Growth of the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

QUILT CIRCLE2020 a Letter from the President
THE QUILT CIRCLE2020 A Letter From the President This 2020 Quilt Circle edition commemorates the 20th Anniversary of The Quilt. The fabric of our research and education (R&E) networking community has never been stronger. While our Quilt community has evolved in new and exciting ways in the past two decades, we have also been faced with a number of challenges which we take head-on and always with the spirit of collaboration. As we address the unprecedented challenges presented by the current global public health crisis due to the COVID-19 pandemic, the work of our members is more important than ever to the missions of their member communities. U.S. higher education institutions rely on R&E networks to give them a competitive edge in the most impactful scientific research initiatives which is essential in this crisis. We connect the educational institutions that support university medical centers and their associated hospitals. R&E networks also connect tens of thousands of other community anchor institutions, including K-12 schools, public libraries, local/state government, research sites, cultural institutions, public safety, and tribal lands. Being responsive and providing vital networking infrastructure and resources right now to address immediate needs is who we are and what we do. R&E networks are part of our nation’s critical infrastructure. This year’s edition of The Quilt Circle showcases several examples of the key role of R&E network members in both providing and facilitating the use-network infrastructure to further scientific discovery and collaborations at higher education institutions of all sizes. -

Integration of Mobile Technology Into Museum Education: a Discussion of the State of the Art Mark P
Seton Hall University eRepository @ Seton Hall Theses Spring 5-2011 Integration of Mobile Technology into Museum Education: A Discussion of the State of the Art Mark P. Diemer Seton Hall University Follow this and additional works at: https://scholarship.shu.edu/theses Recommended Citation Diemer, Mark P., "Integration of Mobile Technology into Museum Education: A Discussion of the State of the Art" (2011). Theses. 26. https://scholarship.shu.edu/theses/26 INTEGRATION OF MOBILE TECHNOLOGY Il INTO MUSEUM EDUCATION: A DISCUSSION 1 OF THE STATE OF THE ART i 1 I by I Mark P. Diemer I A thesis submitted in partial fulfillment of the requirements for the degree of I Master of Arts in Museum Professions j I I Seton Hall University May 2011 I I ! 1 i I I I Copy © Mark P. Diemer, 2011. All Rights Reserved. I No part of this document may be reproduced in any form without written permission of the author. Copyrights to images are owned by other copyright holders and should not be reproduced under any circumstances. TIlls document as shown is not for publication and was produced in satisfaction of thesis I requirements. I I I I ,! } ! l I; Seton Hall University Abstract Integration of Mobile Technology into Museum Education: A Discussion of the State of the Art by Mark P. Diemer 'lnesi" Advisor: Dr. Petra Chu Museum Professions Program Approval: This thesis is an attempt to examine the current state of mobile technology use in museum education programs. Mobile technology is fast becoming the communications and learning medium of choice. -

On Multi-Point, In-Network Filtering of Distributed Denial-Of-Service Traffic
On Multi-Point, In-Network Filtering of Distributed Denial-of-Service Traffic Mingwei Zhang∗, Lumin Shi∗, Devkishen Sisodia∗, Jun Li∗, Peter Reihery ∗ University of Oregon fmingwei, luminshi, dsisodia, [email protected] y University of California, Los Angeles [email protected] Abstract—Research has shown that distributed denial-of- in a common language. Further, it is also unknown how these service (DDoS) attacks on the Internet could often be better solutions perform under insufficient knowledge of the attacks handled by enlisting the in-network defense of multiple au- or against intelligent adversaries who can dynamically revise tonomous systems (ASes), rather than relying entirely on the victim’s Internet Service Provider at the edge. Less noticed their attack strategies to escape defense. Without a quantitative but important is the fact that an in-network defense can also comparison, it is hard for a DDoS victim to select the most remove DDoS traffic from the Internet early en route to the suitable solution to achieve its defense goal and meet the victim, thus decreasing the overall load on the Internet and resource requirements. reducing chances of link congestion. However, it is not well In this paper, we introduce a modeling and simulation understood to what degree different in-network defense strategies can achieve such benefits. In this paper, we model the existing framework to systematically evaluate in-network DDoS de- two main categories of in-network DDoS defense algorithms fense algorithms. The framework contains a general model (PushBack, SourceEnd) and propose a new type of algorithm that can describe the attack and defense for various defense (StrategicPoints). -

Engineering of Computer Networking Protocols : an Historical Perspective Gregor V
Engineering of computer networking protocols : an historical perspective Gregor v. Bochmann University of Ottawa with thanks to Colin West and Dave Rayner http://www.site.uottawa.ca/~bochmann/talks/history.ppt McNaughton Lecture 24th Canadian Conference on Electrical and Computer Engineering Niagara Falls, May 2011 Gregor v. Bochmann, University of Ottawa 1 Approximate time line 1960: first high-level programming languages 1965: time sharing operating systems and interactive terminals 1970: first experimental computer networks 1975: X.25 networking standard, proprietary networking architectures, e.g. IBM’s SNA 1980: experimental Internet, OSI standardization started, Teletex (a kind of Web service, Telidon in Canada) 1985: Formal Description Techniques (FDTs) developed, experimental tools 1990: commercial SDL tools, beginning of public use of the Internet and Web 1995: Java released, wide use of the Internet, digital wireless telephony spreads – UML (universal modeling language) 2000: XML and Web Services 2005: beginning integration of wireless services with the Internet 2011: there we are . Gregor v. Bochmann, University of Ottawa 2 Computer communications in the 1970ies Remote access to servers User terminals Batch entry terminals Line multiplexing line speed: 300 bps Link protocols (with sequence numbering) Alternating bit protocol (1969) Bisync, SDLC (IBM) Gregor v. Bochmann, University of Ottawa 3 Computer communications in the 1970ies Computer networks ARPANET (USA): first long distance computer network – first trial in 1969 NPL network (UK): first LAN Cyclade (France): introduced IP service at the network layer – around 1972 Donald Davies, NPL Leonard Kleinrock, UCLA Louis Pouzin with ARPAnet node INRIA (France) Gregor v. Bochmann, University of Ottawa 4 Computer communications in the 1970ies Protocol standards First network protocol standard: X.25 Vendor networking architectures IBM (SNA), DEC, Honeywell, etc. -

ABSTRACT Title of Document: ROBOTICS and the FUTURE OF
ABSTRACT Title of Document: ROBOTICS AND THE FUTURE OF INTERNATIONAL ASYMMETRIC WARFARE Nicholas Grossman, Doctor of Philosophy, 2013 Directed By: Professor George Quester, Department of Government and Politics In the post-Cold War world, the world's most powerful states have cooperated or avoided conflict with each other, easily defeated smaller state governments, engaged in protracted conflicts against insurgencies and resistance networks, and lost civilians to terrorist attacks. This dissertation explores various explanations for this pattern, proposing that some non-state networks adapt to major international transitions more quickly than bureaucratic states. Networks have taken advantage of the information technology revolution to enhance their capabilities, but states have begun to adjust, producing robotic systems with the potential to grant them an advantage in asymmetric warfare. ROBOTICS AND THE FUTURE OF ASYMMETRIC WARFARE By Nicholas Grossman Dissertation submitted to the Faculty of the Graduate School of the University of Maryland, College Park, in partial fulfillment of the requirements for the degree of Doctor of Philosophy 2013 Advisory Committee: Professor George Quester, Chair Professor Paul Huth Professor Shibley Telhami Professor Piotr Swistak Professor William Nolte Professor Keith Olson © Copyright by Nicholas Grossman 2013 Dedication To Marc and Tracy Grossman, who made this all possible, and to Alyssa Prorok, who made it all worth it. ii Acknowledgements Thank you to my dissertation committee for all the advice and support, Anne Marie Clark and Cissy Roberts for making everything run smoothly, Jacob Aronson and Rabih Helou for the comments and encouragement, Alyssa Prorok for invaluable help, and especially to George Quester for years of mentorship. -

Multimedia, Internet, On-Line
Section IV: Multimedia, the Internet, and On-Line Services High-End Digital Video Applications Larry Amiot Electronic and Computing Technologies Division Argonne National Laboratory The emphasis of this paper is on the high-end applications Internet and Intranet that are driving digital video. The research with which I am involved at Argonne National Laboratory is not done on dig- The packet video networks which currently support many ital video per se, but rather on how the research applications applications such as file transfer, Mbone video (talking at the laboratory drive its requirements for digital video. The heads), and World Wide Web browsing are limiting for high- paper will define what digital video is, what some of its com- quality video because of the low throughput one can achieve ponents are, and then discuss a few applications that are dri- via the Internet or intranets. Examples of national packet ving the development of these components. The focus will be switched networks developed in the last several years include on what digital video means to individuals in the research the National Science Foundation Network (NSFNet). The and education community. Department of Energy had its own network called ESNET, and the National Aeronautics and Space Administration The Digital Video Environment (NASA) had a network as well. Recently, the NSFNet was de- commissioned, and commercial interests are now starting to In 1996, a group of people from several universities in the fill that void. Research and education communities are find- Midwest and from Argonne formed a Video Working Group. ing, however, that this new commercial Internet is too re- This body tried to define the areas of digital video of impor- stricting and does not meet their throughput requirements; it tance to their institutions. -

The Great Telecom Meltdown for a Listing of Recent Titles in the Artech House Telecommunications Library, Turn to the Back of This Book
The Great Telecom Meltdown For a listing of recent titles in the Artech House Telecommunications Library, turn to the back of this book. The Great Telecom Meltdown Fred R. Goldstein a r techhouse. com Library of Congress Cataloging-in-Publication Data A catalog record for this book is available from the U.S. Library of Congress. British Library Cataloguing in Publication Data Goldstein, Fred R. The great telecom meltdown.—(Artech House telecommunications Library) 1. Telecommunication—History 2. Telecommunciation—Technological innovations— History 3. Telecommunication—Finance—History I. Title 384’.09 ISBN 1-58053-939-4 Cover design by Leslie Genser © 2005 ARTECH HOUSE, INC. 685 Canton Street Norwood, MA 02062 All rights reserved. Printed and bound in the United States of America. No part of this book may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without permission in writing from the publisher. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Artech House cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. International Standard Book Number: 1-58053-939-4 10987654321 Contents ix Hybrid Fiber-Coax (HFC) Gave Cable Providers an Advantage on “Triple Play” 122 RBOCs Took the Threat Seriously 123 Hybrid Fiber-Coax Is Developed 123 Cable Modems -

Designated Agents for Local Exchange Carriers
Designated Agents for Local Exchange Carriers Document Processor Document Processor 321 Communications, Inc. Access Point, Inc. InCorp Services, Inc. Illinois Corporation Service Company 2501 Chatham Rd., Ste. 110 801 Adlai Stevenson Dr. Springfield IL 62704-7100 Springfield IL 62703-4261 Lisa Brown John Petrakis 321 Communications, Inc. Access2Go, Inc. Regulatory and Tax Consultants 4700 N. Prospect Rd. 3483 Satellite Blvd., Ste. 202 Peoria Heights IL 61616 Duluth GA 30096-5800 Document Processor Document Processor ACN Communication Services, Inc. 360networks (USA) inc. C T Corporation System C T Corporation System 208 S. LaSalle St. 208 S. LaSalle St. Chicago IL 60604 Chicago IL 60604 Doug Forster Document Processor ACN Communication Services, Inc. AboveNet Communications, Inc. Technologies Management, Inc. d/b/a AboveNet Media Networks PO Drawer 200 Illinois Corporation Service Company Winter Park FL 32790-0200 801 Adlai Stevenson Dr. Springfield IL 62703-4261 James W. Broemmer Jr Adams Telephone Co-Operative Robert Sokota PO Box 217 AboveNet Communications, Inc. Golden IL 62339 d/b/a AboveNet Media Networks 360 Hamilton Blvd. James W. Broemmer Jr White Plains NY 10601 Adams TelSystems, Inc. PO Box 217 Robert Neumann Golden IL 62339 Access Media 3, Inc. 900 Commerce Dr., Ste. 200 Gary Pieper Oak Brook IL 60523 Advanced Integrated Technologies Inc. PO Box 51 Brian McDermott Columbia IL 62236 Access Media 3, Inc. Synergies Law Group, PLLC Mark Lammert 1002 Parker St. Advanced Integrated Technologies Inc. Falls Church VA 22046 Compliance Solutions Inc. 740 Florida Central Pkwy., Ste. 2028 Document Processor Longwood FL 32750 Access One, Inc. Corporation Service Company Ronald Dougherty 422 N. -

History of the Internet-English
Sirin Palasri Steven Huter ZitaWenzel, Ph.D. THE HISTOR Y OF THE INTERNET IN THAILAND Sirin Palasri Steven G. Huter Zita Wenzel (Ph.D.) The Network Startup Resource Center (NSRC) University of Oregon The History of the Internet in Thailand by Sirin Palasri, Steven Huter, and Zita Wenzel Cover Design: Boonsak Tangkamcharoen Published by University of Oregon Libraries, 2013 1299 University of Oregon Eugene, OR 97403-1299 United States of America Telephone: (541) 346-3053 / Fax: (541) 346-3485 Second printing, 2013. ISBN: 978-0-9858204-2-8 (pbk) ISBN: 978-0-9858204-6-6 (English PDF), doi:10.7264/N3B56GNC ISBN: 978-0-9858204-7-3 (Thai PDF), doi:10.7264/N36D5QXN Originally published in 1999. Copyright © 1999 State of Oregon, by and for the State Board of Higher Education, on behalf of the Network Startup Resource Center at the University of Oregon. This work is licensed under a Creative Commons Attribution- NonCommercial 3.0 Unported License http://creativecommons.org/licenses/by-nc/3.0/deed.en_US Requests for permission, beyond the Creative Commons authorized uses, should be addressed to: The Network Startup Resource Center (NSRC) 1299 University of Oregon Eugene, Oregon 97403-1299 USA Telephone: +1 541 346-3547 Email: [email protected] Fax: +1 541-346-4397 http://www.nsrc.org/ This material is based upon work supported by the National Science Foundation under Grant No. NCR-961657. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation. -

Bbvaopenmind.Com 19 Key Essays on How Internet Is Changing Our Lives
bbvaopenmind.com 19 Key Essays on How Internet Is Changing Our Lives CH@NGE Zaryn Dentzel How the Internet Has Changed Everyday Life bbvaopenmind.com How the Internet Has Changed Everyday Life ––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––– Zaryn Dentzel CEO, Tuenti bbvaopenmind.com How the Internet Has Changed Everyday Life Society, Community, Individuals Zaryn Dentzel 5 Zaryn Dentzel es.wikipedia.org/wiki/Zaryn_Dentzel Illustration Catell Ronca bbvaopenmind.com 7 Zaryn Dentzel Zaryn Dentzel is the founder and CEO of Tuenti, a Spanish tech company centered on mobile communications whose multi-platform integrates the best of instant messaging and the most private and secure social network. Also a member of the cabinet of advisors to Crown Prince Felipe for the Principe de Girona Foundation, Dentzel is involved in promoting education and entrepreneurship among young people in Spain. He studied at UC Santa Barbara and Occidental College, graduating with a degree in Spanish Literature, and Diplomacy and World Affairs. How the Internet Has Changed Everyday Life Sites and services that have changed my life tuenti.com techcrunch.com spotify.com Kinect Training bbvaopenmind.com Society, Community, Individuals bbvaopenmind.com 9 How the Internet Has Changed Everyday Life What Happened? The Internet has turned our existence upside down. It has revolutionized communications, to the extent that it is now our preferred medium of ev- Zaryn Dentzel eryday communication. In almost everything we do, we use the Internet. Ordering a pizza, buying a television, sharing a moment with a friend, send- ing a picture over instant messaging. Before the Internet, if you wanted to keep up with the news, you had to walk down to the newsstand when it opened in the morning and buy a local edition reporting what had happened the previous day. -
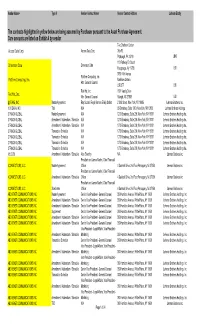
The Contracts Highlighted in Yellow Below Are Being Assumed by Purchaser Pursuant to the Asset Purchase Agreement. Cure Amounts Are Listed on Exhibit a by Vendor
Vendor Name+ Type II Vendor Contact Name Vendor Contact Address Lehman Entity The contracts highlighted in yellow below are being assumed by Purchaser pursuant to the Asset Purchase Agreement. Cure amounts are listed on Exhibit A by vendor. Two Chatham Center Access Data Corp. Access Data Corp. 24th FL Pittsburgh, PA 15219 LBHI 110 Parkway Dr. South Dimension Data Dimension Data Hauppauge, Ny 11788 LBI 3760 14th Avenue Platform Computing, Inc. Platform Computing, Inc. Markham Ontario Attn: General Counsel L3R 3T7 LBI Red Hat, Inc. 1801 Varsity Drive Red Hat, Inc. Attn: General Counsel Raleigh, NC 27606 LBI @STAKE, INC Master Agreement Ray Scutari, Royal Hansen, Emily Sebert 2 Wall Street, New York, NY 10005 Lehman Brothers, Inc. 1010 DATA, INC Trial N/A 65 Broadway, Suite 1010, New York, NY 10006 Lehman Brothers Holdings 2 TRACK GLOBAL Master Agreement N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Amendment / Addendum / Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Amendment / Addendum / Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Transaction Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Transaction Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Transaction Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. 2 TRACK GLOBAL Transaction Schedule N/A 1270 Broadway, Suite 208, New York, NY 10001 Lehman Brothers Holdings Inc. -

Design of a Lan-Based Voice Over Ip (Voip) Telephone System
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by KhartoumSpace DESIGN OF A LAN-BASED VOICE OVER IP (VOIP) TELEPHONE SYSTEM A thesis submitted to the University of Khartoum in partial fulfillment of the requirement for the degree of MSC in Communication & Information Systems BY HASSAN SULEIMAN ABDALLA OMER B.SC of Electrical Engineering (2000) University of Khartoum Supervisor Dr. MOHAMMED ALI HAMAD ABBAS Faculty of Engineering & Architecture Department of Electrical & Electronics Engineering SEPTEMBER 2009 ﺑﺴﻢ اﷲ اﻟﺮﺣﻤﻦ اﻟﺮﺣﻴﻢ ﺻﺪق اﷲ اﻟﻌﻈﻴﻢ iii ACKNOWLEDGEMENTS First I would like to thanks my supervisor Dr. Mohammed Ali Hamad Abbas, because this research project would not have been possible without his support and guidance; so I take this opportunity to offer him my gratitude for his patience ,support and guidance . Special thanks to the Department of Electrical and Electronics Engineering University Of Khartoum for their facilities, also I would like to convey my thanks to the staff member of MSc program for their help and to all my colleges in the MSc program. It is with great affection and appreciation that I acknowledge my indebtedness to my parents for their understanding & endless love. H.Suleiman iv Abstract The objective of this study was to design a program to transmit voice conversations over data network using the internet protocol –Voice Over IP (VOIP). JAVA programming language was used to design the client-server model, codec and socket interfaces. The design was fully explained as to its input, processing and output. The test of the designed voice over IP model was successful, although some delay in receiving the conversation was noticed.