Underlying and Consequential Costs of Cyber Security Breaches: Changes in Systematic Risk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

26MF321B LCD TV English
Owner’s Manual Manuel du Propriétaire Manual del Propietario 26MF321B LCD TV English Necesita ayuda inmediata? Français Español 1-866-341-3738 1-866-341-3738 1-866-341-3738 Quick Use Guide Inside! Guide d’usage Rapide Incluse! Guía de Uso Rápido Incluida! MODEL NUMBER SERIAL NUMBER 2 Return your Product Registration Card or visit at www.magnavox.com/support today to get the very most from your purchase. Registering your model with MAGNAVOX makes you eligible for all of the valuable benefits listed below, so don't miss out. Complete and return your Product Registration Card at once or visit at www.magnavox.com/support to ensure: *Product Safety Notification *Additional Benefits By registering your product, you'll receive notification - Registering your product guarantees that you'll receive directly from the manufacturer - in the rare case of a all of the privileges to which you're entitled, including product recall or safety defect. special money-saving offers. Know these safety symbols The lightning flash with arrowhead symbol, within an equilateral triangle, is intended to alert the user to the presence of CAUTION uninsulated “dangerous voltage” within the apparatus’s enclosure that may be of sufficient magnitude to constitute a risk of RISK OF ELECTRIC SHOCK electric shock to persons. DO NOT OPEN CAUTION: TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT The exclamation point within an equilateral triangle is intended to REMOVE COVER (OR BACK). NO USER-SERVICEABLE PARTS alert the user to the presence of important operating and INSIDE. REFER SERVICING TO QUALIFIED SERVICE PERSONNEL. maintenance (servicing) instructions in the literature accompanying The caution marking is located on the rear or bottom of the cabinet. -

Equipment Setup and Self-Installation Programming Your WOW! Atlas Universal Remote Control
table of contents WOW! equipment setup and self-installation Programming Your WOW! Atlas Universal Remote Control ...........................................................E-1 Programming Channel Control Lock ......................................................................................................E-3 Programming ID Lock ..................................................................................................................................E-3 Programming “Tune-In” Keys For Specific Channels ........................................................................E-4 table of contents Using The Master Power Key ....................................................................................................................E-4 Re-Assigning Device Keys ..........................................................................................................................E-5 Changing Volume Lock ...............................................................................................................................E-5 Atlas Cable Remote Control Codes ........................................................................................................E-7 Digital Cable Self-Installation ..................................................................................................................E-13 Advanced Digital Equipment Setup .....................................................................................................E-16 Connecting a Non-Stereo TV .............................................................................................................E-16 -
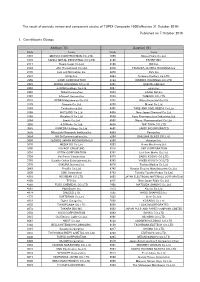
Published on 7 October 2016 1. Constituents Change the Result Of
The result of periodic review and component stocks of TOPIX Composite 1500(effective 31 October 2016) Published on 7 October 2016 1. Constituents Change Addition( 70 ) Deletion( 60 ) Code Issue Code Issue 1810 MATSUI CONSTRUCTION CO.,LTD. 1868 Mitsui Home Co.,Ltd. 1972 SANKO METAL INDUSTRIAL CO.,LTD. 2196 ESCRIT INC. 2117 Nissin Sugar Co.,Ltd. 2198 IKK Inc. 2124 JAC Recruitment Co.,Ltd. 2418 TSUKADA GLOBAL HOLDINGS Inc. 2170 Link and Motivation Inc. 3079 DVx Inc. 2337 Ichigo Inc. 3093 Treasure Factory Co.,LTD. 2359 CORE CORPORATION 3194 KIRINDO HOLDINGS CO.,LTD. 2429 WORLD HOLDINGS CO.,LTD. 3205 DAIDOH LIMITED 2462 J-COM Holdings Co.,Ltd. 3667 enish,inc. 2485 TEAR Corporation 3834 ASAHI Net,Inc. 2492 Infomart Corporation 3946 TOMOKU CO.,LTD. 2915 KENKO Mayonnaise Co.,Ltd. 4221 Okura Industrial Co.,Ltd. 3179 Syuppin Co.,Ltd. 4238 Miraial Co.,Ltd. 3193 Torikizoku co.,ltd. 4331 TAKE AND GIVE. NEEDS Co.,Ltd. 3196 HOTLAND Co.,Ltd. 4406 New Japan Chemical Co.,Ltd. 3199 Watahan & Co.,Ltd. 4538 Fuso Pharmaceutical Industries,Ltd. 3244 Samty Co.,Ltd. 4550 Nissui Pharmaceutical Co.,Ltd. 3250 A.D.Works Co.,Ltd. 4636 T&K TOKA CO.,LTD. 3543 KOMEDA Holdings Co.,Ltd. 4651 SANIX INCORPORATED 3636 Mitsubishi Research Institute,Inc. 4809 Paraca Inc. 3654 HITO-Communications,Inc. 5204 ISHIZUKA GLASS CO.,LTD. 3666 TECNOS JAPAN INCORPORATED 5998 Advanex Inc. 3678 MEDIA DO Co.,Ltd. 6203 Howa Machinery,Ltd. 3688 VOYAGE GROUP,INC. 6319 SNT CORPORATION 3694 OPTiM CORPORATION 6362 Ishii Iron Works Co.,Ltd. 3724 VeriServe Corporation 6373 DAIDO KOGYO CO.,LTD. 3765 GungHo Online Entertainment,Inc. -

VHS to DVD Manual
Introduction Connections ZV427FX4 ZV427FX4 A DVD Recorder/VCR LINE-IN RECORDING (No Tuner) Basic Setup Owner's Manual Recording INSTRUCCIONES EN ESPAÑOL INCLUIDAS. Playback Editing Function Setup VCR Functions Others Español © 2013 Funai Electric Co., Ltd. SAFETY INFORMATION The model and serial numbers of this unit may be found on the cabinet. Model No.: You should record and retain those numbers for future reference. Serial No.: WARNING: TO REDUCE THE RISK OF FIRE OR ELECTRIC SHOCK, DO NOT EXPOSE THIS APPARATUS TO RAIN OR MOISTURE. APPARATUS SHALL NOT BE EXPOSED TO DRIPPING OR SPLASHING AND NO OBJECTS FILLED WITH LIQUIDS, SUCH AS VASES, SHALL BE PLACED ON THE APPARATUS. The lightning flash with arrowhead symbol, within an CAUTION equilateral triangle, is intended to alert the user to the RISK OF ELECTRIC SHOCK presence of uninsulated “dangerous voltage” within the DO NOT OPEN product’s enclosure that may be of sufficient magnitude to constitute a risk of electric shock to persons. CAUTION: TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT The exclamation point within an equilateral triangle is REMOVE COVER (OR BACK). NO USER SERVICEABLE intended to alert the user to the presence of important operating and maintenance (servicing) instructions in PARTS INSIDE. REFER SERVICING TO QUALIFIED the literature accompanying the appliance. SERVICE PERSONNEL. The importantp note and rating are located on the rear or The symbol for CLASS ll (Double Insulation) bottom of the cabinet. IMPORTANT SAFETY INSTRUCTIONS 1. Read these instructions. 10. Protect the powerpgp cord from being walked on 2. Keep these instructions. or pinchedpp particularlypypg ypg at plugs, convenience 3. -
DIRECTV® Universal Remote Control User's Guide
DirecTV-M2081A.qxd 12/22/2004 3:44 PM Page 1 ® DIRECTV® Universal Remote Control User’s Guide DirecTV-M2081A.qxd 12/22/2004 3:44 PM Page 2 TABLE OF CONTENTS Introduction . .3 Features and Functions . .4 Key Charts . .4 Installing Batteries . .8 Controlling DIRECTV® Receiver. .9 Programming DIRECTV Remote . .9 Setup Codes for DIRECTV Receivers . .10 Setup Codes for DIRECTV HD Receivers . .10 Setup Codes for DIRECTV DVRs . .10 Programming to Control Your TV. .11 Programming the TV Input Key . .11 Deactivate the TV Input Select Key . .11 Programming Other Component Controls . .12 Manufacturer Codes . .13 Setup Codes for TVs . .13 Setup Codes for VCRs . .16 Setup Codes for DVD Players . .19 Setup Codes for Stereo Receivers . .20 Setup Codes for Stereo Amplifiers . .22 Searching For Your Code in AV1 or AV2 Mode . .23 Verifying The Codes . .23 Changing Volume Lock . .24 Restore Factory Default Settings . .25 Troubleshooting . .26 Repair or Replacement Policy . .27 Additional Information . .28 2 DirecTV-M2081A.qxd 12/22/2004 3:44 PM Page 3 INTRODUCTION Congratulations! You now have an exclusive DIRECTV® Universal Remote Control that will control four components, including a DIRECTV Receiver, TV, and two stereo or video components (e.g 2nd TV, DVD, or stereo). Moreover, its sophisticated technology allows you to consolidate the clutter of your original remote controls into one easy-to-use unit that's packed with features such as: z Four-position slide switch for easy component selection z Code library for popular video and stereo components z Code search to help program control of older or discon- tinued components z Memory protection to ensure you will not have to re- program the remote when the batteries are replaced Before using your DIRECTV Universal Remote Control, you may need to program it to operate with your particular com- ponent. -

Funai Electric Co., Ltd. 7-1, Nakagaito 7-Chome, Daito City, Osaka
(Translation) Securities Code: 6839 June 6, 2012 NOTICE OF THE 60TH ORDINARY GENERAL MEETING OF SHAREHOLDERS Dear Shareholders: We would like to express our appreciation for your continued good offices. Please take notice that the 60th Ordinary General Meeting of Shareholders of Funai Electric Co., Ltd. (the “Company”) will be held as described below and you are cordially invited to attend the meeting. Since voting rights can be exercised in writing, even if you are not present at the meeting, please go over the Reference Document for the General Meeting of Shareholders set forth below and send us by return mail the enclosed voting form indicating your approval or disapproval of the propositions no later than 5:00 p.m. on June 21 (Thursday), 2012. Yours very truly, Tomonori Hayashi Representative Director, President, and Chief Executive Officer Funai Electric Co., Ltd. 7-1, Nakagaito 7-chome, Daito City, Osaka Description 1. Date and hour: June 22 (Friday), 2012, 10:00 a.m. 2. Place: 5F, Multipurpose Hall, Technology Bldg. of the Company 7-1, Nakagaito 7-chome, Daito City, Osaka 3. Matters forming the objects of the meeting: Matters to be reported: 1. Report on the business report, the consolidated financial statements, and the results of audit of the consolidated financial statements by the accounting auditors and the Board of Corporate Auditors for the 60th fiscal year (from April 1, 2011 to March 31, 2012) 2. Report on the non-consolidated financial statements for the 60th fiscal year (from April 1, 2011 to March 31, 2012) Matters to be resolved: Proposition No. -

Top 300 Organizations Granted U.S. Patents in 2007
Top 300 Organizations Granted U.S. Patents in 2007 NOTE: IPO DOES NOT INTEND TO ENCOURAGE MORE PATENTING IN U.S. This annual report listing the organizations that received the most U.S. utility patents is being published by fO kramedarT & tnetaP .S.U eht morf deniatbo atad no desab si tI .raey evitucesnoc ht52 eht rof OPI rof eht ht52 evitucesnoc .raey tI si desab no atad deniatbo morf eht .S.U tnetaP & kramedarT fO fi .ec Patents granted to parent and subsidiary companies are combined in some instances. See the end notes for background on how the report was prepared. IPO does not intend for this report to encourage or discourage patenting. Some critics believe companies are applying for too many patents. In 2007 the U.S. Patent & Trademark Office announced that it would no longer publish its own report on organizations receiving the most patents, because it wanted to discour- age “any perception that we believe more is better.” IPO has opted to continue publishing this IPO report, however, because the number of patents granted is one of the few objective measures of the patent system as a whole and the patenting activities of individual industries and companies. IPO and others are study- ing ways to develop more reliable measures of patent quality. May 21, 2008 Contents: Numerical Listing . 2 Alphabetical Listing . 6 Notes . 10 © Copyright 2008 Intellectual Property Owners Association 1 2007 Patent Owners Numerical Listing Rank Organization Patent Rank Organization Patent 1 International Business Machines Corp. 3,125 45 Sanyo Electric Co., Ltd. 454 2 Samsung Electronics Co., Ltd. -
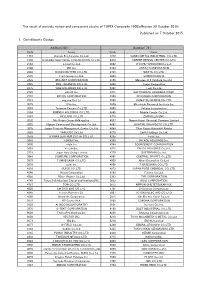
Published on 7 October 2015 1. Constituents Change the Result Of
The result of periodic review and component stocks of TOPIX Composite 1500(effective 30 October 2015) Published on 7 October 2015 1. Constituents Change Addition( 80 ) Deletion( 72 ) Code Issue Code Issue 1712 Daiseki Eco.Solution Co.,Ltd. 1972 SANKO METAL INDUSTRIAL CO.,LTD. 1930 HOKURIKU ELECTRICAL CONSTRUCTION CO.,LTD. 2410 CAREER DESIGN CENTER CO.,LTD. 2183 Linical Co.,Ltd. 2692 ITOCHU-SHOKUHIN Co.,Ltd. 2198 IKK Inc. 2733 ARATA CORPORATION 2266 ROKKO BUTTER CO.,LTD. 2735 WATTS CO.,LTD. 2372 I'rom Group Co.,Ltd. 3004 SHINYEI KAISHA 2428 WELLNET CORPORATION 3159 Maruzen CHI Holdings Co.,Ltd. 2445 SRG TAKAMIYA CO.,LTD. 3204 Toabo Corporation 2475 WDB HOLDINGS CO.,LTD. 3361 Toell Co.,Ltd. 2729 JALUX Inc. 3371 SOFTCREATE HOLDINGS CORP. 2767 FIELDS CORPORATION 3396 FELISSIMO CORPORATION 2931 euglena Co.,Ltd. 3580 KOMATSU SEIREN CO.,LTD. 3079 DVx Inc. 3636 Mitsubishi Research Institute,Inc. 3093 Treasure Factory Co.,LTD. 3639 Voltage Incorporation 3194 KIRINDO HOLDINGS CO.,LTD. 3669 Mobile Create Co.,Ltd. 3197 SKYLARK CO.,LTD 3770 ZAPPALLAS,INC. 3232 Mie Kotsu Group Holdings,Inc. 4007 Nippon Kasei Chemical Company Limited 3252 Nippon Commercial Development Co.,Ltd. 4097 KOATSU GAS KOGYO CO.,LTD. 3276 Japan Property Management Center Co.,Ltd. 4098 Titan Kogyo Kabushiki Kaisha 3385 YAKUODO.Co.,Ltd. 4275 Carlit Holdings Co.,Ltd. 3553 KYOWA LEATHER CLOTH CO.,LTD. 4295 Faith, Inc. 3649 FINDEX Inc. 4326 INTAGE HOLDINGS Inc. 3660 istyle Inc. 4344 SOURCENEXT CORPORATION 3681 V-cube,Inc. 4671 FALCO HOLDINGS Co.,Ltd. 3751 Japan Asia Group Limited 4779 SOFTBRAIN Co.,Ltd. 3844 COMTURE CORPORATION 4801 CENTRAL SPORTS Co.,LTD. -

Survey of Integrated Reports in Japan 2018
Survey of Integrated Reports in Japan 2018 Integrated Reporting Center of Excellence KPMG in Japan March 2019 home.kpmg/jp Message from global thought leaders In this, the fifth year this survey report has been issued, KPMG has solicited the observations of thought leaders on corporate reporting. Japanese businesses pride themselves on a longer-term focus compared to the rest of the world, where prioritizing short-term gains has too often become the norm. Focusing on long-term value creation and taking into account all of the resources an organization uses is the sustainable, profitable, and proven way to manage a business. Many Japanese businesses are just beginning to implement integrated thinking and reporting. The findings in this report show that senior management must take ownership to spread integrated thinking in their businesses – not just in accounting but in strategy, operations, marketing, and the rest of the company as well. This report makes me optimistic and excited for Japanese business leaders as they strive to think, act, and communicate in an integrated and sustainable way. Dominic Barton ― International Integrated Reporting Council, Chairman Integrated Reporting improves communication between companies and investors and where most effective, sets the stage for enhanced corporate value creation over the mid to long-term. Investors desire integrated reports which provide comprehensive information disclosure useful for making investment decisions. The International Corporate Governance Network (ICGN) has encouraged integrated reporting for many years. In 2015, ICGN s Disclosure and Transparency Committee ’ released Guidance on Integrated Business Reporting. The Guidance amplifies that strategic decisions should be based on factors that are broader than those reflected in the financial statements. -
![Corporate Profile 2020 [PDF: 5156KB]](https://docslib.b-cdn.net/cover/1434/corporate-profile-2020-pdf-5156kb-2901434.webp)
Corporate Profile 2020 [PDF: 5156KB]
FUNAI ELECTRIC (H.K.), LTD. FUNAI SERVICE CORPORATION FUNAI ELECTRIC R&D FUNAI LEXINGTON (SHENZHEN) CO., LTD. TECHNOLOGY CORPORATION FUNAI ELECTRIC CO., LTD. Head ofce P&F MEXICANA, FUNAI SERVICE CO., LTD. S.A. DE C.V. FUNAI (THAILAND) CO., LTD. FUNAI GENERAL SERVICE CO., LTD. FUNAI MANUFACTURING, FUNAI MALAYSIA R and D SDN. BHD. S.A. DE C.V. 2020 FUNAI TRADING CORP. Graphic Corporation Corporate Profile FUNAI ELECTRIC PHILIPPINES INC. FUNAI CORPORATION, INC. TOKYO BRANCH OFFICE FUNAI ELECTRIC CEBU, INC. PreXion Corporation CHUGOKU FUNAI ELECTRIC CO., LTD. | Corporate Philosophy | Corporate Philosophy Framework The Fundamental Principle, Corporate Precepts, and Corporate Commitments are the foundation and supporting pillars of our corporate activities, and clearly express the founding spirit. The Corporate Philosophy and Group Vision were established in 2018, based on these pillars. They convey the corporate image and guidelines for conduct, and evolve with the times and social conditions. Fundamental Principle Dream with Conviction, and Act on Information Management Philosophy Challenge the company to grow by becoming helpful in the community Group Vision Funai creates products that are the choice of people around the world “Around the world,” as a global company “The choice,” aiming for top share in the industry “Creates products,” that people will love Contents Corporate Philosophy 1 Topics 10 Message from the President & CEO 3 Core Competencies 11 At a Glance 5 ESG 13 Financial Highlights 6 ESG Topics 16 Business Description 7 History 17 Our Initiatives for 2020 9 1 Corporate Commitments To adopt continual product improvements To continually promote ever deeper trust To seek further harmony and mutual prosperity Corporate Precepts Perseverance overcomes all difficulties. -

In the United States District Court for the District of Delaware
IN THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF DELAWARE MnCs & p ARTNERS AMERICA, INC. and GOLD CHARM LIMITED., Plaintiffs, V. TOSHIBA CORPORATION and TOSHIBA No. 14-cv-803 (RGA) AMERICAN INFORMATION SYSTEMS, Defendants, SAMSUNG DISPLAY Co., LTD., Intervenor. Mncs & p ARTNERS, AMERICA, INC. and GOLD CHARM LTD., Plaintiffs, v. FUNAI ELECTRIC Co. LTD., FUNAI No. 14-cv-804 (RGA) CORPORATION INC., and P&F USA INC., Defendants, SAMSUNG DISPLAY Co., LTD., Intervenor. MEMORANDUM OPINION Dennis J. Butler, John D. Simmons, PANITCH SCHWARZE BELISARIO & NADEL, LLP, Wilmington, Del.; Frederick A. Teece, Bryon T. Wasserman, Aaron R. Ettelman, ICE MILLER LLP, Philadelphia, Penn.; Anthony Nimmo, ICE MILLER LLP, Chicago, Ill., Keith Jones, Stephen F. Murray, PANITCH SCHWARZE BELISARIO & NADEL, LLP, Philadelphia, Penn., attorneys for Plaintiffs MiiCs & Partners America, Inc. and Gold Charm Limited. Benjamin J. Schladweiler, Nicholas D. Mozal, Ross ARONSTAM & MORITZ LLP, Wilmington, Del.; J.C. Rozendaal, Michael E. Joffre, William H. Milliken, STERNE, KESSLER, GOLDSTEIN & Fox P.L.L.C., Washington, D.C., attorneys for Defendants Funai Electric Co. Ltd., Funai Corporation Inc., and P&F USA Inc. Robert W. Mallard, DORSEY & WHITNEY LLP, Wilmington, Del.; Paul T. Meiklejohn, David Tseng, DORSEY & WHITNEYLLP, Seattle, Wash.; Clinton L. Conner, DORSEY & WHITNEY LLP, Minneapolis, Minn., attorneys for Defendants Toshiba Corporation, and Toshiba America Information Systems, Inc. Adam W. Poff, Pilar G. Kraman, YOUNG CONAWAY STARGATT & TAYLOR LLP, Wilmington, Del., Kevin B. Collins, Jeffrey H. Lerner, David A. Garr, Jared R. Frisch, COVINGTON & BURLING, LLP, Washington, D.C., Robert T. Haslam, COVINGTON & BURLING, LLP, Redwood Shores, Cal., attorneys for Intervenor Samsung Display Co., Ltd. -
Potenza ST Universal Remote Control
Nebula Potenza ST.fm Page 1 Monday, October 15, 2007 4:55 PM Potenza ST Universal Remote Control Users Guide PREPROGRAMMED FOR YOUR SET-TOP BOX Nebula Potenza ST.fm Page 2 Monday, October 15, 2007 4:55 PM TABLE OF CONTENTS Introduction . 4 Features and Functions . 5 Key Charts. 6 Device Table . 8 Installing Batteries. 9 Programming Device Control. 9 Setting Up a Combo Unit. 11 Searching for Your Code . 12 Checking the Codes . 13 Using Learning . 14 Learning Precautions . 14 Programming a Learned Key . 14 Deleting a Single Learning Key. 15 Deleting All Learned Keys in a Specific Mode . 16 Programming Channel Control Lock . 16 Unlocking Channel Control. 17 Locking Channel Control to STB. 17 Changing Volume Lock . 17 Unlocking Volume Control for a Single Device (Individual Volume Unlock) . 18 Unlocking All Volume Control (Global Volume Unlock) . 18 Locking Volume Control To One Mode (Global Volume Lock) 19 Programming ID Lock. 19 Programming Macro Keys . 20 Programming a Macro Key. 20 Clearing a Macro Key . 21 Using the Master Power Key. 21 Programming the Master Power Key . 21 Using the Master Power Key. 22 Clearing the Master Power Key . 22 Re-Assigning Device Keys. 23 Clearing Custom Programming . 24 Troubleshooting . 24 FCC Notice . 25 Additional Information . 26 Manufacturer’s Codes . 27 Setup Codes for Audio Amplifiers. 27 Setup Codes for Audio Receivers. 27 Setup Codes for Audio Accessories . 30 Setup Codes for Cable Boxes/Converters . 30 Setup Codes for DVD Players . 32 Setup Codes for DVD Recorders. 37 Setup Codes for DVD Combos. 37 Satellite Receivers and DVR/PVR Systems.