Proceedings of IEEE 27 International Symposium on Parallel And
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Stackable Lcc/Lcd Oven Instruction Manual
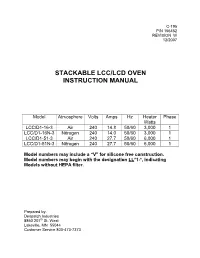
C-195 P/N 156452 REVISION W 12/2007 STACKABLE LCC/LCD OVEN INSTRUCTION MANUAL Model Atmosphere Volts Amps Hz Heater Phase Watts LCC/D1-16-3 Air 240 14.8 50/60 3,000 1 LCC/D1-16N-3 Nitrogen 240 14.0 50/60 3,000 1 LCC/D1-51-3 Air 240 27.7 50/60 6,000 1 LCC/D1-51N-3 Nitrogen 240 27.7 50/60 6,000 1 Model numbers may include a “V” for silicone free construction. Model numbers may begin with the designation LL *1-*, indicating Models without HEPA filter. Prepared by: Despatch Industries 8860 207 th St. West Lakeville, MN 55044 Customer Service 800-473-7373 NOTICE Users of this equipment must comply with operating procedures and training of operation personnel as required by the Occupational Safety and Health Act (OSHA) of 1970, Section 6 and relevant safety standards, as well as other safety rules and regulations of state and local governments. Refer to the relevant safety standards in OSHA and National Fire Protection Association (NFPA), section 86 of 1990. CAUTION Setup and maintenance of the equipment should be performed by qualified personnel who are experienced in handling all facets of this type of system. Improper setup and operation of this equipment could cause an explosion that may result in equipment damage, personal injury or possible death. Dear Customer, Thank you for choosing Despatch Industries. We appreciate the opportunity to work with you and to meet your heat processing needs. We believe that you have selected the finest equipment available in the heat processing industry. -

Handheld Computing Terminal Industrializing Mobile Gateway for the Internet of Things
Handheld Computing Terminal Industrializing Mobile Gateway for the Internet of Things Retail Inventory Logistics Management Internet of Vehicles Electric Utility Inspection www.AMobile-solutions.com About AMobile Mobile Gateway for IIoT Dedicated IIoT, AMobile develops mobile devices and gateways for data collectivity, wireless communications, local computing and processing, and connectivity between the fields and cloud. In addition, AMobile's unified management platform-Node-Watch monitors and manages not only mobile devices but also IoT equipment in real-time to realize industrial IoT applications. Manufacturing • IPC mobile • Mobility computing technology Retail Inspection (IP-6X, Military • Premier member grade, Wide- - early access Blockchain temperature) Healthcare Logistics • Manufacturing resource pool Big Data & AI • Logistics • Global customer support Handheld Mobile Computing Data Collector Smart Meter Mobile Inspection Device with Keyboard Assistant Mobile Computing IoT Terminal Device Ultra-rugged Intelligent Barcode Reader Vehicle Mount Handheld Device Handheld Device Tablet Mobile Gateway AMobile Intelligent established in 2013, a joint venture by Arbor Technology, MediaTek, and Wistron, is Pressure Image an expert in industrial mobile computers and solutions for industrial applications including warehousing, Temperature Velocity Gyroscope logistics, manufacturing, and retail. Leveraging group resources of manufacturing and services from Wistron, IPC know-how and distribution channels from Arbor, mobility technology and -

The Lcc 4.X Code-Generation Interface
The lcc 4.x Code-Generation Interface Christopher W. Fraser and David R. Hanson Microsoft Research [email protected] [email protected] July 2001 Technical Report MSR-TR-2001-64 Abstract Lcc is a widely used compiler for Standard C described in A Retargetable C Compiler: Design and Implementation. This report details the lcc 4.x code- generation interface, which defines the interaction between the target- independent front end and the target-dependent back ends. This interface differs from the interface described in Chap. 5 of A Retargetable C Com- piler. Additional infomation about lcc is available at http://www.cs.princ- eton.edu/software/lcc/. Microsoft Research Microsoft Corporation One Microsoft Way Redmond, WA 98052 http://www.research.microsoft.com/ The lcc 4.x Code-Generation Interface 1. Introduction Lcc is a widely used compiler for Standard C described in A Retargetable C Compiler [1]. Version 4.x is the current release of lcc, and it uses a different code-generation interface than the inter- face described in Chap. 5 of Reference 1. This report details the 4.x interface. Lcc distributions are available at http://www.cs.princeton.edu/software/lcc/ along with installation instruc- tions [2]. The code generation interface specifies the interaction between lcc’s target-independent front end and target-dependent back ends. The interface consists of a few shared data structures, a 33-operator language, which encodes the executable code from a source program in directed acyclic graphs, or dags, and 18 functions, that manipulate or modify dags and other shared data structures. On most targets, implementations of many of these functions are very simple. -

A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges
sensors Review A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges M. Nadeem Ahangar 1, Qasim Z. Ahmed 1,*, Fahd A. Khan 2 and Maryam Hafeez 1 1 School of Computing and Engineering, University of Huddersfield, Huddersfield HD1 3DH, UK; [email protected] (M.N.A.); [email protected] (M.H.) 2 School of Electrical Engineering and Computer Science, National University of Sciences and Technology, Islamabad 44000, Pakistan; [email protected] * Correspondence: [email protected] Abstract: The Department of Transport in the United Kingdom recorded 25,080 motor vehicle fatali- ties in 2019. This situation stresses the need for an intelligent transport system (ITS) that improves road safety and security by avoiding human errors with the use of autonomous vehicles (AVs). There- fore, this survey discusses the current development of two main components of an ITS: (1) gathering of AVs surrounding data using sensors; and (2) enabling vehicular communication technologies. First, the paper discusses various sensors and their role in AVs. Then, various communication tech- nologies for AVs to facilitate vehicle to everything (V2X) communication are discussed. Based on the transmission range, these technologies are grouped into three main categories: long-range, medium- range and short-range. The short-range group presents the development of Bluetooth, ZigBee and ultra-wide band communication for AVs. The medium-range examines the properties of dedicated short-range communications (DSRC). Finally, the long-range group presents the cellular-vehicle to everything (C-V2X) and 5G-new radio (5G-NR). An important characteristic which differentiates each category and its suitable application is latency. -

Fog Computing for Detecting Vehicular Congestion, an Internet of Vehicles Based Approach: a Review
> REPLACE THIS LINE WITH YOUR PAPER IDENTIFICATION NUMBER (DOUBLE-CLICK HERE TO EDIT) < 1 Fog Computing for Detecting Vehicular Congestion, An Internet of Vehicles based Approach: A review Arnav Thakur and Reza Malekian, Senior Member, IEEE double by the year 2020 [3]. To enhance the efficiency of the Abstract—Vehicular congestion is directly impacting the transportation sector and reduce the associated economic and efficiency of the transport sector. A wireless sensor network for environmental consequences, an accurate real-time vehicular vehicular clients is used in Internet of Vehicles based solutions traffic congestion identification system is required to be used for traffic management applications. It was found that vehicular in effective traffic management schemes that improve traffic congestion detection by using Internet of Vehicles based connected vehicles technology are practically feasible for flow and utilization of road infrastructure. congestion handling. It was found that by using Fog Computing Vehicular congestion is quantified by using the traffic based principles in the vehicular wireless sensor network, density estimate metric which is the number of vehicles per communication in the system can be improved to support larger unit area [4]. The traffic density estimation techniques use number of nodes without impacting performance. In this paper, parameters that include road occupancy rates, difference of connected vehicles technology based vehicular congestion incoming and outgoing traffic in an observation area, traffic identification techniques are studied. Computing paradigms that can be used for the vehicular network are studied to develop a flow estimation and motion detection and tracking to identify practically feasible vehicular congestion detection system that congestion [5]. -

An Intelligent Edge-Chain Enabled Access Control Mechanism For
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publication. Citation information: DOI 10.1109/JIOT.2021.3061467, IEEE Internet of Things Journal JOURNAL OF LATEX CLASS FILES, VOL. 14, NO. 8, AUGUST 2015 1 An Intelligent Edge-Chain Enabled Access Control Mechanism for IoV Yuanni Liu, Man Xiao, Shanzhi Chen, Fellow, IEEE, Fan Bai, Jianli Pan, Member, IEEE, Di Zhang, Senior Member, IEEE Abstract—The current security method of Internet of Vehicles the amounts of vehicles exceed one billion and is expected (IoV) systems is rare, which makes it vulnerable to various to reach two billion by 2035 [6], [7]. As explosive on-road attacks. The malicious and unauthorized nodes can easily in- devices are connecting to Internet, communication security vade the IoV systems to destroy the integrity, availability, and confidentiality of information resources shared among vehicles. becomes a big issue. As we know, the communication security Indeed, access control mechanism can remedy this. However, as method of current IoV devices is rare, making it easy to be a static method, it cannot timely response to these attacks. To attacked. Such malicious attacks include replay, camouflage, solve this problem, we propose an intelligent edge-chain enabled and message tampering attacks et al. [8]. The attacked IoV access control framework with vehicle nodes and RoadSide Units devices may rise potential risks, such as critical electronic (RSUs) in this study. In our scenario, vehicle nodes act as lightweight nodes, whereas RUSs serve as full and edge nodes control unit hacking and control, untrustworthy messages from to provide access control services. -

Position Prediction for Routing in Software Defined Internet of Vehicles
Journal of Communications Vol. 15, No. 2, February 2020 Position Prediction for Routing in Software Defined Internet of Vehicles Muhammad Ali Jibran1, Muhammad Tahir Abbas2, Adeel Rafiq1, and Wang-Cheol Song1 1, Jeju National University, Jeju, South Korea 2 Karlstad University, Karlstad, Sweden Email: [email protected]; [email protected] Abstract—By the prediction of future location for a vehicle in In the past few years, vehicle to vehicle (V2V) Internet of Vehicles (IoV), data forwarding schemes can be communication gain a lot of attention because of its further improved. Major parameters for vehicle position potential to make our journey comfortable on the roads. prediction includes traffic density, motion, road conditions, and The core requirement of connected cars include a reliable vehicle current position. In this paper, therefore, our proposed and fast communication with very low latency response system enforces the accurate prediction with the help of real- time traffic from the vehicles. In addition, the proposed Neural to and from a service provider. In the meanwhile, it needs Network Model assists Edge Controller and centralized to be more efficient to manage a huge number of requests controller to compute and predict vehicle future position inside simultaneously with no traffic congestion. In ITS, a and outside of the vicinity, respectively. Last but not least, in vehicle on the road always initiates a new connection order to get real-time data, and to maintain a quality of request towards the traffic controller in case of path experience, the edge controller is explored with Software failure. Traffic controller estimates a new path each time Defined Internet of Vehicles. -

Deep Learning-Based Intrusion System for Vehicular Ad Hoc Networks
Computers, Materials & Continua CMC, vol.65, no.1, pp.653-681, 2020 Deep Learning-Based Intrusion System for Vehicular Ad Hoc Networks Fei Li1, *, Jiayan Zhang1, Edward Szczerbicki2, Jiaqi Song 1, Ruxiang Li 1 and Renhong Diao1 Abstract: The increasing use of the Internet with vehicles has made travel more convenient. However, hackers can attack intelligent vehicles through various technical loopholes, resulting in a range of security issues. Due to these security issues, the safety protection technology of the in-vehicle system has become a focus of research. Using the advanced autoencoder network and recurrent neural network in deep learning, we investigated the intrusion detection system based on the in-vehicle system. We combined two algorithms to realize the efficient learning of the vehicle’s boundary behavior and the detection of intrusive behavior. In order to verify the accuracy and efficiency of the proposed model, it was evaluated using real vehicle data. The experimental results show that the combination of the two technologies can effectively and accurately identify abnormal boundary behavior. The parameters of the model are self-iteratively updated using the time-based back propagation algorithm. We verified that the model proposed in this study can reach a nearly 96% accurate detection rate. Keywords: Internet of vehicles, safety protection technology, intrusion detection system, advanced auto-encoder, recurrent neural network, time-based back propagation algorithm. 1 Introduction In recent years, intelligent vehicles, a fusion of Internet technology and the machinery manufacturing industry, have resulted in the development of comprehensive information services for travel and daily commutes [Unluturk, Oguz and Atay (2015); Contreras- Castillo, Zeadally and Guerrero-Ibañez (2017)]. -

The Concepts of Connected Car and Internet of Cars and Their Impact on Future People Mobility
INFORMATION SYSTEMS IN MANAGEMENT Information Systems in Management (2017) Vol. 6 (3) 234 −245 THE CONCEPTS OF CONNECTED CAR AND INTERNET OF CARS AND THEIR IMPACT ON FUTURE PEOPLE MOBILITY AGNIESZKA SZMELTER Department of Logistics, University of Gda ńsk (UG) Technological convergence has had a huge impact on development of automo- tive industry. Two main concepts related to mobile technology and the Internet of Things (IoT) in this industry are car connectivity and Internet of Cars (IoC). The ar- ticle aims to present these two concepts with special emphasis on the characteristics of people mobility in future cities. Keywords: automotive, logistics, information logistics, convergence, technological convergence, internet of things, internet of cars, connected car, car connectivity, mobility, public transport. 1. Introduction The global economy, which is currently characterized by development of mo- bile and Internet technologies, is in large part composed of the services sector. A new paradigm appeared: information and communication technologies enable achievement of the economic and / or social objectives by use of cooperation methods (including sharing). ICT contribute to the acceleration of economic recov- ery and the creation of "sustainable digital future" [7]. This paper aims to achieve cognitive objective, which is to present the impact of technological developments in automotive industry (especially the concepts of car connectivity and Internet of Cars) on the development of new people mobility behaviour in cities. The author hypothesizes that technological convergence, pre- sent in currently-sold cars and cars of the future significantly contributes and will contribute to development of new patterns of mobility in cities. The main research method used in the study is analysis of secondary sources, including literature and branch studies made by experts in automotive industry. -

Huawei HCIA-Iot V. 2.5 Evaluation Questions Michel Bakni
Huawei HCIA-IoT v. 2.5 Evaluation Questions Michel Bakni To cite this version: Michel Bakni. Huawei HCIA-IoT v. 2.5 Evaluation Questions. Engineering school. Huawei HCIA-IoT v. 2.5, Bidart, France. 2021, pp.77. hal-03189245 HAL Id: hal-03189245 https://hal.archives-ouvertes.fr/hal-03189245 Submitted on 2 Apr 2021 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License Huawei HCIA-IoT v. 2.5 Evaluation Questions March 2021 Michel BAKNI Author: Michel BAKNI Editor: Sandra HANBO Version: 1.0 , 2021 DOI: 10.6084/m9.figshare.14336687 Copyright notice This work is licensed under Creative Commons Attribution 4.0 International (CC BY 4.0) You are free to: Share — copy and redistribute the material in any medium or format Adapt — remix, transform, and build upon the material for any purpose, even commercially. The licensor cannot revoke these freedoms as long as you follow the license terms: Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made. You may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use. -

Linux Assembly HOWTO Linux Assembly HOWTO
Linux Assembly HOWTO Linux Assembly HOWTO Table of Contents Linux Assembly HOWTO..................................................................................................................................1 Konstantin Boldyshev and François−René Rideau................................................................................1 1.INTRODUCTION................................................................................................................................1 2.DO YOU NEED ASSEMBLY?...........................................................................................................1 3.ASSEMBLERS.....................................................................................................................................1 4.METAPROGRAMMING/MACROPROCESSING............................................................................2 5.CALLING CONVENTIONS................................................................................................................2 6.QUICK START....................................................................................................................................2 7.RESOURCES.......................................................................................................................................2 1. INTRODUCTION...............................................................................................................................2 1.1 Legal Blurb........................................................................................................................................2 -

Internet of Autonomous Vehicles: Architecture, Features, and Socio-Technological Challenges Furqan Jameel, Zheng Chang, Jun Huang, Tapani Ristaniemi
ACCEPTED IN IEEE WIRELESS COMMUNICATIONS 1 Internet of Autonomous Vehicles: Architecture, Features, and Socio-Technological Challenges Furqan Jameel, Zheng Chang, Jun Huang, Tapani Ristaniemi Abstract Mobility is the backbone of urban life and a vital economic factor in the development of the world. Rapid urbanization and the growth of mega-cities is bringing dramatic changes in the capabilities of vehicles. Innovative solutions like autonomy, electrification, and connectivity are on the horizon. How, then, we can provide ubiquitous connectivity to the legacy and autonomous vehicles? This paper seeks to answer this question by combining recent leaps of innovation in network virtualization with remarkable feats of wireless communications. To do so, this paper proposes a novel paradigm called the Internet of autonomous vehicles (IoAV). We begin painting the picture of IoAV by discussing the salient features, and applications of IoAV which is followed by a detailed discussion on the key enabling technologies. Next, we describe the proposed layered architecture of IoAV and uncover some critical functions of each layer. This is followed by the performance evaluation of IoAV which shows significant advantage of the proposed architecture in terms of transmission time and energy consumption. Finally, to best capture the benefits of IoAV, we enumerate some social and technological challenges and explain how some unresolved issues can disrupt the widespread use of autonomous vehicles in the future. Index Terms Autonomous vehicles, Autonomy, Internet of autonomous vehicles (IoAV), Technological challenges I. INTRODUCTION The development of the automotive landscape in the coming years will be significantly influenced by the global political and economic conditions. The idea of sustainability against the background of dwindling and rapidly increasing supplies of fossil fuels will also be consolidated on a global scale [1].