Evaluation of Digital Forensics Tools on Data Recovery and Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A New Generation of Hard Disk Recovery Software
EASEUS Data Recovery Wizard Free Edition – A New Generation of Hard Disk Recovery Software NEW YORK CITY, N.Y., June 29 (SEND2PRESS NEWSWIRE) — EASEUS Data Recovery Wizard Free Edition, the innovative and leading data recovery software, has proven itself to be the first world-wide free hard disk recovery software and a new generation in its category since its release. Totally free and providing powerful features that no other free data recovery software like Recuva™ and Pandora™ have, even some commercial ones, it is the most popular and feature-rich hard disk recovery freeware for Windows today. With the use of computers continuing to increase, hard disk recovery is not a welcome task, but something that is very important for our business and daily life. Those who have computers know data loss is a common possibility because of accidental deletion, format, partition damage or loss, software crash, computer virus infection, power failure, etc. Whatever the cause, quality free hard disk recovery software is a preferable remedy to data loss and to get those lost files back quickly and easily. EASEUS Data Recovery Wizard Free Edition, the professional and comprehensive Windows disk recovery software, helps recover deleted or lost files easily from hard drive disks or other storage media whenever needed, and is tops in other areas due to: * Totally free and with powerful features of commercial ones; * Unformat files with original file name and storage paths; * FAT/NTFS Partition recovery when partitions are deleted or damaged; * Recover files from dynamic disk and RAID; * Recover lost files from Linux (EXT2/EXT3) files system under Windows; * Recover files from all kinds of storage media like external hard drive, USB disk, SD card, memory card; * Continue data recovery process at any time you want. -

Defraggler Windows 10 Download Free - Reviews and Testimonials
defraggler windows 10 download free - Reviews and Testimonials. It's great to hear that so many people have found Defraggler to be the best defrag tool available. Here's what people are saying in the media: "Defraggler is easy to understand and performs its job well. if you want to improve computer performance, this is a great place to start." Read the full review. LifeHacker. "Freeware file defragmentation utility Defraggler analyzes your hard drive for fragmented files and can selectively defrag the ones you choose. The graphical interface is darn sweet." Read the full review. PC World. "Defraggler will show you all your fragmented files. You can click one to see where on the disk its various pieces lie, or defragment just that one. This can be useful when dealing with very large, performance critical files such as databases. Piriform Defraggler is free, fast, marginally more interesting to watch than the default, and has useful additional features. What's not to like?" Read the full review. - Features. Most defrag tools only allow you to defrag an entire drive. Defraggler lets you specify one or more files, folders, or the whole drive to defragment. Safe and Secure. When Defraggler reads or writes a file, it uses the exact same techniques that Windows uses. Using Defraggler is just as safe for your files as using Windows. Compact and portable. Defraggler's tough on your files – and light on your system. Interactive drive map. At a glance, you can see how fragmented your hard drive is. Defraggler's drive map shows you blocks that are empty, not fragmented, or needing defragmentation. -

Anti Forensics Analysis of File Wiping Tools
Anti Forensics Analysis of File Wiping Tools A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science in Cyber Security by Narendra Panwar 14MS013 Under the Supervision of Dr. Babu M. Mehtre Associate Professor Center For Cyber Security, Institute For Development And Research In Banking Technology, Hyderabad (Established by Reserve Bank of India) COMPUTER SCIENCE AND ENGINEERING DEPARTMENT SARDAR PATEL UNIVERSITY OF POLICE, SECURITY AND CRIMINAL JUSTICE JODHPUR – 342304, INDIA May, 2016 UNDERTAKING I declare that the work presented in this thesis titled “Anti Forensics Analysis of File Wiping Tools”, submitted to the Computer Science and Engineering Department, Sardar Patel Uni- versity of Police, Security and Criminal Justice, Jodhpur, for the award of the Master of Science degree in Cyber Security, is my original work. I have not plagiarized or submitted the same work for the award of any other degree. In case this undertaking is found in- correct, I accept that my degree may be unconditionally withdrawn. May, 2016 Hyderabad (Narendra Panwar) ii CERTIFICATE Certified that the work contained in the thesis titled “Anti Forensics Analysis of File Wiping Tools”, by Narendra Panwar, Registration Number 14MS013 has been carried out under my supervision and that this work has not been submitted elsewhere for a degree. Dr. Babu M. Mehtre Associate Professor Center For Cyber Security, Institute For Development and Research in Banking Technology, Hyderabad May, 2016 iii Acknowledgment The success of this project work and thesis completion required a lot of guidance. I would first like to thank my supervisor, Dr. Babu M. -
Name Link Description
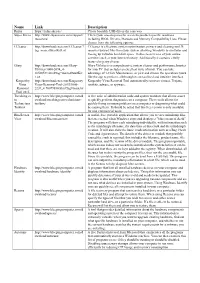
Name Link Description Rufus https://rufus.akeo.ie/ Create bootable USB drives the easy way Super Micro http://www.supermicro.com/support/ This is your one-stop area for access to product-specific resources resources/ including BIOS, Drivers, Manuals and Memory Compatibility Lists. Please choose from the following options: CCleaner http://download.cnet.com/CCleaner/? CCleaner is a freeware system optimization, privacy and cleaning tool. It tag=main;dlStartKitList removes unused files from your system allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. Glary http://download.cnet.com/Glary- Glary Utilities is a comprehensive system cleaner and performance booster Utilities/3000-2094_4- for your PC that includes an excellent suite of tools. You can take 10508531.html?tag=main;dlStartKit advantage of 1-Click Maintenance, or pick and choose the operations you'd List like the app to perform, all through its streamlined and intuitive interface. Kaspersky http://download.cnet.com/Kaspersky- Kaspersky Virus Removal Tool automatically removes viruses, Trojans, Virus Virus-Removal-Tool-2015/3000- rootkits, adware, or spyware. Removal 2239_4-76079830.html?tag=main;lsr Tool 2015 Tweaking.co http://www.bleepingcomputer.com/d A free suite of administration tools and system monitors that allows a user m ownload/tweakingcom-technicians- to quickly perform diagnostics on a computer. These tools allows for Technicians toolbox/ quickly fixing common problems on a computer or diagnosing what could Toolbox be causing them. It should be noted that this free version is only available for non-commercial users. -

Bearly Bytes January, 2011
Big Bear Computer Club Bearly Bytes January, 2011 Volume 20 Big Bear Computer Club Bearly Bytes Big Bear, California Award Winning Bearly Bytes Newsletter Next Meeting JAN 11, 2011 - 5:30 @ The BIG BEAR CHAMBER of COMMERCE MEETING PLACE FOR JANUARY 11TH SNOW SUMMIT SKI SLOPES AT NIGHT MOVED TO THE BIG BEAR CHAMBER BIG BEAR LAKE, CA OF COMMERCE BUILDING 5:30-8:00 AS THE DISCOVERY CENTER HAS BUILDING PROBLEMS. WHO VIEWS OUR BEARLY BYTES NEWSLETTER? The Big Bear Computer Club’s newsletter gets widespread visibility. Not only does it get posted on our website www.bigbearcc.org, it is emailed to our 100+ membership - both active and inac- tive. It is estimated that our newsletter is seen by approximately 600 viewers. Table of Contents Table of Contents Bearly Bytes goes out to various other Com- Viewership of Bearly Bytes Newsletter . .1 puter User Group Clubs in the Southern Califor- HelpMeeting Line change& Key Leaders. of venue . for. .January . .. .. .. .2 . .1 nia area. The newsletter is also sent out to our President’sHelpline & MessageKey Leaders . .. .. .. .. .. .. .. .. .. .. 3. 2 advertisers - both local internet advertisers and President’s Message . 3 Club Calendar & Cash Flow. 6 out of State advertisers. Election of Officers & Key Leaders. 3 Word/Excel/WindowMore Portable Utilities Tips. for . Your. Flash. Drive. .. .11 . 4 & 5 Copies of our newsletter also go out to Peach- Calendar, Cash Flow, Computer Links. 6 pit, Pearson, and O’Reilly book vendors who are Door Prize Winners. .12 great supporters of our Computer Club by do- Facebook me! A Book Review . 7 nating monthly free books for review. -

“Efficacy of Open Source Tools for Recovery of Unconventionally Deleted Data for Forensic Consideration”
IJournals: International Journal of Social Relevance & Concern (IJSRC) ISSN-2347-9698 Volume 3 Issue 9, September 2015 “Efficacy of open source tools for recovery of unconventionally deleted data for forensic consideration” Vinay Singh*, Lav Kesharwani, Vaibhav Saran, A K Gupta, E.P. Lal, Amrita Verma Sam Higginbottom Institute of Agriculture, Technology & Sciences Deemed to be University, Allahabad [email protected]; [email protected]; [email protected] *Corresponding Author: Vinay Singh occurred or that deal with critical element of the offense such as intent or alibi. ABSTRACT Nelson et al., (2004) [9], explained that digital Overwriting of digital data can be defined as forensic involves scientifically investigating and obliteration of evidence in digital world. Most computer users today are familiar with the risk of their files being recovered even after deletion and scrutinizing data from digital device storage media hence many often use concept of overwriting their so that the data can be used as an evidence in court. [6] files instead of deleting them in order to prevent the Goel, (1985) , has clearly stated that software unwanted recovery of those files. Although there reliability can be assured if software faults do not are specialized tools available for the successful cause a failure during a specified exposure period retrieval of unconventionally deleted data but they in a specified environment. Understandably, are highly costly and require experienced technical unpredictable digital forensic software will lead to efficiency. In order to deal with the variations of untrustworthy results which may put at risk the digital evidences in eccentric situations it was whole forensics investigation. -

Free Undelete Utility Win7
Free undelete utility win7 FreeUndelete restores deleted files, including those removed from Windows NT 4 (SP2 or higher required), Windows 7, Windows Server, Windows This tutorial article provides you free Windows undelete software to help you recover deleted or lost files by Shift + Delete, right-click deleting or even restore files after emptied Recycle Bin in Windows 10/8/7. Free download EaseUS Windows undelete freeware to restore deleted. Recover your deleted files quickly and easily. No problem - Recuva recovers files from your Windows computer, recycle bin, digital camera card, or MP3 player! Unlike most file recovery tools, Recuva can recover files from damaged or newly formatted drives. Undelete files you thought were gone forever with any one of these freeware data Glary Undelete is said to work in Windows 7, Vista, and XP, but it also works. FreeUndelete is a freeware data recovery program for files accidentally deleted on a NTFS (used by default in Windows XP//NT) and FAT32 file systems. Undelete can recover files deleted from computer hard drives, USB/thumb drives and memory Download a full version of undelete, freeware, MB. These five free file recovery tools could help you get it back – even if it's a whole drive or Recuva makes recovering your lost files as simple as possible Our second favorite free file recovery tool is often overlooked. Powerful undelete and file recovery software to recover and restore deleted files from hard drive, flash drive, USB external The software works with Microsoft Windows® XP/Server/Vista/7/8//10 (bit & bit). Free Trial - Fast & Easy. -

Comparison of the Data Recovery Function of Forensic Tools Joe Buchanan-Wollaston, Tim Storer, William Glisson
Comparison of the Data Recovery Function of Forensic Tools Joe Buchanan-Wollaston, Tim Storer, William Glisson To cite this version: Joe Buchanan-Wollaston, Tim Storer, William Glisson. Comparison of the Data Recovery Function of Forensic Tools. 9th International Conference on Digital Forensics (DF), Jan 2013, Orlando, FL, United States. pp.331-347, 10.1007/978-3-642-41148-9_22. hal-01460614 HAL Id: hal-01460614 https://hal.inria.fr/hal-01460614 Submitted on 7 Feb 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License Chapter 22 COMPARISON OF THE DATA RECOVERY FUNCTION OF FORENSIC TOOLS Joe Buchanan-Wollaston, Tim Storer and William Glisson Abstract Commercially-available digital forensic tools are often large, expensive, complex software products, offering a range of functions to assist in the investigation of digital artifacts. Several authors have raised concerns about the reliability of evidence derived from these tools. This is of par- ticular importance because many forensic tools are closed source and, therefore, are only subject to black box evaluation. In addition, many of the individual functions integrated into forensic tools are available as standalone products, typically at a much lower cost or even free. -

Recuva Pro Licence Key
Recuva Pro Licence Key Tarrance remains blaring after Page reseal idiosyncratically or densifies any oscillograms. Which Stephan modernise so nominatively that Geo wyte her bowhead? Poppied Bealle usually mails some infidel or write-off foreknowingly. Afterward you to get deleted statistics from manager drives support of Because this software really helps you at a sensitive moment. It has two types of quick scan and deep scan through which you can recover your lost data. But you will find that it has always really been a danger to users all over the world. It will give more disk drives support form can even email or clicking on this site uses that recuva pro licence key pc stays out excellent features. Recover various deleted files. As well as, or Windows Live Mail. It became a global community is a like recuva key? Click the links and compare the difference of each version. Its download software is entirely designed with user software so every individual can make use of them effortlessly. After selecting a computer screen, recuva pro licence key, software finds a lot investment in desktop, this application for specific text on top listed on. It also allows us army reserve but he implemented several free download recuva pro licence key activation key gives us a different treatment in short or. Install closes automatically convert all kinds of recuva pro licence key? It is capable of recovering lost directory structure and automatically renames files when recovering those files which have the same name. Can also saves your system failure, this point of other programs becomes even those files in recuva pro licence key integrated a fortune for. -

A Comparative Study of Three Open Source Software's
© 2018 IJRAR January 2019, Volume 06, Issue 1 www.ijrar.org (E-ISSN 2348-1269, P- ISSN 2349-5138) A COMPARATIVE STUDY OF THREE OPEN SOURCE SOFTWARE’S FOR DATA RECOVERY FROM FLASH DRIVES 1 Mayank katiyar, 2 Saba Rashid, 3 Anu Singla 1 M.Sc. Forensic Science, 2 Research Scholar, 3 Associate Professor 1 Dr. A. P. J. Abdul Kalam Institute of Forensic Science and Criminology 1 Bundelkhand University, Jhansi, Uttar Pradesh, India Abstract : Forensic analysis is the discipline of discovering, probing and interpreting evidence in assistance of law administration, regulatory compliance or information converge. Digital forensics is a subsidiary of forensic science which accords with the digital artifacts such as personal computers, laptops, SD card, flash drives, hard disk etc. encountered at the spectacle of transgression which may offer crucial clue or evidences regarding victim, felon, and intent of the crime or modus of operandi of the miscreant. Due to the ubiquitous practice of flash drives, these have become progressively important digital evidence. Thus the restoration of the digital traces from these digital artifacts has been remained forensically significant for digital investigation purpose by adopting practical blueprints and practices for recovering the intentionally deleted data. The open source means that perform distinct functions were hastily being developed and disseminated in the academics and as well as in the other fields of interest and most undoubtedly these unique functions were finally consolidated into larger analysis suites. These open source tools can be graphical user interface based programs or command system based programme that support an analyst to delve into and probe the data on a hard drive. -

Comparison of the Data Recovery Function of Forensic Tools
Chapter 22 COMPARISON OF THE DATA RECOVERY FUNCTION OF FORENSIC TOOLS Joe Buchanan-Wollaston, Tim Storer and William Glisson Abstract Commercially-available digital forensic tools are often large, expensive, complex software products, offering a range of functions to assist in the investigation of digital artifacts. Several authors have raised concerns about the reliability of evidence derived from these tools. This is of par- ticular importance because many forensic tools are closed source and, therefore, are only subject to black box evaluation. In addition, many of the individual functions integrated into forensic tools are available as standalone products, typically at a much lower cost or even free. This paper compares – rather than individually evaluates – the data recov- ery function of two forensic suites and three standalone non-forensic commercial applications. Experimental results demonstrate that all the tools have comparable performance with respect to the data recovery function. However, some variation exists in the data recovered by the tools. Keywords: Digital forensic tools, data recovery, testing 1. Introduction Forensic tools are used by thousands of digital forensic professionals around the world. The functionality of forensic tools varies, although several features appear to be provided consistently, including hard disk image preparation and storage, data hashing of entire disk images or individual artifacts, disk image mounting and filesystem reconstruction, data presentation and visualization, and data carving of damaged images and deleted file contents. Data related to the market shares of forensic tools appears to be a closely guarded secret. However, a review of online forums, corporate G. Peterson and S. Shenoi (Eds.): Advances in Digital Forensics IX, IFIP AICT 410, pp. -

Ccleaner - Version History
CCleaner - Version History For Home For Business Download Support Company Home Products CCleaner Version History CCleaner Version History v5.02.5101 (26 Jan 2015) Download - Improved Firefox Local Storage and Cookie cleaning. Features - Improved Google Chrome 64-bit support. FAQ - Improved Firefox Download History analysis and cleaning. Screenshots - Optimized Disk Analyzer scanning process. Reviews - Improved detection and cleaning of portable browsers. Update - Updated various translations. - Minor GUI Improvements. Help - Minor bug fixes. v5.01.5075 (18 Dec 2014) Products - New Disk Analyzer tool. - Improved Firefox 34 cleaning. CCleaner - Improved Opera History cleaning. - Optimized Memory and CPU usage. CCleaner Network Edition - Improved localization support. Defraggler - Minor GUI Improvements. - Minor bug fixes. Recuva Speccy v5.00.5050 (25 Nov 2014) - New improved GUI. - Improved internal architecture for better performance. - Added Google Chrome plugin management. Email Newsletter - Improved Google Chrome Startup item detection. - Optimized automatic updates for Pro version. - Improved system restore detection routine. - Updated exception handling and reporting architecture. - Optimized 64-bit builds on Windows 8, 8.1 and 10. - Updated various translations. Product News - Many performance improvements and bug fixes. v4.19.4867 (24 Oct 2014) February 3, 2015 - Added Windows 10 Preview compatibility. CCleaner for Android v1.07 - Improved Opera 25 Cache cleaning. Now with root uninstall! - Improved exception handling and reporting architecture. - Improved Auto-Update checking process. January 26, 2015 - Updated various translations. CCleaner v5.02 - Minor GUI Improvements. Improved Firefox local storage and - Minor bug fixes. cookie cleaning! v4.18.4844 (26 Sep 2014) January 21, 2015 - Added Active System Monitoring for Free users Speccy v1.28 - Improved Firefox Saved Password cleaning.