Solaris Security Tale
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Solaris: the Carrier-Grade Operating System Technical Brief
An Oracle White Paper February 2011 Oracle Solaris: The Carrier-Grade Operating System Oracle White Paper—Oracle Solaris: The Carrier-Grade OS Executive Summary.............................................................................1 ® Powering Communication—The Oracle Solaris Ecosystem..............3 Integrated and Optimized Stack ......................................................5 End-to-End Security ........................................................................5 Unparalleled Performance and Scalability.......................................6 Increased Reliability ........................................................................7 Unmatched Flexibility ......................................................................7 SCOPE Alliance ..............................................................................7 Security................................................................................................8 Security Hardening and Monitoring .................................................8 Process and User Rights Management...........................................9 Network Security and Encrypted Communications .......................10 Virtualization ......................................................................................13 Oracle VM Server for SPARC .......................................................13 Oracle Solaris Zones .....................................................................14 Virtualized Networking...................................................................15 -

Solaris 10 End of Life
Solaris 10 end of life Continue Oracle Solaris 10 has had an amazing OS update, including ground features such as zones (Solaris containers), FSS, Services, Dynamic Tracking (against live production operating systems without impact), and logical domains. These features have been imitated in the market (imitation is the best form of flattery!) like all good things, they have to come to an end. Sun Microsystems was acquired by Oracle and eventually, the largest OS known to the industry, needs to be updated. Oracle has set a retirement date of January 2021. Oracle indicated that Solaris 10 systems would need to raise support costs. Oracle has never provided migratory tools to facilitate migration from Solaris 10 to Solaris 11, so migration to Solaris has been slow. In September 2019, Oracle decided that extended support for Solaris 10 without an additional financial penalty would be delayed until 2024! Well its March 1 is just a reminder that Oracle Solaris 10 is getting the end of life regarding support if you accept extended support from Oracle. Combined with the fact gdpR should take effect on May 25, 2018 you want to make sure that you are either upgraded to Solaris 11.3 or have taken extended support to obtain any patches for security issues. For more information on tanningix releases and support dates of old and new follow this link ×Sestive to abort the Unix Error Operating System originally developed by Sun Microsystems SolarisDeveloperSun Microsystems (acquired by Oracle Corporation in 2009)Written inC, C'OSUnixWorking StateCurrentSource ModelMixedInitial release1992; 28 years ago (1992-06)Last release11.4 / August 28, 2018; 2 years ago (2018-08-28)Marketing targetServer, PlatformsCurrent: SPARC, x86-64 Former: IA-32, PowerPCKernel typeMonolithic with dynamically downloadable modulesDefault user interface GNOME-2-LicenseVariousOfficial websitewww.oracle.com/solaris Solaris is the own operating system Of Unix, originally developed by Sunsystems. -

Sun SPARC Enterprise T5440 Servers
Sun SPARC Enterprise® T5440 Server Just the Facts SunWIN token 526118 December 16, 2009 Version 2.3 Distribution restricted to Sun Internal and Authorized Partners Only. Not for distribution otherwise, in whole or in part T5440 Server Just the Facts Dec. 16, 2009 Sun Internal and Authorized Partner Use Only Page 1 of 133 Copyrights ©2008, 2009 Sun Microsystems, Inc. All Rights Reserved. Sun, Sun Microsystems, the Sun logo, Sun Fire, Sun SPARC Enterprise, Solaris, Java, J2EE, Sun Java, SunSpectrum, iForce, VIS, SunVTS, Sun N1, CoolThreads, Sun StorEdge, Sun Enterprise, Netra, SunSpectrum Platinum, SunSpectrum Gold, SunSpectrum Silver, and SunSpectrum Bronze are trademarks or registered trademarks of Sun Microsystems, Inc. in the United States and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the United States and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. UNIX is a registered trademark in the United States and other countries, exclusively licensed through X/Open Company, Ltd. T5440 Server Just the Facts Dec. 16, 2009 Sun Internal and Authorized Partner Use Only Page 2 of 133 Revision History Version Date Comments 1.0 Oct. 13, 2008 - Initial version 1.1 Oct. 16, 2008 - Enhanced I/O Expansion Module section - Notes on release tabs of XSR-1242/XSR-1242E rack - Updated IBM 560 and HP DL580 G5 competitive information - Updates to external storage products 1.2 Nov. 18, 2008 - Number -

Opensolaris Et La Sécurité Master 2 SSI Université Du Sud, Toulon Et Du Var
David Pauillac OpenSolaris et la sécurité Master 2 SSI Université du Sud, Toulon et du Var novembre 2007 ii Copyright c 2007 David PAUILLAC. Ce document est distribué sous Licence GNU Free Documentation License 1. Vous pouvez copier et/ou distribuer ce document à condition de respecter les termes de la GFDL, version 1.2 ou toute version publiée ultérieurement par la Free Software Foundation. Une copie de la licence est incluse en annexe C intitulée “GNU Free Documentation License”. Les nom et logos OpenSolaris sont des marques déposées par Sun Microsystem. 1. GFDL David Pauillac c novembre 2007 - OpenSolaris et la sécurité Avant-propos À propos du document Ce document, à l’origine, était destiné aux étudiants de master2 SSI de l’université de Sud, Toulon et du Var. Cependant, j’espère qu’il pourra ser- vir aussi aux administrateurs devant (ou désirant) utiliser un système basé sur OpenSolaris (tel que le système de Sun Microsystem, Solaris, largement répandu). Il m’a semblé intéressant de comparer, lorsque celà est nécessaire, OpenSo- laris et GNU/Linux ; en effet, ce dernier est bien plus connu dans le monde universitaire que le système ouvert de Sun Microsystem. Ainsi, le but de ce document n’est pas de remplacer la documentation fournie avec le système Solaris, mais juste de fournir des informations impor- tantes pour installer, configurer et sécuriser un système basé sur OpenSolaris, que ce soit sur un serveur ou sur une station de travail. Pour toute remarque ou question, vous pouvez contacter l’auteur à l’adresse suivante: [email protected] En introduction, il m’a semblé important de retracer brièvement l’histoire des systèmes UNIX ainsi que de traiter certains points théoriques de ce type de systèmes d’exploitation. -

Red Hat Enterprise Linux: Your Solaris Alternative
RED HAT ENTERPRISE LINUX: YOUR SOLARIS ALTERNATIVE 2 INTRODUCTION 3 FACTORS THAT INFLUENCE OPERATING SYSTEM CHOICE New projects Mandated migration 4 BUSINESS REQUIREMENTS TO CONSIDER Strength of ISV support Application migration considerations Performance Availability and scalability Security 11 TOTAL COST OF OWNERSHIP (TCO) Feature of comparison 13 DETAILED COMPARISON OF SELECTED FEATURES Filesystems and volume managers: Ext3, Ext4, XFS vs. UFS and ZFS DTrace vs SystemTap Software management 18 CONCLUSION Platform support Customer value www.redhat.com Red Hat Enterprise Linux: Your Solaris Alternative INTRODUCTION There were two primary reasons that IT professionals previously chose the Oracle Sun SPARC platform to power their IT infrastructures: the performance of the hardware and the robustness of the Solaris operating system. As the price, performance, and reliability of industry-standard x86_64 servers have increased to the point where they can meet and exceed these features, the reasons to continue buying SPARC hardware have become less and less compelling. This is particularly true with with large, multi-core x86 systems that are designed specifically for Linux©, such as the latest 128-core systems. Similarly, Linux, and in particular, Red Hat© Enterprise Linux, have emerged as the operating system of choice to leverage the benefits of open, industry-standard architectures. Selecting an operating system for your IT infrastructure has long-term consequences. The selection process must take into account not only the technical features of the current operating system, but the ability for the operating system to enable and support your future business requirements. While Oracle has quelled some worry over their commitment to Solaris, the move to Solaris 11 will likely be as painful as the move from Solaris 8/9 to Solaris 10, as Solaris 11 is significantly different from Solaris 10. -

Migrating to Oracle Solaris with Oracle Database 11G on Intel Xeon
A migration guide commissioned by Intel Corp. and Oracle Table of contents Table of contents ....................................................................... 2 Preface ...................................................................................... 4 Introduction ............................................................................... 5 Scope of this Guide ..................................................................................... 5 A move that will yield real benefits ............................................................ 6 Features of the Sun Fire X4800 Server with the Intel Xeon Processor 7500 series ........................................................................................................... 6 Features of Oracle Solaris 10 ...................................................................... 7 Planning the migration .............................................................. 9 Considerations for moving your applications ............................................. 9 Java-based applications ...............................................................................9 A note about application data ......................................................................9 Considerations for moving platforms ......................................................... 9 Application compatibility ..............................................................................9 Difference in operating systems ...................................................................9 Considerations -
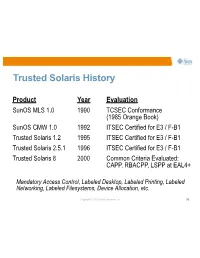
Trusted Solaris History
Trusted Solaris History Product Year Evaluation SunOS MLS 1.0 1990 TCSEC Conformance (1985 Orange Book) SunOS CMW 1.0 1992 ITSEC Certified for E3 / F-B1 Trusted Solaris 1.2 1995 ITSEC Certified for E3 / F-B1 Trusted Solaris 2.5.1 1996 ITSEC Certified for E3 / F-B1 Trusted Solaris 8 2000 Common Criteria Evaluated: CAPP, RBACPP, LSPP at EAL4+ Mandatory Access Control, Labeled Desktop, Labeled Printing, Labeled Networking, Labeled Filesystems, Device Allocation, etc. Copyright © 2009 Sun Microsystems, Inc. 79 Trusted Solaris History Product Year Evaluation SunOS MLS 1.0 1990 TCSEC Conformance (1985 Orange Book) SunOS CMW 1.0 1992 ITSEC Certified for E3 / F-B1 Trusted Solaris 1.2 1995 ITSEC Certified for E3 / F-B1 Trusted Solaris 2.5.1 1996 ITSEC Certified for E3 / F-B1 Trusted Solaris 8 2000 Common Criteria Evaluated: CAPP, RBACPP, LSPP at EAL4+ Mandatory Access Control, Labeled Desktop, Labeled Printing, Labeled Networking, Labeled Filesystems, Device Allocation, etc. Copyright © 2009 Sun Microsystems, Inc. 79 Solaris Trusted Extensions •A redesign of the Trusted Solaris product using a layered architecture. •An extension of the Solaris 10 security foundation providing access control policies based on the sensitivity/label of objects. •A set of label-aware services which implement multilevel security. Copyright © 2009 Sun Microsystems, Inc. 80 Extending Solaris 10 Security Features •Process Rights Management (Privileges) >Fine-grained privileges for X windows >Rights management applied to desktop actions •User Rights Management (RBAC) >Labels and clearances >Additional desktop policies •Solaris Containers (Zones) >Unique Sensitivity Labels >Trusted (label-based) Networking Copyright © 2009 Sun Microsystems, Inc. 81 Trusted Extensions in a Nutshell •Every object has a label associated with it. -

DS2OS - Deliverable B Operating System Technologies
Consiglio Nazionale delle Ricerche Istituto di Calcolo e Reti ad Alte Prestazioni DS2OS - Deliverable B Operating System Technologies Giovanni Schmid, Alessandra Rossi RT-ICAR-NA-2010-03 Dicembre 2010 Consiglio Nazionale delle Ricerche, Istituto di Calcolo e Reti ad Alte Prestazioni (ICAR) – Sede di Napoli, Via P. Castellino 111, I-80131 Napoli, Tel: +39-0816139508, Fax: +39- 0816139531, e-mail: [email protected], URL: www.na.icar.cnr.it 1 Consiglio Nazionale delle Ricerche Istituto di Calcolo e Reti ad Alte Prestazioni DS2OS - Deliverable B Operating System Technologies Giovanni Schmid1, Alessandra Rossi Rapporto Tecnico N.: Data: RT-ICAR-NA-2010-03 Dicembre 2010 1 Istituto di Calcolo e Reti ad Alte Prestazioni, ICAR-CNR, Sede di Napoli, Via P. Castellino 111, 80131 Napoli I rapporti tecnici dell’ICAR-CNR sono pubblicati dall’Istituto di Calcolo e Reti ad Alte Prestazioni del Consiglio Nazionale delle Ricerche. Tali rapporti, approntati sotto l’esclusiva responsabilità scientifica degli autori, descrivono attività di ricerca del personale e dei collaboratori dell’ICAR, in alcuni casi in un formato preliminare prima della pubblicazione definitiva in altra sede. 2 DS2OS - Deliverable B Operating System Technologies Giovanni Schmid, Alessandra Rossi December 1, 2010 1 Introduction The Distributed Security-Oriented Operating Systems (DS2OS) Project aims to integrate Dynamic Delegation facilities into open-source operating systems technologies, in order to obtain the building blocks of fully scalable and interoperable distributed environments. Dynamic Delegation (DD) is an access control facility which allows users or applications on a given host to grant specific authorizations to remote principals about resources they own as a result of their accounting profiles on such host. -

Virtualization and Namespace Isolation in the Solaris Operating System (PSARC/2002/174)
Virtualization and Namespace Isolation in the Solaris Operating System (PSARC/2002/174) John Beck, David Comay, Ozgur L., Daniel Price, and Andy T. Solaris Kernel Technology Andrew G. and Blaise S. Solaris Network and Security Technologies Revision 1.6 (OpenSolaris) September 7, 2006 ii Contents 1 Introduction 1 1.1 Zone Basics . 2 1.2 Zone Principles . 3 1.3 Terminology and Conventions . 5 1.4 Outline . 6 2 Related Work 7 3 Zone Runtime 9 3.1 Zone State Model . 9 3.2 Zone Names and Numeric IDs . 10 3.3 Zone Runtime Support . 10 3.3.1 zoneadmd(1M) ............................... 10 3.3.2 zsched . 12 3.4 Listing Zone Information . 12 4 Zone Administration 13 4.1 Zone Configuration . 13 4.1.1 Configuration Data . 14 4.2 Zone Installation . 15 4.3 Virtual Platform Administration . 16 4.3.1 Readying Zones . 16 4.3.2 Booting Zones . 16 4.3.3 Halting Zones . 17 4.3.4 Rebooting Zones . 17 4.3.5 Automatic Zone Booting . 18 4.4 Zone Login . 18 4.4.1 Zone Console Login . 18 4.4.2 Interactive and Non-Interactive Modes . 19 4.4.3 Failsafe Mode . 20 4.4.4 Remote Login . 20 4.5 Monitoring and Controlling Zone Processes . 21 iii 5 Administration within Zones 23 5.1 Node Name . 23 5.2 Name Service Usage within a Zone . 23 5.3 Default Locale and Timezone . 24 5.4 Initial Zone Configuration . 24 5.5 System Log Daemon . 24 5.6 Commands . 25 5.7 Internals of Booting Zones . -

Oracle Solaris and Fujitsu SPARC Enterprise Systems — Integrated and Optimized for Enterprise Computing
A Fujitsu White Paper May 2011 Oracle Solaris and Fujitsu SPARC Enterprise Systems — Integrated and Optimized for Enterprise Computing Oracle Solaris and Fujitsu SPARC Enterprise Systems—Integrated and Optimized for Enterprise Computing Executive Overview............................................................................. 2 Introduction—Datacenter Integration .................................................. 2 Overview ............................................................................................. 2 The Oracle Solaris Ecosystem........................................................ 2 SPARC Processors......................................................................... 3 Architected for Reliability..................................................................... 6 Oracle Solaris Predictive Self Healing ............................................ 7 Highly Reliable Memory Subsystems.............................................. 8 Oracle Solaris ZFS for Reliable Data .............................................. 9 Reliable Networking ........................................................................ 9 Scalable Performance....................................................................... 10 World Record Performance........................................................... 12 Network Performance ................................................................... 14 Security ............................................................................................. 14 Integrated with Fujitsu SPARC -

(Prstat, Iostat, Mpstat, Vmstat) • Solaris Containers* • Dtrace
Deploying SAS®9 on Solaris™ 10: Calling Superheroes to Fight Supervillians Maureen Chew, Sun Microsystems Abstract : Solaris 10 brings a dream team cast of superheroes that can enlighten and empower meek and mild mannered SAS users / systems administrators to fight the evil villians and archenemies which prevent successful SAS deployments. Solaris 10 Containers brings Spider-Man to the rescue in the form of extreme agility as we explore a novel approach to promotion of SAS 9 test environments to production as well as extreme 'web' security in stopping attackers cold by forming protective shields or nets. Service Management Framework(SMF), part of the Solaris 10 Predictive Self-Healing feature, brings the superhuman healing factors known to the Incredible Hulk and X-Men's Wolverine and Archangel. Discover how SMF can monitor and self-heal key services such as SAS Metadata server and OLAP server. Solaris 10 DTrace is Batman's utility belt needed by Solaris admins and users who need to be 'in the know'. Ever present,unobtrusive, DTrace has what you need, when you need it and provides the capbility to answer "What? Where? When? How? Why?" in complex, large scale, multi-user deployment environments. Last but not least, Wonder Woman's Lasso of Truth gets thrown for a bonus section on SAS 9 installation and deployment tips. The much anticipated release of Sun's Solaris 10 in February '05, represents a tremendous amount of innovation. Coupled with the Solaris open source release, there is no doubt that widespread adoption of Solaris 10 will follow. Solaris 10 is an excellent platform for deployment of SAS 9 applications. -

Solaris Trusted Extensions Installation, Configuration
Solaris Trusted Extensions Installation, Configuration Student Guide - Volume I SC-327-S10 Rev B D61906GC10 Edition 1.0 2009 D62627 Copyright © 2009, Oracle and/or its affiliates. All rights reserved. Disclaimer This document contains proprietary information, is provided under a license agreement containing restrictions on use and disclosure, and is protected by copyright and other intellectual property laws. You may copy and print this document solely for your own use in an Oracle training course. The document may not be modified or altered in any way. Except as expressly permitted in your license agreement or allowed by law, you may not use, share, download, upload, copy, print, display, perform, reproduce, publish, license, post, transmit, or distribute this document in whole or in part without the express authorization of Oracle. The information contained in this document is subject to change without notice. If you find any problems in the document, please report them in writing to: Oracle University, 500 Oracle Parkway, Redwood Shores, California 94065 USA. This document is not warranted to be error-free. Sun Microsystems, Inc. Disclaimer This training manual may include references to materials, offerings, or products that were previously offered by Sun Microsystems, Inc. Certain materials, offerings, services, or products may no longer be offered or provided.Oracle and its affiliates cannot be held responsible for any such references should they appear in the text provided. Restricted Rights Notice If this documentation is delivered to the U.S. Government or anyone using the documentation on behalf of the U.S. Government, the following notice is applicable: U.S.