675 PlayStation 3 Sega $47.50 100+ PS3 Aliens Colonial Marines Collector's 010086690637 PlayStation 3 Sega $76.00 9 Edition PS3 010086690170 PlayStation 3 Sega Aliens Colonial Marines PS3 $50.00 92 010086690194 PlayStation 3 Sega Alpha Protocol PS3 $14.00 14 047875843479 PlayStation 3 Activision Amazing Spider-Man PS3 $39.00 100+ 010086690545 PlayStation 3 Sega Anarchy Reigns PS3 $24.00 100+ 722674110525 PlayStation 3 Namco Bandai Armored Core V PS3 $23.00 100+ 014633157147 PlayStation 3 Electronic Arts Army of Two: The 40th Day PS3 $16.00 61 008888345343 PlayStation 3 Ubisoft Assassin's Creed II PS3 $15.00 100+ Assassin's Creed III Limited Edition 008888397717 PlayStation 3 Ubisoft $116.00 4 PS3 008888347231 PlayStation 3 Ubisoft Assassin's Creed III PS3 $47.50 100+ 008888343394 PlayStation 3 Ubisoft Assassin's Creed PS3 $14.00 100+ 008888346258 PlayStation 3 Ubisoft Assassin's Creed: Brotherhood PS3 $16.00 100+ 008888356844 PlayStation 3 Ubisoft Assassin's Creed: Revelations PS3 $22.50 100+ 013388340446 PlayStation 3 Capcom Asura's Wrath PS3 $16.00 55 008888345435 -

Videogames at the Library: Ahistoricalperspective
VideoGames at the Library: AHistoricalPerspective Gustavo Marfia∗,AlessandroAmoroso∗,MarcoRoccetti∗,GiulioBasile∗,ClaudioE.Palazzi† ∗ Dipartimento di Scienze dell’Informazione - Universit`adiBologna,Italia Email: {amoroso, marfia, roccetti}@cs.unibo.it † Dipartimento di Matematica Pura e Applicata - Universit`adegli Studi di Padova, Italia Email: [email protected] Abstract —We present an overview or the video games available at the Film Library of Bologna. This institution, in collaboration with the University of Bologna, has a whole collateral branch dedicated to the video games, as they can be considered a recreational activity somehow related to movies. This collection of video games conceptually starts from the ones that are strictly connected to movies, and then expands to a wider class of video games. A video game could be related with a movie either as its direct inspiration, its prequel or collateral plot, or also be created as a direct consequence of that movie. The expansion of the collection available in the Library includes a historical set of video games. In this paper we discuss the historical perspective of the relationship between technology and video games, providinga complete historical view of the video games by means of the titles and the consoles available in the Library. Several dedicated consoles are still in working conditions and could be used by the visitors of the Library. I. INTRODUCTION The collection of the Play Room of the Film Library of Bologna contains about 2000 video games, whose releases Fig. 1. Temporal distribution of games available at the Library with respect to the hardware platforms range from 1979, till the present date. -

Bullet Physics and the Blender Game Engine
92801c06.qxd 5/14/08 1:54 PM Page 271 Bullet Physics and the Blender Game Engine Blender is a unique 3D animation suite in that it contains a full-featured game engine for the creation of games and other free-standing inter- active content. Nevertheless, in spite of its core of devoted fans, the game engine is an all-too- often overlooked feature of Blender. 271 I B In this chapter, you’ll learn the basics of work- ULLET ing with BGE and Bullet Physics to the point P HYSICSANDTHE that you can easily create dynamic rigid body animations, which can then be used in the Blender animation environment you’re accus- B LENDER tomed to. If you are new to BGE, you will be G surprised by how much amazing functionality it AME will open up for you. If not, this chapter should E NGINE provide some interesting ideas for how to inte- grate real-time generated physics simulations with rendered animations. Chapter Contents 6 The Blender Game Engine Rigid body simulation and Ipos Constraints,ragdolls,and robots 92801c06.qxd 5/14/08 1:54 PM Page 272 The Blender Game Engine It goes without saying that for people who are mainly interested in creating games, the game engine is one of Blender’s major attractions. The BGE is widely used by hobbyist game creators, and lately its appeal has begun to broaden to larger game projects. Luma Studios used BGE to create their prototype racing game ClubSilo, shown in Figure 6.1. The Blender Institute, the creative production extension of the Blender Foundation, is currently planning “Project Apricot,” which will use BGE in conjunction with the Crystal Space game development kit and other open source tools in producing an open game of professional quality to be released under the Creative Commons license. -

Module: Introduction
CDP 2015 Climate Change 2015 Information Request CDP NVIDIA Corporation Module: Introduction Page: Introduction CC0.1 Introduction Please give a general description and introduction to your organization. NVIDIA is the world leader in visual computing. The GPU, which we invented in 1999, serves as the visual cortex of modern computers and is at the heart of our products and services. Our work opens up new universes to explore, enables amazing creativity and discovery, and powers what were once science fiction inventions like self-learning machines and self-driving cars. NVIDIA focuses on serving large markets where visual computing is essential. For each, we offer a platform of processors, software, systems and services. We innovate across PC, data center and mobile technologies. And our inventions power the products of OEMs across industries. GeForce GTX, our GPU brand for PC gamers, is the world’s largest gaming platform, with 200 million users. In conjunction with GeForce Experience, an application that configures games to run optimally and tunes a PC’s performance continually, GeForce GPUs transform everyday PCs into powerful gaming machines. SHIELD, NVIDIA’s first living-room entertainment device, will change the way people enjoy entertainment at home. The world’s first 4K Android TV, it delivers video, music, apps and amazing games. With the ability to easily connect to a store full of apps, SHIELD will do for smart TVs what smartphones did for cell phones. The SHIELD tablet and SHIELD portable round out our family of mobile devices. The NVIDIA GRID game-streaming service, dubbed “a Netflix of games,” allows gamers to connect their SHIELD devices to a GeForce supercomputer in the cloud. -

A Game Engine for the Blind
Bachelor in Computer Science and Engineering 2016/2017 Bachelor Thesis Designing User Experiences: a Game Engine for the Blind Álvaro Cáceres Muñoz Tutor/s: Teresa Onorati Thesis defense date: July 3rd, 2017 This work is subject to the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License. Abstract Video games experience an ever-increasing interest by society since their incep- tion on the 70’s. This form of computer entertainment may let the player have a great time with family and friends, or it may as well provide immersion into a story full of details and emotional content. Prior to the end user playing a video game, a huge effort is performed in lots of disciplines: screenwriting, scenery design, graphical design, programming, opti- mization or marketing are but a few examples. This work is done by game studios, where teams of professionals from different backgrounds join forces in the inception of the video game. From the perspective of Human-Computer Interaction, which studies how people interact with computers to complete tasks [9], a game developer can be regarded as a user whose task is to create the logic of a video game using a computer. One of the main foundations of HCI1. is that an in-depth understanding of the user’s needs and preferences is vital for creating a usable piece of technology. This point is important as a single piece of technology (in this case, the set of tools used by a game developer) may – and should have been designed to – be used on the same team by users with different knowledge, abilities and capabilities. -

Investor Presentation Q3 Fy2021
INVESTOR PRESENTATION Q3 FY2021 November 23, 2020 Except for the historical information contained herein, certain matters in this presentation including, but not limited to, statements as to: our financial position; our markets; the performance, benefits, abilities and impact of our products and technology; the availability of our products and technology; our partnerships and customers; our use of cash; the acquisition of Arm and its impacts; NVIDIA’s financial outlook for the fourth quarter of fiscal 2021; our growth and growth drivers; our financial policy; future revenue growth; our opportunities in existing and new markets; the TAM for our products; and performance in our financial metrics are forward-looking statements within the meaning of the Private Securities Litigation Reform Act of 1995. These forward-looking statements and any other forward-looking statements that go beyond historical facts that are made in this presentation are subject to risks and uncertainties that may cause actual results to differ materially. Important factors that could cause actual results to differ materially include: global economic conditions; our reliance on third parties to manufacture, assemble, package and test our products; the impact of technological development and competition; development of new products and technologies or enhancements to our existing product and technologies; market acceptance of our products or our partners' products; design, manufacturing or software defects; changes in consumer preferences and demands; changes in industry standards and interfaces; unexpected loss of performance of our products or technologies when integrated into systems and other factors. NVIDIA has based these forward-looking statements largely on its current expectations and projections about future events and trends that it believes may affect its financial condition, results of operations, business strategy, short-term and long-term business operations and objectives, and financial needs. -
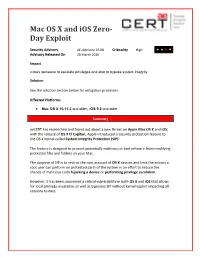
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -

NVIDIA Geforce RTX 2080 User Guide | 3 Introduction
2080 TABLE OF CONTENTS 01 INTRODUCTION ..................................................................................... 3 About This Guide ................................................................................................................................ 3 Minimum System Requirements ....................................................................................................... 4 02 UNPACKING .......................................................................................... 5 Equipment .......................................................................................................................................... 6 03 Hardware Installation ............................................................................. 7 Safety Instructions ............................................................................................................................. 7 Before You Begin ................................................................................................................................ 8 Installing the GeForce Graphics Card ............................................................................................... 8 04 SOFTWARE INSTALLATION ................................................................... 12 GeForce Experience Software Installation ...................................................................................... 12 05 CONFIGURING NVLink ......................................................................... 14 06 CONFIGURING HDMI ........................................................................... -
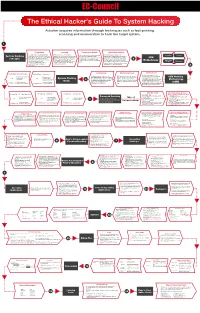
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Creating Video Games for the Visually Impaired Anthony Russo, Neal
Creating Video Games for the Visually Impaired Anthony Russo, Neal Sacks, & Steven Vandal WPI IQP MBJ 0007 Professor Brian Moriarty April 12, 2012 Introduction The video game industry has expanded rapidly in recent years, growing from a 9.5 billion dollar industry in 2007 to a 25.1 billion dollar industry in 2010. This growth is due to the common interest that almost all Americans now hold in games, as a seventy-two percent of all americans play video games on a regular basis (ESA). However, because games rely heavily on impressive graphics and are primarily an immersive visual experience, very few games are made with the blind or the visually impaired in mind. In the 1970s when video games first emerged, it was virtually impossible to create a game that did not involve some sort of visuals. This is mainly due to a lack of technology, as almost all computers, games, and electronic speakers and displays could only output crude, pixilated visuals and rough, synthesized sound. However, technology has steadily improved to the point where games that do not need visuals are a possibility. Games for the visually impaired are an untapped industry, especially with the technology that exists today. By conducting interviews with the visually impaired we discovered what types of games the visual impaired prefer, what they would enjoy to play, and what ideas they have for developing these games. The History of Video Games for the Visually Impaired There are many games that can be played by the visually impaired. Interactive fiction and other text-based games have been popular for a long time, though to a lesser extent in recent years.