1. Introduction to Computers 1.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Video Compression Tools Video Compression Tools
Video Compression Tools Video Compression Tools Douglas Dixon Manifest Technology® LLC May 2005 www.manifest-tech.com 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 1 Video Compression Tools Automated Video Processing Tools Video Compression and Conversion • Video Processing Canopus – Video compression and conversion ProCoder – Automated batch processing • Processing Steps Discreet cleaner – Select source files – Define video and audio pre-processing – Define target formats and compression – Select target locations and filters Sorenson – Convert, compress, output Squeeze 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 2 1 Video Compression Tools Video Compression Tools Video Editing to Compression Tools • Consumer Video Editors – Automated, w/ DVD – $50 - $150 • Format-Specific – Clips: Capture, organize, export – Downloads – Apple iMovie, Windows Movie Maker – QuickTime Player Pro, $29 – Adobe Premiere Elements – Win Media Encoder – Sony Vegas Movie Studio – RealProducer, Plus $199 – Pinnacle Studio – Roxio VideoWave, Ulead VideoStudio • Video Processing – Batch compression • Professional Video Editors – $500 - $600 – Compositing, motion, effects – Sorenson Squeeze – Projects – $300 - $1700 – Canopus ProCoder – Apple Final Cut Pro – Discreet cleaner – Adobe Premiere Pro, Sony Vegas – Avid Xpress, Pinnacle Edition – Ulead MediaStudio Pro 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 3 Video Compression Tools QuickTime Player Pro 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 4 2 Video Compression Tools Windows Media Encoder 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 5 Video Compression Tools Automated Video Processing Individuals and Workgroups • Sorenson Squeeze – Squeeze 4 (4.1) - Aug. -

Ulead Mediastudio Pro 8.0 Free Download
Ulead mediastudio pro 8.0 free download click here to download Ulead MediaStudio Pro, free and safe download. Ulead MediaStudio Pro 8 developed by Ulead is making a good case for itself, however. Can it rise up to the. Nov 15, Ulead MediaStudio Pro free download. Get the latest version now. Ulead MediaStudio Pro 8 is powerful, versatile and intuitive video editing. Ulead MediaStudio Pro is a prevailing, flexible and intuitive video editing suite designed for enthusiasts and professionals. It is recommended for independent. Ulead MediaStudio Pro 8 is powerful versatile and intuitive video editing software for professionals and enthusiasts in independent production event. Ulead MediaStudio Pro Free Download ~ Download free Software. Ulead MediaStudio Pro 8 Free Download With Crack Full Version. Mar 2, Ulead MediaStudio Pro 8 Free Download setup in direct link. Professional video editing and hundreds of amazing effects with ulead. Sep 22, MediaStudio Pro is powerful, versatile and intuitive video editing software, Free to try Corel Windows /XP Version Full Specs. Download the newest VideoStudio for free today and see what all the hype is Ulead MediaStudio Pro was an advanced video editing software suitable for Paint were excluded from MediaStudio Pro when the version released in Download Ulead MediaStudio Pro 8. Suite of nonlinear, digital Editors. Version : 8. Program available in:In English; Program license:Trial version; Program by. Jul 8, Free Download Ulead MediaStudio Pro - A feature-packed software utility that provides users with advanced technology and creative tools for. how can i use ulead media studio pro 8 in window 7 32 bit?. -

0789737973 Sample.Pdf
YouTube® for Business: Online Video Marketing for Any Business Associate Publisher Greg Wiegand Copyright © 2009 by Pearson Education, Inc. All rights reserved. No part of this book shall be reproduced, stored in a Acquisitions Editor retrieval system, or transmitted by any means, electronic, mechanical, photo- Michelle Newcomb copying, recording, or otherwise, without written permission from the pub- lisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in Development Editor the preparation of this book, the publisher and author assume no responsibil- Kevin Howard ity for errors or omissions. Nor is any liability assumed for damages resulting from the use of the information contained herein. Managing Editor ISBN-13: 978-0-7897-3797-7 Patrick Kanouse ISBN-10: 0-7897-3797-3 Library of Congress Cataloging-in-Publication Data Project Editor Mandie Frank Miller, Michael, 1958- Copy Editor YouTube for business : online video marketing for any business / Mike Henry Michael Miller. p. cm. Indexer Includes index. Brad Herriman ISBN 978-0-7897-3797-7 1. Internet marketing. 2. Webcasting. 3. YouTube (Firm) I. Title. Technical Editor HF5415.1265.M556 2009 John Rice 658.8'72--dc22 Publishing Coordinator 2008028344 Cindy Teeters Printed in the United States of America First Printing: August 2008 Designer Trademarks Anne Jones All terms mentioned in this book that are known to be trademarks or service Composition marks have been appropriately capitalized. Que Publishing cannot attest to the accuracy of this information. Use of a term in this book should not be Bronkella Publishing regarded as affecting the validity of any trademark or service mark. -
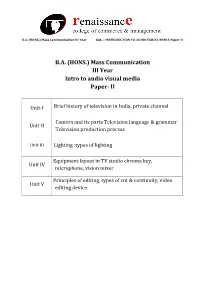
Mass Communication III Year Intro to Audio Visual Media Paper- II
B.A. (HONS.) Mass Communication III Year Sub. – INTRODUCTION TO AUDIO VISUAL MEDIA Paper II B.A. (HONS.) Mass Communication III Year Intro to audio visual media Paper- II Unit-I Brief history of television in India, private channel Camera and its parts Television language & grammar Unit-II Television production process Unit III Lighting :types of lighting Equipment layout in TV studio chroma key, Unit IV microphone, vision mixer Principles of editing, types of cut & continuity, video Unit V editing device B.A. (HONS.) Mass Communication III Year Sub. – INTRODUCTION TO AUDIO VISUAL MEDIA Paper II Unit-I Brief history of television in India, private channel Television came to India on September 15, 1959 with experimental transmission from Delhi. It was a modest beginning with a make shift studio, a low power transmitter and only 21 community television sets.All India Radio provided the engineering and programme professionals. A daily one-hour service with a news bulletin was started in 1965. In1972 television services were extended to a second city—Mumbai. By1975 television stations came up in Calcutta, Chennai, Srinagar, Amritsar and Lucknow. In 1975-76 the Satellite Instructional Television Experiment brought television programmes for people in 2400 villages inthe most inaccessible of the least developed areas tlirough a satellite lentto India for one year.Doordarshan is a Public broadcast terrestrial ltelevision channel run by Prasar Bharati, a board formedby the Government of India. It is one of the largest broadcasting organizations in the world in terms of the of studios and transmitters. Doordarshanhad its beginning with the experimental telecast started in Delhi in September, 1959 with a small transmitter and a makeshift studio. -

DVD Authoring Tools
DVD Authoring Tools DVD Authoring Tools Douglas Dixon Manifest Technology® LLC May 2005 www.manifest-tech.com 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 1 DVD Authoring Tools DVD Authoring Tools Consumer to Professional • Disc Suites, Video Editing Tools • Personal / Automated DVD Authoring – Capture - Layout – Burn, Direct to DVD, $30 - $100 – Apple iDVD, Sonic MyDVD, Ulead DVD MovieFactory • Corporate / Professional DVD Authoring – Customized menus & navigation – Multiple tracks, $300, $500 - $700 – Apple DVD Studio Pro, Adobe Encore DVD – Sonic DVDit / ReelDVD, Ulead DVD Workshop • “Hollywood” / Feature – Commercial titles, hardware encoders, $10K's – Sonic DVD Producer, Sonic Scenarist • Enhanced: eDVD / WMV HD 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 2 1 DVD Authoring Tools Disc Suites, Video Editors Disc Burning Suites and Video Editing • CD / DVD Data Suites (~ $75 - $100) – Burn data files, audio, photos, videos • Roxio Easy Media Creator, Nero – Copy, extract and reduce to fit, DVD to CD • Video Editors, export to DVD – Consumer (~ $75 - $150) • Adobe Premiere Elements • CyberLink PowerDirector, InterVideo WinProducer • Pinnacle Studio, Roxio VideoWave • Sony Vegas Movie Studio+DVD, Ulead VideoStudio – Professional (~ $500 - $700) • Adobe Premiere Pro, Pinnacle Edition • Sony Vegas Video, Ulead MediaStudio Pro 5/2005 Copyright 2001-2005 Douglas Dixon, All Rights Reserved - www.manifest-tech.com Page 3 DVD Authoring Tools Personal -

ADVC Professional Family Analog/Digital Video Conversion
DATA SHEET ADVC PROFESSIONAL FAMILY High-Quality Analog/Digital Video Conversion Our ADVC® professional family supports virtually any professional video Key Features conversion need. Each contains our innovative Canopus® DV codec technology, which provides the industry’s best picture-quality preservation during analog/ • Connects analog video equipment to FireWire- DV conversion. equipped computers for video editing As standalone units or connected to a computer, all ADVC professional family • Compatible with Windows and Macintosh products feature broad compatibility with video equipment and software and operating system-based DV editing systems intelligent input/output selection with automatic signal detection. • Compatible with leading editing and DVD authoring applications including Grass Valley™ ADVC55 – Compact A/D Conversion EDIUS®, Sony Vegas, Apple Final Cut Pro and Our ADVC55 unit connects VHS, Hi8, and other analog video equipment to a DV iMovie, Avid Xpress DV and Liquid, Adobe camera, deck, or editing system. It’s ideal for capturing analog video into FireWire- Premiere Pro, Ulead MediaStudio Pro, and equipped notebook and desktop editing computers. There are no drivers to install Windows Movie Maker and the unit does not require a power supply when used with a 6-pin DV cable. • No drivers or software applications to install ADVC110 – High-Quality, Bi-Directional A/D Conversion • Powered by IEEE 1394 (FireWire) connector Our ADVC110 unit connects to all analog and digital video cameras, decks, and (ADVC55 and ADVC110 only) editing systems. This portable and easy-to-use digital video converter is ideal for • NTSC and PAL compatible capturing and outputting analog video from any FireWire-equipped notebook or desktop computer. -

Microsoft Windows 95/98/ME/2000/XP/2003/Vista/7 32-B
SoftKey Revealer retrieves Serials and Keys for over 700 software products: Microsoft Windows 95/98/ME/2000/XP/2003/Vista/7 32-bit Microsoft Office XP/2003/2007 Microsoft Internet Explorer 010 Editor 3 3D Screensavers (many) 3Planesoft Screensavers AAA LOGO ABBY FineReader 7, 8 Absolute Time Corrector Acala Products Access Password Recovery Genie ACDSee Products AceMoney Active Desktop Calendar 6,7 Actual Window Manager 4,5,6 Addweb Website Promoter 6,7,8 Adobe Acrobat 5, 6, 7, 8 Adobe Acrobat Distiller 6 Adobe After Effects 6, 6.5, 7 Adobe Illustrator 10,CS,CS2 Adobe Lightroom 1.0 Adobe Photoshop 5, 5.5, 6, 7, CS, CS2 Adobe Photoshop Elements 3, 4 Adobe Premiere 5, 5.5, CS3 Advanced SystemCare Pro 3 AirplanePDQ Alice-soft Products Alien Skin Eye Candy 4, 5 Alcohol 120% All Image All Media Fixer Amabilis 3D Canvas 6 Ashampoo Products Ashampoo Burning Studio ASPack Atlantis Word Processor 1.x Atomic ZIP Password Recovery Audio Recorder Deluxe Autodesk Products -AutoCAD -AutoCAD Electrical -AutoCAD LT -AutoCAD Mechanical -Autodesk Architectural Desktop -Autodesk Building Systems -Autodesk Civil 3D -Autodesk Land Desktop -Autodesk Map 3D -Autodesk Survey -Autodesk Utility Design -Autodesk VIZ Autoplay Menu Builder AutoWorld 3D Garage AVI Toolbox Avira AntiVir PersonalEdition Classic Axailis IconWorkshop Axialis Professional Screen Saver Producer BadCopy BeFaster Belarc Advisor BitComet Acceleration Patch BootXP 2 Borland C++ Builder 6, 7 Borland Delphi 5, 6, 7, 8 CachemanXP Cakewalk SONAR Producer Edition 4,5,6,7,8 CD2HTML CDMenu CDMenuPro -

Symbols Applications File Format Layer, 429 APS (Analog Protection 2-3/3-2 Pulldown, 439 System), 454 Aqua Interface (Mac OS X), 90 a Arcsoft Showbiz
25 dvdindex 9/17/02 4:24 PM Page 499 Index Symbols Applications File Format layer, 429 APS (Analog Protection 2-3/3-2 pulldown, 439 System), 454 Aqua interface (Mac OS X), 90 A ArcSoft ShowBiz. See ShowBiz Adobe Premiere 6.5, 496 aspect ratios, 6, 439-440 selecting in DVDit!, 288-289 affordability of DVD media, 21 assets, 440 AIFF (Audio Interchange File importing in DVD Studio Pro, 365 Format), 439 ReelDVD, 394 alpha channels, 439 format settings, 395 alternate tracks, 9, 61 Assets View window (DVD Studio playback controls, 64 Pro), 339-341 analog, 440 audio audio formats, 53-54 adding in MyDVD, 242-243 copy protection, 42 amplifying, 440 Analog Protection System (APS), 454 audio signals, 52-53 anamorphic, 440 audio streams, 440 background audio, adding to menus with Angle function, 65 DVDit!, 309-310 animating, 440 capturing antialiasing, 440 PowerDirector, 198-200 applications, 23 WinProducer, 216 authoring software, 24 compression DVD MovieFactory, 26 Media Player, 168 iDVD, 25 MP3, 144-145 MyDVD, 25 music files, 169 Pinnacle Studio 7 video editor, 26 connecting audio signals, 52-53 data-burning software, 24 types, 52 DVD player software, 23-24 25 dvdindex 9/17/02 4:24 PM Page 500 500 Index Dolby Digital, 54 DVDit! 2.5, 487 DTS (Digital Theater Systems), 54 Express DV, 483 DVD Studio Pro, 356-357 iDVD 2, 25, 486 editing (PowerDirector), 207-208 Impression DVD-Pro 2.2, 490 filters (WinProducer), 219-220 MyDVD 4, 25, 484 formats, 41 NeoDVDstandard/Plus 4, 482 analog, 53-54 Pinnacle Studio 7 video editor, 26 digital, 55 PowerDirector -
Video & Audio Editing #3 (200-286)
Section3 PHOTO - VIDEO - PRO AUDIO Video & Audio Editing Analog Editing Equipment ............202-205 Live DV Capture .............................206-207 ADS Technology..............................208-209 Adobe ...............................................210-211 Avid...................................................212-213 Apple Computer..............................214-221 LaCie Hard/Optical Drives ............222-224 Canopus ...........................................225-233 Matrox..............................................234-235 Pinnacle Systems.............................236-241 Sony..................................................242-244 CineForm ................................................243 Red Giant.................................................245 Section 3a Audio for Video Editing .................246-286 VIDEONICS MXPRO/MXPRODV 10-Bit Digital Video Mixers The MXPro is a professional four-input video mixer with powerful features and performance. It offers unmatched 10-bit digital 4:2:2 video quality as well as a S/N ratio over 60 dB and a video band- width of 5.5 MHz. It has over 500 digital video effects and transitions including dissolves, trailing effects and multiple picture-in-picture. There are shape wipes, soft wipe edges and easy to use ‘banks’ of effects with user-defined favorites. All shape effects can be enhanced with soft edges, colored borders and drop shadows for 3-D like impact. Frame synchronizer and dual-field infinite-window time base corrector (TBC) allow clean transitions, including the ability to hold an image frozen through a transition. Unique preview screen shows miniature copies of all four inputs in your choice of formats and sizes, so you can work with just one or two monitors. Digital effects include freeze, black and white, negative, mosaic, paint and flip. Has a chroma keyer and a color corrector that remembers settings for each channel. Built-in audio mixer includes a special background music VIDEO & AUDIO EDITING feature that lets you manipulate audio tracks independent of video. -
MSP8 Manual.Book
User Guide Ulead Systems, Inc. September 2005 P/N: C22-180-110-0A0001 First edition for Ulead® MediaStudio Pro® 8, September 2005. © 1992-2005 Ulead Systems, Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or storing in a retrieval system, or translated into any language in any form without the express written permission of Ulead Systems, Inc. Software license The software described in this document is furnished under a License Agreement which is included with the product. This Agreement specifies the permitted and prohibited uses of the product. Licenses and trademarks All rights reserved. Ulead, the Ulead Systems logo, and MediaStudio are registered trademarks of Ulead Systems, Inc. Intel, Pentium and MMX are registered trademarks and/or trademarks of Intel Corporation. Microsoft, Windows, DirectX and/or other Microsoft products referenced herein are either trademarks or registered trademarks of Microsoft Corporation. Adobe, the Adobe logo, and Acrobat are trademarks of Adobe Systems Incorporated. QuickTime and the QuickTime logo are trademarks used under license. QuickTime is registered in the U.S. and other countries. All other product names and any registered and unregistered trademarks mentioned in this manual are used for identification purposes only and remain the exclusive property of their respective owners. Sample files Files provided as samples on the program CD can be used for personal demonstrations, productions and presentations. No rights are granted for commercial reproduction or redistribution of any sample files. North & South America International Ulead Systems Inc. Ulead Systems, Inc. -
Download Ulead Video Studio 11 Full Version Ulead Video Studio 11
download ulead video studio 11 full version Ulead Video Studio 11. With the introduction of many video editing software in the market now you don’t need to be Steven Spielberg to make a movie. You can do it easily now with the aid of tools like Ulead Video Studio. Ulead Video Studio is a powerful and strong video editing and DVD authoring tool. Features of Ulead Video Studio 11. Easy to use. Simple Interface. Videos can be exported to DVD, HD-DVD and AVCHD. Both storyboard and timeline editing. Text can be added. Brightness and hue can be adjusted. Videos can be cropped and trimmed. Video can be split into small portions. Audio stream can be separated. ,Program download Ulead Video Studio 11, Download Ulead Video Studio 11, Download Ulead Video Studio 11, Program Ulead Video Studio 11, Ulead Video Studio 11 Full activated, crack program Ulead Video Studio 11, program explanation Ulead Video Studio 11. Looking for Ulead VideoStudio? Ulead VideoStudio is now called VideoStudio and it is better than ever! User Forum. Connect with other users to get advice, swap tips and techniques and discuss VideoStudio. User Guide. A complete PDF guide to all the information you need to get started in VideoStudio. Knowledgebase. Find frequently asked questions and answers about VideoStudio in the Corel Knowledgebase. Studio Backlot * From our friends at Studio Backlot, access their library of tutorials and creative content. * Content is available only in English. Subtitles are available on select training videos. Studio Backlot offers training in English and French. Get all of the old features you loved about Ulead VideoStudio and a whole lot more when you upgrade to the latest version of VideoStudio. -

High-Quality Analog/Digital Video Conversion
PRODUCT DATA SHEET ADVC PROFESSIONAL FAMILY High-Quality Analog/Digital Video Conversion The ADVC® professional family ADVC110 – High-Quality, TwinPact100 – Transform PC supports virtually any professional Bi-Directional A/D Conversion Graphics into High-Quality Video video conversion need. Each contains Our ADVC110 unit connects to all analog The multifunctional TwinPact100 offers our innovative Canopus® DV codec and digital video cameras, decks, and the highest quality bi-directional analog/ technology, which provides the industry’s editing systems. This portable and easy- digital video conversion, track and best picture-quality preservation during to-use digital video converter is ideal for zoom scan conversion of computer analog/DV conversion. capturing and outputting analog video graphics to analog and digital video, and As standalone units or connected to a from any FireWire (IEEE 1394a)-equipped capture-to-DV of on-screen graphics. The computer, all ADVC professional family notebook or desktop computer. There are TwinPact100 can be used with virtually products feature broad compatibility no drivers to install and the unit does not any Windows- or Mac OS-based video with video equipment and software and require a power supply when used with a editing system, or as a standalone intelligent input/output selection with 6-pin FireWire (IEEE 1394a) cable. device. automatic signal detection. ADVC300 – Bi-Directional A/D ADVC55 – Compact A/D Conversion With Analog Filtering Conversion Featuring high-quality image- Our ADVC55 unit connects VHS, Hi8, and enhancement technology—including other analog video equipment to a DV digital noise reduction and image camera, deck, or editing system. It’s ideal stabilization using line time base for capturing analog video into FireWire correction (LTBC)—our ADVC300 unit (IEEE 1394a)-equipped notebook and instantly cleans, stabilizes, and preserves desktop editing computers.