Open PDF Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
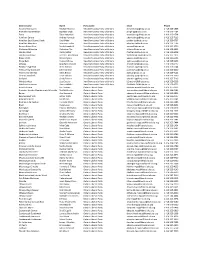
District Name
District name Name Party name Email Phone Algoma-Manitoulin Michael Mantha New Democratic Party of Ontario [email protected] 1 416 325-1938 Bramalea-Gore-Malton Jagmeet Singh New Democratic Party of Ontario [email protected] 1 416 325-1784 Essex Taras Natyshak New Democratic Party of Ontario [email protected] 1 416 325-0714 Hamilton Centre Andrea Horwath New Democratic Party of Ontario [email protected] 1 416 325-7116 Hamilton East-Stoney Creek Paul Miller New Democratic Party of Ontario [email protected] 1 416 325-0707 Hamilton Mountain Monique Taylor New Democratic Party of Ontario [email protected] 1 416 325-1796 Kenora-Rainy River Sarah Campbell New Democratic Party of Ontario [email protected] 1 416 325-2750 Kitchener-Waterloo Catherine Fife New Democratic Party of Ontario [email protected] 1 416 325-6913 London West Peggy Sattler New Democratic Party of Ontario [email protected] 1 416 325-6908 London-Fanshawe Teresa J. Armstrong New Democratic Party of Ontario [email protected] 1 416 325-1872 Niagara Falls Wayne Gates New Democratic Party of Ontario [email protected] 1 416 212-6102 Nickel Belt France GŽlinas New Democratic Party of Ontario [email protected] 1 416 325-9203 Oshawa Jennifer K. French New Democratic Party of Ontario [email protected] 1 416 325-0117 Parkdale-High Park Cheri DiNovo New Democratic Party of Ontario [email protected] 1 416 325-0244 Timiskaming-Cochrane John Vanthof New Democratic Party of Ontario [email protected] 1 416 325-2000 Timmins-James Bay Gilles Bisson -

RIDING MPP CANDIDATE PARTY Ajax Joe Dickson Liberal Stephen
RIDING MPP CANDIDATE PARTY Ajax Joe Dickson Liberal Stephen Leahy Green Rod Phillips PC Monique Hughes NDP Algoma—Manitoulin Charles Fox Liberal Justin Tilson Green Jib Turner PC Michael Mantha NDP Aurora - Oak Ridges - Richmond Hill Naheed Yaqubian Liberal Stephanie Nicole Duncan Green Michael Parsa PC Katrina Sale NDP Barrie-Innisfil Bonnie North Green Pekka Reinio NDP Andrea Khanjin PC Ann Hoggarth Liberal Barrie-Springwater-Oro-Medonte Keenan Aylwin Green Jeff Kerk Liberal Doug Downey PC Dan Janssen NDP Bay of Quinte Robert Quaiff Liberal Mark Daye Green Todd Smith PC Joanne Belanger NDP Beaches—East York Rima Berns-McGown NDP Arthur Potts Liberal Debra Scott Green Sarah Mallo PC Brampton Centre Safdar Hussain Liberal Laila Zarrabi Yan Green Harjit Jaswal PC Sara Singh NDP Brampton East Dr. Parminder Singh Liberal Raquel Fronte Green Sudeep Verma PC Gurratan Singh NDP Brampton North Harinder Malhi Liberal Pauline Thornham Green Ripudaman Dhillon PC Kevin Yarde NDP Brampton South Sukhwant Thethi Liberal Lindsay Falt Green Prabmeet Sarkaria PC Paramjit Gill NDP Brampton West Vic Dhillon Liberal Julie Guillemet-Ackerman Green Amarjot Sandhu PC Jagroop Singh NDP Brantford - Brant Ruby Toor Liberal Ken Burns Green Will Bouma PC Alex Felsky NDP Bruce—Grey—Owen Sound Elizabeth Marshall Trillium Francesca Dobbyn Liberal Don Marshall Green Karen Gventer NDP Bill Walker PC Burlington Jane McKenna PC Eleanor McMahon Liberal Andrew Drummond NDP Vince Fiorito Green Cambridge Kathryn McGarry Liberal Michele Braniff Green Belinda Karahalios PC Marjorie -

Director's Bulletin
Validating our Mission/Vision May 15, 2006 IFITH RESPECT FOR LIFE WEEK May 14 – 20, 2006 T Subjects: H DIRECTOR’S E 1. SAINTS OF THE TORONTO CATHOLIC DISTRICT SCHOOL BOARD BULLETIN 2. RESPECT FOR LIFE WEEK--repeat 2005-2006 3. AID TO WOMEN--repeat 4. PROFESSION DEVELOPMENT ONE-TIME PAYMENT In a school community 5. PERMITS FOR SCHOOL FUNCTIONS formed by Catholic 6. MAY IS SPEECH, LANGUAGE AND HEARING MONTH beliefs and traditions, 7. SCHOOL ANNIVERSARIES, OFFICIAL OPENINGS & BLESSINGS our Mission is to - St. Marcellus’ 40th Anniversary educate students - Loretto College Solemn Blessing & Official Opening to their full potential 8. EVENT NOTICES - Walk Against Violence Everywhere (W.A.V.E.) --repeat - Poetry Reciting Contest in Filipino - Dante Alighieri’s Faith Day with Fr. Stan--repeat - Bishop Marrocco/Thomas Merton’s ‘Monte Cristo’--repeat A Community of Faith - Senator O’Connor’s ‘Grease’ - TCDSB Staff Arts’ ‘Anne of Green Gables’--repeat 9. SHARING OUR GOOD NEWS - St. Luke Catholic School - St. Andrew, St. Boniface and St. Charles Garner Catholic Schools With Heart in Charity - St. Charles Catholic School - Prince of Peace Catholic School - Brebeuf College School - Immaculate Conception Catholic School - TCDSB’s Go Outside the Box Anchored in Hope - TCDSB’s International Languages Symposium 10. MEMORIALS 11. BIRTHS AND ADOPTIONS 12. BENEFITS CORNER - Additional Benefits Deductions--repeat 13. OCCUPATIONAL HEALTH & SAFETY - WHMIS Training Completions The Toronto Catholic District 14 PROFESSIONAL DEVELOPMENT OPPORTUNITIES School Board -

Queen's Park Notes
Queen’s Park notes FOLLOW US @Mobilepk For the week of October 3–7, 2016 NEW BILLS INTRODUCED BILL 31, JONATHAN’S LAW (EMPLOYEE Reform Amendment Act (Relationship with LEAVE OF ABSENCE WHEN CHILD DIES) Grandparents). Mantha’s bill makes one addition NDP MPP Peter Tabuns (Toronto—Danforth) and one amendment to the Children’s Law Reform introduced Bill 31, Jonathan’s Law (Employee Act. The addition prohibits a person entitled to Leave of Absence When Child Dies). Tabuns’ custody of a child from creating or maintaining bill would allow employees, who have been unreasonable barriers to the formation and employed for at least six consecutive months, continuation of personal relationships between a leave of absence without pay for up to 52 the child and the child’s grandparents. The weeks, if a child of the employee dies. amendment would set out the needs and circumstances of a child that the court must BILL 32, RIGHT TO CARE ACT (CHILDREN 16 consider in determining the best interests of the YEARS OF AGE AND OLDER) child. The bill adds to that list the emotional ties PC MPP Jim McDonell (Stromont—Dundas— between the child and the child’s grandparents South Glengarry) introduced Bill 32, Right to and the willingness of each person applying for Care Act (Children 16 Years of Age and Older). custody of the child to facilitate contact with the McDonnell’s bill would amend the Child and child’s grandparents, if such contact would be Family Services Act. The bill would amend the appropriate in the circumstances. law to allow temporary care agreements to be made in respect of children who are 16 years of BILL 35, EMPOWERING HOME CARE age or older. -

2018 Election Liberal Party of Ontario Candidates
2018 Election Liberal Party of Ontario Candidates NAME RIDING WEBSITE LINK Joe Dickson Ajax [email protected] Naheed Yaqubian Aurora-Oak Ridges- [email protected] Richmond Hill Ann Hoggarth Barrie-Innisfil [email protected] Robert Quaiff Bay of Quinte [email protected] Arthur Potts Beaches-East York [email protected] Safdar Hussain Brampton Centre [email protected] Dr. Parminder Singh Brampton East [email protected] Harinder Malhi Brampton North [email protected] Sukhwant Thethi Brampton South [email protected] Vic Dhillon Brampton West [email protected] Ruby Toor Brantford-Brant [email protected] Francesca Dobbyn Bruce-Grey-Owen Sound [email protected] Eleanor McMahon Burlington [email protected] Kathryn McGarry Cambridge [email protected] Theresa Qadri Carleton [email protected] Margaret Schleier Stahl Chatham-Kent-Leamington [email protected] Cristina Martins Davenport [email protected] Michael Coteau Don Valley East [email protected] Shelley Carroll Don Valley North [email protected] Kathleen Wynne Don Valley West [email protected] Bob Gordanier Dufferin-Caledon [email protected] Granville Anderson Durham [email protected] 1 | P a g e NAME RIDING WEBSITE LINK Mike Colle Eglinton-Lawrence [email protected] Carlie Forsythe -

June 28, 2004 Hon. Dalton Mcguinty Premier Room 281 Legislative Building Toronto on M7A 1A1 Dear Premier, the Ontario Public He
The mission of OPHA is to provide leadership on issues affecting the public’s health and to strengthen the impact of people who are active in public and community health throughout Ontario. 700 Lawrence Ave. W., Suite 310 June 28, 2004 Toronto, Ontario M6A 3B4 Tel: (416) 367-3313 Hon. Dalton McGuinty 1-800-267-6817 (Ont) Premier Fax: (416) 367-2844 Room 281 Legislative Building E-mail: [email protected] www.opha.on.ca Toronto ON M7A 1A1 Honorary Patron The Hon. David C. Onley Dear Premier, Lieutenant Governor of Ontario The Ontario Public Health Association (OPHA) congratulates you for President Carol Timmings your decision to allocate an additional four million dollars for school- E-mail: [email protected] based children's breakfast programs in Ontario. We share your appreciation of the health and educational benefits these programs Executive Director Connie Uetrecht promote in students who participate. In order to be assured of the E-mail: [email protected] most positive use of this additional funding, the OPHA respectfully makes the following suggestions: Constituent Societies ANDSOOHA – Public Health Nursing Management in Ontario 1. Money needed to fund programs for the coming school year (2004-5) should be directed as soon as possible to Breakfast Association of Ontario Health Centres for Learning. This will minimize confusion among all of the organizations that work in the field of breakfast programs, Association of Public Health provide adequate time to alert all stakeholders about any Epidemiologists in Ontario impending changes, and ensure that there will be no Association of Supervisors of Public disruption of funding to the many organizations that operate Health Inspectors of Ontario on limited budgets. -

Human-Capital-Report 2018.Pdf
Contents Message from the Organizers.............................................................................................................................2 Acknowledgements .............................................................................................................................................4 Francophone Human Capital Forum ...................................................................................................................6 Background .........................................................................................................................................................8 Research Methodology .......................................................................................................................................10 Research Findings ..............................................................................................................................................12 Mercer Report .....................................................................................................................................................12 Key findings - What are the current Francophone Employment Opportunities in Ontario?.................................12 Francophone Human Capital Forum Roundtable Discussions ...........................................................................15 Research Scope .................................................................................................................................................18 RESEARCH COMISSIONED -

Old Times John Stackhouse ’81 Is Reinventing the Daily News Winter/Spring 2011 Page 12 U Pper Can Ada College’S Alumni P Ubli Catio N
CHANGE MAKERS: OLD TIMES JOHN STACKHOUSE ’81 IS REINVENTING THE DAILY NEWS WINTER/SPRING 2011 PAGE 12 U PPER CAN ADA COLLEGE’S ALUMNI P UBLI CATIO N FOR AGAINST THE ART OF DEBATE ‘REV UP’ YOUR POWERS OF PERSUASION Winter/Spring 2011 Old Times i About Contents this issue he reputation of our UCC debaters, as a powerhouse on It was an unnerving tactic. Usually, boisterous UCC fans Cover story the national stage, has been gathering momentum over cheer player introductions and good plays. That night, the 4 The Art of Debate: The Power of Persuasion the past half decade. As you’ll read in our cover story, 300-strong UCC crowd was silent — until the 10th point T UCC’s current crop of debaters is emerging as a pow- we’re exceedingly proud of their work, not just as debating as they’d been briefed in Assembly. With UCC up 7–2, FY 4 erhouse on the national stage. Plus as the Old Boys superstars but as ambassadors for the College. Their true mis- student Oneil Halstead scored a three pointer and the featured here illustrate, debating furnishes you with sion is to promote the value of measured perspective and the crowd erupted. By all accounts, UCC’s 52–44 victory can be some of the great life skills — the ability to persuade quest for common ground, as among the most potent persua- attributed in some measure to the Blue Army’s “assault.” Old Times is produced and lead, whatever your calling. sion and leadership tactics, whatever your career or life path. -

2018 Ontario Candidates List May 8.Xlsx
Riding Ajax Joe Dickson ‐ @MPPJoeDickson Rod Phillips ‐ @RodPhillips01 Algoma ‐ Manitoulin Jib Turner ‐ @JibTurnerPC Michael Mantha ‐ @ M_Mantha Aurora ‐ Oak Ridges ‐ Richmond Hill Naheed Yaqubian ‐ @yaqubian Michael Parsa ‐ @MichaelParsa Barrie‐Innisfil Ann Hoggarth ‐ @AnnHoggarthMPP Andrea Khanjin ‐ @Andrea_Khanjin Pekka Reinio ‐ @BI_NDP Barrie ‐ Springwater ‐ Oro‐Medonte Jeff Kerk ‐ @jeffkerk Doug Downey ‐ @douglasdowney Bay of Quinte Robert Quaiff ‐ @RQuaiff Todd Smith ‐ @ToddSmithPC Joanne Belanger ‐ No social media. Beaches ‐ East York Arthur Potts ‐ @apottsBEY Sarah Mallo ‐ @sarah_mallo Rima Berns‐McGown ‐ @beyrima Brampton Centre Harjit Jaswal ‐ @harjitjaswal Sara Singh ‐ @SaraSinghNDP Brampton East Parminder Singh ‐ @parmindersingh Simmer Sandhu ‐ @simmer_sandhu Gurratan Singh ‐ @GurratanSingh Brampton North Harinder Malhi ‐ @Harindermalhi Brampton South Sukhwant Thethi ‐ @SukhwantThethi Prabmeet Sarkaria ‐ @PrabSarkaria Brampton West Vic Dhillon ‐ @VoteVicDhillon Amarjot Singh Sandhu ‐ @sandhuamarjot1 Brantford ‐ Brant Ruby Toor ‐ @RubyToor Will Bouma ‐ @WillBoumaBrant Alex Felsky ‐ @alexfelsky Bruce ‐ Grey ‐ Owen Sound Francesca Dobbyn ‐ @Francesca__ah_ Bill Walker ‐ @billwalkermpp Karen Gventer ‐ @KarenGventerNDP Burlington Eleanor McMahon ‐@EMcMahonBurl Jane McKenna ‐ @janemckennapc Cambridge Kathryn McGarry ‐ Kathryn_McGarry Belinda Karahalios ‐ @MrsBelindaK Marjorie Knight ‐ @KnightmjaKnight Carleton Theresa Qadri ‐ @TheresaQadri Goldie Ghamari ‐ @gghamari Chatham‐Kent ‐ Leamington Rick Nicholls ‐ @RickNichollsCKL Jordan -

Etobicoke North Action on Poverty Profile
Etobicoke North Action on Poverty Profile Story Behind the Stats The Etobicoke North riding lies in the very northwest corner of Toronto and includes Wards 1 and 2. It is bordered by the Humber River to the east and Dixon Road/Highway 401 to the south. Many young people in this area live in poverty, as they face high rates of unemployment, are food insecure, and live with parents who struggle to pay the rent on minimum wage incomes. Youth drop out of school at higher rates than in other areas of Toronto and, unable to find work, may drift into gang-related and criminal activity. Key Figures 108,505 people live in % Etobicoke North 27,160 live in poverty – 25.4%* Population living 25.4 in poverty 24.5 Children (under 37.1 18) living in “Poverty in this community is poverty 31.8 cyclical. The disadvantages it Housing in need of 8.3 major repairs 7.8 creates for community members actually keep them from escaping 10.2 Crowded housing 4.7 it.” 40.6 Tenant households 45.6 Althea Martin-Risden Director of Community Programs and Services Rexdale Community Health Centre Etobicoke North City of Toronto The Action on Poverty profile series was created by Social Planning Toronto and the Alliance for a Poverty-Free Toronto. The profile includes Census data from Statistics Canada’s Federal Electoral District Profiles and Community Profiles. *For details on calculations and definitions, go to www.spno.ca Taking Action in Etobicoke North The Rexdale Community Health Centre (CHC) is committed to achieving a healthier community by advocating for the physical, economic, social, and mental well-being of the community through primary health care, community programs, advocacy, and so on. -

2018 Ontario Candidates List Updated June 1
Riding Ajax Joe Dickson - @MPPJoeDickson Rod Phillips - @RodPhillips01 Monique Hughes - @monique4ajax Algoma - Manitoulin Charles Fox - @votecharlesfox Jib Turner - @JibTurnerPC Michael Mantha - @M_Mantha Aurora - Oak Ridges - Richmond Hill Naheed Yaqubian - @yaqubian Michael Parsa - @MichaelParsa Katrina Sale - No social media Barrie-Innisfil Ann Hoggarth - @AnnHoggarthMPP Andrea Khanjin - @Andrea_Khanjin Pekka Reinio - @BI_NDP Barrie - Springwater - Oro-Medonte Jeff Kerk - @jeffkerk Doug Downey - @douglasdowney Dan Janssen - @bsom_ondp Bay of Quinte Robert Quaiff - @RQuaiff Todd Smith - @ToddSmithPC Joanne Belanger - No social media Beaches - East York Arthur Potts - @apottsBEY Sarah Mallo - @sarah_mallo Rima Berns-McGown - @beyrima Brampton Centre Safdar Hussain - No social media Harjit Jaswal - @harjitjaswal Sara Singh - @SaraSinghNDP Brampton East Parminder Singh - @parmindersingh Simmer Sandhu - @simmer_sandhu Gurratan Singh - @GurratanSingh Brampton North Harinder Malhi - @Harindermalhi Ripudaman Dhillon - @ripudhillon_bn Kevin Yarde - @KevinYardeNDP Brampton South Sukhwant Thethi - @SukhwantThethi Prabmeet Sarkaria - @PrabSarkaria Paramjit Gill - @ParamjitGillNDP Brampton West Vic Dhillon - @VoteVicDhillon Amarjot Singh Sandhu - @sandhuamarjot1 Jagroop Singh - @jagroopsinghndp Brantford - Brant Ruby Toor - @RubyToor Will Bouma - @WillBoumaBrant Alex Felsky - @alexfelsky Bruce - Grey - Owen Sound Francesca Dobbyn - @Francesca__ah_ Bill Walker - @billwalkermpp Karen Gventer - @KarenGventerNDP Burlington Andrew Drummond - No Twitter, -

Public Accounts of Ontario 2004-05 Volume 3 / Comptes Publiques De L
Comptes publics de l’ Public Accounts of I N I S T R Y O F I N I S T È R E D E S M M F I N A N C E F I N A N C E S Public Comptes ONTARIO ONTARIO Accounts publics of de ONTARIO l’ONTARIO 2004-2005 2004–2005 This publication is available in English and in French. Copies in either language may be obtained by mail from Publications Ontario, 50 Grosvenor Street, Toronto, Ontario M7A 1N8; by calling (416) 326-5300, toll-free 1-800-668-9938; or by visiting the Publications Ontario Bookstore at 880 Bay Street, Toronto. D E T A I L E D S C H E D U L E S For further options, including on-line ordering, please visit the Publications Ontario website at www. publications.gov.on.ca. For electronic access, visit the Ministry of Finance website at www.fin.gov.on.ca. O F P A Y M E N T S Ce document est publié en français et en anglais. On peut obtenir l’une ou l’autre de ces versions par la poste en écrivant à Publications Ontario, 50, rue Grosvenor, Toronto (Ontario) M7A 1N8 ou en télé- phonant au 416 326-5300 ou au 1 800 668-9938 (interurbains sans frais). On peut aller en chercher des D É T A I L S D E S P A I E M E N T S exemplaires à la librairie de Publications Ontario, située au 880, rue Bay, Toronto.