Proof of Work and Proof of Stake Consensus Protocols: a Blockchain Application for Local Complementary Currencies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chia Proof of Space Construction
Chia Proof of Space Construction Introduction In order to create a secure blockchain consensus algorithm using disk space, a Proof of Space is scheme is necessary. This document describes a practical contruction of Proofs of Space, based on Beyond Hellman’s Time- Memory Trade-Offs with Applications to Proofs of Space [1]. We use the techniques laid out in that paper, extend it from 2 to 7 tables, and tweak it to make it efficient and secure, for use in the Chia Blockchain. The document is divided into three main sections: What (mathematical definition of a proof of space), How (how to implement proof of space), and Why (motivation and explanation of the construction) sections. The Beyond Hellman paper can be read first for more mathematical background. Chia Proof of Space Construction Introduction What is Proof of Space? Definitions Proof format Proof Quality String Definition of parameters, and M, f, A, C functions: Parameters: f functions: Matching function M: A′ function: At function: Collation function C: How do we implement Proof of Space? Plotting Plotting Tables (Concepts) Tables Table Positions Compressing Entry Data Delta Format ANS Encoding of Delta Formatted Points Stub and Small Deltas Parks Checkpoint Tables Plotting Algorithm Final Disk Format Full algorithm Phase 1: Forward Propagation Phase 2: Backpropagation Phase 3: Compression Phase 4: Checkpoints Sort on Disk Plotting Performance Space Required Proving Proof ordering vs Plot ordering Proof Retrieval Quality String Retrieval Proving Performance Verification Construction -

Complementary Currencies: Mutual Credit Currency Systems and the Challenge of Globalization
Complementary Currencies: Mutual Credit Currency Systems and the Challenge of Globalization Clare Lascelles1 Abstract Complementary currencies—currencies operating alongside the official currency—have taken many forms throughout the last century or so. While their existence has a rich history, complementary currencies are increasingly viewed as anachronistic in a world where the forces of globalization promote further integration between economies and societies. Even so, towns across the globe have recently witnessed the introduction of complementary currencies in their region, which connotes a renewed emphasis on local identity. This paper explores the rationale behind the modern-day adoption of complementary currencies in a globalized system. I. Introduction Coined money has two sides: heads and tails. ‘Heads’ represents the state authority that issued the coin, while ‘tails’ displays the value of the coin as a medium of exchange. This duality—the “product of social organization both from the top down (‘states’) and from the bottom up (‘markets’)”—reveals the coin as “both a token of authority and a commodity with a price” (Hart, 1986). Yet, even as side ‘heads’ reminds us of the central authority that underwrote the coin, currency can exist outside state control. Indeed, as globalization exerts pressure toward financial integration, complementary currencies—currencies existing alongside the official currency—have become common in small towns and regions. This paper examines the rationale behind complementary currencies, with a focus on mutual credit currency, and concludes that the modern-day adoption of complementary currencies can be attributed to the depersonalizing force of globalization. II. Literature Review Money is certainly not a topic unstudied. -

IPFS and Friends: a Qualitative Comparison of Next Generation Peer-To-Peer Data Networks Erik Daniel and Florian Tschorsch
1 IPFS and Friends: A Qualitative Comparison of Next Generation Peer-to-Peer Data Networks Erik Daniel and Florian Tschorsch Abstract—Decentralized, distributed storage offers a way to types of files [1]. Napster and Gnutella marked the beginning reduce the impact of data silos as often fostered by centralized and were followed by many other P2P networks focusing on cloud storage. While the intentions of this trend are not new, the specialized application areas or novel network structures. For topic gained traction due to technological advancements, most notably blockchain networks. As a consequence, we observe that example, Freenet [2] realizes anonymous storage and retrieval. a new generation of peer-to-peer data networks emerges. In this Chord [3], CAN [4], and Pastry [5] provide protocols to survey paper, we therefore provide a technical overview of the maintain a structured overlay network topology. In particular, next generation data networks. We use select data networks to BitTorrent [6] received a lot of attention from both users and introduce general concepts and to emphasize new developments. the research community. BitTorrent introduced an incentive Specifically, we provide a deeper outline of the Interplanetary File System and a general overview of Swarm, the Hypercore Pro- mechanism to achieve Pareto efficiency, trying to improve tocol, SAFE, Storj, and Arweave. We identify common building network utilization achieving a higher level of robustness. We blocks and provide a qualitative comparison. From the overview, consider networks such as Napster, Gnutella, Freenet, BitTor- we derive future challenges and research goals concerning data rent, and many more as first generation P2P data networks, networks. -

Evaluating Inclusion, Equality, Security, and Privacy in Pseudonym Parties and Other Proofs of Personhood
Identity and Personhood in Digital Democracy: Evaluating Inclusion, Equality, Security, and Privacy in Pseudonym Parties and Other Proofs of Personhood Bryan Ford Swiss Federal Institute of Technology in Lausanne (EPFL) November 5, 2020 Abstract of enforced physical security and privacy can address the coercion and vote-buying risks that plague today’s E- Digital identity seems at first like a prerequisite for digi- voting and postal voting systems alike. We also examine tal democracy: how can we ensure “one person, one vote” other recently-proposed approaches to proof of person- online without identifying voters? But the full gamut of hood, some of which offer conveniencessuch as all-online digital identity solutions – e.g., online ID checking, bio- participation. These alternatives currently fall short of sat- metrics, self-sovereign identity, and social/trust networks isfying all the key digital personhood goals, unfortunately, – all present severe flaws in security, privacy, and trans- but offer valuable insights into the challenges we face. parency, leaving users vulnerable to exclusion, identity loss or theft, and coercion. These flaws may be insur- mountable because digital identity is a cart pulling the Contents horse. We cannot achieve digital identity secure enough to support the weight of digital democracy, until we can 1 Introduction 2 build it on a solid foundation of digital personhood meet- ing key requirements. While identity is about distinguish- 2 Goals for Digital Personhood 4 ing one person from another through attributes or affilia- tions, personhood is about giving all real people inalien- 3 Pseudonym Parties 5 able digital participation rights independent of identity, 3.1 Thebasicidea. -

Asymmetric Proof-Of-Work Based on the Generalized Birthday Problem
Equihash: Asymmetric Proof-of-Work Based on the Generalized Birthday Problem Alex Biryukov Dmitry Khovratovich University of Luxembourg University of Luxembourg [email protected] [email protected] Abstract—The proof-of-work is a central concept in modern Long before the rise of Bitcoin it was realized [20] that cryptocurrencies and denial-of-service protection tools, but the the dedicated hardware can produce a proof-of-work much requirement for fast verification so far made it an easy prey for faster and cheaper than a regular desktop or laptop. Thus the GPU-, ASIC-, and botnet-equipped users. The attempts to rely on users equipped with such hardware have an advantage over memory-intensive computations in order to remedy the disparity others, which eventually led the Bitcoin mining to concentrate between architectures have resulted in slow or broken schemes. in a few hardware farms of enormous size and high electricity In this paper we solve this open problem and show how to consumption. An advantage of the same order of magnitude construct an asymmetric proof-of-work (PoW) based on a compu- is given to “owners” of large botnets, which nowadays often tationally hard problem, which requires a lot of memory to gen- accommodate hundreds of thousands of machines. For prac- erate a proof (called ”memory-hardness” feature) but is instant tical DoS protection, this means that the early TLS puzzle to verify. Our primary proposal Equihash is a PoW based on the schemes [8], [17] are no longer effective against the most generalized birthday problem and enhanced Wagner’s algorithm powerful adversaries. -
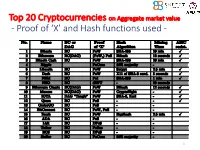
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Piecework: Generalized Outsourcing Control for Proofs of Work
(Short Paper): PieceWork: Generalized Outsourcing Control for Proofs of Work Philip Daian1, Ittay Eyal1, Ari Juels2, and Emin G¨unSirer1 1 Department of Computer Science, Cornell University, [email protected],[email protected],[email protected] 2 Jacobs Technion-Cornell Institute, Cornell Tech [email protected] Abstract. Most prominent cryptocurrencies utilize proof of work (PoW) to secure their operation, yet PoW suffers from two key undesirable prop- erties. First, the work done is generally wasted, not useful for anything but the gleaned security of the cryptocurrency. Second, PoW is natu- rally outsourceable, leading to inegalitarian concentration of power in the hands of few so-called pools that command large portions of the system's computation power. We introduce a general approach to constructing PoW called PieceWork that tackles both issues. In essence, PieceWork allows for a configurable fraction of PoW computation to be outsourced to workers. Its controlled outsourcing allows for reusing the work towards additional goals such as spam prevention and DoS mitigation, thereby reducing PoW waste. Meanwhile, PieceWork can be tuned to prevent excessive outsourcing. Doing so causes pool operation to be significantly more costly than today. This disincentivizes aggregation of work in mining pools. 1 Introduction Distributed cryptocurrencies such as Bitcoin [18] rely on the equivalence \com- putation = money." To generate a batch of coins, clients in a distributed cryp- tocurrency system perform an operation called mining. Mining requires solving a computationally intensive problem involving repeated cryptographic hashing. Such problem and its solution is called a Proof of Work (PoW) [11]. As currently designed, nearly all PoWs suffer from one of two drawbacks (or both, as in Bitcoin). -

Short Selling Attack: a Self-Destructive but Profitable 51% Attack on Pos Blockchains
Short Selling Attack: A Self-Destructive But Profitable 51% Attack On PoS Blockchains Suhyeon Lee and Seungjoo Kim CIST (Center for Information Security Technologies), Korea University, Korea Abstract—There have been several 51% attacks on Proof-of- With a PoS, the attacker needs to obtain 51% of the Work (PoW) blockchains recently, including Verge and Game- cryptocurrency to carry out a 51% attack. But unlike PoW, Credits, but the most noteworthy has been the attack that saw attacker in a PoS system is highly discouraged from launching hackers make off with up to $18 million after a successful double spend was executed on the Bitcoin Gold network. For this reason, 51% attack because he would have to risk of depreciation the Proof-of-Stake (PoS) algorithm, which already has advantages of his entire stake amount to do so. In comparison, bad of energy efficiency and throughput, is attracting attention as an actor in a PoW system will not lose their expensive alternative to the PoW algorithm. With a PoS, the attacker needs mining equipment if he launch a 51% attack. Moreover, to obtain 51% of the cryptocurrency to carry out a 51% attack. even if a 51% attack succeeds, the value of PoS-based But unlike PoW, attacker in a PoS system is highly discouraged from launching 51% attack because he would have to risk losing cryptocurrency will fall, and the attacker with the most stake his entire stake amount to do so. Moreover, even if a 51% attack will eventually lose the most. For these reasons, those who succeeds, the value of PoS-based cryptocurrency will fall, and attempt to attack 51% of the PoS blockchain will not be the attacker with the most stake will eventually lose the most. -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe. -

Blockchain and Cryptocurrency in Africa a Comparative Summary of the Reception and Regulation of Blockchain and Cryptocurrency in Africa
Blockchain and Cryptocurrency in Africa A comparative summary of the reception and regulation of Blockchain and Cryptocurrency in Africa 2018 Baker McKenzie, Johannesburg IMPORTANT DISCLAIMER: The material in this report is of the nature of general comment only. It is not offered as legal advice on any specific issue or matter and should not be taken as such. Readers should refrain from acting on the basis of any discussion contained in this report without obtaining specific legal advice on the particular facts and circumstances at issue. While the authors have made every effort to provide accurate and up-to-date information on laws and policy, these matters are continuously subject to change. Furthermore, the application of these laws depends on the particular facts and circumstances of each situation, and therefore readers should consult their lawyer before taking any action. Information contained herein is as at November 2018. CONTENTS PREFACE ............................................................................................................................................1 GEOGRAPHICAL OVERVIEW ....................................................................................................... 2 COUNTRY PROFILES ..................................................................................................................... 3 1. Botswana ................................................................................................................................................................... 3 2. Ghana .........................................................................................................................................................................4 -

How to Not Get Caught When You Launder Money on Blockchain?
How to Not Get Caught When You Launder Money on Blockchain? Cuneyt G. Akcora1, Sudhanva Purusotham2, Yulia R. Gel2 Mitchell Krawiec-Thayer3, Murat Kantarcioglu2 1University of Manitoba, 2 UT Dallas, 3 Monero Research Lab 65 Chancellor Circle Winnipeg, MB, Canada R3T 2N2 [email protected], fSudhanva.Purushotham, ygl, [email protected], [email protected] Abstract transactions and circumvent existing AI-based money laun- dering techniques. Our insights, however, are intended not to The number of blockchain users has tremendously grown in assist criminals to obfuscate their malicious activities but to recent years. As an unintended consequence, e-crime trans- motivate the AI community for further research in this area actions on blockchains has been on the rise. Consequently, public blockchains have become a hotbed of research for de- of critical societal importance and, as a result, to advance veloping AI tools to detect and trace users and transactions the state of art methodology in the AI-based cryptocurrency that are related to e-crime. money laundering detection. We argue that following a few select strategies can make In the remainder of this paper, we first identify tech- money laundering on blockchain virtually undetectable with niques that can be used by criminals to launder money on most of the currently existing tools and algorithms. As a re- blockchain and then empirically show why these techniques sult, the effective combating of e-crime activities involving would be effective in hiding patterns used by potential AI cryptocurrencies requires the development of novel analytic models. methodology in AI. 2 Related Work 1 Introduction The success of Bitcoin (Nakamoto 2008) has encouraged Cryptocurrencies have emerged as an important rapidly hundreds of similar digital coins (Tschorsch and Scheuer- evolving financial tool that allows for cross-border transac- mann 2016). -

Coinbase Explores Crypto ETF (9/6) Coinbase Spoke to Asset Manager Blackrock About Creating a Crypto ETF, Business Insider Reports
Crypto Week in Review (9/1-9/7) Goldman Sachs CFO Denies Crypto Strategy Shift (9/6) GS CFO Marty Chavez addressed claims from an unsubstantiated report earlier this week that the firm may be delaying previous plans to open a crypto trading desk, calling the report “fake news”. Coinbase Explores Crypto ETF (9/6) Coinbase spoke to asset manager BlackRock about creating a crypto ETF, Business Insider reports. While the current status of the discussions is unclear, BlackRock is said to have “no interest in being a crypto fund issuer,” and SEC approval in the near term remains uncertain. Looking ahead, the Wednesday confirmation of Trump nominee Elad Roisman has the potential to tip the scales towards a more favorable cryptoasset approach. Twitter CEO Comments on Blockchain (9/5) Twitter CEO Jack Dorsey, speaking in a congressional hearing, indicated that blockchain technology could prove useful for “distributed trust and distributed enforcement.” The platform, given its struggles with how best to address fraud, harassment, and other misuse, could be a prime testing ground for decentralized identity solutions. Ripio Facilitates Peer-to-Peer Loans (9/5) Ripio began to facilitate blockchain powered peer-to-peer loans, available to wallet users in Argentina, Mexico, and Brazil. The loans, which utilize the Ripple Credit Network (RCN) token, are funded in RCN and dispensed to users in fiat through a network of local partners. Since all details of the loan and payments are recorded on the Ethereum blockchain, the solution could contribute to wider access to credit for the unbanked. IBM’s Payment Protocol Out of Beta (9/4) Blockchain World Wire, a global blockchain based payments network by IBM, is out of beta, CoinDesk reports.