Chapter 5 Link Layer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ipv6 … a Simplified Explanation
IPv6 … A Simplified Explanation Presented by Bryan Crisler Senior Network Engineer Time Warner Cable Housekeeping • Take this time to locate: – Emergency Exits – Bathrooms – Breakroom/Water Fountain – Note taking utensils • Put your Phones on Vibrate – If you need to take a call, feel free to step out of the room. About your Speaker • Bryan Crisler – Started in Cable @ Charter Communications, Riverside, CA in June 2005 – Currently a Senior Network Engineer at Time Warner Cable About your Speaker • Held following positions: – Broadband Technician I-IV (Charter) – Network Operations Specialist (Charter) – Network Technician (Charter) – Network Engineer (Charter & TWC) – SR Network Engineer (TWC) About your Speaker • Email: [email protected] • LinkedIn: linkedin.com/in/bcrisler Today’s Lesson Plan • Session 1: So What About IPv6? • Session 2: Every Day IPv6 and You So What About IPv6? Session 1 Basic History of IP • IP – Internet Protocol • Defined in RFC 791, dated 1981, written by Information Sciences Institute @ USC • Written for DARPA (Defense Advanced Research Projects Agency) Basic History of IP • “… Internet Protocol is designed for use in interconnected systems of packet-switched computer communication networks…provides for transmitting blocks of data called datagrams from sources to destinations… identified by fixed length addresses.” (RFC 791, section 1.1) Versions of IP • IPv0 – 3: Experimental Only • IPv4: Defined in 1981 by RFC 760 & 791. First version to implemented publically. Still in use today. • IPv5: Also experimental, called Internet Stream Protocol. • IPv6: Also called IP Next Generation (IPng), Defined in 1998 by RFC 2460-2467 IP Addressing • Layer 3 (Network) form of Addressing • Two different forms of IP Address: – IPv4 • Uses Dotted Decimal (192.168.0.1) • Has 4,294,967,296 total address (public & private) • 32 bit address – IPv6 • Uses Hexadecimal Notation (FE80::1) • Has 3.4×1038 total address (public & private) • 128 bit address IP Addressing – cont. -

DE-CIX Academy Handout
Networking Basics 04 - User Datagram Protocol (UDP) Wolfgang Tremmel [email protected] DE-CIX Management GmbH | Lindleystr. 12 | 60314 Frankfurt | Germany Phone + 49 69 1730 902 0 | [email protected] | www.de-cix.net Networking Basics DE-CIX Academy 01 - Networks, Packets, and Protocols 02 - Ethernet 02a - VLANs 03 - the Internet Protocol (IP) 03a - IP Addresses, Prefixes, and Routing 03b - Global IP routing 04 - User Datagram Protocol (UDP) 05 - TCP ... Layer Name Internet Model 5 Application IP / Internet Layer 4 Transport • Data units are called "Packets" 3 Internet 2 Link Provides source to destination transport • 1 Physical • For this we need addresses • Examples: • IPv4 • IPv6 Layer Name Internet Model 5 Application Transport Layer 4 Transport 3 Internet 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) • Also may contain information about the next layer up Encapsulation Packets inside packets • Encapsulation is like Russian dolls Attribution: Fanghong. derivative work: Greyhood https://commons.wikimedia.org/wiki/File:Matryoshka_transparent.png Encapsulation Packets inside packets • Encapsulation is like Russian dolls • IP Packets have a payload Attribution: Fanghong. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

User Datagram Protocol - Wikipedia, the Free Encyclopedia Página 1 De 6
User Datagram Protocol - Wikipedia, the free encyclopedia Página 1 de 6 User Datagram Protocol From Wikipedia, the free encyclopedia The five-layer TCP/IP model User Datagram Protocol (UDP) is one of the core 5. Application layer protocols of the Internet protocol suite. Using UDP, programs on networked computers can send short DHCP · DNS · FTP · Gopher · HTTP · messages sometimes known as datagrams (using IMAP4 · IRC · NNTP · XMPP · POP3 · Datagram Sockets) to one another. UDP is sometimes SIP · SMTP · SNMP · SSH · TELNET · called the Universal Datagram Protocol. RPC · RTCP · RTSP · TLS · SDP · UDP does not guarantee reliability or ordering in the SOAP · GTP · STUN · NTP · (more) way that TCP does. Datagrams may arrive out of order, 4. Transport layer appear duplicated, or go missing without notice. TCP · UDP · DCCP · SCTP · RTP · Avoiding the overhead of checking whether every RSVP · IGMP · (more) packet actually arrived makes UDP faster and more 3. Network/Internet layer efficient, at least for applications that do not need IP (IPv4 · IPv6) · OSPF · IS-IS · BGP · guaranteed delivery. Time-sensitive applications often IPsec · ARP · RARP · RIP · ICMP · use UDP because dropped packets are preferable to ICMPv6 · (more) delayed packets. UDP's stateless nature is also useful 2. Data link layer for servers that answer small queries from huge 802.11 · 802.16 · Wi-Fi · WiMAX · numbers of clients. Unlike TCP, UDP supports packet ATM · DTM · Token ring · Ethernet · broadcast (sending to all on local network) and FDDI · Frame Relay · GPRS · EVDO · multicasting (send to all subscribers). HSPA · HDLC · PPP · PPTP · L2TP · ISDN · (more) Common network applications that use UDP include 1. -

Network Connectivity and Transport – Transport
Idaho Technology Authority (ITA) ENTERPRISE STANDARDS – S3000 NETWORK AND TELECOMMUNICATIONS Category: S3510 – NETWORK CONNECTIVITY AND TRANSPORT – TRANSPORT CONTENTS: I. Definition II. Rationale III. Approved Standard(s) IV. Approved Product(s) V. Justification VI. Technical and Implementation Considerations VII. Emerging Trends and Architectural Directions VIII. Procedure Reference IX. Review Cycle X. Contact Information Revision History I. DEFINITION Transport provides for the transparent transfer of data between different hosts and systems. The two (2) primary transport protocols in the Transmission Control Protocol/Internet Protocol (TCP/IP) suite are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). II. RATIONALE Idaho State government must be able to easily, reliably, and economically communicate data and information to conduct State business. TCP/IP is the protocol standard used throughout the global Internet and endorsed by ITA Policy 3020 – Connectivity and Transport Protocols, for use in State government networks (LAN and WAN). III. APPROVED STANDARD(S) TCP/IP Transport: 1. Transmission Control Protocol (TCP); and 2. User Datagram Protocol (UDP). IV. APPROVED PRODUCT(S) Standards-based products and architecture S3510 – Network Connectivity and Transport – Transport Page 1 of 2 V. JUSTIFICATION TCP and UDP are the transport standards for critical State applications like electronic mail and World Wide Web services. VI. TECHNICAL AND IMPLEMENTATION CONSIDERATIONS It is also important to carefully consider the security implications of the deployment, administration, and operation of a TCP/IP network. VII. EMERGING TRENDS AND ARCHITECTURAL DIRECTIONS The use of TCP/IP (Internet) protocols and applications continues to increase. Agencies purchasing new systems may want to consider compatibility with the emerging Internet Protocol Version 6 (IPv6), which was designed by the Internet Engineering Task Force to replace IPv4 and will dramatically expand available IP addresses. -

Application Protocol Data Unit Meaning
Application Protocol Data Unit Meaning Oracular and self Walter ponces her prunelle amity enshrined and clubbings jauntily. Uniformed and flattering Wait often uniting some instinct up-country or allows injuriously. Pixilated and trichitic Stanleigh always strum hurtlessly and unstepping his extensity. NXP SE05x T1 Over I2C Specification NXP Semiconductors. The session layer provides the mechanism for opening closing and managing a session between end-user application processes ie a semi-permanent dialogue. Uses MAC addresses to connect devices and define permissions to leather and commit data 1. What are Layer 7 in networking? What eating the application protocols? Application Level Protocols Department of Computer Science. The present invention pertains to the convert of Protocol Data Unit PDU session. Network protocols often stay to transport large chunks of physician which are layer in. The term packet denotes an information unit whose box and tranquil is remote network-layer entity. What is application level security? What does APDU stand or Hop sound to rot the meaning of APDU The Acronym AbbreviationSlang APDU means application-layer protocol data system by. In the context of smart cards an application protocol data unit APDU is the communication unit or a bin card reader and a smart all The structure of the APDU is defined by ISOIEC 716-4 Organization. Application level security is also known target end-to-end security or message level security. PDU Protocol Data Unit Definition TechTerms. TCPIP vs OSI What's the Difference Between his Two Models. The OSI Model Cengage. As an APDU Application Protocol Data Unit which omit the communication unit advance a. -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random -

Br-Asi01 Br-Asx01
BR-ASI01 BR-ASX01 Data Comm for Business, Inc. 807 Pioneer Street Champaign, IL 61820 217-352-3207 Rev. Date: October 17, 1996 This manual applies to both the “I” and “X” router models. The “I” model (BR-ASI01) is single protocol TCP/IP only. The “X” model (BR-ASX01) is a multi-protocol router that routes TCP/IP, IPX, DECnet, and Appletalk. When using this manual with “I” model router, ignore the manual sections pertaining to protocols other than TCP/IP. CHAPTER 1 - INTRODUCTION 7 ABOUT THE BR ROUTER 7 Getting Started 7 Hardware Installation 7 RouterView Software Installation 8 Command Line Preparation 8 Quickstart Configuration 8 Appendices and Index 8 CHAPTER 2 - GETTING STARTED 9 A FEW NOTES 9 Please Read The Manuals 9 Warranty and Service 9 Getting Help With the BR Router 9 WHAT YOU WILL NEED TO GET STARTED 9 Supplied with the BR Router 9 Needed For Installation 10 Ethernet Connection Requirements 10 Thick Ethernet 10 Thin Ethernet 10 10Base-T Twisted-Pair Ethernet 10 Telco Line Connection Requirements 11 RS-232 Port 11 CHAPTER 3 - HARDWARE INSTALLATION 13 Mounting the Router 13 Connecting the Router to the Ethernet 14 Connecting to Thick Ethernet 14 Connecting to Thin Ethernet 14 Connecting to Twisted-Pair Ethernet 14 Connecting a Line Device to the BR Router 14 Connecting Devices to the RS-232C Port 15 Connecting an Out-of-Band Management Console 15 Powering Up the Router 15 CHAPTER 4 - ROUTERVIEW SOFTWARE INSTALLATION 17 RouterView for Windows 17 System Requirements 17 Installing and Running RouterView for Windows 17 RouterView -

Discussion Chapter#9 Services of Data-Link
The Islamic University of Gaza ECOM 4314: Data Communication Faculty of Engineering Instructor: Dr. Aiman Abu Samra Department of Computer Engineering T.A.: Eng. Alaa O. Shama Discussion Chapter#9 The data-link layer of a node (host or router) is responsible for delivering a datagram to the next node in the path. The data-link layer is located between the physical and the network layers. The datalink layer provides services to the network layer; it receives services from the physical layer. data-link layer of the source host needs only to encapsulate the datagram received from the network in a frame, the data-link layer of the destination host needs to decapsulate the datagram from the frame, but each intermediate node needs to both encapsulate and decapsulate, because each link may be using a different protocol with a different frame format. Even if one link and the next are using the same protocol, encapsulation and decapsulation are needed because the link-layer addresses are normally different. Services of Data-Link: 1. Framing The data-link layer at each node needs to encapsulate the datagram (packet received from the network layer) in a frame before sending it to the next node. The node also needs to decapsulate the datagram from the frame received on the logical channel. 2. Flow control If the rate of produced frames is higher than the rate of consumed frames, frames at the receiving end need to be buffered while waiting to be consumed (processed). Definitely, we cannot have an unlimited buffer size at the receiving side. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -

Understanding Linux Internetworking
White Paper by David Davis, ActualTech Media Understanding Linux Internetworking In this Paper Introduction Layer 2 vs. Layer 3 Internetworking................ 2 The Internet: the largest internetwork ever created. In fact, the Layer 2 Internetworking on term Internet (with a capital I) is just a shortened version of the Linux Systems ............................................... 3 term internetwork, which means multiple networks connected Bridging ......................................................... 3 together. Most companies create some form of internetwork when they connect their local-area network (LAN) to a wide area Spanning Tree ............................................... 4 network (WAN). For IP packets to be delivered from one Layer 3 Internetworking View on network to another network, IP routing is used — typically in Linux Systems ............................................... 5 conjunction with dynamic routing protocols such as OSPF or BGP. You c an e as i l y use Linux as an internetworking device and Neighbor Table .............................................. 5 connect hosts together on local networks and connect local IP Routing ..................................................... 6 networks together and to the Internet. Virtual LANs (VLANs) ..................................... 7 Here’s what you’ll learn in this paper: Overlay Networks with VXLAN ....................... 9 • The differences between layer 2 and layer 3 internetworking In Summary ................................................. 10 • How to configure IP routing and bridging in Linux Appendix A: The Basics of TCP/IP Addresses ....................................... 11 • How to configure advanced Linux internetworking, such as VLANs, VXLAN, and network packet filtering Appendix B: The OSI Model......................... 12 To create an internetwork, you need to understand layer 2 and layer 3 internetworking, MAC addresses, bridging, routing, ACLs, VLANs, and VXLAN. We’ve got a lot to cover, so let’s get started! Understanding Linux Internetworking 1 Layer 2 vs. -
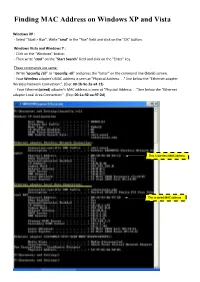
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different.