Algorithmic Jim Crow
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
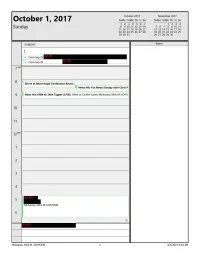
October 1, 2017
October 2017 November 2017 October 1, 2017 SuMo TuWe Th Fr Sa SuMo TuWe Th Fr Sa 1 2 3 4 S 6 7 1 2 3 4 Sunday 8 9 10 11 1213 14 5 6 7 8 9 10 11 15 16 17 18 19 20 21 12 13 14 15 16 17 18 22 23 24 25 26 27 28 19 20 21 22 23 24 25 29 30 31 26 27 28 29 30 SUNDAY Notes 1 From Sep 29 From Sep 29 8 F rive at Mont Royal Conference Room] ~ ews Hit: Fox News Sunday with Ch~ I 9 News Hit: CNN w/ Jake Tapper (LIVE); Hotel Le Candie Suites; Mulvaney, Mick M. EOP/ C 10 11 1 2 3 4 5 Mu vaney, Mick M. EOP/ OMB 6 Mulvaney, Mick M. EOP/OMB 1 4/ 1/ 2019 9:03 AM October 2017 November 2017 October 2, 2017 SuMo TuWe Th Fr Sa SuMo TuWe Th Fr Sa 1 2 3 4 S 6 7 1 2 3 4 Monday 8 9 10 11 1213 14 5 6 7 8 9 10 11 15 16 17 18 19 20 21 12 13 14 15 16 17 18 22 23 24 25 26 27 28 19 20 21 22 23 24 25 29 30 31 26 27 28 29 30 MONDAY Notes 2 Deregulation Day (TBD - White House) - Mulvaney, Mick M. EOP/ OMB No Greater Sacrifice Congressional Shoot-Out (Blue Course) - Mulvaney, John M. 8 9 l~ one Call w/ Sec. Mnuchin; He will 4 1 9:30am Puerto Rico Trip Prep Meeting; VI 10 Prep: Flood Insurance Principals Meeting; EEOB 2S2; Mulvaney, Mick M. -

Politics Book Discussion Guide
One Book One Northwestern Book Group Discussion Politics Politics ¡ How do you think someone’s political affiliation (Republican, Democrat, Green, Libertarian, Independent, etc.) may affect his or her analysis of the likelihood of certain world events? When have you seen this happen in real life? ¡ E.g. elections, wars, trade deals, environmental policy, etc. ¡ How can someone manage his or her own biases when making political predictions? Use your ideas and Silver’s. ¡ This election cycle has had a series of anomalies, especially regarding the race for and selection of presidential candidates. ¡ What specific anomalies have you noticed in this election cycle? ¡ How can political analysts factor in the possibility of anomalies in their predictions, given that there is no model to look back on that incorporates these anomalies? Politics ¡ In May 2016, Nate Silver published a blog post called “How I Acted Like A Pundit And Screwed Up On Donald Trump.” In the post, he lists reasons for why he incorrectly predicted that Trump would not win the Republican nomination for President, including that he ignored polls in favor of “educated guesses.” Harry Enten, a senior analyst at Nate Silver’s website FiveThirtyEight, describes more of this problem in an interview with This American Life. ¡ Why do you think Silver and his team ignored polls in this case, when they have relied on them heavily in the past? ¡ How do you think Silver’s predictions would have turned out differently if he had taken polls into consideration? ¡ Do you think Silver’s personal biases regarding the presidential candidate influenced his decisions when making his predictions? Why or why not? Politics: Case Study ¡ The Context: In July 2016, Supreme Court Justice Ruth Bader Ginsburg was criticized for making public statements about the unfitness of presidential candidate Donald Trump. -

Invisible Forces: Portraits of Instructional Approaches to Mindset Development in Secondary and Postsecondary Writing Classes
Invisible Forces: Portraits of Instructional Approaches to Mindset Development in Secondary and Postsecondary Writing Classes The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Liu, Pei Pei. 2019. Invisible Forces: Portraits of Instructional Approaches to Mindset Development in Secondary and Postsecondary Writing Classes. Doctoral dissertation, Harvard Graduate School of Education. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:42081668 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Invisible Forces: Portraits of Instructional Approaches to Mindset Development in Secondary and Postsecondary Writing Classes Pei Pei Liu Mandy Savitz-Romer Karen Brennan Sara Lawrence-Lightfoot A Thesis Presented to the Faculty of the Graduate School of Education of Harvard University in Partial Fulfillment of the Requirements for the Degree of Doctor of Education 2019 © 2019 Pei Pei Liu All Rights Reserved i For my father 劉 志 隆 1942-2018 ii Acknowledgments I am indebted to so many for this work. First and foremost, I thank my parents, Triung Yueh Yang and Shih-Long Liu, who always put their three kids first and, in raising us outside of their birth country, conquered challenges that I did not fully appreciate until far too late into adulthood. I try to enact my gratitude for what you have given me by working for the benefit of others. -

Special Edition
2017 Dr. Martin Luther King Jr. ‘City of Roses’ Special Edition www.portlandobserver.com Established in 1970 Volume XLVI • Number 2 Wednesday • January 11, 2017 Committed to Cultural Diversity Page 2 MARTIN LUTHER KING JR. January 11, 2017 2017 special edition Kate Brown Sworn In versity is not a threat; it is, in fact Making it clear The our greatest strength,” Merkley that the fight for Week said. equality will not in PCC Chair Quits Post retreat after the Review The chair of Portland Communi- most bitter and ty College board has resigned to divisive national ple with disabilities because of protest a recent decision to make election in mem- $338 in back due rent. the college a sanctuary campus. ory, Kate Brown Bracing for More Snow Gene Pitts said his concern was was sworn in to her first full term Just as Portland began to thaw for students losing their feder- as governor of Oregon Monday. In out from a weekend of snow and al Pell grants, should the federal her speech, she outlined plans to freezing rain, a new storm front is government under the Trump ad- address job creation, reforming Or- expected to hit the city overnight ministration penalize sanctuary egon’s tax system, public transpor- Tuesday into Wednesday morn- designations that deny federal im- tation funding, passing gun control ing, bringing an accumulation of migration enforcement. legislation and expanding the state’s 1-4 inches of snow. Medicaid program for all children. Viola Davis Honored Third Hypothermia Death Merkley Wants Registry Ban “Moonlight,” the critically and U.S. -

A Giant Whiff: Why the New CBA Fails Baseball's Smartest Small Market Franchises
DePaul Journal of Sports Law Volume 4 Issue 1 Summer 2007: Symposium - Regulation of Coaches' and Athletes' Behavior and Related Article 3 Contemporary Considerations A Giant Whiff: Why the New CBA Fails Baseball's Smartest Small Market Franchises Jon Berkon Follow this and additional works at: https://via.library.depaul.edu/jslcp Recommended Citation Jon Berkon, A Giant Whiff: Why the New CBA Fails Baseball's Smartest Small Market Franchises, 4 DePaul J. Sports L. & Contemp. Probs. 9 (2007) Available at: https://via.library.depaul.edu/jslcp/vol4/iss1/3 This Notes and Comments is brought to you for free and open access by the College of Law at Via Sapientiae. It has been accepted for inclusion in DePaul Journal of Sports Law by an authorized editor of Via Sapientiae. For more information, please contact [email protected]. A GIANT WHIFF: WHY THE NEW CBA FAILS BASEBALL'S SMARTEST SMALL MARKET FRANCHISES INTRODUCTION Just before Game 3 of the World Series, viewers saw something en- tirely unexpected. No, it wasn't the sight of the Cardinals and Tigers playing baseball in late October. Instead, it was Commissioner Bud Selig and Donald Fehr, the head of Major League Baseball Players' Association (MLBPA), gleefully announcing a new Collective Bar- gaining Agreement (CBA), thereby guaranteeing labor peace through 2011.1 The deal was struck a full two months before the 2002 CBA had expired, an occurrence once thought as likely as George Bush and Nancy Pelosi campaigning for each other in an election year.2 Baseball insiders attributed the deal to the sport's economic health. -

Political Journalists Tweet About the Final 2016 Presidential Debate Hannah Hopper East Tennessee State University
East Tennessee State University Digital Commons @ East Tennessee State University Electronic Theses and Dissertations Student Works 5-2018 Political Journalists Tweet About the Final 2016 Presidential Debate Hannah Hopper East Tennessee State University Follow this and additional works at: https://dc.etsu.edu/etd Part of the American Politics Commons, Communication Technology and New Media Commons, Gender, Race, Sexuality, and Ethnicity in Communication Commons, Journalism Studies Commons, Political Theory Commons, Social Influence and Political Communication Commons, and the Social Media Commons Recommended Citation Hopper, Hannah, "Political Journalists Tweet About the Final 2016 Presidential Debate" (2018). Electronic Theses and Dissertations. Paper 3402. https://dc.etsu.edu/etd/3402 This Thesis - Open Access is brought to you for free and open access by the Student Works at Digital Commons @ East Tennessee State University. It has been accepted for inclusion in Electronic Theses and Dissertations by an authorized administrator of Digital Commons @ East Tennessee State University. For more information, please contact [email protected]. Political Journalists Tweet About the Final 2016 Presidential Debate _____________________ A thesis presented to the faculty of the Department of Media and Communication East Tennessee State University In partial fulfillment of the requirements for the degree Master of Arts in Brand and Media Strategy _____________________ by Hannah Hopper May 2018 _____________________ Dr. Susan E. Waters, Chair Dr. Melanie Richards Dr. Phyllis Thompson Keywords: Political Journalist, Twitter, Agenda Setting, Framing, Gatekeeping, Feminist Political Theory, Political Polarization, Presidential Debate, Hillary Clinton, Donald Trump ABSTRACT Political Journalists Tweet About the Final 2016 Presidential Debate by Hannah Hopper Past research shows that journalists are gatekeepers to information the public seeks. -

Silver, Nate (B
Silver, Nate (b. 1978) by Linda Rapp Encyclopedia Copyright © 2015, glbtq, Inc. Entry Copyright © 2013 glbtq, Inc. Reprinted from http://www.glbtq.com Statistical analyst Nate Silver first came to wide public attention in 2008, when he correctly predicted the outcome of the presidential election in 49 out of 50 states and also forecast accurate results for all of the 35 races for the United States Senate. He achieved a similar rate of success in 2012, that time getting the call of the vote for president right in every state. Nathaniel Silver is the son of Brian Silver, a professor of political science at Michigan State University, and Sally Silver, a community activist. He was born in East Lansing on January 13, 1978. Nate Silver. Photograph by Randy Stewart. Sally Silver described her son to Patricia Montemurri of the Detroit Free Press as a Image appears under the "very precocious youngster who quickly became an avid reader but even sooner Creative Commons showed an uncanny aptitude for mathematics. By the age of four, he could perform Attribution-Share Alike multiplication of double-digit numbers in his head" and had also grasped the concept 2.0 Generic license. of negative numbers. "My parents have always supported me tremendously," Nate Silver told Montemurri. "There was an emphasis on education and intellectual exploration. It was a household that had good values." The Silvers encouraged their son to pursue whatever interested him most, and this proved to include baseball. When his father took him to games at iconic Tiger Stadium in Detroit in 1984, he was swept up in the magic of that championship season and became a devoted fan of the team. -

"Islamophobia" in America
Episode 209- Dr. Omid Safi: “Islamophobia” in America [00:00:08] Welcome to inSocialWork the podcast series of the University of Buffalo School of Social Work at www.inSocialWork.org. We're glad you could join us today. The purpose of inSocialWork is to engage practitioners and researchers in lifelong learning and to promote research to practice and practice to research. We educate. We connect. We care. We're inSocialWork. [00:00:37] Hello and welcome to inSocialWork. I'm your host Charles Simms. Muslims have been part of the fabric of America for more than 500 years. There were likely Muslim members of Columbus's crew when they arrived in the American Hemisphere in 1492. Trans-Atlantic slavery would have certainly brought Africans who practice Islam to the developing United States. During the ratification of the United States Constitution concern was voiced that one day there could be a Muslim president yet in the early 1800s the Ramadan Fast was once ended in the White House. As one can see the history of Muslims in America is long and complicated. Today regrettably the word Muslim often engenders feelings of fear, anxiety, or anger. How did we get here? What does this mean for Muslims living in America? What should social workers know? In this podcast our guest Dr. Omid Safi examines the complex history of Muslims in America. In doing so his discussion helps us to more fully understand the term Islamophobia. He critiques how the fear of Muslims has under the guise of making America safe led to the resurgence of previously used tactics of state sponsored intrusions into our civil liberties and calls for strategies that violate human rights. -

Reflections on “The Signal & the Noise” by Nate Silver
Reflections on “The Signal & the Noise” by Nate Silver Nigel Marriott, MSc, Cstat, CSci Statistical Consultant www.marriott-stats.com September 2013 WARNING! Contains Plot Spoilers! RSS13, Newcastle www.marriott-stats.com The Signal & the Noise in a Nutshell • We are not very good at forecasting. • This is not because it is not possible to forecast • It is because we are human and we make human errors • We also fail to learn from our mistakes • The books contains 7 chapters illustrating the kind of mistakes we make • It then gives 6 chapters on how we can do better RSS13, Newcastle www.marriott-stats.com 7 Chapters of Errors (I) 1) Rating Agencies Risk Valuation of CDOs in 2007 ❑ CDOs were rated as AAA which implied P(Fail in 5yrs) = 1 in 850 ❑ By 2009, 28% of CDOs had failed, 200x expectations. ❑ Reasons include lack of history to model risk, lack of incentives to build quality models, failure to understand multivariate non-linear correlations. ❑ Essentially failure to appreciate OUT OF SAMPLE modelling risks. ❑ I had written about precisely this kind of risk in my MSC thesis in 1997. 2) Political Punditry and predicting 2008 US Presidential Election ❑ Pundits are either Foxes or Hedgehogs. ❑ Hedgehogs receive the publicity but Foxes are better forecasters. ❑ Foxes get better with experience, Hedgehogs get worse with time! ❑ “Where are the 1-handed statisticians & economists!?” ❑ I have always been happy to use multiple methods of forecasting. RSS13, Newcastle www.marriott-stats.com 7 Chapters of Errors (II) 3) Sport Forecasting (focus on Sabermetrics) ❑ At the time of “Moneyball” in 2003, sabermetricians were percieved as a threat to traditional scouts. -

Targeted Sampling from Massive Block Model Graphs with Personalized Pagerank∗
Targeted sampling from massive block model graphs with personalized PageRank∗ Fan Chen1, Yini Zhang2, and Karl Rohe1 1Department of Statistics 2School of Journalism and Mass Communication University of Wisconsin, Madison, WI 53706, USA Abstract This paper provides statistical theory and intuition for Personalized PageRank (PPR), a popular technique that samples a small community from a massive network. We study a setting where the entire network is expensive to thoroughly obtain or maintain, but we can start from a seed node of interest and \crawl" the network to find other nodes through their connections. By crawling the graph in a designed way, the PPR vector can be approximated without querying the entire massive graph, making it an alternative to snowball sampling. Using the degree-corrected stochastic block model, we study whether the PPR vector can select nodes that belong to the same block as the seed node. We provide a simple and interpretable form for the PPR vector, highlighting its biases towards high degree nodes outside of the target block. We examine a simple adjustment based on node degrees and establish consistency results for PPR clustering that allows for directed graphs. These results are enabled by recent technical advances showing the element-wise convergence of eigenvectors. We illustrate the method with the massive Twitter friendship graph, which we crawl using the Twitter API. We find that (i) the adjusted and unadjusted PPR techniques are complementary approaches, where the adjustment makes the results particularly localized around the seed node and (ii) the bias adjustment greatly benefits from degree regularization. Keywords Community detection; Degree-corrected stochastic block model; Local clustering; Network sampling; Personalized PageRank arXiv:1910.12937v2 [cs.SI] 1 Jul 2020 1 Introduction Much of the literature on graph sampling has treated the entire graph, or all of the people in it, as the target population. -

DAVID WASSERMAN Senior Election Analyst, the Cook Political Report and NBC Contributor
DAVID WASSERMAN Senior Election Analyst, The Cook Political Report and NBC Contributor David Wasserman is the U.S. House editor and senior election analyst for the non-partisan newsletter, The Cook Political Report, and a contributor to NBC News. Founded in 1984, The Cook Political Report provides analyses of U.S. presidential, Senate, House, and gubernatorial races. The New York Times called The Cook Political Report “a newsletter that both parties regard as authoritative.” Wasserman analyzes the current political environment in lively and entertaining presentations that he can tailor to his audiences’ specific interests or locales. His data-driven forecasting looks at both national and local trends (if requested, he can even do a district-by-district outlook), the relationship between consumer brand loyalty and voting, and what the future holds for American elections. He is exclusively represented by Leading Authorities speakers bureau. Highly-Praised Expertise. Nate Silver of FiveThirtyEight.com has written: “Wasserman’s knowledge of the nooks and crannies of political geography can make him seem like a local,” and the Los Angeles Times called Wasserman “whip smart” and a “scrupulously nonpartisan” analyst whose “numbers nerd-dom was foretold at a young age.” Chuck Todd, host of NBC's Meet the Press, recently called David "pretty much the only person you need to follow on Election Night." In 2016, Wasserman drew wide praise for his accurate pre-election analysis, including his uncanny September piece entitled, “How Trump Could Win the White House While Losing the Popular Vote.” Leading Republican pollster Kristen Soltis Anderson concluded, “Nobody of my generation knows American politics as well as Dave Wasserman.” Political Intelligence. -

The Grifters, Chapter 3 – Election Prediction November 9, 2020
The Grifters, Chapter 3 – Election Prediction November 9, 2020 That’s Nate Silver, founder and face of election “modeler” FiveThirtyEight, performing his traditional “Awkshually, we weren’t wrong” dance after mangling yet another national election. Haha. No, that’s a falsehood, as the fact checkers would say. That claim was made with no evidence, as an ABC News reporter would say. In truth, this is a picture of Nate Silver speaking at the “ABC Leadership Breakfast” during Advertising Week XII. Of course Advertising Week uses the same numbering system as the SuperBowl ™. That would be 2015 in normie text, about a year prior to FiveThirtyEight’s mangling of the prior national election. You will only see Nate Silver on ABC News and other ABC media properties and events, because FiveThirtyEight is a wholly-owned subsidiary of ABC News. ABC News, of course, is a wholly-owned subsidiary of The Walt Disney Corporation. Hold that thought. ©2020 Ben Hunt 1 All rights reserved. That’s Fivey Fox, the FiveThirtyEight cartoon mascot, who is happy to guide you through the genius-level mathematics and super-science that “powers” FiveThirtyEight’s election models. You may have also seen Fivey Fox on ABC News programming, as part of a weekly animated cartoon segment broadcast over the past nine months to “inform” viewers about “how the election actually works”. For all you FiveThirtyEight and ABC News viewers, I’d guess that most of you find Fivey Fox and the cartoon infographics pretty cringey. I’d guess that most of you believe, however, that these animated cartoons are not aimed at you, but at “low-information” viewers who are not easily capable of understanding how the election actually works, and certainly not capable of understanding the genius-level mathematics and super-science behind FiveThirtyEight’s election models.