Quicktime File Format.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mac OS 8 Update
K Service Source Mac OS 8 Update Known problems, Internet Access, and Installation Mac OS 8 Update Document Contents - 1 Document Contents • Introduction • About Mac OS 8 • About Internet Access What To Do First Additional Software Auto-Dial and Auto-Disconnect Settings TCP/IP Connection Options and Internet Access Length of Configuration Names Modem Scripts & Password Length Proxies and Other Internet Config Settings Web Browser Issues Troubleshooting • About Mac OS Runtime for Java Version 1.0.2 • About Mac OS Personal Web Sharing • Installing Mac OS 8 • Upgrading Workgroup Server 9650 & 7350 Software Mac OS 8 Update Introduction - 2 Introduction Mac OS 8 is the most significant update to the Macintosh operating system since 1984. The updated system gives users PowerPC-native multitasking, an efficient desktop with new pop-up windows and spring-loaded folders, and a fully integrated suite of Internet services. This document provides information about Mac OS 8 that supplements the information in the Mac OS installation manual. For a detailed description of Mac OS 8, useful tips for using the system, troubleshooting, late-breaking news, and links for online technical support, visit the Mac OS Info Center at http://ip.apple.com/infocenter. Or browse the Mac OS 8 topic in the Apple Technical Library at http:// tilsp1.info.apple.com. Mac OS 8 Update About Mac OS 8 - 3 About Mac OS 8 Read this section for information about known problems with the Mac OS 8 update and possible solutions. Known Problems and Compatibility Issues Apple Language Kits and Mac OS 8 Apple's Language Kits require an updater for full functionality with this version of the Mac OS. -

XMP SPECIFICATION PART 3 STORAGE in FILES Copyright © 2016 Adobe Systems Incorporated
XMP SPECIFICATION PART 3 STORAGE IN FILES Copyright © 2016 Adobe Systems Incorporated. All rights reserved. Adobe XMP Specification Part 3: Storage in Files NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. Adobe, the Adobe logo, Acrobat, Acrobat Distiller, Flash, FrameMaker, InDesign, Illustrator, Photoshop, PostScript, and the XMP logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. MS-DOS, Windows, and Windows NT are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Apple, Macintosh, Mac OS and QuickTime are trademarks of Apple Computer, Inc., registered in the United States and other countries. UNIX is a trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. All other trademarks are the property of their respective owners. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and noninfringement of third party rights. Contents 1 Embedding XMP metadata in application files . -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

(A/V Codecs) REDCODE RAW (.R3D) ARRIRAW
What is a Codec? Codec is a portmanteau of either "Compressor-Decompressor" or "Coder-Decoder," which describes a device or program capable of performing transformations on a data stream or signal. Codecs encode a stream or signal for transmission, storage or encryption and decode it for viewing or editing. Codecs are often used in videoconferencing and streaming media solutions. A video codec converts analog video signals from a video camera into digital signals for transmission. It then converts the digital signals back to analog for display. An audio codec converts analog audio signals from a microphone into digital signals for transmission. It then converts the digital signals back to analog for playing. The raw encoded form of audio and video data is often called essence, to distinguish it from the metadata information that together make up the information content of the stream and any "wrapper" data that is then added to aid access to or improve the robustness of the stream. Most codecs are lossy, in order to get a reasonably small file size. There are lossless codecs as well, but for most purposes the almost imperceptible increase in quality is not worth the considerable increase in data size. The main exception is if the data will undergo more processing in the future, in which case the repeated lossy encoding would damage the eventual quality too much. Many multimedia data streams need to contain both audio and video data, and often some form of metadata that permits synchronization of the audio and video. Each of these three streams may be handled by different programs, processes, or hardware; but for the multimedia data stream to be useful in stored or transmitted form, they must be encapsulated together in a container format. -
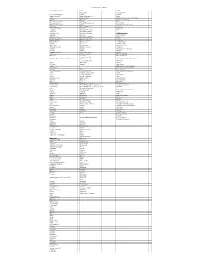
Software List (1-3-2017)
Software List (1-3-2017) Information Commons BU 104 LLCD Adobe Flash Academic online JVC Pro HD Manager Chrome Acrobat Adobe Reader DC Adobe Photoshop CS6 Adobe Itunes Adobe Reader XI Comprehensive Medical Terminology Maple 16 Drive M:\ Glencoe Keyboarding Microsoft Office 2016 Firefox Itunes Microsoft Publisher Irwin/GDP Keyboarding Kurzeil 3000 MS visual studio 2015 Itunes Microsoft Office Suite 2007 Quicktime Kurzweil 3000 v.12 Quick time SPSS for Windows Maple 16 Skills bank real player Microsoft Office 2016 Vista 3-Scanners MS platform installer Windows 7 & 10 Microsoft Visio 2016 Wellington Center sharepoint MS SQL Internet Explorer XPS viewer MS Visual Studio 2015 ITunes Express for desktop Quicken deluxe 2014 McAfee Express for Web VLC Media Player Quicktime MS silverlight Windows 10 " " Media Player Statdisk Scanner Mozilla Firefox Skype 2016 MS silverlight Adobe Reader XI windows dvd maker wolfram cdf player Windows 8 Onedrive Filezilla Microsoft Office Suite 2013 notepad++ Gimp 2 Maple 16 respounds/lockdown opera mobile emulator Statdisk 3D builder VM ware/ vsphere Wolfram CDF Player MS Azure wire shark VLC Media Player cisco packet tracker MACS Software (Information Commons) 3D builder Brunswick Front Desk Computers java development kit Windows 7 System project 2016 Adobe 9 Developer notepad++ Apple Itunes Utilities IBM Iseries access for windows Time Machine Intel Management and Security TextEdit UC 222 Iseries navigator System Preferences Acrobat Reader XI Malware Bytes Anti Malware Stickies Adult Clinical Simulation Mcaffe -

Develop-19 9408 September 1994.Pdf
develop E D I T O R I A L S T A F F T H I N G S T O K N O W C O N T A C T I N G U S Editor-in-Cheek Caroline Rose develop, The Apple Technical Feedback. Send editorial suggestions Managing Editor Cynthia Jasper Journal, a quarterly publication of or comments to Caroline Rose at Technical Buckstopper Dave Johnson Apple Computer’s Developer Press AppleLink CROSE, Internet Bookmark CD Leader Alex Dosher group, is published in March, June, [email protected], or fax September, and December. develop (408)974-6395. Send technical Our Boss Greg Joswiak articles and code have been reviewed questions about develop to Dave His Boss Dennis Matthews for robustness by Apple engineers. Johnson at AppleLink JOHNSON.DK, Review Board Pete (“Luke”) Alexander, Dave Internet [email protected], CompuServe Radcliffe, Jim Reekes, Bryan K. (“Beaker”) This issue’s CD. Subscription issues 75300,715, or fax (408)974-6395. Or Ressler, Larry Rosenstein, Andy Shebanow, of develop are accompanied by the write to Caroline or Dave at Apple Gregg Williams develop Bookmark CD. The Bookmark Computer, Inc., One Infinite Loop, Contributing Editors Lorraine Anderson, CD contains a subset of the materials M/S 303-4DP, Cupertino, CA 95014. Steve Chernicoff, Toni Haskell, Judy on the monthly Developer CD Series, Helfand, Jody Larson, Joe Williams which is available from APDA. Article submissions. Ask for our Indexer Marc Savage Included on the CD are this issue and Author’s Guidelines and a submission all back issues of develop along with the form at AppleLink DEVELOP, A R T & P R O D U C T I O N code that the articles describe. -

Mac OS for Quicktime Programmers
Mac OS For QuickTime Programmers Apple Computer, Inc. Technical Publications April, 1998 Apple Computer, Inc. Apple, the Apple logo, Mac, LIMITED WARRANTY ON MEDIA © 1998 Apple Computer, Inc. Macintosh, QuickDraw, and AND REPLACEMENT All rights reserved. QuickTime are trademarks of Apple ALL IMPLIED WARRANTIES ON THIS No part of this publication or the Computer, Inc., registered in the MANUAL, INCLUDING IMPLIED software described in it may be United States and other countries. WARRANTIES OF reproduced, stored in a retrieval The QuickTime logo is a trademark MERCHANTABILITY AND FITNESS system, or transmitted, in any form of Apple Computer, Inc. FOR A PARTICULAR PURPOSE, ARE or by any means, mechanical, Adobe, Acrobat, Photoshop, and LIMITED IN DURATION TO NINETY electronic, photocopying, recording, PostScript are trademarks of Adobe (90) DAYS FROM THE DATE OF or otherwise, without prior written Systems Incorporated or its DISTRIBUTION OF THIS PRODUCT. permission of Apple Computer, Inc., subsidiaries and may be registered in Even though Apple has reviewed this except in the normal use of the certain jurisdictions. manual, APPLE MAKES NO software or to make a backup copy Helvetica and Palatino are registered WARRANTY OR REPRESENTATION, of the software or documentation. trademarks of Linotype-Hell AG EITHER EXPRESS OR IMPLIED, WITH The same proprietary and copyright and/or its subsidiaries. RESPECT TO THIS MANUAL, ITS notices must be affixed to any ITC Zapf Dingbats is a registered QUALITY, ACCURACY, permitted copies as were affixed to trademark of International Typeface MERCHANTABILITY, OR FITNESS the original. This exception does not Corporation. FOR A PARTICULAR PURPOSE. AS A allow copies to be made for others, RESULT, THIS MANUAL IS Simultaneously published in the whether or not sold, but all of the DISTRIBUTED “AS IS,” AND YOU United States and Canada. -

Getting Started a Guide for Your Apple Mobile Learning Lab Contents
Getting Started A guide for your Apple Mobile Learning Lab Contents Introduction 1 Setting Up and Working with Your Mobile Lab 3 Setting Up Your Mobile Lab 3 Daily Setup 6 Sharing the Mobile Lab 9 Creating and Managing User Accounts 9 Installing Software 11 Sharing and Storing Files 14 Apple Remote Desktop: Managing Student Computers from One Computer 15 Using Parental Controls to Provide Extra Security 16 Maintaining Your Mobile Lab 17 Using the Tools That Come with Your Mobile Lab 20 Using iChat AV to Communicate and Collaborate with Video, Audio, and Text 20 Having Instant Access to Information with Widgets 22 Finding Files in a Flash with Spotlight 23 Crunching Numbers with Calculator and Grapher 24 Browsing the Internet with Safari 25 Staying Up to Date with iCal 27 Producing Digital Media Projects with iLife 28 Creating Digital Stories with iMovie 29 Creating Digital Music and Recording Audio with GarageBand 30 Organizing, Editing, and Sharing Digital Photos with iPhoto 32 Building Websites with Photos, Movies, Podcasts, and Text with iWeb 34 Organizing and Playing Music and Audio with iTunes 36 Reaching All Learners with Built-in Accessibility Features 37 Communicating via Email with Mail 38 Supporting Writing with Dictionary and TextEdit 39 Getting Started: A guide for your Apple Mobile Learning Lab II Contents More Tools to Use with Your Mobile Lab 40 Increasing Student Achievement with the Apple Digital Learning Series 40 Using the iPod as a Portable Learning Tool 44 Creating, Presenting, and Publishing Work with iWork 45 Additional Resources 47 Apple Learning Interchange 47 Apple Education 47 Apple Professional Development 48 Apple Support 48 Mobile Lab Teacher Sign-Up Sheet 49 Mobile Lab Student Checkout Sheet 50 Mobile Lab Teacher Checkout Sheet 51 © 2007 Apple Inc. -

Codec Is a Portmanteau of Either
What is a Codec? Codec is a portmanteau of either "Compressor-Decompressor" or "Coder-Decoder," which describes a device or program capable of performing transformations on a data stream or signal. Codecs encode a stream or signal for transmission, storage or encryption and decode it for viewing or editing. Codecs are often used in videoconferencing and streaming media solutions. A video codec converts analog video signals from a video camera into digital signals for transmission. It then converts the digital signals back to analog for display. An audio codec converts analog audio signals from a microphone into digital signals for transmission. It then converts the digital signals back to analog for playing. The raw encoded form of audio and video data is often called essence, to distinguish it from the metadata information that together make up the information content of the stream and any "wrapper" data that is then added to aid access to or improve the robustness of the stream. Most codecs are lossy, in order to get a reasonably small file size. There are lossless codecs as well, but for most purposes the almost imperceptible increase in quality is not worth the considerable increase in data size. The main exception is if the data will undergo more processing in the future, in which case the repeated lossy encoding would damage the eventual quality too much. Many multimedia data streams need to contain both audio and video data, and often some form of metadata that permits synchronization of the audio and video. Each of these three streams may be handled by different programs, processes, or hardware; but for the multimedia data stream to be useful in stored or transmitted form, they must be encapsulated together in a container format. -

A Comparison of Video Formats for Online Teaching Ross A
Contemporary Issues in Education Research – First Quarter 2017 Volume 10, Number 1 A Comparison Of Video Formats For Online Teaching Ross A. Malaga, Montclair State University, USA Nicole B. Koppel, Montclair State University, USA ABSTRACT The use of video to deliver content to students online has become increasingly popular. However, educators are often plagued with the question of which format to use to deliver asynchronous video material. Whether it is a College or University committing to a common video format or an individual instructor selecting the method that works best for his or her course, this research presents a comparison of various video formats that can be applied to online education and provides guidance in which one to select. Keywords: Online Teaching; Video Formats; Technology Acceptance Model INTRODUCTION istance learning is one of the most talked-about topics in higher education today. Online and hybrid (or blended) learning removes location and time-bound constraints of the traditional college classroom to a learning environment that can occur anytime or anywhere in a global environment. DAccording to research by the Online Learning Consortium, over 5 million students took an online course in the Fall 2014 semester. This represents an increase in online enrollment of over 3.9% in just one year. In 2014, 28% of higher education students took one or more courses online (Allen, I. E. and Seaman, J, 2016). With this incredible growth, albeit slower than the growth in previous years, institutions of higher education are continuing to increase their online course and program offerings. As such, institutions need to find easy to develop, easy to use, reliable, and reasonably priced technologies to deliver online content. -

Format Support
Episode 6 Format Support FILE FORMAT CODEC Episode Episode Episode Pro EngineCOMMENTS Adaptive bitrate streaming Microsoft Smooth Streaming H.264 (AAC audio) O Windows OS only. Available with Episode Engine License. Apple HLS H.264 (AAC audio) O Available with Episode Engine License. Windows Media WMV, ASF VC-1 O O O WM9 I/O I/O I/O WMV7 and 8 through F4M component on Mac WMA I/O I/O I/O WMA Pro I/O I/O I/O Flash FLV Flash 8 (VP6s/VP6e) I/O I/O I/O SWF Flash 8 (VP6s/VP6e) I/O I/O I/O MOV/MP4/F4V Flash 9 (H.264) I/O I/O I/O F4V as extension to MP4 WebM WebM VP8 O O O Vorbis O O O 3GPP 3GPP AAC I/O I/O I/O H.263 I/O I/O I/O H.264 I/O I/O I/O MainConcept and x264 MPEG-4 I/O I/O I/O 3GPP2 3GPP2 AAC I/O I/O I/O H.263 I/O I/O I/O H.264 I/O I/O I/O MainConcept and x264 MPEG-4 I/O I/O I/O MPEG Elementary Streams MPEG-1 Elementary Stream MPEG-1 (video) I/O I/O I/O MPEG-2 Elementary Stream MPEG-2 I/O I/O I/O MPEG Program Streams PS AAC O O O MainConcept and x264 H.264 I/O I/O I/O MPEG-1/2 (audio) I/O I/O I/O MPEG-2 I/O I/O I/O MPEG-4 I/O I/O I/O MPEG Transport Streams TS AAC I O O AES I I/O I/O H.264 I I/O I/O MainConcept and x264 AVCHD I I I HDV I I/O I/O MPEG - 1/2 (audio) I I/O I/O MPEG - 2 I I/O I/O MPEG - 4 I I/O I/O PCM I I I Matrox MAX H.264 I/O I/O I/O QT codec (*output possible via QT), Requires Matrox MAX hardware - Mac OS X only MPEG System Streams M1A MPEG-1 (audio) I/O I/O I/O M1V MPEG-1 (audio) I/O I/O I/O Episode 6 Format Support Format Support FILE FORMAT CODEC Episode Episode Episode Pro EngineCOMMENTS MPEG-4 MP4 AAC I/O I/O I/O -

Important for All Apple Printing and Graphics Developers: the Information in This Technote Is Still Relevant up to and Including
TN 1057 - Querying PS Printers at dtp Creation Time the GX Page: 1 Way NOTE: This Technical Note has been retired. Please see the Technical Notes page for current documentation. CONTENTS Important for all Apple Printing and Graphics Developers: Necessary Requirements for Querying Your Printer Implementing Message Overrides The information in this Technote is still relevant up to and including Mac OS 7.6 Additional Dialog Handling Functions with QuickDraw GX 1.1.5. Beginning with The Query Code the release of Mac OS 8.0, however, Apple plans to deliver a system which Summary incorporates QuickDraw GX graphics and typography only. QuickDraw GX printer References drivers and GX printing extensions will Downloadables not be supported in Mac OS 8.0 or in future Mac OS releases. Apple's goal is to simplify the user experience of printing by unifying the Macintosh graphic and printing architectures and standardizing on the classic Printing Manager. For details on Apple's official announcement, refer to </technotes/gxchange.html> For some time now, Apple developers have asked how they can query their PostScript printers at dtp creation time using the same methods as the LaserWriter GX printer driver. This Technote discusses how the LaserWriter GX driver does it at query time and provides you with the printing messages you need to override in order to achieve the same functionality. You may need to change or add to the code TN 1057 - Querying PS Printers at dtp Creation Time the GX Page: 2 Way in this Note. For example, if you want to query for the number of paper trays or query for an envelope tray, you will need to modify this code, as explained later in this Note.