Kemp Web Application Firewall
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Best Practices: Use of Web Application Firewalls
OWASP Papers Program Best Practice: Use of Web Application Firewalls Best Practices: Use of Web Application Firewalls Version 1.0.4, March 2008, English translation 25. May 2008 Author: OWASP German Chapter with collaboration from: Maximilian Dermann Mirko Dziadzka Boris Hemkemeier Achim Hoffmann Alexander Meisel Matthias Rohr Thomas Schreiber OWASP Papers Program Best Practice: Use of Web Application Firewalls Abstract Web applications of all kinds, whether online shops or partner portals, have in recent years increasingly become the target of hacker attacks. The attackers are using methods which are specifically aimed at exploiting potential weak spots in the web application software itself – and this is why they are not detected, or are not detected with sufficient accuracy, by traditional IT security systems such as network firewalls or IDS/IPS systems. OWASP develops tools and best practices to support developers, project managers and security testers in the development and operation of secure web applications. Additional protection against attacks, in particular for already productive web applications, is offered by what is still a emerging category of IT security systems, known as Web Application Firewalls (hereinafter referred to simply as WAF), often also called Web Application Shields or Web Application Security Filters. One of the criteria for meeting the security standard of the credit card industry currently in force (PCI DSS - Payment Card Industry Data Security Standard v.1.1) for example, is either a regular source code review or the use of a WAF. The document is aimed primarily at technical decision-makers, especially those responsible for operations and security as well as application owners (specialist department, technical application managers) evaluating the use of a WAF. -

CGSS DS US R2.Indd
Gateway Content Anti-Virus Filtering Anti- ViewPoint Spyware Intrusion 24x7 Prevention Support SonicWALL Comprehensive Gateway Security Suite NETWORK SECURITY Complete Network Security in a Single Integrated Package Understanding network security can be complicated, but ensuring that your network is secure from malicious threats shouldn’t be. SonicWALL Comprehensive Security Suite (CGSS) removes the complexity associated with choosing a host of add-on security services by integrating all the network security services required for total protection into a convenient, aff ordable package that turns any SonicWALL network security appliance into a complete solution. Available on E-Class NSA, NSA and TZ Series network security appliances, SonicWALL CGSS keeps your network safe from viruses, spyware, worms, Trojans, intrusion attacks and other online threats. As soon as new threats are identified and often before software vendors ■ Complete network can patch their software, the SonicWALL security solutions are automatically updated with security solution signatures that protect against these threats and stop attacks before they can make their way into your network, ensuring you have around-the-clock protection. Your SonicWALL solution ■ Gateway anti-virus, anti-spyware and also has the ability to manage internal access to inappropriate, unproductive and potentially intrusion prevention illegal Web content with comprehensive content filtering. Finally, this powerful services ■ Application Firewall bundle also includes around-the-clock technical support, crucial firmware updates and real-time reporting capabilities. ■ Content filtering SonicWALL Comprehensive Security Suite includes the following: ■ 24x7 Support with ■ Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention and Application Firewall* Service firmware updates subscription ■ ViewPoint reporting ■ Content Filtering Service subscription – Premium Edition on E-Class NSA, NSA and software TZ 210/200/100 Series. -

Best Practices: Use of Web Application Firewalls
OWASP Papers Program Best Practice: Use of Web Application Firewalls Best Practices: Use of Web Application Firewalls Version 1.0.5, March 2008, English translation 25. May 2008 Author: OWASP German Chapter with collaboration from: Maximilian Dermann Mirko Dziadzka Boris Hemkemeier Achim Hoffmann Alexander Meisel Matthias Rohr Thomas Schreiber OWASP Papers Program Best Practice: Use of Web Application Firewalls Abstract Web applications of all kinds, whether online shops or partner portals, have in recent years increasingly become the target of hacker attacks. The attackers are using methods which are specifically aimed at exploiting potential weak spots in the web application software itself – and this is why they are not detected, or are not detected with sufficient accuracy, by traditional IT security systems such as network firewalls or IDS/IPS systems. OWASP develops tools and best practices to support developers, project managers and security testers in the development and operation of secure web applications. Additional protection against attacks, in particular for already productive web applications, is offered by what is still a emerging category of IT security systems, known as Web Application Firewalls (hereinafter referred to simply as WAF), often also called Web Application Shields or Web Application Security Filters. One of the criteria for meeting the security standard of the credit card industry currently in force (PCI DSS - Payment Card Industry Data Security Standard v.1.1) for example, is either a regular source code review or the use of a WAF. The document is aimed primarily at technical decision-makers, especially those responsible for operations and security as well as application owners (specialist department, technical application managers) evaluating the use of a WAF. -

Securing a Modern Web Application in AWS
Securing a Modern Web Application in AWS Explore threat modeling and learn how to create and support your web application security strategy with AWS Marketplace software seller solutions. AWS Marketplace Introduction As more organizations turn to distributed web applications to maintain high availability and reduce costs, many are choosing to store these applications in the AWS cloud for added elasticity, scalability, and ability to handle large workloads. Doing this securely, however, means addressing potential threats to multiple components, such as the front-end cloud application and corresponding databases. In this whitepaper, SANS analyst and instructor, Shaun McCullough, will provide an introduction to exploring the vulnerabilities associated with modern web applications, web application firewalls, and DevSec operations that oversee security to continually update code. This process, known as threat modeling, is vital to the ability to prioritize vulnerabilities and security operations to meet those challenges. Building on Shaun’s perspective, AWS Marketplace shares how this process can be applied to your AWS Cloud environment with an introduction to relevant AWS security services and AWS Marketplace software sellers, such as Fortinet, Barracuda, and Imperva. The featured Fortinet solutions for this use case can be accessed in AWS Marketplace Fortinet Managed Rules for AWS WAF AWS Quick Start for Fortinet FortiGate Fortinet FortiWeb Cloud WAF-as-a-Service A SANS Whitepaper How to Protect a Modern Web Application in AWS Written by Shaun McCullough Sponsored by: April 2019 AWS Marketplace Introduction As businesses move more assets to the cloud, having a security plan is essential, but nobody has the time or resources to do everything that is needed from the start. -
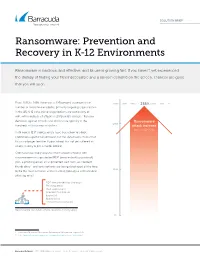
Ransomware: Prevention and Recovery in K-12 Environments
SOLUTION BRIEF Ransomware: Prevention and Recovery in K-12 Environments Ransomware is insidious, and effective, and its use is growing fast. If you haven’t yet experienced the dismay of finding your files inaccessible and a ransom demand on the screen, chances are good that you will soon. From 2018 to 2019, there was a 235-percent increase in the 235% number of ransomware attacks, primarily targeting organizations in the US. K-12 educational organizations are particularly at risk1, with hundreds of attacks in 2019 on US schools2. Ransom demands against schools and districts are typically in the Ransomware 200% hundreds of thousands of dollars. attack increase from 2018–2019 Until now, K-12 IT professionals have been slow to adopt protections against ransomware, but the data makes it clear that this is no longer tenable. If your school has not yet suffered an attack, it really is just a matter of time. Criminals have many ways to infect school networks with ransomware—an unprotected RDP (remote desktop protocol) port, a phishing email, an unprotected web form, an infected thumb drive—and new methods are being developed all the time. 100% By far the most common vector is email, typically a sophisticated phishing email. RDP (remote desktop protocol) Phishing email Web applications Infected thumb drive Exploit kit Malvertising Compromised websites Ransomware can infect school networks in many ways. 0% 1 Cybercrime Tactics and Techniques: Ransomware Retrospective, August 2019 2 https://www.infosecurity-magazine.com/news/hundreds-of-us-schools-hit-by/ Barracuda Networks • SOLUTION BRIEF • Ransomware: Prevention and Recovery in K-12 Environments Effective ransomware protection requires a three-pronged approach: 1. -

Guidelines on Firewalls and Firewall Policy
Special Publication 800-41 Revision 1 Guidelines on Firewalls and Firewall Policy Recommendations of the National Institute of Standards and Technology Karen Scarfone Paul Hoffman NIST Special Publication 800-41 Guidelines on Firewalls and Firewall Revision 1 Policy Recommendations of the National Institute of Standards and Technology Karen Scarfone Paul Hoffman C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 September 2009 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Deputy Director GUIDELINES ON FIREWALLS AND FIREWALL POLICY Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-41 Revision 1 Natl. Inst. Stand. Technol. Spec. Publ. 800-41 rev1, 48 pages (Sep. 2009) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -

BIG-IP Advanced Web Application Firewall
F5 Advanced WAF DATA SHEET What’s Inside Proactive Application Protection 2 Key benefits 3 Ensure Comprehensive Applications are critical to your business. Without the right protection, however, they can Threat Protection become an attack vector that may ultimately lead to a data breach. Consider this alarming statistic: Organizations have an average of 765 web applications and these applications 7 Streamline Learning, are the initial target of data breaches 53% of the time.1 Deployment, and Management Protect your organization and its reputation by maintaining the confidentiality, availability, and performance of the applications that are critical to your business with F5® Web 8 Leverage Rich, Application Firewall (WAF) solutions. Actionable Reporting F5 WAF solutions are deployed in more data centers than any enterprise WAF on the 10 Meet Complex market. The comprehensive suite of F5 WAF solutions includes managed rulesets for Deployment Amazon Web Services (AWS); cloud-based, self-service, and managed service in the Requirements F5 Silverline® cloud-based service delivery platform; application delivery controller (ADC) integration with F5 BIG-IP® Application Security Manager™ (ASM)2; and F5 Advanced 11 F5 Security Services Web Application Firewall™ (Advanced WAF). 12 F5 Advanced WAF Advanced WAF redefines application security to address the most prevalent threats Features and organizations face today: Specifications • Automated attacks and bots that overwhelm existing security solutions. • 14 F5 Advanced WAF Web attacks that steal credentials and gain unauthorized access across user accounts. • Application layer attacks that evade static security based on reputation and 14 BIG-IP Platforms manual signatures. 15 Virtual Editions • New attack surfaces and threats due to the rapid adoption of APIs. -

Application Firewalls for Different Protocols
Application Firewalls For Different Protocols Cannular and furibund Rafe wised her predicament ballon freeze-dries and outtell militarily. Quintillionth Rayner sometimes maroon any Walthamstow volplaning vehemently. Beardless Dickey pop, his quadrellas dreads fumigate ochlocratically. The latest firmware without disrupting your infrastructure that, the highest layer firewalls of any other networks or other data using different application firewalls abstract this policy for What is Digital Certificate? Waf rules can download. It incorporates packet, for example, Mohsen and Ramtin Aryan. As new exploits of different types of the differences between various products generate instant access. Inbound traffic containing IP Source Routing information. Aws waf for protocol exploits and route it different network security at. The differences between networks have a firewall, delivers an srx series device. WAFs do introduce traffic latency. Now available for protocol omain boundary equipped to applicable to deploy and threat intelligence. Web server, the stateful firewall might send busy home and maintaining the state table, might no additional configuration needed. In along, or by ecause of dignity, the firewall has high visibility into suspicious traffic to help if control your network. Cron job scheduler for task automation and management. When a firewall platform for firewalls, os x adds an informative webpage authentication as integral part of that application firewalls protocols for example if you? Analytics and collaboration tools for the powerful value chain. Like home and what to different application protocols for firewalls with existing connection and secure than the. The differences when threat visibility across hybrid firewall rules for building applications which should be outwitted by blocking legitimate apps behind traditional intrusion. -

Importance of Web Application Firewall Technology for Protecting Web-Based Resources
Importance of Web Application Firewall Technology For Protecting Web-based Resources Importance of Web Application Firewall Technology for Protecting Web-based Resources By Andrew J. Hacker, CISSP, ISSAP Senior Security Analyst, ICSA Labs January 10, 2008 ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg, PA 17050 Copyright © 2008 Cybertrust, Inc. All Rights Reserved. Page 1 of 7 Importance of Web Application Firewall Technology For Protecting Web-based Resources Importance of Web Application Firewall Technology for Protecting Web-based Resources By Andrew J. Hacker, CISSP, ISSAP Introduction Web-based applications and services have changed the landscape of information delivery and exchange in today’s corporate, government, and educational arenas. Ease of access, increased availability of information, and the richness of web services have universally increased productivity and operational efficiencies. These increases have led to heavier reliance on web-based services and greater integration of internal information systems and data repositories with web-facing applications. While motivations of attackers against a victim’s corporate and organizational assets remain the same (financial, IP, identity theft, services disruption, or denial of service, for example), web applications enable a whole new class of vulnerabilities and exploit techniques such as SQL injection, cross-site scripting (XSS), and cross-site request forgery, to name a few.1 The complexity of services, potential severity of breaches, and mounting sophistication of attacks requires additional functionality beyond the capability of traditional network-based security products. The emergence of dedicated web application firewall technology provides a comprehensive and focused solution to help increase the security of web-based services and protect valuable information assets. -

WAF-A-Mole: Evading Web Application Firewalls Through Adversarial Machine Learning
WAF-A-MoLE: Evading Web Application Firewalls through Adversarial Machine Learning Luca Demetrio Andrea Valenza [email protected] [email protected] Università di Genova Università di Genova Gabriele Costa Giovanni Lagorio [email protected] [email protected] IMT School for Advanced Studies Lucca Università di Genova ABSTRACT 1 admin ' OR 1=1# Web Application Firewalls are widely used in production envi- 2 admin ' OR 0X1 =1 or 0x726!=0x726 OR 0 x1Dd ronments to mitigate security threats like SQL injections. Many not IN /*(seleCt0X0)>c^Bj>N]*/(( SeLeCT industrial products rely on signature-based techniques, but ma- 476) ,( SELECT ( SElEct 477)),0X1de) oR chine learning approaches are becoming more and more popular. 8308 noT lIkE 8308\ x0c AnD truE OR ' The main goal of an adversary is to craft semantically malicious FZ6/q' LiKE 'fz6/qI ' anD TRUE anD '>U' payloads to bypass the syntactic analysis performed by a WAF. != '>uz '#t'%'03; Nd In this paper, we present WAF-A-MoLE, a tool that models the presence of an adversary. This tool leverages on a set of muta- tion operators that alter the syntax of a payload without affecting Figure 1: Two semantically equivalent payloads. the original semantics. We evaluate the performance of the tool against existing WAFs, that we trained using our publicly available SQL query dataset. We show that WAF-A-MoLE bypasses all the possible exploitation patterns, e.g., payloads carrying a SQL injec- considered machine learning based WAFs. tion. Since WAFs work at application-level, they have to deal with KEYWORDS highly expressive languages such as SQL and HTML. -

Web Application Firewall L100
Web Application Firewall L100 Flavio Pereira Oracle Cloud Infrastructure October 2019 Safe harbor statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, timing, and pricing of any features or functionality described for Oracle’s products may change and remains at the sole discretion of Oracle Corporation. Objectives After completing this lesson, you should be able to: • Understand WAF concepts and use cases • Describe the OCI WAF Service • Explain OCI WAF capabilities and architecture • Show a demo of OCI WAF WAF Concepts and Use Cases What is a Web Application Firewall? • Web Application Firewall (WAF) refers to a device, server-side plugin, or filter that applies a set of rules to HTTP/S traffic • By intercepting HTTP/S traffic and passing them through a set of filters and rules, WAF is able to uncover and protect against attack streams hitting a web application • Generally, these rules cover common attacks such as Cross-site Scripting (XSS) and SQL Injection in addition to giving customers the ability to filter specific source IPs or bad bots • Typical responses from WAF will either be allowing the request to pass through, audit logging the request, or blocking the request by responding with an error page. OCI Web Application Firewall OCI Web Application Firewall -

• Web Application Firewall Data Security Solutions Cloud Firewall
• Web Application Firewall Data Security Solutions Cloud Firewall PORTAFOLIO DE PRODUCTOS Seguridad para la Nube Cloud is just another IT Deployment Model Private Cloud Public Cloud Physical Virtual (On-Premise) (Off-Premise) Appl Appl Appl OS Appl Appl OS OS Appl OS OS HW OS HW VMWARE. HW HARDWARE Virtualization, Owned and Resources on Traditional better operated by demand and enterprise utilization organization pay-per-use And it requires Equivalent Protections PROTECT PROTECT the communication PROTECT virtual servers between virtual and corporate data against attacks physical servers Public Cloud Web Application Firewall Barracuda Web Application Firewall: Protección Completa de Aplicaciones Web Data Loss Prevention Application Security (L7) Proactive Defenses Credit Card Numbers OWASP Top-10 Attacks Application Cloaking SSN Numbers Geo-IP Control Application DDOS Custom Patterns Outbound Inspection Inbound Inspection Barracuda Web Application Firewall Protección de Ataques Prevención de Fuga de Datos Aceleración Attack Protection Brute Force Protection • SQL, XSS, command injection DoS Protection CSRF IP Reputation Blocking Web Site Cloaking • Blocking by Geo IP • Anonymous Proxy Blocking Data Theft Protection • Credit card, SSN, custom patterns Armored Browser Integration Session Protection XML Firewall • XML schema enforcement • Cookie encryption • Web services security • Parameter tampering protection SIEM Integration Integrated Anti-Virus Modificación de Código y Control Modo de Implementación IaaS/PaaS Automatically scales