HTTP/2: Analysis and Measurements
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HTTP2 Explained
HTTP2 Explained Daniel Stenberg Mozilla Corporation [email protected] ABSTRACT credits to everyone who helps out! I hope to make this document A detailed description explaining the background and problems better over time. with current HTTP that has lead to the development of the next This document is available at http://daniel.haxx.se/http2. generation HTTP protocol: HTTP 2. It also describes and elaborates around the new protocol design and functionality, 1.3 License including some implementation specifics and a few words about This document is licensed under the the future. Creative Commons Attribution 4.0 This article is an editorial note submitted to CCR. It has NOT license: been peer reviewed. The author takes full responsibility for this http://creativecommons.org/licenses/by/4.0/ article’s technical content. Comments can be posted through CCR Online. 2. HTTP Today Keywords HTTP 1.1 has turned into a protocol used for virtually everything HTTP 2.0, security, protocol on the Internet. Huge investments have been done on protocols and infrastructure that takes advantage of this. This is taken to the 1. Background extent that it is often easier today to make things run on top of HTTP rather than building something new on its own. This is a document describing http2 from a technical and protocol level. It started out as a presentation I did in Stockholm in April 2014. I've since gotten a lot of questions about the contents of 2.1 HTTP 1.1 is Huge that presentation from people who couldn't attend, so I decided to When HTTP was created and thrown out into the world it was convert it into a full-blown document with all details and proper probably perceived as a rather simple and straight-forward explanations. -

Introduction of an Advanced Caching Layer Leveraging the Varnish Technology Stack and Integrating It to the Existing Web Platform
Introduction of an Advanced Caching Layer Leveraging the Varnish Technology Stack and Integrating It to the Existing Web Platform Author: Irina Vasilieva Director: Jaime M. Delgado Merce June 21, 2018 Barcelona School of Informatics Universitat Polit`ecnicade Catalunya Thesis presented for the Bachelor Degree of Computer Science Abstract Web performance nowadays plays a significant role for many leading enterprises and the ones that trying to gain more visibility and users. Multiple studies and research papers in the area show that poor performance have a negative impact on business goals. An endless waiting for slow Web pages to load frus- trates demanding visitors into seeking alternatives and as a result, abandoning a website. Many different solutions and approaches came up recently to solve performance and scalability issues on the web sites. It is no surprise, that companies attempt to retain their users, improve user experience, conversions and SEO rankings to get a profitable revenue. HTTP requests reduction, file compression, in- frastructure, image optimization are some of the web performance optimization techniques, or even a combination of them, enterprises find useful for their web platforms. Varnish, an open source software, was suggested as a proxy caching server to prove that it can drastically improve hit rate and response times on the website. It can deal with performance and scalability at the highest level. In order to demonstrate the caching capability of Varnish a web platform was built based on Adobe Experience Manager with its own out of the box caching tool, named dispatcher. The main focus is to replace dispatcher and compare the web per- formance outcome. -

Improving Packet Caching Scalability Through the Concept Of
IMPROVING PACKET CACHING SCALABILITY THROUGH THE CONCEPT OF AN EXPLICIT END OF DATA MARKER A Thesis Submitted to the Graduate School of the University of Notre Dame in Partial Fulfillment of the Requirements for the Degree of Master of Science in Computer Science and Engineering by Xiaolong Li, B.S., M.S. ________________________________ Aaron Striegel, Director Graduate Program in Computer Science and Engineering Notre Dame, Indiana July 2006 c Copyright by Xiaolong Li 2006 All Rights Reserved Improving Packet Caching Scalability Through the Concept of an Explicit End of Data Marker Abstract by Xiaolong Li The web has witnessed an explosion of dynamic content generation to provide web users with an interactive and personalized experience. While traditional web caching techniques work well when redundancy occurs on an object-level basis (page, image, etc.), the use of dynamic content presents unique challenges. Although past work has addressed mechanisms for detecting redundancy despite dynamic content, the scalability of such techniques is limited. In this thesis, an effective and highly scalable approach, Explicit End of Data (EEOD) is presented, which allows the content designer to easily signal bound- aries between cacheable and non-cacheable content. EEOD provides application- to-stack mechanisms to guarantee separation of packets with the end goal of sim- plifying packet-level caching mechanisms. Most importantly, EEOD does not re- quire client-side modifications and can function in a variety of server-side/network deployment modes. Additionally, experimental studies are presented, showing EEOD offers 25% and 30% relative improvements in terms of bandwidth efficiency and retrieval time over current approaches in the literature. -

A Systematic Review of Web Server Technologies Brixton Hamilton
A Systematic Review of Web Server Technologies Brixton Hamilton Abstract The choice between different web server technologies is an increasingly relevant problem that users must face. This article will outline the features and functionalities that web servers perform, the differences between them, focusing on Apache, IIS, Jetty and Nginx, and how those relate to the requirements of different users. I will analyse the current trends in web server technologies, and suggest how they might continue to change in the future. As the internet rapidly grows and evolves, so must the web server technologies we use to host the websites on it. From merely tens of thousands of sites predominantly using NCSA server technology shortly after the birth of the internet, as of November 2016 there are 171 Million active sites[1], and over time the ever-changing needs of these sites will need to be met by more suitable web servers. The role of the web server in isolation is clear-cut, it must handle HTTP requests. However, outside this it must work with database systems (such as MySQL or MongoDB), serve dynamic content using server-side scripting languages (e.g. PHP or ASP .NET), and deal with the operating system on which it runs (most commonly Linux). Many different web server technologies exist, and when choosing between them, compatibility with the other elements of your server architecture is important. For the past 20 years, the clear-cut leader for active websites has been Apache, an adaptable, open- source server, usually run alongside Linux, PHP and MySQL as part of a ‘LAMP Stack’. -

Migrating-To-Red-Hat-Amq-7.Pdf
Red Hat AMQ 2021.Q2 Migrating to Red Hat AMQ 7 For Use with Red Hat AMQ 2021.Q2 Last Updated: 2021-07-26 Red Hat AMQ 2021.Q2 Migrating to Red Hat AMQ 7 For Use with Red Hat AMQ 2021.Q2 Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -
Play Framework Documentation
Play framework documentation Welcome to the play framework documentation. This documentation is intended for the 1.1 release and may significantly differs from previous versions of the framework. Check the version 1.1 release notes. The 1.1 branch is in active development. Getting started Your first steps with Play and your first 5 minutes of fun. 1. Play framework overview 2. Watch the screencast 3. Five cool things you can do with Play 4. Usability - details matter as much as features 5. Frequently Asked Questions 6. Installation guide 7. Your first application - the 'Hello World' tutorial 8. Set up your preferred IDE 9. Sample applications 10. Live coding script - to practice, and impress your colleagues with Tutorial - Play guide, a real world app step-by-step Learn Play by coding 'Yet Another Blog Engine', from start to finish. Each chapter will be a chance to learn one more cool Play feature. 1. Starting up the project 2. A first iteration of the data model 3. Building the first screen 4. The comments page 5. Setting up a Captcha 6. Add tagging support 7. A basic admin area using CRUD 8. Adding authentication 9. Creating a custom editor area 10. Completing the application tests 11. Preparing for production 12. Internationalisation and localisation The essential documentation Generated with playframework pdf module. Page 1/264 Everything you need to know about Play. 1. Main concepts i. The MVC application model ii. A request life cycle iii. Application layout & organization iv. Development lifecycle 2. HTTP routing i. The routes file syntax ii. Routes priority iii. -

The Netty Project 3.2 User Guide the Proven Approach to Rapid Network
The Netty Project 3.2 User Guide The Proven Approach to Rapid Network Application Development 3.2.6.Final Preface .............................................................................................................................. iii 1. The Problem ........................................................................................................... iii 2. The Solution ........................................................................................................... iii 1. Getting Started ............................................................................................................... 1 1.1. Before Getting Started ............................................................................................ 1 1.2. Writing a Discard Server ......................................................................................... 1 1.3. Looking into the Received Data ................................................................................ 3 1.4. Writing an Echo Server ........................................................................................... 4 1.5. Writing a Time Server ............................................................................................ 5 1.6. Writing a Time Client ............................................................................................. 7 1.7. Dealing with a Stream-based Transport ...................................................................... 8 1.7.1. One Small Caveat of Socket Buffer ................................................................ -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Freebsd's Firewall Feast
SEE TEXT ONLY FreeBSD’s Firewall Feast By Michael W Lucas reeBSD is famous for all sorts of fantastic gets silently dropped, and which is sent back to features, such as ZFS, jails, bhyve virtual- the source with a letter of complaint. A packet- ization, and the Ports Collection. It’s forwarding packet filter is the original firewall. F somewhat infamous, however, for having The firewalls all have a common core feature three different firewalls: PF, IPFilter, and IPFW. set considered the minimum for a modern pack- Where did all these firewalls come from, and et filter. They can track the state of a TCP/IP con- why are they all still in the system? nection and permit traffic based on existing con- The IT industry has repeatedly abused, nections. They can all return resets or silently stretched, and tormented the word firewall to fit drop connections. All can manage non-routable all sorts of different products. When someone addresses and perform network address transla- uses firewall, ask them exactly what they’re talk- tion. They all work with lists of rules defining ing about. Do they mean a caching HTTP proxy how to respond to traffic from different IP like Squid or Varnish? A generic proxy like addresses and network ports. Incoming packets relayd? Or a TCP/IP packet filter? are compared to the list of rules until they are All of FreeBSD’s firewalls are packet filters. permitted or rejected. They control which TCP/IP addresses and ports The firewalls have their own unique features, can connect to the host. -
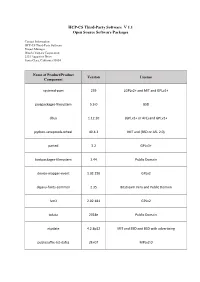
HCP-CS Third-Party Software V1.1
HCP-CS Third-Party Software V 1.1 Open Source Software Packages Contact Information: HCP-CS Third-Party Software Project Manager Hitachi Vantara Corporation 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component systemd-pam 239 LGPLv2+ and MIT and GPLv2+ javapackages-filesystem 5.3.0 BSD dbus 1.12.10 (GPLv2+ or AFL) and GPLv2+ python-setuptools-wheel 40.4.3 MIT and (BSD or ASL 2.0) parted 3.2 GPLv3+ fontpackages-filesystem 1.44 Public Domain device-mapper-event 1.02.150 GPLv2 dejavu-fonts-common 2.35 Bitstream Vera and Public Domain lvm2 2.02.181 GPLv2 tzdata 2018e Public Domain ntpdate 4.2.8p12 MIT and BSD and BSD with advertising publicsuffix-list-dafsa 2E+07 MPLv2.0 Name of Product/Product Version License Component subversion-libs 1.10.2 ASL 2.0 ncurses-base 6.1 MIT javapackages-tools 5.3.0 BSD libX11-common 1.6.6 MIT apache-commons-pool 1.6 ASL 2.0 dnf-data 4.0.4 GPLv2+ and GPLv2 and GPL junit 4.12 EPL-1.0 fedora-release 29 MIT log4j12 1.2.17 ASL 2.0 setup 2.12.1 Public Domain cglib 3.2.4 ASL 2.0 and BSD basesystem 11 Public Domain slf4j 1.7.25 MIT and ASL 2.0 libselinux 2.8 Public Domain tomcat-lib 9.0.10 ASL 2.0 Name of Product/Product Version License Component LGPLv2+ and LGPLv2+ with exceptions and GPLv2+ glibc-all-langpacks 2.28 and GPLv2+ with exceptions and BSD and Inner-Net and ISC and Public Domain and GFDL antlr-tool 2.7.7 ANTLR-PD LGPLv2+ and LGPLv2+ with exceptions and GPLv2+ glibc 2.28 and GPLv2+ with exceptions and BSD and Inner-Net and ISC and Public Domain and GFDL apache-commons-daemon -

Learning HTTP 2.Pdf
L e a r n i n g H T T P/2 A PRACTICAL GUIDE FOR BEGINNERS Stephen Ludin & Javier Garza Learning HTTP/2 A Practical Guide for Beginners Stephen Ludin and Javier Garza Beijing Boston Farnham Sebastopol Tokyo Learning HTTP/2 by Stephen Ludin and Javier Garza Copyright © 2017 Stephen Ludin, Javier Garza. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com/safari). For more information, contact our corporate/insti‐ tutional sales department: 800-998-9938 or [email protected]. Acquisitions Editor: Brian Anderson Indexer: Wendy Catalano Editors: Virginia Wilson and Dawn Schanafelt Interior Designer: David Futato Production Editor: Shiny Kalapurakkel Cover Designer: Karen Montgomery Copyeditor: Kim Cofer Illustrator: Rebecca Demarest Proofreader: Sonia Saruba June 2017: First Edition Revision History for the First Edition 2017-05-14: First Release 2017-10-27: Second Release See http://oreilly.com/catalog/errata.csp?isbn=9781491962442 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Learning HTTP/2, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the authors have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the authors disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. -

Varnish Documentation Release 3.0.2
Varnish Documentation Release 3.0.2 Varnish Project January 09, 2012 CONTENTS 1 Varnish Installation 3 1.1 Prerequisites...............................................3 1.2 Installing Varnish.............................................3 1.3 Compiling Varnish from source.....................................4 1.4 Getting hold of us............................................6 1.5 Reporting bugs..............................................7 1.6 Upgrading from Varnish 2.1 to 3.0....................................9 2 Using Varnish 13 2.1 Backend servers............................................. 13 2.2 Starting Varnish............................................. 14 2.3 Logging in Varnish............................................ 14 2.4 Sizing your cache............................................ 15 2.5 Put Varnish on port 80.......................................... 15 2.6 Varnish Configuration Language - VCL................................. 16 2.7 Statistics................................................. 18 2.8 Achieving a high hitrate......................................... 19 2.9 Cookies.................................................. 22 2.10 Vary.................................................... 23 2.11 Pitfall - Vary: User-Agent........................................ 24 2.12 Purging and banning........................................... 24 2.13 Edge Side Includes............................................ 26 2.14 Running inside a virtual machine (VM)................................. 27 2.15 Advanced Backend configuration...................................