An Algorithm for the Detection of Move Repetition Without the Use of Hash-Keys
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

View 2020 Circular
2020 South African Junior Chess Championships 2020 Wild Card Chess Championship 2020 South Africa Junior Blitz Chess Championships 2020 South Africa Doubles Chess Championships 2020 Inter Regional Team Chess Championship 3 to 12 January 2021 Hosted by 4 Knights International Events Company CIRCULAR 1 Version 1.0 26 September 2020 Table of Contents 1. LOCAL ORGANIZING COMMITTEE (LOC) 5 1. CONVENER................................................................................................................................................. 5 2. TREASURER ................................................................................................................................................ 5 3. TECHNICAL DIRECTOR .................................................................................................................................. 5 4. CHIEF ARBITER ........................................................................................................................................... 5 5. ACCOMMODATION...................................................................................................................................... 5 6. MEDIA AND PHOTO’S .................................................................................................................................. 5 7. PUBLIC RELATIONS ...................................................................................................................................... 5 8. LOGISTICS ................................................................................................................................................. -

Learning Long-Term Chess Strategies from Databases
Mach Learn (2006) 63:329–340 DOI 10.1007/s10994-006-6747-7 TECHNICAL NOTE Learning long-term chess strategies from databases Aleksander Sadikov · Ivan Bratko Received: March 10, 2005 / Revised: December 14, 2005 / Accepted: December 21, 2005 / Published online: 28 March 2006 Springer Science + Business Media, LLC 2006 Abstract We propose an approach to the learning of long-term plans for playing chess endgames. We assume that a computer-generated database for an endgame is available, such as the king and rook vs. king, or king and queen vs. king and rook endgame. For each position in the endgame, the database gives the “value” of the position in terms of the minimum number of moves needed by the stronger side to win given that both sides play optimally. We propose a method for automatically dividing the endgame into stages characterised by different objectives of play. For each stage of such a game plan, a stage- specific evaluation function is induced, to be used by minimax search when playing the endgame. We aim at learning playing strategies that give good insight into the principles of playing specific endgames. Games played by these strategies should resemble human expert’s play in achieving goals and subgoals reliably, but not necessarily as quickly as possible. Keywords Machine learning . Computer chess . Long-term Strategy . Chess endgames . Chess databases 1. Introduction The standard approach used in chess playing programs relies on the minimax principle, efficiently implemented by alpha-beta algorithm, plus a heuristic evaluation function. This approach has proved to work particularly well in situations in which short-term tactics are prevalent, when evaluation function can easily recognise within the search horizon the con- sequences of good or bad moves. -

Rules & Regulations for the Candidates Tournament of the FIDE
Rules & regulations for the Candidates Tournament of the FIDE World Championship cycle 2012-2014 1. Organisation 1. 1 The Candidates Tournament to determine the challenger for the 2014 World Chess Championship Match shall be organised in the first quarter of 2014 and represent an integral part of the World Chess Championship regulations for the cycle 2012- 2014. Eight (8) players will participate in the Candidates Tournament and the winner qualifies for the World Chess Championship Match in the first quarter of 2014. 1. 2 Governing Body: the World Chess Federation (FIDE). For the purpose of creating the regulations, communicating with the players and negotiating with the organisers, the FIDE President has nominated a committee, hereby called the FIDE Commission for World Championships and Olympiads (hereinafter referred to as WCOC) 1. 3 FIDE, or its appointed commercial agency, retains all commercial and media rights of the Candidates Tournament, including internet rights. These rights can be transferred to the organiser upon agreement. 1. 4 Upon recommendation by the WCOC, the body responsible for any changes to these Regulations is the FIDE Presidential Board. 1. 5 At any time in the course of the application of these Regulations, any circumstances that are not covered or any unforeseen event shall be referred to the President of FIDE for final decision. 2. Qualification for the 2014 Candidates Tournament The players who qualify for the Candidates Tournament are determined according to the following, in order of priority: 2. 1 World Championship Match 2013 - The player who lost the 2013 World Championship Match qualifies. 2. 2 World Cup 2013 - The two (2) top winners of the World Cup 2013 qualify. -

Super Human Chess Engine
SUPER HUMAN CHESS ENGINE FIDE Master / FIDE Trainer Charles Storey PGCE WORLD TOUR Young Masters Training Program SUPER HUMAN CHESS ENGINE Contents Contents .................................................................................................................................................. 1 INTRODUCTION ....................................................................................................................................... 2 Power Principles...................................................................................................................................... 4 Human Opening Book ............................................................................................................................. 5 ‘The Core’ Super Human Chess Engine 2020 ......................................................................................... 6 Acronym Algorthims that make The Storey Human Chess Engine ......................................................... 8 4Ps Prioritise Poorly Placed Pieces ................................................................................................... 10 CCTV Checks / Captures / Threats / Vulnerabilities ...................................................................... 11 CCTV 2.0 Checks / Checkmate Threats / Captures / Threats / Vulnerabilities ............................. 11 DAFiii Attack / Features / Initiative / I for tactics / Ideas (crazy) ................................................. 12 The Fruit Tree analysis process ............................................................................................................ -

Chess-Training-Guide.Pdf
Q Chess Training Guide K for Teachers and Parents Created by Grandmaster Susan Polgar U.S. Chess Hall of Fame Inductee President and Founder of the Susan Polgar Foundation Director of SPICE (Susan Polgar Institute for Chess Excellence) at Webster University FIDE Senior Chess Trainer 2006 Women’s World Chess Cup Champion Winner of 4 Women’s World Chess Championships The only World Champion in history to win the Triple-Crown (Blitz, Rapid and Classical) 12 Olympic Medals (5 Gold, 4 Silver, 3 Bronze) 3-time US Open Blitz Champion #1 ranked woman player in the United States Ranked #1 in the world at age 15 and in the top 3 for about 25 consecutive years 1st woman in history to qualify for the Men’s World Championship 1st woman in history to earn the Grandmaster title 1st woman in history to coach a Men's Division I team to 7 consecutive Final Four Championships 1st woman in history to coach the #1 ranked Men's Division I team in the nation pnlrqk KQRLNP Get Smart! Play Chess! www.ChessDailyNews.com www.twitter.com/SusanPolgar www.facebook.com/SusanPolgarChess www.instagram.com/SusanPolgarChess www.SusanPolgar.com www.SusanPolgarFoundation.org SPF Chess Training Program for Teachers © Page 1 7/2/2019 Lesson 1 Lesson goals: Excite kids about the fun game of chess Relate the cool history of chess Incorporate chess with education: Learning about India and Persia Incorporate chess with education: Learning about the chess board and its coordinates Who invented chess and why? Talk about India / Persia – connects to Geography Tell the story of “seed”. -
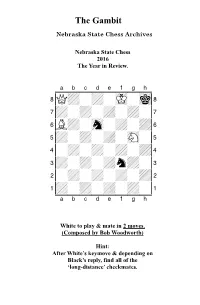
2016 Year in Review
The Gambit Nebraska State Chess Archives Nebraska State Chess 2016 The Year in Review. XABCDEFGHY 8Q+-+-mK-mk( 7+-+-+-+-' 6L+-sn-+-+& 5+-+-+-sN-% 4-+-+-+-+$ 3+-+-+n+-# 2-+-+-+-+" 1+-+-+-+-! xabcdefghy White to play & mate in 2 moves. (Composed by Bob Woodworth) Hint: After White’s keymove & depending on Black’s reply, find all of the ‘long-distance’ checkmates. Gambit Editor- Kent Nelson The Gambit serves as the official publication of the Nebraska State Chess Association and is published by the Lincoln Chess Foundation. Send all games, articles, and editorial materials to: Kent Nelson 4014 “N” St Lincoln, NE 68510 [email protected] NSCA Officers President John Hartmann Treasurer Lucy Ruf Historical Archivist Bob Woodworth Secretary Gnanasekar Arputhaswamy Webmaster Kent Smotherman Regional VPs NSCA Committee Members Vice President-Lincoln- John Linscott Vice President-Omaha- Michael Gooch Vice President (Western) Letter from NSCA President John Hartmann January 2017 Hello friends! Our beloved game finds itself at something of a crossroads here in Nebraska. On the one hand, there is much to look forward to. We have a full calendar of scholastic events coming up this spring and a slew of promising juniors to steal our rating points. We have more and better adult players playing rated chess. If you’re reading this, we probably (finally) have a functional website. And after a precarious few weeks, the Spence Chess Club here in Omaha seems to have found a new home. And yet, there is also cause for concern. It’s not clear that we will be able to have tournaments at UNO in the future. -

An Arbiter's Notebook
Fifty-move Confusion Visit Shop.ChessCafe.com for the largest selection of chess books, sets, and clocks in Question Hello, Geurt. Nowadays there is no specific rule for a draw by North America: perpetual check. Yet somehow I remember there being one; where you could claim a draw by showing the arbiter that you could keep checking whatever the opponent did against any legal move. My memory is that the rule was scrapped just a few years ago, because threefold repetition and the fifty-move rule are good enough. After a bit of Googling around, I noticed firstly that the rule was removed much earlier than I could possibly remember (in the fifties?) and secondly that nobody seems to know when exactly it happened. Do you know when the rule was An Arbiter’s removed from the Laws of Chess? Are there older versions of the Laws available online somewhere? Thank you very much, Remco Gerlich Notebook (The Netherlands) Answer I am not sure whether perpetual check was ever included in the Chess Informant 85 Geurt Gijssen Laws of Chess. Kazic’s The Chess Competitor’s Handbook, published in Only .99 cents! 1980, does not mention it. But there is a very interesting item in this Handbook, which was dates back to 1958: FIDE INTERPRETATION ART 12.4 (1958A) Question: Can a player lose the game by exceeding the time-limit when the position is such that no mate is possible, whatever continuation the players may employ (this concerns Part II of the Laws)? Answer: The Commission declares that the Laws must be interpreted in such a way that in this case, as in the case of perpetual check, a draw cannot be decreed against the will of one of the players before the situation in Article 12.4 is attained. -

Quick Guide by Steven Craig Miller
A Quick Guide by Steven Craig Miller Tournament etiquette is a lot simpler than table manners . We expect Scholastic Players to always demonstrate the following basic courtesies : 1. Do your best to show up on time , as this is considerate, and extreme tardiness can cause a game to be forfeited. 2. Shake your opponent's hand as soon as you meet them at the table, tell them your name, and wish them good luck. 3. Don't talk to your opponent during the game , or answer your opponent if they speak to you, except in three cases: to say "I resign" if you want to (though this may also be accomplished simply by gently tipping your king over), to ask your opponent if they will agree to a draw , or to announce "j'doube" (or "I adjust," when straightening a piece). It is not necessary to announce "check," though you may do so if you like. If you have an important question or concern, stop both sides of the clock, raise your hand and quietly wait for a tournament official's help. 4. If your opponent refuses your offer of a draw, don't keep repeating the draw offer on each subsequent move--this is considered bad form. 5. Noisy or messy eating (or gum chewing) is not allowed . 6. Avoid making tapping noises or doing anything that may annoy or distract your opponent or the other players around you. If you encounter someone else doing something like this, and it is making it very hard for you to concentrate on the game, raise your hand for a tournament official's assistance and politely explain the situation to them. -

An Arbiter's Notebook
10.2 Again Purchases from our shop help keep ChessCafe.com freely accessible: Question: Dear, Mr. Gijssen. I was playing in a tournament and the board next to me played this game: 1.Nf3 Nf6 2.Ng1 Ng8 3.Nf3 Nf6 4.Ng1 Ng8. When a draw was claimed, the arbiter demanded that both players replay the game. When one of them refused, the arbiter forfeited them. Does the opening position count for purposes of threefold repetition? Matthew Larson (UK) Answer In my opinion, the arbiter was right not to accept this game. I refer to Article 12.1 of the Laws of Chess: An Arbiter’s The players shall take no action that will bring the game of chess into disrepute. Notebook To produce a "game" as mentioned in your letter brings the game of chess The Greatest Tournaments into disrepute. The only element in your letter that puzzles me is the fact that Geurt Gijssen 2001-2009 the arbiter forfeited both players, although only one refused to play a new by Chess Informant game. The question of the threefold repetition is immaterial in this case. Question Greetings, Mr. Gijssen. I acted as a member of the appeals committee in a rapid chess tournament (G60/sudden death). I also won that tournament, but I am not a strong player, just 2100 FIDE, with a good understanding of the rules. The incident is as follows: A player lost a game and signed the score sheet, and then he appealed the decision of the arbiter to the committee with regards to some bad rulings during the game. -

Kasparov's Nightmare!! Bobby Fischer Challenges IBM to Simul IBM
California Chess Journal Volume 20, Number 2 April 1st 2004 $4.50 Kasparov’s Nightmare!! Bobby Fischer Challenges IBM to Simul IBM Scrambles to Build 25 Deep Blues! Past Vs Future Special Issue • Young Fischer Fires Up S.F. • Fischer commentates 4 Boyscouts • Building your “Super Computer” • Building Fischer’s Dream House • Raise $500 playing chess! • Fischer Articles Galore! California Chess Journal Table of Con tents 2004 Cal Chess Scholastic Championships The annual scholastic tourney finishes in Santa Clara.......................................................3 FISCHER AND THE DEEP BLUE Editor: Eric Hicks Contributors: Daren Dillinger A miracle has happened in the Phillipines!......................................................................4 FM Eric Schiller IM John Donaldson Why Every Chess Player Needs a Computer Photographers: Richard Shorman Some titles speak for themselves......................................................................................5 Historical Consul: Kerry Lawless Founding Editor: Hans Poschmann Building Your Chess Dream Machine Some helpful hints when shopping for a silicon chess opponent........................................6 CalChess Board Young Fischer in San Francisco 1957 A complet accounting of an untold story that happened here in the bay area...................12 President: Elizabeth Shaughnessy Vice-President: Josh Bowman 1957 Fischer Game Spotlight Treasurer: Richard Peterson One game from the tournament commentated move by move.........................................16 Members at -

The Truth About Chess Rating 1 the Rating Expectation Function
The Truth about Chess Rating Vladica Andreji´c University of Belgrade, Faculty of Mathematics, Serbia email: [email protected] 1 The Rating Expectation Function The main problem of chess rating system is to determine the f function, which assigns probability to rating difference i.e. to the expected result. It actually means that if the player A whose rating is RA plays N games against the player B whose rating is RB, one can expect that A will score N · f(RA − RB) points i.e. final ratio of points in the match where A plays against B will be f(RA − RB): f(RB − RA), where f(RB − RA) = 1 − f(RA − RB). Behaviour of chess rating depends on the f function whose features can be observed in the simplest nontrivial case of extensive series of games played between three players A, B and C. In case that we know the final score of the match between A and B as well as the score of the match where B plays against C, will it be possible to predict the score of the match where A plays against C? One of potential hypotheses is that the nature of rating system preserves established ratios. It actually means that if A and B play, and the result is consistent with a : b ratio, and B and C play and the result is consistent with b : c ratio, we expect A and C to play so that the result is consistent with a : c ratio. If we introduce x and y to respectively denote the rating difference between A and B, and B and C, the hypothesis could be expressed as the following functional equation (f(x + y)) : (1 − f(x + y)) = (f(x)f(y)) : ((1 − f(x))(1 − f(y))); (1) that is valid for each real x and y. -

Extended Null-Move Reductions
Extended Null-Move Reductions Omid David-Tabibi1 and Nathan S. Netanyahu1,2 1 Department of Computer Science, Bar-Ilan University, Ramat-Gan 52900, Israel [email protected], [email protected] 2 Center for Automation Research, University of Maryland, College Park, MD 20742, USA [email protected] Abstract. In this paper we review the conventional versions of null- move pruning, and present our enhancements which allow for a deeper search with greater accuracy. While the conventional versions of null- move pruning use reduction values of R ≤ 3, we use an aggressive re- duction value of R = 4 within a verified adaptive configuration which maximizes the benefit from the more aggressive pruning, while limiting its tactical liabilities. Our experimental results using our grandmaster- level chess program, Falcon, show that our null-move reductions (NMR) outperform the conventional methods, with the tactical benefits of the deeper search dominating the deficiencies. Moreover, unlike standard null-move pruning, which fails badly in zugzwang positions, NMR is impervious to zugzwangs. Finally, the implementation of NMR in any program already using null-move pruning requires a modification of only a few lines of code. 1 Introduction Chess programs trying to search the same way humans think by generating “plausible” moves dominated until the mid-1970s. By using extensive chess knowledge at each node, these programs selected a few moves which they consid- ered plausible, and thus pruned large parts of the search tree. However, plausible- move generating programs had serious tactical shortcomings, and as soon as brute-force search programs such as Tech [17] and Chess 4.x [29] managed to reach depths of 5 plies and more, plausible-move generating programs fre- quently lost to brute-force searchers due to their tactical weaknesses.