Imperial War Museums Improves Visibility and Control Over Its Sensitive Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IWM Digital Resource for Volunteers
IWM Digital Resource for Volunteers An Interactive Qualifying Project Submitted to the Faculty of the WORCESTER POLYTECHNIC INSTITUTE In partial fulfillment of the requirements for the Degree of Bachelor of Science by: Linda Baker Shintaro Clanton Andrew Gregory Rachel Plante Project advisors: VJ Manzo Jianyu Liang June 23, 2016 This report represents the work of one or more WPI undergraduate students submitted to the faculty as evidence of completion of a degree requirement. WPI routinely publishes these reports on its web site without editorial or peer review. ABSTRACT The Interaction Volunteers at Imperial War Museums London engage with visitors in the exhibits and discuss about certain artifacts. The communication of information among the Interaction Volunteer team, however, has been inefficient as the system relied on paper resources. Our IQP team surveyed volunteers and conducted a focus group to gather input about layout and features for a potential digital resource which the Interaction Volunteers could use in management of artifactual content and digital forms. This information was then used to design a website utilizing a content management system in order to make the communication of information more simple and efficient for the Interaction Volunteer team. ii ACKNOWLEDGEMENTS Our team would like to thank our advisors, Professors V.J. Manzo and Jianyu Liang, for their continued support and guidance in completing this project. We would especially like to thank Mr. Grant Rogers, Informal Learning and Engagement Manager at Imperial War Museums London, for sponsoring and providing insight for our project and for sharing his enthusiasm for the museum. In addition, we would like to extend our gratitude to the Learning and Engagement Department and Digital Design Department at Imperial War Museums London, for providing us the resources we needed to complete our project, and to the Volunteer Program at Imperial War Museums London for their advice and participation in our project. -

Key Bus Routes in Central London
Route 8 Route 9 Key bus routes in central London 24 88 390 43 to Stoke Newington Route 11 to Hampstead Heath to Parliament to to 73 Route 14 Hill Fields Archway Friern Camden Lock 38 Route 15 139 to Golders Green ZSL Market Barnet London Zoo Route 23 23 to Clapton Westbourne Park Abbey Road Camden York Way Caledonian Pond Route 24 ZSL Camden Town Agar Grove Lord’s Cricket London Road Road & Route 25 Ground Zoo Barnsbury Essex Road Route 38 Ladbroke Grove Lisson Grove Albany Street Sainsbury’s for ZSL London Zoo Islington Angel Route 43 Sherlock Mornington London Crescent Route 59 Holmes Regent’s Park Canal to Bow 8 Museum Museum 274 Route 73 Ladbroke Grove Madame Tussauds Route 74 King’s St. John Old Street Street Telecom Euston Cross Sadler’s Wells Route 88 205 Marylebone Tower Theatre Route 139 Charles Dickens Paddington Shoreditch Route 148 Great Warren Street St. Pancras Museum High Street 453 74 Baker Regent’s Portland and Euston Square 59 International Barbican Route 159 Street Park Centre Liverpool St Street (390 only) Route 188 Moorgate Appold Street Edgware Road 11 Route 205 Pollock’s 14 188 Theobald’s Toy Museum Russell Road Route 274 Square British Museum Route 390 Goodge Street of London 159 Museum Liverpool St Route 453 Marble Lancaster Arch Bloomsbury Way Bank Notting Hill 25 Gate Gate Bond Oxford Holborn Chancery 25 to Ilford Queensway Tottenham 8 148 274 Street Circus Court Road/ Lane Holborn St. 205 to Bow 73 Viaduct Paul’s to Shepherd’s Marble Cambridge Hyde Arch for City Bush/ Park Circus Thameslink White City Kensington Regent Street Aldgate (night Park Lane Eros journeys Gardens Covent Garden Market 15 only) Albert Shaftesbury to Blackwall Memorial Avenue Kingsway to Royal Tower Hammersmith Academy Nelson’s Leicester Cannon Hill 9 Royal Column Piccadilly Circus Square Street Monument 23 Albert Hall Knightsbridge London St. -

IWM-HMS-Belfast-Brochure.Pdf
WELCOME ABOARD There are certain occasions The Admiral’s Quarters which demand special Capacity: Minimum 18 / Maximum 20 (Subject to package) Comprising the original Dining Room and Lounge area of the Admiral’s own living quarters, treatment, where the the Admiral’s Quarters are the perfect space for both boardroom meetings and elegant dining. Restored to reflect how the space would have looked during the 1950’s, the choice of venue is crucial. Admiral’s Quarters provide a luxurious and intimate space for events. Seldom will you find one as unique as HMS Belfast. The Morgan Giles Room Capacity: Minimum 35 / Maximum 90 (Subject to package) Ideal for private dining, meetings, product launches, weddings, receptions and parties, HMS Belfast This room once served as an Officers’ mess and so includes a bar. Named after the UNIQUE Admiral who served in her and later was responsible for ensuring the ship was offers spectacular 360 degree views of London and authentically decorated rooms, each with their own saved from the scrap yard, the room has been restored to reflect the original individual characteristics. Guests can dine in the 1950’s décor and its wood panelled walls echo the camaraderie that was such a SPACES vital part of life on board this great ship. Officers’ Mess, climb a gun turret or watch the sun set on the Quarterdeck. CONFERENCES • MEETINGS DINING • PARTIES • SOCIAL OCCASIONS Permanently moored between London Bridge and The Ward & Ante Room Tower Bridge, HMS Belfast is the most significant Capacity: Minimum 30 / Maximum 100 (Subject to package) surviving Second World War Royal Navy warship. -

By Mike Klozar Have You Dreamed of Visiting London, but Felt It Would
By Mike Klozar Have you dreamed of visiting London, but felt it would take a week or longer to sample its historic sites? Think again. You can experience some of London's best in just a couple of days. Day One. • Thames River Walk. Take a famous London Black Cab to the Tower of London. The ride is an experience, not just a taxi. (15-30 min.) • Explore the Tower of London. Keep your tour short, but be sure to check out the Crown Jewels. (1-2 hrs.) • Walk across the Tower Bridge. It's the fancy blue one. (15 min.) From here you get the best view of the Tower of London for photos. • Cross over to Butler's Wharf and enjoy lunch at one of the riverfront restaurants near where Bridget lived in Bridget Jones's Diary. (1.5 hrs.) • Keeping the Thames on your right, you'll come to the warship HMS Belfast. Tours daily 10 a.m.-4 p.m. (30 min.-1 hr.) • Walk up London Bridge Street to find The Borough Market. Used in countless films, it is said to be the city's oldest fruit and vegetable market, dating from the mid-1200s. (1 hr.) • Back on the river, you'll discover a tiny ship tucked into the docks: a replica of Sir Francis Drake's Golden Hind, which braved pirates in the days of yore. (15 min.) • Notable London pubs are situated along the route and are good for a pint, a cup of tea and a deserved break. Kids are welcome. -
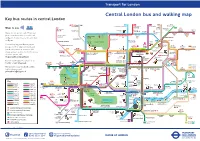
Central London Bus and Walking Map Key Bus Routes in Central London
General A3 Leaflet v2 23/07/2015 10:49 Page 1 Transport for London Central London bus and walking map Key bus routes in central London Stoke West 139 24 C2 390 43 Hampstead to Hampstead Heath to Parliament to Archway to Newington Ways to pay 23 Hill Fields Friern 73 Westbourne Barnet Newington Kentish Green Dalston Clapton Park Abbey Road Camden Lock Pond Market Town York Way Junction The Zoo Agar Grove Caledonian Buses do not accept cash. Please use Road Mildmay Hackney 38 Camden Park Central your contactless debit or credit card Ladbroke Grove ZSL Camden Town Road SainsburyÕs LordÕs Cricket London Ground Zoo Essex Road or Oyster. Contactless is the same fare Lisson Grove Albany Street for The Zoo Mornington 274 Islington Angel as Oyster. Ladbroke Grove Sherlock London Holmes RegentÕs Park Crescent Canal Museum Museum You can top up your Oyster pay as Westbourne Grove Madame St John KingÕs TussaudÕs Street Bethnal 8 to Bow you go credit or buy Travelcards and Euston Cross SadlerÕs Wells Old Street Church 205 Telecom Theatre Green bus & tram passes at around 4,000 Marylebone Tower 14 Charles Dickens Old Ford Paddington Museum shops across London. For the locations Great Warren Street 10 Barbican Shoreditch 453 74 Baker Street and and Euston Square St Pancras Portland International 59 Centre High Street of these, please visit Gloucester Place Street Edgware Road Moorgate 11 PollockÕs 188 TheobaldÕs 23 tfl.gov.uk/ticketstopfinder Toy Museum 159 Russell Road Marble Museum Goodge Street Square For live travel updates, follow us on Arch British -

Never-Before-Seen Documents Reveal IWM's Plan for Evacuating Its Art
Never-before-seen documents reveal IWM’s plan for evacuating its art collection during the Second World War Never-before-seen documents from Imperial War Museums’ (IWM) collections will be displayed as part of a new exhibition at IWM London, uncovering how cultural treasures in British museums and galleries were evacuated and protected during the Second World War. The documents, which include a typed notice issued to IWM staff in 1939, titled ‘Procedure in the event of war,’ and part of a collection priority list dated 1938, are among 15 documents, paintings, objects, films and sculptures that will be displayed as part of Art in Exile (5 July 2019 – 5 January 2020). At the outbreak of the Second World War, a very small proportion of IWM’s collection was chosen for special evacuation, including just 281works of art and 305 albums of photographs. This accounted for less than 1% of IWM’s entire collection and 7% of IWM’s art collection at the time, which held works by prominent twentieth- century artists including William Orpen, John Singer Sargent, Paul Nash and John Lavery. Exploring which works of art were saved and which were not, Art in Exile will examine the challenges faced by cultural organisations during wartime. With the exodus of Britain’s cultural treasures from London to safety came added pressures on museums to strike a balance between protecting, conserving and displaying their collections. The works on IWM’s 1938 priority list, 60 of which will be reproduced on one wall in the exhibition, were destined for storage in the country homes of IWM’s Trustees, where it was believed German bombers were unlikely to venture. -
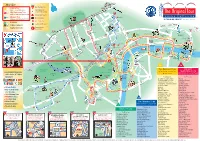
A4 Web Map 26-1-12:Layout 1
King’s Cross Start St Pancras MAP KEY Eurostar Main Starting Point Euston Original Tour 1 St Pancras T1 English commentary/live guides Interchange Point City Sightseeing Tour (colour denotes route) Start T2 W o Language commentaries plus Kids Club REGENT’S PARK Euston Rd b 3 u Underground Station r n P Madame Tussauds l Museum Tour Russell Sq TM T4 Main Line Station Gower St Language commentaries plus Kids Club q l S “A TOUR DE FORCE!” The Times, London To t el ★ River Cruise Piers ss Gt Portland St tenham Ct Rd Ru Baker St T3 Loop Line Gt Portland St B S s e o Liverpool St Location of Attraction Marylebone Rd P re M d u ark C o fo t Telecom n r h Stansted Station Connector t d a T5 Portla a m Museum Tower g P Express u l p of London e to S Aldgate East Original London t n e nd Pl t Capital Connector R London Wall ga T6 t o Holborn s Visitor Centre S w p i o Aldgate Marylebone High St British h Ho t l is und S Museum el Bank of sdi igh s B tch H Gloucester Pl s England te Baker St u ga Marylebone Broadcasting House R St Holborn ld d t ford A R a Ox e re New K n i Royal Courts St Paul’s Cathedral n o G g of Justice b Mansion House Swiss RE Tower s e w l Tottenham (The Gherkin) y a Court Rd M r y a Lud gat i St St e H n M d t ill r e o xfo Fle Fenchurch St Monument r ld O i C e O C an n s Jam h on St Tower Hill t h Blackfriars S a r d es St i e Oxford Circus n Aldwyc Temple l a s Edgware Rd Tower Hil g r n Reg Paddington P d ve s St The Monument me G A ha per T y Covent Garden Start x St ent Up r e d t r Hamleys u C en s fo N km Norfolk -

R.Ajnjr. Guished Services During the Operations Dn Korea:— Lieutenant Commander Fsp) G
4684 THE LONDON GAZETTE, 13 AUGUST, 1954 Whitehall, August 1'3', 1954. Major Ferris -Nelson GRANT, Royal Marines, 41 The QUEEN has been pleased by (Letters Patent Independent Commando, Royal Marines. under the Great Seal of 'the (Realm, bear-ing date the Legion of Merit, Degree of Legionnaire. 9th instant, to confer the honour of Knighthood Captain John Harold UNWIN, D.S.C., Royal Navy, upon Alan Stewart Watt, Esquire, CJB.E., Commis- HM.S. MOUNTS BAY. sioner for Australia in the Federation of Malaya. Bronze Star Medal. {Her Majesty's approval of this Knighthood was Commander Charles (Henry Francis JOY, Royal signified on the lOfA June, 1954.] Navy. Bronze Star Medal with Combat " V ". Captain James Jeffrey 'Edward FARNOL, D.S.C., Royal DA/NGBRQUS DRUGS (RIBGUiLATIOINS, 1053. Navy, H.M.S. MORECAMBE (BAY. SUSPENSION OF WITHDRAWAL OF AUTHORITIES. Lieutenant-Commander William (Edward Hunter Whereas the authorities, respectively conferred RopWELL, D.S.C., Royal Navy. by the {Dangerous Drugs Regulations, 1937, and Captain (Edgar George Derek POUNDS, Royal the Raw Opium, etc., Regulations, 1937, on Gerald Marines, 41 Independent Commando, Royal Stonehill, MjRjCS., L-RjCJP., by virtue of his being Marines. a duly qualified medical practitioner to be in posses- Captain Peter Roome THOMAS, Royal Marines, 41 sion of and to supply the drugs and preparations to Independent Commando, .Royal Marines. which those Regulations applied were, the said Quartermaster - Sergeant Charles Frederick Gerald Stonehill having been convicted of offences HAMBLETON, Ch. X. 1698, Royal Marines, 41 Jnde- against the Dangerous Drugs Acts, 1920 to 1932, pendent Commando, (Royal Marines withdrawn in pursuance of the powers conferred on Sergeant Joseph Jeremiah MAILL, Ch. -

Hew Locke Cv
HEW LOCKE CV Born 1959, Edinburgh Lives and works in London Education 1994 MA Sculpture, Royal College of Art, London, UK 1988 Falmouth University, UK, BA (Hons) Fine Art Selected Solo Exhibitions 2017-18 Reversal of Fortune, Fringe Projects Miami, The Alfred I. duPont Building, Miami, FL, USA For Those in Peril on the Sea, Perez Art Museum Miami, Miami, FL, USA Cui Bono, installation in Bremen Rathouse, originally comissioned in conjunction with Der Blinde Fleck by Kunsthalle Bremen, Bremen, Germany 2016 The Wine Dark Sea, Edward Tyler Nahem Fine Art, New York, USA 2015 IWM Contemporary: Hew Locke, IWM London, UK The Tourists, HMS Belfast, London, UK Magna Carta Commission, Runnymede Surrey, UK 2014 Beyond the Sea Wall, Hales Gallery, London, UK Give and Take, performance in the Turbine Hall, Tate Modern, London. Part of Up Hill Down Hall 2013 For Those in Peril on the Sea, installation at launch of Pérez Art Museum Miami, USA Adrift, All Hallows by the Tower Church, Thames Festival, London, UK 2012 Day of the Dead Festival, a new installation titled ‘Adrift’ created for the Old Vic Tunnels, London, UK 2011 For Those in Peril on the Sea, St. Mary & St. Eanswythe Church, Folkestone Triennial, UK The Nameless, KAdE Kunsthal, Amersfoort, the Netherlands Are We There Yet?, The Gallery, the Arts University College at Bournemouth, UK Starchitect, ArtSway, Hampshire & as part of The New Forest Pavillion, Venice Biennale, Venice, Italy 2010 The Nameless, Hales Gallery, London, UK 2008 The Kingdom of the Blind, Rivington Palace, London, UK How do you want me?, Hales Gallery, London, UK London, 7 Bethnal Green Road, E1 6LA. -

"Keeping Things Shipshape", Conservation Management on HMS
‘Keeping Things Shipshape’ Conservation Management on HMS Belfast MA Museum Studies 2013 Amy Foulds Abstract Amy Foulds Word Count: 12, 770 ‘Keeping Things Shipshape’: Conservation Management on HMS Belfast This study aims to highlight the difficulties of conserving historic ships when they are required to function as an accessible museum as well as officially being an accessioned museum object, and how these difficulties can be successfully managed. By framing the assessment of HMS Belfast’s conservation management plan in the wider debate surrounding large object conservation and the levels of restoration rather than preservation that have been considered acceptable in the past, the key shift in attitude to a more ethical, museum-focused approach can be better appreciated. Through interviews with staff and volunteers directly involved in the conservation process, an idea of how the ship’s Conservation Policy was created and how it can be implemented to ensure the preservation of the ship’s original fabric and key historic significance can be gained. Once the contents of the policy and how they affect conservation planning in theory are understood, the impact of providing access and interpretation to visitors, limited resources and external environmental factors is considered, along with the various techniques employed in managing them utilising policy frameworks to ensure minimum destruction of historical evidence. Through contact with other museum ships, benchmarks to assess success can be established, with favourable comparisons being drawn internationally. Finally, there are suggestions for improvements and opportunities for the future, both for HMS Belfast and other historic vessels. ! ! ! ! ! ! ! ! "#$%&'()*+),)%-.! ! Firstly I would like to show my appreciation to my Dissertation Supervisor, Dieter Hopkin, and the Museum Studies Department at the University of Leicester for all of their advice and guidance during the completion of this project. -

HMS BELFAST Private Tours IWM.ORG.UK Private Tours
HMS BELFAST Private Tours IWM.ORG.UK Private Tours A guided tour of HMS Belfast, will bring the ship to life with stories of heroism and humour, as you learn what it was like to serve onboard. The historic warship served in the freezing waters of the Arctic Convoys, was one of the first ships to fire her guns on D-Day and had an important role as part of the United Nations forces in Korea in the early 1950s. You will learn about all this and more as you climb her nine decks, from the bottom boiler deck plates to the gun direction platform on the superstructure. A private tour of of HMS Belfast offers a unique experience to tour the ship with one of our Yeoman Expert Guides. The tour follows the route from the stern forwards, starting with an introduction on the Quarterdeck. You will visit the boiler and engine rooms, sick bay, provision issue rooms, shell rooms, the mess, the big guns and finally the bridge. Tours can be tailored if you have questions regarding the trades of your relatives who served in the periods discussed. Please forward any questions of this nature in advance. Visitors may wish to visit Tom’s Kitchen, our quayside deli, or Tom’s Bar which has amazing views of Tower Bridge and the Thames for a refreshment break, before or after the tour. © IWM_SITE_BELF_249 Tour Prices Tours last approximately one hour Before Hours (08.00 -10.00) £400 During Hours £300 (Summer 10.00 -16.45 Winter 10.00 -15.45) After Hours £400 (Summer from 18.30 Winter from 17.30) Weekend and Bank Holiday £400 Capacity Maximum of 12 people per each tour group To make a booking, please advise ▪ The tour guide level you would be interested in. -

Delegate Guide Old Billingsgate Market, London 28Th September 2021
ONE DAY ■ ONE MARKET ■ UNLIMITED OPPORTUNITIES DELEGATE GUIDE OLD BILLINGSGATE MARKET, LONDON 28TH SEPTEMBER 2021 Sponsored by WWW.CRMARKETPLACE.COM Brought to you by Follow us 2 LOCATION Old Billingsgate Market, The venue is in the heart of the City of 1 Old Billingsgate Walk, London; the Grade II Victorian building 16 Lower Thames St, London, that was originally Billingsgate fish market EC3R 6DX provides a flexible space in a convenient retail location close to a range of London T E E BANK R T Tube Stations. S H C R U H C E The venue provides us with up to 40,000 MANSION HOUSE C A R G sq ft of purpose built and flexible space to LONDON CANNON STREET accommodate everyone in one room. U MONUMENT PPE R T HA ME S S TR ■ EET The space is enclosed and air LOWE R THA conditioned so everyone will be MES S TREET E G comfortable whatever the weather RIVER THAMES D I R B N outside. O D N O L ■ It has modern facilities and a huge terrace fronting The Thames with stunning views of London Bridge, LONDON BRIDGE The Shard and HMS Belfast. Travelling to the event Old Billingsgate Market is easily accessible from a number of Central London mainline, London Underground and Docklands Light Railway stations. The nearest mainline station is Fenchurch Street. The nearest tube stations are Monument and Bank station, both just 5 minutes away. There is a recommended list of hotels available via the website. Please note that the prices quoted may vary at the time of booking and are all subject to availability.