The Technology of Programming for a Cluster Computer by the Remote Terminal with Os Windows
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Muuglines the Manitoba UNIX User Group Newsletter
MUUGLines The Manitoba UNIX User Group Newsletter Volume 28 No. 10, June 2016 Editor: Bradford C. Vokey Next Meeting: June 14th, 2016, )here to Find the Meeting 7:30 pm University of Winnipeg Room 1M28 Manitoba Hall Main Topic: Gentoo Eric Raine will be presenting on the Gentoo Linux Dist. Differ- ences in installation from Ubuntu will be covered. Also covered is how to configure installation of packages and update. entoo is a free operating s!stem based on either Linux or Free#$D that can be automaticall! optimi%ed and customized for just about any applic- ation or need. RTFM: Termina Control Commands Due to a recent influx of new and novice members 'revor Cordes will be doing an R'") instead of a daemon dash this month. The topic is something ever! *+,- user should master. terminal control commands (i.e.0 ^2 and ^L3 and rudimentar! job control. These little dual ke! presses will streamline !our terminal sessions and make you more efficient. 4ou5ll wonder how you ever got b! without them6 Door %rize'#( )eetings are held in the University of Winnipeg's 'his month we will be giving )anitoba Hall (marked “M” on the map30 along awa! the O8Reill! book #almoral Street south of Ellice Avenue. We can be "Using csh & tcsh"0 found in room 1)@A0 but may occasionall! get b! Paul Du#ois. relocated to nearb! rooms. If there is a change0 it should be conve!ed via a sign on the door to 1)@A. Type Less, Accomplish More. Doors are usuall! open b! 7.CC pm with the meeting starting at 7.DC pm. -

Beyond Compare User Guide
Copyright © 2012 Scooter Software, Inc. Beyond Compare Copyright © 2012 Scooter Software, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Published: July 2012 Contents 3 Table of Contents Part 1 Welcome 7 1 What's. .N..e..w............................................................................................................................. 8 2 Standa..r.d.. .v..s. .P..r..o..................................................................................................................... 9 Part 2 Using Beyond Compare 11 1 Home. .V...i.e..w.......................................................................................................................... -

17.06.10 Release Total Commander 7.55 Final 16.06.10 Fixed
17.06.10 Release Total Commander 7.55 final 16.06.10 Fixed: Internal unpack function didn't ask to overwrite target if the t arget directory allowed to write, but not to list the directory contents 16.06.10 Fixed: Do not use CONNECT_PROMPT option for UNC servers in the form \\s erver, only for shares 16.06.10 Fixed: If PromptForUser=1, do not call connect function if already conn ected (check via WNetGetUser) 16.06.10 Fixed: cd \\server\share /user: didn't work on the command line 15.06.10 Release Total Commander 7.55 final (pre2) 15.06.10 Added: Call network connect function with CONNECT_PROMPT option to prom pt for user name: wincmd.ini [Configuration] PromptForUser=1 15.06.10 Fixed: FTP: When "Send commands" also contained a CWD command, reconnec ting to an ftp server via history went to that directory instead of the director y in the history 14.06.10 Fixed: Problems with tabs when an ftp connection was saved with "@" cha racter in its name (TC tries to reconnect on each tab change) 13.06.10 Added: "cd" command in button bar and user menu: When parameter /user: is added without giving a user name, call connect function with CONNECT_PROMPT o ption to prompt for user name 13.06.10 Fixed: Look for key file also under %LOCALAPPDATA%\VirtualStore on Wind ows Vista/7 if TC is installed in "Program files" dir (reason: some older mail p rograms may store the key there!) 13.06.10 Fixed: FTP Upload: File was appended instead of overwritten if the conn ection was lost before starting the transfer (e.g. -

Hwb: the Hardware Book (Offline)
HwB: The Hardware Book (Offline) Welcome to the Hardware Book. Internet's largest free collection of connector pinouts and cable descriptions. Newsflash! A new version of The Hardware Book has been released as of 2001-06-08! See News for more details. This is an offline version, the latest release of HwB can be found at http://www.hardwarebook.net/. Connectors Pinouts for connectors, buses etc. Cables How to build serial cables and many other cables. Adapters How to build adapters. Circuits Misc circuits (active filters etc). Tables Misc tables with info. (AWG..) WWW Links Links to other electronic resources. News News information about The Hardware Book. Wanted Information we are currently looking for. About Who did this? And why? Comment Send your comments to the author. Copyright © The Hardware Book Team 1996-2001. May be copied and redistributed, partially or in whole, as apropriate. Document last modified: 2001-06-08 file:///C|/tmp/tech/HwB/index.html [6/14/2001 11:59:19 PM] HwB: Connector Menu (Offline) [ Audio/Video | Buses | Cartridges/Expansions | Cellular Phones | Memories | Misc | Networks | Parallel | PC | Power Supply | Serial | Storage | Mice/Keyboards/Joysticks ] What does the information that is listed for each connector mean? See the tutorial. Audio/Video Audio ActionMedia 2 Audio/Video Capture Amiga 1000 RF Monitor Apple AudioVision CBM 1902A NeoGeo Audio/Video Sony RGB Multi Input TI-99/4A Video/Audio Consoles Atari Jaguar A/V N64 Video PlayStation A/V Sega Dreamcast A/V Sega Genesis 2/32X/Nomad A/V Sega Genesis/Master -

Introducción a Linux Equivalencias Windows En Linux Ivalencias
No has iniciado sesión Discusión Contribuciones Crear una cuenta Acceder Página discusión Leer Editar Ver historial Buscar Introducción a Linux Equivalencias Windows en Linux Portada < Introducción a Linux Categorías de libros Equivalencias Windows en GNU/Linux es una lista de equivalencias, reemplazos y software Cam bios recientes Libro aleatorio análogo a Windows en GNU/Linux y viceversa. Ayuda Contenido [ocultar] Donaciones 1 Algunas diferencias entre los programas para Windows y GNU/Linux Comunidad 2 Redes y Conectividad Café 3 Trabajando con archivos Portal de la comunidad 4 Software de escritorio Subproyectos 5 Multimedia Recetario 5.1 Audio y reproductores de CD Wikichicos 5.2 Gráficos 5.3 Video y otros Imprimir/exportar 6 Ofimática/negocios Crear un libro 7 Juegos Descargar como PDF Versión para im primir 8 Programación y Desarrollo 9 Software para Servidores Herramientas 10 Científicos y Prog s Especiales 11 Otros Cambios relacionados 12 Enlaces externos Subir archivo 12.1 Notas Páginas especiales Enlace permanente Información de la Algunas diferencias entre los programas para Windows y y página Enlace corto GNU/Linux [ editar ] Citar esta página La mayoría de los programas de Windows son hechos con el principio de "Todo en uno" (cada Idiomas desarrollador agrega todo a su producto). De la misma forma, a este principio le llaman el Añadir enlaces "Estilo-Windows". Redes y Conectividad [ editar ] Descripción del programa, Windows GNU/Linux tareas ejecutadas Firefox (Iceweasel) Opera [NL] Internet Explorer Konqueror Netscape / -

LINUX: Rute User's Tutorial and Exposition
LINUX: Rute User’s Tutorial and Exposition Paul Sheer August 14, 2001 Pages up to and including this page are not included by Prentice Hall. 2 “The reason we don’t sell billions and billions of Guides,” continued Harl, after wiping his mouth, “is the expense. What we do is we sell one Guide billions and billions of times. We exploit the multidimensional nature of the Universe to cut down on manufacturing costs. And we don’t sell to penniless hitchhikers. What a stupid notion that was! Find the one section of the market that, more or less by definition, doesn’t have any money, and try to sell to it. No. We sell to the affluent business traveler and his vacationing wife in a billion, billion different futures. This is the most radical, dynamic and thrusting business venture in the entire multidimensional infinity of space-time-probability ever.” ... Ford was completely at a loss for what to do next. “Look,” he said in a stern voice. But he wasn’t certain how far saying things like “Look” in a stern voice was necessarily going to get him, and time was not on his side. What the hell, he thought, you’re only young once, and threw himself out of the window. That would at least keep the element of surprise on his side. ... In a spirit of scientific inquiry he hurled himself out of the window again. Douglas Adams Mostly Harmless Strangely, the thing that least intrigued me was how they’d managed to get it all done. I suppose I sort of knew. -

Enhanced Networking on IBM Z/VSE
Front cover Enhanced Networking on IBM z/VSE Use LFP on Z/VM and in LPAR for selected applications Experience the benefits of OpenSSL Learn how to use IPv6 on z/VSE Joerg Schmidbauer Jeffrey Barnard Ingo Franzki Karsten Graul Don Stoever Rene Trumpp ibm.com/redbooks International Technical Support Organization Enhanced Networking on IBM z/VSE December 2014 SG24-8091-01 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. Second Edition (December 2014) This edition (SG24-8091-01) applies to z/VSE V5 R2. © Copyright International Business Machines Corporation 2014. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi The team who wrote this book . xi Now you can become a published author, too! . xii Comments welcome. xii Stay connected to IBM Redbooks . xiii IBM Redbooks promotions . .xv Summary of changes. xvii December 2014, Second Edition . xvii Chapter 1. Networking options overview . 1 1.1 Overview . 2 1.2 Hardware options . 2 1.2.1 OSA-Express . 2 1.2.2 OSA-Integrated Console Controller . 3 1.2.3 OSA-Express in QDIO mode . 4 1.2.4 OSA-Express . 5 1.2.5 OSA for NCP support . 5 1.2.6 Intra-Ensemble Data Network support . 6 1.2.7 OSA-Express multi-port support . 7 1.2.8 Using VTAM (SNA) and TCP/IP (non-QDIO) parallel on the same CHPID . 8 1.2.9 HiperSockets (IQD). -

CIT381 COURSE TITLE: File Processing and Management
NATIONAL OPEN UNIVERSITY OF NIGERIA SCHOOL OF SCIENCE AND TECHNOLOGY COURSE CODE: CIT381 COURSE TITLE: File Processing and Management CIT381 COURSE GUIDE COURSE GUIDE CIT381 FILE PROCESSING AND MANAGEMENT Course Team Ismaila O. Mudasiru (Developer/Writer) - OAU NATIONAL OPEN UNIVERSITY OF NIGERIA ii CIT381 COURSE GUIDE National Open University of Nigeria Headquarters 14/16 Ahmadu Bello Way Victoria Island Lagos Abuja Office No. 5 Dar es Salaam Street Off Aminu Kano Crescent Wuse II, Abuja Nigeria e-mail: [email protected] URL: www.nou.edu.ng Published By: National Open University of Nigeria First Printed 2011 ISBN: 978-058-525-7 All Rights Reserved CONTENTS PAGE iii CIT381 COURSE GUIDE Introduction …………………..…………………………………… 1 What You Will Learn in this Course………………………………. 1 Course Aims ………………………………………………………. 2 Course Objectives …………………………………………………. 2 Working through this Course………………………….…………… 3 The Course Materials………………………………………………. 3 Study Units…………………………………………………………. 3 Presentation Schedule……………….……………………………… 4 Assessment…………………………………………………………. 5 Tutor-Marked Assignment…………………………………………. 5 Final Examination and Grading……………………………………. 6 Course Marking Scheme…………………………………………… 6 Facilitators/Tutors and Tutorials…………………………………… 6 Summary…………………………………………………………… 7 iv CIT381 FILE PROCESSING AND MANAGEMENT Introduction File Processing and Management is a second semester course. It is a 2- credit course that is available to students offering Bachelor of Science, B. Sc., Computer Science, Information Systems and Allied degrees. Computers can store information on several different types of physical media. Magnetic tape, magnetic disk and optical disk are the most common media. Each of these media has its own characteristics and physical organisation. For convenience use of the computer system, the operating system provides a uniform logical view of information storage. The operating system abstracts from the physical properties of its storage devices to define a logical storage unit, the file. -
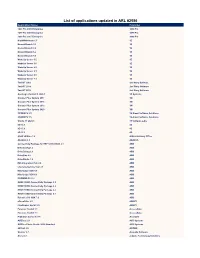
List of Applications Updated in ARL #2586
List of applications updated in ARL #2586 Application Name Publisher 1099 Pro 2005 Enterprise 1099 Pro 1099 Pro 2006 Enterprise 1099 Pro 1099 Pro 2007 Enterprise 1099 Pro NightWatchman 6.5 1E Nomad Branch 5.2 1E Nomad Branch 6.0 1E Nomad Branch 6.2 1E Nomad Branch 6.3 1E WakeUp Server 5.5 1E WakeUp Server 5.6 1E WakeUp Server 6.0 1E WakeUp Server 6.1 1E WakeUp Server 6.5 1E WakeUp Server 7.1 1E TaxACT 2002 2nd Story Software TaxACT 2014 2nd Story Software TaxACT 2018 2nd Story Software Geomagic Control X 2020.1 3D Systems Grouper Plus System 2017 3M Grouper Plus System 2018 3M Grouper Plus System 2019 3M Grouper Plus System 2020 3M CODESYS 2.3 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions Studio 3T 2020.9 3T Software Labs 4D 15.1 4D 4D 15.3 4D 4D 16.3 4D ASAP Utilities 7.8 A Must in Every Office AbaStart 2.5 ABACUS Connectivity Package for REF 541/543/545 2.1 ABB DriveConfig 1.2 ABB DriveDebug 2.9 ABB DriveSize 4.9 ABB DriveStudio 1.5 ABB IMS Integration Hub 2.8 ABB Lifecycle Service Tool 2.1 ABB MineScape SDK 5.1 ABB MineScape SDK 6.1 ABB PROMOD IV 11.2 ABB REM615 IED Connectivity Package 2.1 ABB REM615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 5.1 ABB Robotics PC SDK 7.0 ABB eFormFiller 2.5 ABBYY FineReader Sprint 5.0 ABBYY Forensic Toolkit 7.1 AccessData Forensic Toolkit 7.1 AccessData PrizmDoc Server 13.14 AccuSoft ACDSee 2.0 ACD Systems ACDSee Photo Studio 2019 Standard ACD Systems dBTrait 5.5 ACOEM Soulver 2.7 Acqualia Software Arena 4.1 acQuire -

Introduction to Linux
Introduction to Linux A Hands on Guide Machtelt Garrels CoreSequence.com <[email protected]> Version 1.8 Last updated 20030916 Edition Introduction to Linux Table of Contents Introduction.........................................................................................................................................................1 1. Why this guide?...................................................................................................................................1 2. Who should read this book?.................................................................................................................1 3. New versions of this guide...................................................................................................................1 4. Revision History..................................................................................................................................1 5. Contributions.......................................................................................................................................2 6. Feedback..............................................................................................................................................2 7. Copyright information.........................................................................................................................3 8. What do you need?...............................................................................................................................3 9. Conventions used -

List Software Pengganti Windows Ke Linux
Tabel Padanan Aplikasi Windows di Linux Untuk Migrasi Selasa, 18-08-2009 Kesulitan besar dalam melakukan migrasi dari Windows ke Linux adalah mencari software pengganti yang berkesesuaian. Berikut ini adalah tabel padanan aplikasi Windows di Linux yang disusun dalam beberapa kategori. Nama Program Windows Linux 1) Networking. 1) Netscape / Mozilla. 2) Galeon. 3) Konqueror. 4) Opera. [Prop] Internet Explorer, 5) Firefox. Web browser Netscape / Mozilla, Opera 6) Nautilus. [Prop], Firefox, ... 7) Epiphany. 8) Links. (with "-g" key). 9) Dillo. 10) Encompass. 1) Links. 1) Links 2) ELinks. Console web browser 2) Lynx 3) Lynx. 3) Xemacs + w3. 4) w3m. 5) Xemacs + w3. 1) Evolution. 2) Netscape / Mozilla/Thunderbird messenger. 3) Sylpheed / Claws Mail. 4) Kmail. Outlook Express, 5) Gnus. Netscape / Mozilla, 6) Balsa. Thunderbird, The Bat, 7) Bynari Insight GroupWare Suite. Email client Eudora, Becky, Datula, [Prop] Sylpheed / Claws Mail, 8) Arrow. Opera 9) Gnumail. 10) Althea. 11) Liamail. 12) Aethera. 13) MailWarrior. 14) Opera. 1) Evolution. Email client / PIM in MS 2) Bynari Insight GroupWare Suite. Outlook Outlook style [Prop] 3) Aethera. 4) Sylpheed. 5) Claws Mail 1) Sylpheed. 2) Claws Mail Email client in The Bat The Bat 3) Kmail. style 4) Gnus. 5) Balsa. 1) Pine. [NF] 2) Mutt. Mutt [de], Pine, Pegasus, Console email client 3) Gnus. Emacs 4) Elm. 5) Emacs. 1) Knode. 2) Pan. 1) Agent [Prop] 3) NewsReader. 2) Free Agent 4) Netscape / Mozilla Thunderbird. 3) Xnews 5) Opera [Prop] 4) Outlook 6) Sylpheed / Claws Mail. 5) Netscape / Mozilla Console: News reader 6) Opera [Prop] 7) Pine. [NF] 7) Sylpheed / Claws Mail 8) Mutt.