And Unit Code As Your Motion Sensor (MS16A) and the Same Housecode As Your Transceiver (TM751)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security Evaluation of the Z-Wave Wireless Protocol
Security Evaluation of the Z-Wave Wireless Protocol Behrang Fouladi Sahand Ghanoun SensePost UK Ltd. [email protected] [email protected] Abstract — The Z-Wave wireless communication protocol has ZigBee protocol with regards to home automation. This is been widely used in home automation and wireless sensors partly due to interoperability of devices and shorter time to networks. Z-Wave is based on a proprietary design and a sole market on the vendor side. Another benefit is that it is less chip vendor. There have been a number of academic and subjected to signal interference compared to the ZigBee practical security researches on home automation systems based protocol, which operates on the widely populated 2.4 GHz on ZigBee and X10 protocols, however, no public vulnerability research on Z-Wave could be found prior to this work. band shared by both Bluetooth and Wi-Fi devices. The In this paper, we analyze the Z-Wave protocol stack layers and protocol specification and software development kit (SDK) [4] design a radio packet capture device and related software named are not open and only available to the device manufacturers Z-Force to intercept Z-Wave communications. This device (OEMs) who have signed an NDA with Sigma Designs. The enables us to decode different layers of the Z-Wave protocol and SDK costs between 1500 to 3500 US dollars and the NDA study the implementation of encryption and data origin prevents OEMs from disclosing the content of the SDK authentication in the application layer. We then present the publically. The aim of this research is to build a low cost Z- details of a vulnerability discovered using Z-Force tool in AES Wave packet capture and injection tool which facilitates the encrypted Z-Wave door locks that can be remotely exploited to security testing of home automation systems as well as aides unlock doors without the knowledge of the encryption keys. -

Simon XT User Manual
Simon XT User Manual P/N 466-2266 • REV F • OCT13 Copyright © 2012 UTC Fire & Security Americas Corporation, Inc. Interlogix is part of UTC Climate Controls & Security, a unit of United Technologies Corporation. All rights reserved. Disclaimer The information in this document is subject to change without notice. UTC Fire & Security, assumes no responsibility for inaccuracies or omissions and specifically disclaims any liabilities, losses, or risks, personal or otherwise, incurred as a consequence, directly or indirectly, of the use or application of any of the contents of this document. For the latest documentation, contact your local supplier or visit us online at http://www.utcfireandsecurity.com/. This publication may contain examples of screen captures and reports used in daily operations. Examples may include fictitious names of individuals and companies. Any similarity to names and addresses of actual businesses or persons is entirely coincidental. Trademarks and Simon and Simon XT are trademarks of UTC Fire & Security. patents Other trade names used in this document may be trademarks or registered trademarks of the manufacturers or vendors of the respective products. Manufacturer UTC Fire & Security Americas Corporation, Inc. 1275 Red Fox Rd., Arden Hills, MN 55112-6943, USA Software license Important: This end-user license agreement (“Agreement”) is a legal agreement between UTC FIRE & agreement SECURITY and You. Read the follow ing terms and conditions carefully before installing or using this Software. This agreement provides a license from UTC FIRE & SECURITY to use the Software. It also contains warranty information, disclaimers, and liability limitations. Installing and/or using the Software confirms Your agreement to be bound by these terms and conditions. -

Getting Started with HCA and X10
Getting Started with HCA and X10 This Getting Started Guide continues from the previous “Getting Started with HCA – Installation and Introduction” which covers installing HCA and the basic operations available from the ribbon. This guide assumes that you have reviewed that. In this guide these topics are covered. • Connecting an X10 capable interface to HCA • Creating a new design file • Adding X10 devices using the HCA Designer • Controlling devices from the HCA user interface • Scheduling a device to come on at sunset • Responding to a button press on a keypad If you have not already purchased HCA and you are looking to test drive this software, you can download a free 30-day trial of HCA Plus from the HCA support website at www.HomeControlAssistant.com. Connecting the X10 interface to HCA Before HCA can control X10 devices in your home, you must connect an interface to your computer. There are several different interfaces that can send and receive X10 signals. We recommend that you use the Smart Home PowerLinc model 2413. The advantage of that interface is that it can send and receive both the older X10 signals and the newer Insteon signals. That lets you use your existing devices but add newer ones and be able to control both. Instructions for installing the 2413 PowerLinc can be found in the Getting Started with HCA and Insteon guide. You can also use the older CM11 and CM15 interfaces. The CM11 is a serial interface and can be connected to the computer and the communications port it uses is specified in the HCA hardware setup. -

X10 Debugging Tips
X10 DEBUGGING TIPS INTRODUCTION Although X10 powerline communications provides many great benefits, one of its biggest downsides is the potential reliability problems. In fact, the most frequent questions we receive from HomeVision users are about X10 problems in their homes. Over the years we’ve learned some good ways to help isolate these problems. We hope that these tips will help if you run into X10 problems, even if you’re using a different home automation system. Problems can generally be grouped into two categories: 1. Major problems: X10 never works 2. Intermittent problems: X10 sometimes works There are many possible things that can cause such X10 problems. We will discuss troubleshooting the major problems, then address the much more common intermittent X10 problems. SOLVING MAJOR X10 PROBLEMS Let’s start with the worst-case scenario: HomeVision is neither sending nor receiving X10 commands. In this situation, the problem lies in one of four places: 1. The HomeVision controller. 2. The X10 powerline interface device. This is usually a TW-523 or PSC05, although there are others. We’ll refer to all of them as “TW-523” in this article. 3. The cable connecting the HomeVision controller to the TW-523. 4. A serious X10 signal degradation problem in your home. So how do we troubleshoot these? Here goes … Check the TW-523 Module LED First, verify that the red LED on the TW-523 module is lit. If not, make sure it’s plugged into a live circuit. If the LED is still not lit, then the TW-523 is defective. -
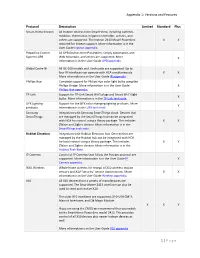
Appendix 1: Versions and Features 1 | Page Protocol Description Limited
Appendix 1: Versions and Features Protocol Description Limited Standard Plus Smart-Home Insteon All Insteon devices from SmartHome, including switches, modules, thermostat, irrigation controller, sensors, and others are supported. The Insteon 2413 Model PowerLinc X X required for Insteon support. More information is in the User Guide Insteon appendix. Powerline Control All UPB Devices from PulseWorx, Simply Automated, and Systems UPB Web Mountain, and others are supported. More X information is in the User Guide UPB appendix. Global Cache IR All GC-100 models and iTach units are supported. Up to four IR Interfaces can operate with HCA simultaneously. X X More information is in the User Guide IR appendix. Phillips Hue Complete support for Philips Hue color light bulbs using the Phillips Bridge. More information is in the User Guide X Phillips Hue appendix. TP-Link Support for TP-Link Smart Wi-Fi plugs and Smart Wi-Fi light X bulbs. More information is in the TP-Link tech note. LIFX Lighting Support for the LIFX color changing lighting products. More X products information is in the LIFX tech note. Samsung Integration with Samsung SmartThings cloud. Devices that SmartThings are managed by the SmartThings hub can be integrated with HCA for control using a library package. This includes X X ZWave and Zigbee devices. More information is in the SmartThings tech note. Hubitat Elevation Integration with Hubitat Elevation hub. Devices that are managed by the Hubitat hub can be integrated with HCA for local control using a library package. This includes X X ZWave and Zigbee devices. More information is in the Hubitat Tech Note. -

SMART AUTOMATION SYSTEM BASED on WIRELESS and Iot
Vol-3 Issue-2 2017 IJARIIE-ISSN(O)-2395-4396 SMART AUTOMATION SYSTEM BASED ON WIRELESS AND IoT Miss.Chetashri Prakash Purandare 1, Prof. D. D. Patil 2 1 Third Year Engineering Student, Department of Computer Science & Engineering, Hindi Seva Mandal’s, Shri Sant Gadge Baba College of Engineering & Technology, Bhusawal - 425203, Dist. – Jalgaon, Maharashtra, India. 2 Associate Professor & Head, Department of Computer Science & Engineering, Hindi Seva Mandal’s, Shri Sant Gadge Baba College of Engineering & Technology, Bhusawal - 425203, Dist. – Jalgaon, Maharashtra, India y ABSTRACT Today technologies have changed every aspect of comfort & luxury. Our residential solutions for lighting, safety, audio and video, energy management reflects the superiority in terms of next generation technology which offers safety and comfort. Smart Automation will help you in realizing your dreams and imagination with the help of wireless technologies. The purpose of home automation system using internet and wireless networks is to control the parameters like voltage, current and temperature and monitor it. It helps to improve the performance of control network. IoT (Internet of Things) is fast rising technology which involves interaction among object (things) through internet without human interference. The main objective of using smart automation based on wireless and IoT is to reduce the unnecessary energy consumption of smart home. Keyword: - Smart automation, Internet of Things (IoT), Wireless, Energy control, Sensors, Smart living. 1. INTRODUCTION In the past decade, due to the increase in high speed communication networks and increased Internet use, interest in the smart home has grown. The concept of smart home is the environment where information technologies are being employed to assist and support people everyday activities [2]. -

Smart Assistants for Smart Homes
Smart assistants for smart homes KATHARINA RASCH Doctoral Thesis in Electronic and Computer Systems Stockholm, Sweden 2013 TRITA-ICT/ECS AVH 13:16 KTH School of Information and 1653-6363 Communication Technology KTH/ICT/ECS/AVH-13/16-SE SE 164-40 Kista 978-91-7501-837-9 SWEDEN Akademisk avhandling som med tillstånd av Kungliga Tekniska Högskolan framlägges till offentlig granskning för avläggande av teknologie doktorsexamen i elektronik och datorsystem den 11 Oktober 2013 klockan 13 i Sal E, Forum Isafjordsgatan 39, Kista, Kungliga Tekniska Högskolan. © Katharina Rasch, September 2013 Tryck: Universitetsservice US AB iii Abstract The smarter homes of tomorrow promise to increase comfort, aid elderly and disabled people, and help inhabitants save energy. Unfortunately, smart homes today are far from this vision – people who already live in such a home struggle with complicated user interfaces, inflexible home configurations, and difficult installation procedures. Under these circumstances, smart homes are not ready for mass adoption. This dissertation addresses these issues by proposing two smart assistants for smart homes. The first assistant is a recommender system that suggests useful services (i.e actions that the home can perform for the user). The recommended services are fitted to the user’s current situation, habits, and preferences. With these recommendations it is possible to build much simpler user interfaces that highlight the most interesting choices currently available. Configuration becomes much more flexible: since the recommender system automatically learns user habits, user routines no longer have to be manually described. Evaluations with two smart home datasets show that the correct service is included in the top five recommendations in 90% of all cases. -

Space Requirements
OPTIMIZE TION OF ENVIROMENTAL CONTROL TO FIT LIVING SPACE REQUIREMENTS A Senior Thesis By Maxim S. Eckmann 1997-98 University Undergraduate Research Fellow Texas A&M University Group: Engineering II Optimization of Environmental Control to Fit Living Space Requirements by Maxim S. Eckmann Submitted to the Office of Honors Programs and Academic Scholarships Texas A&M University in partial fulfillment of the requirements for 1997-98 UNIVERSITY UNDERGRADUATE RESEARCH FELLOWS PROGRAM April 16, 1998 Approved as to style and content by: Dr. William Hyman (Fac Advisor) Department Head, Biomedical Engineering Susanna Finnell, Executive Director Honors Programs and Academic Scholarships Fellows Group: Engineering II Optimization of Environmental Control to Fit Living Space Requirements Maxim S. Eckmann Biomedical Engineering Undergraduate Program Texas A&M University ABSTRACT This study examines the application of Environmental Control Systems (ECSsl for people with disabilities who live in the dormitory. ECSs allow people with disabilities to control appliances in their homes and parameters in their environment. The purpose of this study is to analyze effectiveness and efficiency of current ECSs when they are used in this setting, and formulate ways of reducing the cost and complexity of these systems. ECSs are compared against the needs of a real client with disabilities who lives in a dormitory room on the Texas ARM University main campus. General conclusions about the strengths and weakncsscs of the systems, when applied to the small living space, arc formulated. Alternative ECS designs are conceived and discussed. Finally, an example ECS component subsystem design is produced in detail. April 16, 1998 Table of Contents Illustrations v Sumtnary vl Introduction. -

Wall Receptacle Module, Model SR227
Wall Receptacle Module, Model SR227 The SR227 Wall Receptacle Module is designed to control unrestricted loads up Check Out our Web site at: to 15 Amps. It has two outlets, the upper one is X10 controlled and the lower one is always on. The SR227 does not respond to All Lights On. www.x10.com Installation • Turn the power off at the circuit breaker panel. For more information on X10 products and • Remove the wall plate and unscrew the old receptacle from its box. special promotional offers. • Disconnect the wiring to the old receptacle. • Connect the black wire on the SR227 to Live (black wire), connect the white wire on the SR227 to Neutral (white wire), and connect the green wire on the SR227 to ground (or to a metal wall box) using the wire nuts provided. Refer to the diagram above. X10 Wireless Technology, Inc. 90 Day Limited Warranty • Refi t the SR227 in the wall box and fi nish off with the trim plate provided. X10.com, a division of X10 Wireless Technology, Inc. (X10) warrants X10 products to be Turn the power back on at the circuit breaker panel. free from defective material and workmanship for a period of 90 days from the original date Setting up the SR227 Wall Receptacle Module of purchase at retail. X10 agrees to repair or replace, at it’s sole discretion, a defective X10 • Using a small screwdriver, set the black Unit Code dial to an unused code that product if returned to X10 within the warranty period and with proof of purchase. -

Home Control Assistant Version 12 User Guide
Home Control Assistant Version 12 User Guide WWW.HCATech.com The information contained in this document is subject to change without notice. Advanced Quonset Technology, Inc. provides this information “as is” without warranty of any kind, either expressed or implied, but not limited to the implied warranty of mechantability and fitness for a particular purpose. Advanced Quonset Technology, Inc. may improve or change the product at any time without further notice; this document does not represent a commitment on the part of Advanced Quonset Technology, Inc. The software described in this document is furnished under a license agreement or nondisclosure agreement. The software may be used or copied only in accordance with the terms of the licensing agreement. Windows is a registered trademark, and Windows NT is a trademark of Microsoft Corporation. All other product names and services identified in this document are trademarks or registered trademarks of their respective companies and are used throughout this document in editorial fashion only and for the benefit of such companies. No such uses, or the use of any trade name, is intended to convey an endorsement or other affiliation with Advanced Quonset Technology, Inc. © 2001-2013 Advanced Quonset Technology, Inc. All rights reserved. Printed in the U.S.A. November 30, 2013 Chapter 1 What is the Home Control Assistant?............................................................................................................1 About this guide.........................................................................................................................................................1 -

Lighting Control White Paper
Lighting Control White Paper A Brief Technology Overview of the Lighting Control Marketplace X-10, Insteon, Z-Wave, ZigBee, RadioRA2, Universal Powerline Bus (UPB) Fuchsia Research Corporation August 2014 Introduction When considering lighting control and home automation, there are many options in the marketplace, to include selection of a supplier, technology, company’s breadth of product line, ease of use, ease of installation, and service and support. Doing a Google search for ‘home automation’ or ‘lighting control’ can many times lead to confusion, resulting in head scratching ‘chaos’, given the information provided blogs, trade publications, hobbyists, and DIYers, many times provides incomplete and sometimes incorrect information. If you have a multi-million dollar primary or vacation home, working with a high-end/cost architect, have a $50,000-$100,000+ budget for home automation and/or lighting control, this White Paper is probably not for you. This White Paper is for the rest of us, objective, to provide a general overview of the market, technologies, and assist in your selection of a home automation lighting control solution to best meet your needs – and budget. X-10 X-10 was developed in 1975 by Pico Electronics of Glenrothes, Scotland. It uses primarily power line wiring for signaling and control, the signals involve radio frequency bursts representing digital information. X-10 has led the way using powerline communication over the past 40 years and could easily be considered the father of home automation. Some thoughts considering X-10. Select X-10 if you have a very limited budget, no more than $10-$15 per device. -

Practical Computerized Home Automation
Practical Computerized Home Automation BRUCE MOMJIAN Home automation is computer control of home devices, typically electrical. Using inexpensive hardware and open source software, it is possible to programmatically control many devices in your home, providing ease and enjoyment for your family. https://momjian.us/presentations Creative Commons Attribution License images are copyright of their respective websites Last updated: August, 2021 1/72 Outline 1. What is computerized automation? 2. Evaluating technologies 3. Sample deployment 4. Device programming basics 5. What is success? 6. Home automation applications 2/72 1. What Is Computerized Automation? Non-Programmatic Automation • Timers • Clapper • Dawn/Dusk Sensors • Motion Sensors 3/72 Programmatic Automation • Device behavior can be combined • No distance limitations • Activity detection • Fully programmable / scriptable • Access to external data 4/72 2. Evaluating Technologies: Home Networks • Wired telephone • Cordless telephone (900MHz, 2.4GHz, 5.8 GHz, 1.9GHz) • Wired local area network (Ethernet) • Wireless local area network (802.11) • Electrical • New wireless networks 5/72 Home Network Choices • Power Line Control (PLC) • X10: signal transmitted at 60 Hz zero-crossings (120 kHz) • Universal Power Bus (UPB): out-of-band signal (4–40 kHz) • Radio frequency (wireless) • Z-Wave: 900 MHz • Zigbee: 900 MHz and 2.4GHz (IEEE standard 802.15.4) • Hybrid • Insteon: out-of-band PLC (131 kHz) and radio frequency (900MHz), plus X10 support http://www.smarthome.com/INSTEON_comparison.html http://www.sgiclearinghouse.org/Technologies?q=node/2126 6/72 Choosing a Home Network Technology • Open source computer control • heyu supports X10 • MisterHouse (Perl-based) supports all listed technologies • Availability of devices • electrical plug control • wireless remotes • chimes • sensors • doors, locks • thermostats/HVAC • 220-volt control • Signal reliability (X10 is the worst) • Technology longevity (X10’s future is uncertain) • Simplicity of device replacement • Cost • Subset of Internet of Things 7/72 3.