Comparison of the Data Recovery Function of Forensic Tools
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A New Generation of Hard Disk Recovery Software
EASEUS Data Recovery Wizard Free Edition – A New Generation of Hard Disk Recovery Software NEW YORK CITY, N.Y., June 29 (SEND2PRESS NEWSWIRE) — EASEUS Data Recovery Wizard Free Edition, the innovative and leading data recovery software, has proven itself to be the first world-wide free hard disk recovery software and a new generation in its category since its release. Totally free and providing powerful features that no other free data recovery software like Recuva™ and Pandora™ have, even some commercial ones, it is the most popular and feature-rich hard disk recovery freeware for Windows today. With the use of computers continuing to increase, hard disk recovery is not a welcome task, but something that is very important for our business and daily life. Those who have computers know data loss is a common possibility because of accidental deletion, format, partition damage or loss, software crash, computer virus infection, power failure, etc. Whatever the cause, quality free hard disk recovery software is a preferable remedy to data loss and to get those lost files back quickly and easily. EASEUS Data Recovery Wizard Free Edition, the professional and comprehensive Windows disk recovery software, helps recover deleted or lost files easily from hard drive disks or other storage media whenever needed, and is tops in other areas due to: * Totally free and with powerful features of commercial ones; * Unformat files with original file name and storage paths; * FAT/NTFS Partition recovery when partitions are deleted or damaged; * Recover files from dynamic disk and RAID; * Recover lost files from Linux (EXT2/EXT3) files system under Windows; * Recover files from all kinds of storage media like external hard drive, USB disk, SD card, memory card; * Continue data recovery process at any time you want. -

Guidelines on Mobile Device Forensics
NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Sam Brothers Wayne Jansen http://dx.doi.org/10.6028/NIST.SP.800-101r1 NIST Special Publication 800-101 Revision 1 Guidelines on Mobile Device Forensics Rick Ayers Software and Systems Division Information Technology Laboratory Sam Brothers U.S. Customs and Border Protection Department of Homeland Security Springfield, VA Wayne Jansen Booz Allen Hamilton McLean, VA http://dx.doi.org/10.6028/NIST.SP. 800-101r1 May 2014 U.S. Department of Commerce Penny Pritzker, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Under Secretary of Commerce for Standards and Technology and Director Authority This publication has been developed by NIST in accordance with its statutory responsibilities under the Federal Information Security Management Act of 2002 (FISMA), 44 U.S.C. § 3541 et seq., Public Law (P.L.) 107-347. NIST is responsible for developing information security standards and guidelines, including minimum requirements for Federal information systems, but such standards and guidelines shall not apply to national security systems without the express approval of appropriate Federal officials exercising policy authority over such systems. This guideline is consistent with the requirements of the Office of Management and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in Circular A- 130, Appendix IV: Analysis of Key Sections. Supplemental information is provided in Circular A- 130, Appendix III, Security of Federal Automated Information Resources. Nothing in this publication should be taken to contradict the standards and guidelines made mandatory and binding on Federal agencies by the Secretary of Commerce under statutory authority. -

A Usability Analysis of the Autopsy Forensic Browser
Proceedings of the Second International Symposium on Human Aspects of Information Security & Assurance (HAISA 2008) A Usability Analysis of the Autopsy Forensic Browser D.J. Bennett and P. Stephens Department of Computing (Academic), Canterbury Christ Church University, Canterbury, United Kingdom e-mail: {david.bennett, paul.stephens}@canterbury.ac.uk Abstract This paper reviews the usability of the Autopsy Forensic Browser. Two expert-based usability review techniques are used: Cognitive Walkthrough and Heuristic Evaluation. The results of the evaluation indicate that there are many areas where usability could be improved and these are classified into areas of eight overlapping areas. Examples from each area are presented, with suggestions as to methods to alleviate them. The paper concludes with a future work proposal to effect the changes suggested and retest the current and the replacement system with a user-based evaluation. Keywords Usability, Human-Computer Interaction, Interface Design, Autopsy Forensic Browser, The Sleuth Kit, Cognitive Walkthrough, Heuristic Evaluation 1. Introduction This paper reviews the usability of the Autopsy Forensic Browser tool. The reasoning for this is to improve future versions of the tool. In many ways forensic analysis tools are no different to any other mission critical software in terms of the need for usability. However, failure in usability in such tools could lead to outcomes which deny liberty to innocent persons, or enable criminals to continue with criminal activity should an investigation fail in some way. 1.1. Forensics and the Autopsy Forensic Browser Gottschalk et al. (2005) define computer forensics as the identification, preservation, investigation, and documentation of computer systems data used in criminal activity. -

Defraggler Windows 10 Download Free - Reviews and Testimonials
defraggler windows 10 download free - Reviews and Testimonials. It's great to hear that so many people have found Defraggler to be the best defrag tool available. Here's what people are saying in the media: "Defraggler is easy to understand and performs its job well. if you want to improve computer performance, this is a great place to start." Read the full review. LifeHacker. "Freeware file defragmentation utility Defraggler analyzes your hard drive for fragmented files and can selectively defrag the ones you choose. The graphical interface is darn sweet." Read the full review. PC World. "Defraggler will show you all your fragmented files. You can click one to see where on the disk its various pieces lie, or defragment just that one. This can be useful when dealing with very large, performance critical files such as databases. Piriform Defraggler is free, fast, marginally more interesting to watch than the default, and has useful additional features. What's not to like?" Read the full review. - Features. Most defrag tools only allow you to defrag an entire drive. Defraggler lets you specify one or more files, folders, or the whole drive to defragment. Safe and Secure. When Defraggler reads or writes a file, it uses the exact same techniques that Windows uses. Using Defraggler is just as safe for your files as using Windows. Compact and portable. Defraggler's tough on your files – and light on your system. Interactive drive map. At a glance, you can see how fragmented your hard drive is. Defraggler's drive map shows you blocks that are empty, not fragmented, or needing defragmentation. -

Forensic Toolkit (FTK)
Forensic Toolkit (FTK) User Guide | 1 AccessData Legal and Contact Information Document date: January 31, 2018 Legal Information ©2018 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. AccessData Group, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Group, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, AccessData Group, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Group, Inc. reserves the right to make changes to any and all parts of AccessData software, at any time, without any obligation to notify any person or entity of such changes. You may not export or re-export this product in violation of any applicable laws or regulations including, without limitation, U.S. export regulations or the laws of the country in which you reside. AccessData Group, Inc. 588 West 400 South Suite 350 Lindon, UT 84042 USA AccessData Trademarks and Copyright Information The following are either registered trademarks or trademarks of AccessData Group, Inc. All other trademarks are the property of their respective owners. AccessData® AD Summation® Mobile Phone Examiner Plus® AccessData Certified Examiner® (ACE®) Discovery Cracker® MPE+ Velocitor™ AD AccessData™ Distributed Network Attack® Password Recovery Toolkit® AD eDiscovery® DNA® PRTK® AD RTK™ Forensic Toolkit® (FTK®) Registry Viewer® LawDrop® Summation® | 2 A trademark symbol (®, ™, etc.) denotes an AccessData Group, Inc. -
Comparative Evaluation of Mobile Forensic Tools
See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/322250449 Comparative Evaluation of Mobile Forensic Tools Chapter in Advances in Intelligent Systems and Computing · January 2018 DOI: 10.1007/978-3-319-73450-7_11 CITATIONS READS 0 486 6 authors, including: John Alhassan Sanjay Misra Federal University of Technology Minna Covenant University Ota Ogun State, Nigeria 40 PUBLICATIONS 16 CITATIONS 302 PUBLICATIONS 1,059 CITATIONS SEE PROFILE SEE PROFILE Adewole Adewumi Rytis Maskeliunas Covenant University Ota Ogun State, Nigeria Kaunas University of Technology 51 PUBLICATIONS 46 CITATIONS 94 PUBLICATIONS 164 CITATIONS SEE PROFILE SEE PROFILE Some of the authors of this publication are also working on these related projects: Learning from Failure: Evaluation of Agent Dyads in the Context of Adversarial Classification Game View project Biohashing based on Boolean logic operations View project All content following this page was uploaded by Rytis Maskeliunas on 08 January 2018. Provided by Covenant University Repository The user has requested enhancement of the downloaded file. CORE Metadata, citation and similar papers at core.ac.uk Comparative Evaluation of Mobile Forensic Tools J. K. Alhassan1(&), R. T. Oguntoye1, Sanjay Misra2, Adewole Adewumi2, Rytis Maskeliūnas3, and Robertas Damaševičius3 1 Federal University of Technology, Minna, Nigeria [email protected] 2 Covenant University, Otta, Nigeria [email protected] 3 Kaunas University of Technology, Kaunas, Lithuania [email protected] Abstract. The rapid rise in the technology today has brought to limelight mobile devices which are now being used as a tool to commit crime. Therefore, proper steps need to be ensured for Confidentiality, Integrity, Authenticity and legal acquisition of any form of digital evidence from the mobile devices. -

AD-Ediscovery-Product-Review-From
eDiscovery Full eDiscovery Suite Empowering Excellence from Data Collection to Analysis for Endpoint & Remote Data Collection, Forensic Imaging, Document Review, and Much More AD eDiscovery is Company Name Brand challenges for over 30 years. For example, AccessData Group, Inc. one of the more difficult tasks is collecting a single, integrated data from remote computers which has Product Name Brand(s) become even more prevalent in the platform for preservation, AD eDiscovery work-from-home environments we find litigation holds, collection, AD Enterprise ourselves these days. Fortunately, Forensic Toolkit (FTK) AccessData stands out as one of the few data processing, and Quin-C companies that offers tools and platforms AD QBlaze that allow customers to successfully assessment, along with Summation retrieve and process electronically stored legal review and information from anywhere. Latest Developments and Updates production.” • Collect from Microsoft Office 365, Teams, The Comprehensive eDiscovery Mimecast email management, and Family from AccessData Proofpoint cybersecurity. AccessData is a comprehensive provider of • Speed data collection and analysis with computer forensics and litigation support automated tasks. technologies and boasts a broad spectrum • Remotely collect data from Apple macOS of stand-alone and enterprise-grade Catalina and Mojave operating systems. software platforms. • The new AD QBlaze platform simplifies processing and review in an easy-to- One of their flagship products, AD access SaaS model. eDiscovery, supports an end-to-end discovery process across the entire There are many uncertainties one Electronic Discovery Reference Model encounters when attempting to be (EDRM). A single SQL database serves all proficient at eDiscovery processes and components and supports seamless, procedures but there is a company that connected workflows in a forensically has aptly and consistently addressed those sound environment. -

FTK in Action
The Forensic Process Examined: Creating cases for classroom use Yvonne LeClaire Lewis University MSIS 68-595 Table of Contents Introduction ................................................................................................................................................. 4 Digital Evidence ........................................................................................................................................... 5 Computers.................................................................................................................................................. 5 Storage Devices ......................................................................................................................................... 5 Handheld Devices ...................................................................................................................................... 6 Peripheral Devices ..................................................................................................................................... 6 Network Devices ....................................................................................................................................... 7 Miscellaneous Possible Sources ................................................................................................................ 7 Determining the Course of Action ............................................................................................................. 7 Uses for Digital Evidence ........................................................................................................................... -

Performance of Android Forensics Data Recovery Tools
This is author accepted copy; for final version please refer to: B.C. Ogazi-Onyemaechi, Ali Dehghantanha, Kim-Kwang Raymond Choo, “Performance of Android Forensics Data Recovery Tools”, Pages 91-110, Chapter 7, (Elsevier) Contemporary Digital Forensic Investigations Of Cloud And Mobile Applications Performance of Android Forensics Data Recovery Tools Bernard Chukwuemeka Ogazi-Onyemaechi1, Ali Dehghantanha1; Kim-Kwang Raymond Choo2 1School of Computing, Science and Engineering, University of Salford, Manchester, United Kingdom 2 Information Assurance Research Group, University of South Australia, Australia [email protected]; [email protected]; [email protected] Abstract- Recovering deleted or hidden data is among most important duties of forensics investigators. Extensive utilisation of smartphones as subject, objects or tools of crime made them an important part of residual forensics. This chapter investigates the effectiveness of mobile forensic data recovery tools in recovering evidences from a Samsung Galaxy S2 i9100 Android phone. We seek to determine the amount of data that could be recovered using Phone image carver, Access data FTK, Foremost, Diskdigger, and Recover My File forensic tools. The findings reflected the difference between recovery capacities of studied tools showing their suitability in their specialised contexts only. Keywords: Data recovery, digital forensics, deleted file recovery, mobile forensics, Android forensics. 1 1.0 INTRODUCTION Smart mobile devices, particularly smartphones, are increasingly popular in today’s Internet-connected society (1–4). For example, few years ago in 2010, shipments of smartphone grew by 74 percent to 295 million units (3,4). Unsurprisingly, sales of smartphones have been increasing since then (5,6), and it has been estimated that 1.5 billion smartphones will be sold by 2017 and 1 billion mobile subscribers by 2022 (7–15). -

A User-Oriented Network Forensic Analyser
A USER-ORIENTED NETWORK FORENSIC ANALYSER 1 1 1,2 1,2 D. Joy , F. Li , N.L. Clarke and S.M. Furnell 1Centre for Security, Communications and Network Research (CSCAN) Plymouth University, Plymouth, United Kingdom 2Security Research Institute, Edith Cowan University, Western Australia [email protected] Abstract Network forensics is becoming an increasingly important tool in the investigation of cyber and computer- assisted crimes. Unfortunately, whilst much effort has been undertaken in developing computer forensic file system analysers (e.g. Encase and FTK), such focus has not been given to Network Forensic Analyser Tools (NFATs). The single biggest barrier to effective NFATs is the handling of large volumes of low-level traffic and being able to exact and interpret forensic artefacts and their context – for example, being able extract and render application-level objects (such as emails, web pages and documents) from the low-level TCP/IP traffic but also understand how these applications/artefacts are being used. Whilst some studies and tools are beginning to achieve object extraction, results to date are limited to basic objects. No research has focused upon analysing network traffic to understand the nature of its use – not simply looking at the fact a person requested a webpage, but how long they spend on the application and what interactions did they have with whilst using the service (e.g. posting an image, or engaging in an instant message chat). This additional layer of information can provide an investigator with a far more rich and complete understanding of a suspect’s activities. To this end, this paper presents an investigation into the ability to derive high-level application usage characteristics from low-level network traffic meta-data. -

Anti Forensics Analysis of File Wiping Tools
Anti Forensics Analysis of File Wiping Tools A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Science in Cyber Security by Narendra Panwar 14MS013 Under the Supervision of Dr. Babu M. Mehtre Associate Professor Center For Cyber Security, Institute For Development And Research In Banking Technology, Hyderabad (Established by Reserve Bank of India) COMPUTER SCIENCE AND ENGINEERING DEPARTMENT SARDAR PATEL UNIVERSITY OF POLICE, SECURITY AND CRIMINAL JUSTICE JODHPUR – 342304, INDIA May, 2016 UNDERTAKING I declare that the work presented in this thesis titled “Anti Forensics Analysis of File Wiping Tools”, submitted to the Computer Science and Engineering Department, Sardar Patel Uni- versity of Police, Security and Criminal Justice, Jodhpur, for the award of the Master of Science degree in Cyber Security, is my original work. I have not plagiarized or submitted the same work for the award of any other degree. In case this undertaking is found in- correct, I accept that my degree may be unconditionally withdrawn. May, 2016 Hyderabad (Narendra Panwar) ii CERTIFICATE Certified that the work contained in the thesis titled “Anti Forensics Analysis of File Wiping Tools”, by Narendra Panwar, Registration Number 14MS013 has been carried out under my supervision and that this work has not been submitted elsewhere for a degree. Dr. Babu M. Mehtre Associate Professor Center For Cyber Security, Institute For Development and Research in Banking Technology, Hyderabad May, 2016 iii Acknowledgment The success of this project work and thesis completion required a lot of guidance. I would first like to thank my supervisor, Dr. Babu M. -
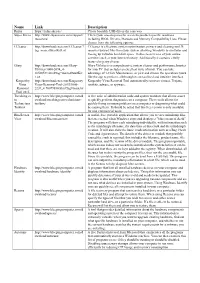
Name Link Description
Name Link Description Rufus https://rufus.akeo.ie/ Create bootable USB drives the easy way Super Micro http://www.supermicro.com/support/ This is your one-stop area for access to product-specific resources resources/ including BIOS, Drivers, Manuals and Memory Compatibility Lists. Please choose from the following options: CCleaner http://download.cnet.com/CCleaner/? CCleaner is a freeware system optimization, privacy and cleaning tool. It tag=main;dlStartKitList removes unused files from your system allowing Windows to run faster and freeing up valuable hard disk space. It also cleans traces of your online activities such as your Internet history. Additionally it contains a fully featured registry cleaner. Glary http://download.cnet.com/Glary- Glary Utilities is a comprehensive system cleaner and performance booster Utilities/3000-2094_4- for your PC that includes an excellent suite of tools. You can take 10508531.html?tag=main;dlStartKit advantage of 1-Click Maintenance, or pick and choose the operations you'd List like the app to perform, all through its streamlined and intuitive interface. Kaspersky http://download.cnet.com/Kaspersky- Kaspersky Virus Removal Tool automatically removes viruses, Trojans, Virus Virus-Removal-Tool-2015/3000- rootkits, adware, or spyware. Removal 2239_4-76079830.html?tag=main;lsr Tool 2015 Tweaking.co http://www.bleepingcomputer.com/d A free suite of administration tools and system monitors that allows a user m ownload/tweakingcom-technicians- to quickly perform diagnostics on a computer. These tools allows for Technicians toolbox/ quickly fixing common problems on a computer or diagnosing what could Toolbox be causing them. It should be noted that this free version is only available for non-commercial users.