Assignment #2 - Access Control CMPSC443 - Introduction to Computer and Network Security Spring 2009 - Prof
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIX Cheat Sheet – Sarah Medland Help on Any Unix Command List a Directory Change to Directory Make a New Directory Remove A
THE 2013 INTERNATIONAL WORKSHOP ON STATISTICAL METHODOLOGY FOR HUMAN GENOMIC STUDIES UNIX cheat sheet – Sarah Medland Help on any Unix command man {command} Type man ls to read the manual for the ls command. which {command} Find out where a program is installed whatis {command} Give short description of command. List a directory ls {path} ls -l {path} Long listing, with date, size and permisions. ls -R {path} Recursive listing, with all subdirs. Change to directory cd {dirname} There must be a space between. cd ~ Go back to home directory, useful if you're lost. cd .. Go back one directory. Make a new directory mkdir {dirname} Remove a directory/file rmdir {dirname} Only works if {dirname} is empty. rm {filespec} ? and * wildcards work like DOS should. "?" is any character; "*" is any string of characters. Print working directory pwd Show where you are as full path. Copy a file or directory cp {file1} {file2} cp -r {dir1} {dir2} Recursive, copy directory and all subdirs. cat {newfile} >> {oldfile} Append newfile to end of oldfile. Move (or rename) a file mv {oldfile} {newfile} Moving a file and renaming it are the same thing. View a text file more {filename} View file one screen at a time. less {filename} Like more , with extra features. cat {filename} View file, but it scrolls. page {filename} Very handy with ncftp . nano {filename} Use text editor. head {filename} show first 10 lines tail {filename} show last 10 lines Compare two files diff {file1} {file2} Show the differences. sdiff {file1} {file2} Show files side by side. Other text commands grep '{pattern}' {file} Find regular expression in file. -

Introduction to Linux – Part 1
Introduction to Linux – Part 1 Brett Milash and Wim Cardoen Center for High Performance Computing May 22, 2018 ssh Login or Interactive Node kingspeak.chpc.utah.edu Batch queue system … kp001 kp002 …. kpxxx FastX ● https://www.chpc.utah.edu/documentation/software/fastx2.php ● Remote graphical sessions in much more efficient and effective way than simple X forwarding ● Persistence - can be disconnected from without closing the session, allowing users to resume their sessions from other devices. ● Licensed by CHPC ● Desktop clients exist for windows, mac, and linux ● Web based client option ● Server installed on all CHPC interactive nodes and the frisco nodes. Windows – alternatives to FastX ● Need ssh client - PuTTY ● http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html - XShell ● http://www.netsarang.com/download/down_xsh.html ● For X applications also need X-forwarding tool - Xming (use Mesa version as needed for some apps) ● http://www.straightrunning.com/XmingNotes/ - Make sure X forwarding enabled in your ssh client Linux or Mac Desktop ● Just need to open up a terminal or console ● When running applications with graphical interfaces, use ssh –Y or ssh –X Getting Started - Login ● Download and install FastX if you like (required on windows unless you already have PuTTY or Xshell installed) ● If you have a CHPC account: - ssh [email protected] ● If not get a username and password: - ssh [email protected] Shell Basics q A Shell is a program that is the interface between you and the operating system -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -

Student Number: Surname: Given Name
Computer Science 2211a Midterm Examination Sample Solutions 9 November 20XX 1 hour 40 minutes Student Number: Surname: Given name: Instructions/Notes: The examination has 35 questions on 9 pages, and a total of 110 marks. Put all answers on the question paper. This is a closed book exam. NO ELECTRONIC DEVICES OF ANY KIND ARE ALLOWED. 1. [4 marks] Which of the following Unix commands/utilities are filters? Correct answers are in blue. mkdir cd nl passwd grep cat chmod scriptfix mv 2. [1 mark] The Unix command echo HOME will print the contents of the environment variable whose name is HOME. True False 3. [1 mark] In C, the null character is another name for the null pointer. True False 4. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod a=x abc.dat is equivalent to the command: a. chmod 755 abc.dat b. chmod 711 abc.dat c. chmod 155 abc.dat d. chmod 111 abc.dat e. none of the above 5. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod ug+w abc.dat is equivalent to the command: a. chmod 766 abc.dat b. chmod 764 abc.dat c. chmod 754 abc.dat d. chmod 222 abc.dat e. none of the above 2 6. [3 marks] The protection code for def.dat is currently dr-xr--r-- , and the protection code for def.dat/ghi.dat is currently -r-xr--r-- . Give one or more chmod commands that will set the protections properly so that the owner of the two files will be able to delete ghi.dat using the command rm def.dat/ghi.dat chmod u+w def.dat or chmod –r u+w def.dat 7. -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Command $Line; Done
http://xkcd.com/208/ >0 TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG >1 TGCAGGTTGTTGTTACTCAGGTCCAGTTCTCTGAGACTGGAGGACTGGGAGCTGAGAACTGAGGACAGAGCTTCA >2 TGCAGGGCCGGTCCAAGGCTGCATGAGGCCTGGGGCAGAATCTGACCTAGGGGCCCCTCTTGCTGCTAAAACCAT >3 TGCAGGATCTGCTGCACCATTAACCAGACAGAAATGGCAGTTTTATACAAGTTATTATTCTAATTCAATAGCTGA >4 TGCAGGGGTCAAATACAGCTGTCAAAGCCAGACTTTGAGCACTGCTAGCTGGCTGCAACACCTGCACTTAACCTC cat seqs.fa PIPE grep ACGT TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTGGTTGGGTACATTATTTTAAGTGTATTTGACAAG >1 TGCAGGTTGTTGTTACTCAGGTCCAGTTCTCTGAGACTGGAGGACTGGGAGCTGAGAACTGAGGACAGAGCTTCA >2 TGCAGGGCCGGTCCAAGGCTGCATGAGGCCTGGGGCAGAATCTGACCTAGGGGCCCCTCTTGCTGCTAAAACCAT >3 TGCAGGATCTGCTGCACCATTAACCAGACAGAAATGGCAGTTTTATACAAGTTATTATTCTAATTCAATAGCTGA >4 TGCAGGGGTCAAATACAGCTGTCAAAGCCAGACTTTGAGCACTGCTAGCTGGCTGCAACACCTGCACTTAACCTC cat seqs.fa Does PIPE “>0” grep ACGT contain “ACGT”? Yes? No? Output NULL >1 TGCAGGTTGTTGTTACTCAGGTCCAGTTCTCTGAGACTGGAGGACTGGGAGCTGAGAACTGAGGACAGAGCTTCA >2 TGCAGGGCCGGTCCAAGGCTGCATGAGGCCTGGGGCAGAATCTGACCTAGGGGCCCCTCTTGCTGCTAAAACCAT >3 TGCAGGATCTGCTGCACCATTAACCAGACAGAAATGGCAGTTTTATACAAGTTATTATTCTAATTCAATAGCTGA >4 TGCAGGGGTCAAATACAGCTGTCAAAGCCAGACTTTGAGCACTGCTAGCTGGCTGCAACACCTGCACTTAACCTC cat seqs.fa Does PIPE “TGCAGGTATATCTATTAGCAGGTTTAATTTTGCCTGCACTTG...G” grep ACGT contain “ACGT”? Yes? No? Output NULL TGCAGGTTGTTGTTACTCAGGTCCAGTTCTCTGAGACTGGAGGACTGGGAGCTGAGAACTGAGGACAGAGCTTCA >2 TGCAGGGCCGGTCCAAGGCTGCATGAGGCCTGGGGCAGAATCTGACCTAGGGGCCCCTCTTGCTGCTAAAACCAT >3 TGCAGGATCTGCTGCACCATTAACCAGACAGAAATGGCAGTTTTATACAAGTTATTATTCTAATTCAATAGCTGA -

File Security and Permissions
File Security and Permissions File Permissions (1) u With respect to a particular file, Unix divides the set of all users on a system into three categories: – user vThe owner of the file. – group users vMost of you are in the group 2ndyr vUsed for easier administration of access control. vNormally only the superuser can set up groups. vUsers can be in more than one group. – others vEveryone else. File Permissions (2) u Permissions can be viewed with the ls -l command obelix[1] > ls -l total 1247 -rw------- 1 csnow 1117 Jul 23 15:49 bad.cpp drwx--x--x 2 csnow 2048 Jul 17 10:13 bibd/ drwxr-xr-x 2 csnow 512 Aug 27 23:18 cache/ -rw------- 1 csnow 2081 Jul 23 15:49 tst2.s -rw-r-xr-- 1 csnow 1275 Jul 23 15:49 vecexpr.cpp r read permission -rw-r-xr-- w write permission x execute permission File type - = file d = directory User Group Other l=symbolic link Permissions Permissions Permissions File Permissions (3) u Permissions are changed with the chmod command. u There are two syntaxes you can use: chmod DDD file [file ...] – DDD are 3 octal digits representing bits of protection – rwx rwx rwx can be thought of as 111 111 111 in binary rw- r-- r-- 110 100 100 6 4 4 chmod 644 file File Permissions (4) u chmod [ugoa][+-=][rwx] file [...] – This is the “symbolic” method. – chmod u+rwx file gives the User Read, Write, and eXecute – chmod g+rx file gives the Group Read and eXecute – chmod o-rwx file removes R, W, and X from Others – chmod a+x file gives All eXecute permission – chmod g=r file gives Group Read permission and makes sure it has nothing -

Ubuntu Server Guide Basic Installation Preparing to Install
Ubuntu Server Guide Welcome to the Ubuntu Server Guide! This site includes information on using Ubuntu Server for the latest LTS release, Ubuntu 20.04 LTS (Focal Fossa). For an offline version as well as versions for previous releases see below. Improving the Documentation If you find any errors or have suggestions for improvements to pages, please use the link at thebottomof each topic titled: “Help improve this document in the forum.” This link will take you to the Server Discourse forum for the specific page you are viewing. There you can share your comments or let us know aboutbugs with any page. PDFs and Previous Releases Below are links to the previous Ubuntu Server release server guides as well as an offline copy of the current version of this site: Ubuntu 20.04 LTS (Focal Fossa): PDF Ubuntu 18.04 LTS (Bionic Beaver): Web and PDF Ubuntu 16.04 LTS (Xenial Xerus): Web and PDF Support There are a couple of different ways that the Ubuntu Server edition is supported: commercial support and community support. The main commercial support (and development funding) is available from Canonical, Ltd. They supply reasonably- priced support contracts on a per desktop or per-server basis. For more information see the Ubuntu Advantage page. Community support is also provided by dedicated individuals and companies that wish to make Ubuntu the best distribution possible. Support is provided through multiple mailing lists, IRC channels, forums, blogs, wikis, etc. The large amount of information available can be overwhelming, but a good search engine query can usually provide an answer to your questions. -
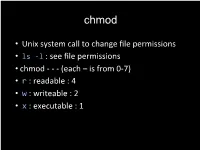
Unix System Call to Change File Permissions • Ls
chmod • Unix system call to change file permissions • ls -l : see file permissions • chmod - - - (each – is from 0-7) • r : readable : 4 • w : writeable : 2 • x : executable : 1 • chmod group+permissions • + adds permissions • - takes away permissions • u: user or owner • g: group • o: others Example • rwx --- --- can also be represented as 700 • chmod 444 file would give what permissions? • What’s another way we could write this? Example • rwx --- --- can also be represented as 700 • chmod 444 file would give what permissions? • Readable to everyone! • Could also do chmod a+r file Translations • chmod 555 • chmod u+x • chmod 640 Translations • chmod 555 • Chmod a+rx • Gives everyone read and execute access • chmod u+x • Chmod 100 • Gives the owner execute access • chmod 640 • Chmod u+rw, chmod g+r • Gives owner read and write permissions • Gives group read permission Common cases • chmod 711 directory: Use for any directory • chmod 644 file.txt: Use for any non-PHP file you create • chmod 600 file.php: Use for PHP files TCP/IP • Transmission Control Protocol/Internet Protocol • Gives a set of standards that govern how data should be packetized, transmitted, routed and received • Increases chances the data will get where you want it to! Ports • Need to tell our end destination what type of data is in the packet; packets might be routed in various ways/paths • 21: FTP: File transfer protocol • 25: SMTP: Email • 53: DNS: Domain Name System • What is the IP address of a domain name? • 80: HTTP: Webpage • 443: HTTPS: Secure webpage HTTP HyperText Transfer Protocol HyperText Check out <a href="https://www.cs50.net">this</a> really cool website! Transfer Protocol Introduction to the HTTP specification, from http://www.ietf.org/rfc/rfc2616.txt. -
Jackson State University Department of Computer Science CSC 438-01/539-01 Systems and Software Security, Spring 2014 Instructor: Dr
Jackson State University Department of Computer Science CSC 438-01/539-01 Systems and Software Security, Spring 2014 Instructor: Dr. Natarajan Meghanathan Project 1: Exploring UNIX Access Control in a Virtual Machine Environment Due: February 26, 2014, 7.30 PM The objective of this project is to explore the different UNIX access control commands and their features. You will do this project in a virtual machine environment. If you already have a virtual machine installed (either in VM Player or Virtual Box, you can skip the following steps and proceed to Page 4). Installing VirtualBox 4.2 and Ubuntu OS Go to https://www.virtualbox.org/wiki/Downloads and download VirtualBox for your operating system. If you work on a lab computer, you need to use the Ubuntu VM .iso file that is stored on the local machine. If you work on your personal computer, you need to download the Ubuntu .iso file from the website listed in Step # 1 and continue. You may use the following steps for installing the Ubuntu VM on the virtualbox. 1. The Ubuntu installation file is located on the desktop of your PC (it can be downloaded from http://www.ubuntu.com/download/ubuntu/download if the .iso file cannot be located on your desktop). 2. On the VirtualBox Manager screen click on “New” 1 3. When prompted, put your J # for the name of the VM and select “Linux” as OS (when you choose Linux as OS, the program should automatically choose Ubuntu as Version, if not select Ubuntu) and click Next. 4. -

Controlling Gpios on Rpi Using Ping Command
Ver. 3 Department of Engineering Science Lab – Controlling PI Controlling Raspberry Pi 3 Model B Using PING Commands A. Objectives 1. An introduction to Shell and shell scripting 2. Starting a program at the Auto-start 3. Knowing your distro version 4. Understanding tcpdump command 5. Introducing tshark utility 6. Interfacing RPI to an LCD 7. Understanding PING command B. Time of Completion This laboratory activity is designed for students with some knowledge of Raspberry Pi and it is estimated to take about 5-6 hours to complete. C. Requirements 1. A Raspberry Pi 3 Model 3 2. 32 GByte MicroSD card à Give your MicroSD card to the lab instructor for a copy of Ubuntu. 3. USB adaptor to power up the Pi 4. Read Lab 2 – Interfacing with Pi carefully. D. Pre-Lab Lear about ping and ICMP protocols. F. Farahmand 9/30/2019 1 Ver. 3 Department of Engineering Science Lab – Controlling PI E. Lab This lab has two separate parts. Please make sure you read each part carefully. Answer all the questions. Submit your codes via Canvas. 1) Part I - Showing IP Addresses on the LCD In this section we learn how to interface an LCD to the Pi and run a program automatically at the boot up. a) Interfacing your RPI to an LCD In this section you need to interface your 16×2 LCD with Raspberry Pi using 4-bit mode. Please note that you can choose any type of LCD and interface it to your PI, including OLED. Below is the wiring example showing how to interface a 16×2 LCD to RPI. -

The Unix Shell
The Unix Shell Permissions Copyright © Software Carpentry 2010 This work is licensed under the Creative Commons Attribution License See http://software-carpentry.org/license.html for more information. shell Permissions Introduction shell pwd, mkdir, cp, ... Permissions Introduction shell pwd, mkdir, cp, ... * Permissions Introduction shell pwd, mkdir, cp, ... * >, | Permissions Introduction shell pwd, mkdir, cp, ... * >, | Who can see what? Permissions Introduction shell pwd, mkdir, cp, ... * >, | Who can see what? change Permissions Introduction shell pwd, mkdir, cp, ... * >, | Who can see what? change run Permissions Introduction Simplified version of Unix permissions Permissions Introduction Simplified version of Unix permissions Windows uses similar concepts… Permissions Introduction Simplified version of Unix permissions Windows uses similar concepts… …but there is no exact translation between the two Permissions Introduction user Permissions Introduction user Has unique user name and user ID Permissions Introduction user Has unique user name and user ID User name is text: "imhotep", "larry", "vlad", … Permissions Introduction user Has unique user name and user ID User name is text: "imhotep", "larry", "vlad", … User ID is numeric (easier for computer to store) Permissions Introduction user group Permissions Introduction user group Has unique group name and group ID Permissions Introduction user group Has unique group name and group ID User can belongs to zero or more groups Permissions Introduction user group Has unique group name