Near-Field Identification of UHF Rfids with Wifi!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Why Can't I Use Bluetooth to Transfer Files to Another Device? Applicable Products: Problem: 1
Why can't I use Bluetooth to transfer files to another device? Applicable products: Problem: 1. The user is unable to send files using Bluetooth. 2. The user is unable to receive files using Bluetooth. Solution: 1. The distance between your phone and the other Bluetooth device may have exceeded the maximum operational range of Bluetooth devices (10 meters). In this case, move your phone closer to the Bluetooth device, and try again. 2. The other Bluetooth device may not have responded to your file transfer request in time. You can try sending the request again and then remind the other party to confirm the transfer more quickly. 3. Your phone is not paired with the Bluetooth device. In this case, first make sure that Bluetooth is enabled on both devices, and that both devices are visible to nearby Bluetooth devices (for laptops, check that the file receiving screen is displayed). Then send the file. 4. Pair the two devices first, and then send the file. 5. Check whether the other Bluetooth device supports the file format you are trying to send. 6. If the other Bluetooth device supports the given file format, try sending the file again. Note: 1. iPhones can be paired with Huawei phones using Bluetooth, but do not support file transfer. 2. The music app preinstalled in your Huawei phone does not support Bluetooth sharing. Therefore, you cannot share music downloaded within the app with other Bluetooth devices. Open the Files app, touch Local > Internal storage > Music, find the name of the song you want to share, and touch to share it with other Bluetooth devices. -

A Critical Review on Huawei's Trusted Execution Environment
Unearthing the TrustedCore: A Critical Review on Huawei’s Trusted Execution Environment Marcel Busch, Johannes Westphal, and Tilo Müller Friedrich-Alexander-University Erlangen-Nürnberg, Germany {marcel.busch, johannes.westphal, tilo.mueller}@fau.de Abstract to error. In theory, any bug in the feature-rich domain, includ- ing severe kernel-level bugs, cannot affect the integrity and Trusted Execution Environments (TEEs) are an essential confidentiality of a TEE, as TEEs are isolated from the rest building block in the security architecture of modern mo- of the system by means of hardware primitives. As ARM is bile devices. In this paper, we review a TEE implementa- the predominant architecture used for chipsets in mobile de- tion, called TrustedCore (TC), that has been used on Huawei vices, the ARM TrustZone (TZ)[6] provides the trust anchor phones for several years. We unveil multiple severe design for virtually all TEEs in mobile devices, including Huawei and implementation flaws in the software stack of this TEE, models. which affect devices including the popular Huawei P9 Lite, Although TEEs have been extensively used by millions released in 2016, and partially the more recent Huawei P20 of products for years, security analyses targeting these sys- Lite, released in 2018. First, we reverse-engineer TC’s com- tems are rarely discussed in public since all major vendors, ponents, their interconnections, and their integration with the including Huawei, Qualcomm, and Samsung, maintain strict Android system, focusing on security aspects. Second, we ex- secrecy about their individual proprietary implementations. amine the Trusted Application (TA) loader of the TC platform However, the correct implementation of a TEE is complex and reveal multiple design flaws. -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -
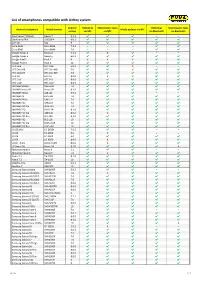
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔ -

Smartphone Camera Modules Comparison 2020 Vol 3: Focus on Huawei
REVERSE COSTING® – STRUCTURAL, PROCESS & COST REPORT P9 P10 P20 Pro Mate 20 Pro P30 Pro Mate 30 Pro P40 Pro Smartphone Camera Modules Comparison 2020 Vol. 3 Focus on Huawei SP20525 - IMAGING report by Audrey LAHRACH Physical Analysis by Véronique LE TROADEC & Guillaume CHEVALIER December 2020 – Sample 22 bd Benoni Goullin 44200 NANTES - FRANCE +33 2 40 18 09 16 [email protected] www.systemplus.fr ©2020 by System Plus Consulting | SP20525 – Smartphone Camera Module Comparison 2020 Vol 3: Focus on Huawei | Sample 1 Table of Contents Cost Comparison 96 Overview / Introduction 5 o CIS Die Cost Comparison o Executive Summary o Reverse Costing Methodology o Front Facing o Glossary o Rear Facing Company Profile & Supply Chain 9 o Total CIS Die Price o Huawei, Sony, Omnivision o CM Cost Comparison o Players & Market Forecast Physical Comparison 19 o Front Facing o Camera Module Overview o Rear Facing o Summary of the Physical Analysis o Total CM Price o Huawei P40 Pro Detailed Physical Analysis 122 o Huawei P30 Pro ➢ P Series o Huawei P20 Pro o P40 Pro ✓ Front & Rear Camera o Huawei P10 o P30 Pro o Huawei P9 ✓ Front & Rear Camera o Mate 30 Pro o P20 Pro o Mate 20 Pro ✓ Front & Rear Camera Physical Evolution 55 o P10 o Display Evolution ✓ Front & Rear Camera o Huawei Front Camera Evolution P Series o P9 o Huawei Rear Camera Evolution P Series ✓ Front & Rear Camera o Huawei Front Camera Evolution/Comparison Mate vs P Series ➢ Mate Series o Huawei Rear Camera Evolution/Comparison Mate vs P Series o Mate 30 Pro o Camera Module Description ✓ Front & Rear Camera o Bonding & Stacking evolution (Sony & Omnivision) o Mate 20 Pro ✓ Front & Rear Camera Feedbacks 240 SystemPlus Consulting services 242 ©2020 by System Plus Consulting | SP20525 – Smartphone Camera Module Comparison 2020 Vol 3: Focus on Huawei | Sample 2 Executive Summary Overview / Introduction o Executive Summary o Reverse Costing Huawei is among the top 3 smartphone OEMs today. -

Mobile- H2 2018
Barometer of mobile Internet connections in Turkey Publication of August 12 th , 2019 H2 2018 – H1 2019 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 Summary table and nPerf score, all technologies combined .............................................. 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 6 2.5 Latency 2G/3G/4G ................................................................................................................ 7 2.6 Browsing test 2G/3G/4G....................................................................................................... 8 2.7 Streaming test 2G/3G/4G .................................................................................................... -

Māori Language Interfaces
10 Māori language resources & Māori initiatives for teaching & learning te reo Māori Māori language interfaces Te Taka Keegan Introduction The decisions around the language of a software interface lie with the software engineer and their development team. The decisions are, or should be, based primarily on the likely target audience and how they will most easily be able to use the interface. That is to say, language decisions should be based on the usability of the interface. If this was applied for all cases it is unlikely that we would see interfaces in te reo Māori From a computational perspective the language of an interface does not need to be in English, it can just as easily be programmed to display in Spanish, in French, in Māori or any other of the 1000 languages that are covered by the Unicode scripts. Ultimately the computer itself does not think, or compute, in a spoken language; all of its operations are undertaken in machine code based on the binary number system, which is then compiled onto various layers of assembly and high level programming languages which ultimately display human language messages in text boxes. What is displayed in those text boxes is quite arbitrary to running the computer, but it is everything to the usability of the interface, and subsequently, the usefulness of the software. This paper considers the usability of the interface and the ramifications for te reo Māori if the interface language, the messages displayed in those text boxes, is written in te reo Māori. An initial question that may arise is 'Why would we want to create software that has an interface in te reo Māori?' Studies have shown (see examples in this paper) that interfaces are more difficult to use in te reo Māori. -

Initiation INDUSTRY N M INDU STRY ME E
Initiation Company Report Consumer E INDUSTRY NM INDUSTRYME NM INDUSTRY How to make the impossible mission possible? February 26, 2019 Two roads diverge in the triathlon track Research Team Tianli Wen ● Xiaomi today as a regional and marketing innovator faces an uphill battle against Head of Research Huawei, a global and technology innovator. Yet Xiaomi’s user base, Internet root and brand loyalty are its key strength. As Internet-Of-Things (IOT) taking root, the Tris X. Gong battle ground will shift to Xiaomi’s favour; ● We suggest Xiaomi to focus on two areas to enhance its valuation: (1) developing +852 21856112 Internet content, (2) spending on R&D. Both require a healthy cash flow, which [email protected] makes margin and profitability improvement imperative; ● Given Xiaomi’s near-term challenges as a global company, we rate the stock a HOLD with a TP of HK$14.55. Xiaomi’s brand, Mi, stands for Mission Impossible. See the last page of the report for important disclosures Blue Lotus Capital Advisors Limited 1 China|Asia ●Initiation Consumer ● Electronics Xiaomi Inc. (HK: 1810) Making the impossible mission possible BUY HOLD SELL ● We initiate Xiaomi with a HOLD rating and TP of HK$14.55 because we Target Price: HK$ 14.55 Current Price: HK$ 12.20 Initiation believe Xiaomi still need to hone its skills as either a technology champion RIC: (HK:1810) BBG: 1810 HK Market cap (HK$ mn) 291,500 like Huawei, or a platform+content powerhouse like Tencent, or both; Average daily volume (HK$ mn) 678 ● Xiaomi’s near-term challenge is to achieve greater profitability so that it can Shares out/float (mn) 17,204/4,360 Source: Bloomberg, Blue Lotus (as of Feb 26, 2019) further build up Internet services and play in the technology top league; ● Global expansion and content are opportunities. -

Qualcomm 3D Sonic Sensor Fingerprint
REVERSE COSTING® – STRUCTURE, PROCESS & COST REPORT Qualcomm 3D Sonic Sensor Fingerprint The second generation of biometric ultrasonic fingerprint authentication, found in the Samsung Galaxy S10 and S10 plus. Back in 2016, LeEco, a former smartphone some mask layers. Also, the Qualcomm design company in China, was the first to Biometric Integrated Circuit (QBIC) has integrate an ultrasonic sensor as a evolved in terms of circuit and power biometric fingerprint authentication handling, integrating more high voltage device. This first integration was under a circuits and more on-chip memory. metal cover at the back of the screen. But This complete analysis of the Ultrasonic the most interesting feature of such a Fingerprint Module includes analyses of sensor is its possible integration under the the sensor die and the Application Specific display without any additional compo- Integration Circuits (ASICs), along with a nents. With the integration in the latest cost analysis and price estimation for the Galaxy S10 series from Samsung, module. It also includes a physical and Qualcomm has proven that the biometric technical comparison with the previous ultrasonic fingerprint under display is now version of the sensor in the LeEco LeMax ready for very high volume production Pro and with the Synaptics’ FS9500 optical and could compete with capacitive or fingerprint sensor. Finally, a cost optical sensors. comparison is included with the Synaptics Either with the Exynos or the Qualcomm sensor. Chipset, the Samsung Galaxy S10 series is the first to feature the Ultrasonic Fingerprint Sensor directly under its COMPLETE TEARDOWN WITH display. The sensor is located on the front of the device directly glued onto the • Detailed photos Title: Qualcomm 3D organic light emitting diode (OLED) • Precise measurements Sonic Sensor material. -
Huawei P10 Quick Start Guide
Quick Start Guide Your device at a glance Thank you for choosing a HUAWEI P10 smartphone. Before you start, let's take a look at your new device. • To power on your device, press and hold the power button until your device vibrates and the screen turns on. • To power off your device, press and hold the power button, and then touch . To force your device to restart, press and hold the power button until your device vibrates. Secondary microphone Dual-lens camera Dual-tone Earpiece flash Optical proximity Laser sensor sensor Front camera Status indicator Card slot Ambient light Volume sensor button Power button Headset jack Primary fingerprint microphone scanner Speaker USB-C port Do not remove your device's pre-fitted screen protector, which guards against scratches and abrasion. 1 Inserting and removing cards Follow the instructions in the following figures to set up your device. NJDSP4% VTR-L09 NJDSP4% 0S VTR-L29 • Do not insert or remove the card tray when your device is powered on. • Ensure that the card is correctly aligned and that the card tray is level when you insert it into your device. Be careful not to scratch your device or hurt yourself when using the SIM eject pin. Store the SIM eject pin out of the reach of children to prevent accidental swallowing or injury. DoCaution not use cut or modified micro-SIM or microSD cards with your device as these may not be recognized and could damage the card tray. 2 Dual card dual standby single pass This description should only be used in conjunction with the VTR-L29. -

The Rise of Security Assistants Over Security Audit Services Yury Chemerkin Multi-Skilled Security Expert Advanced Monitoring Yury Chemerkin
THE RISE OF SECURITY ASSISTANTS OVER SECURITY AUDIT SERVICES YURY CHEMERKIN MULTI-SKILLED SECURITY EXPERT ADVANCED MONITORING YURY CHEMERKIN I have ten years of experience in information security. I‘m a multi-skilled security expert on security & compliance and mainly focused on privacy and leakage showdown. Key activity fields are EMM and Mobile &, Cloud Computing, IAM, Forensics & Compliance. I published many papers on mobile and cloud security, regularly appears at conferences such as CyberCrimeForum, HackerHalted, DefCamp, NullCon, OWASP, CONFidence, Hacktivity, Hackfest, DeepSec Intelligence, HackMiami, NotaCon, BalcCon, Intelligence-Sec, InfoSec NetSysAdmins, etc. LINKEDIN: HTTPS://WWW.LINKEDIN.COM/IN/YURYCHEMERKIN TWITTER: @YURYCHEMERKIN EMAIL: [email protected] MOBILE PROTECTION & ISSUES 1. Data 2. App 3. OS 4. Device 5. Network 6. Compliance MOBILE PROTECTION & ISSUES 1. Data 2. App 3. OS 4. Device 5. Network 6. Compliance UNDERSTANDING DATA PROTECTION Different apps contain the same data values (same passwords, passport data, so on…) Some apps provides a worse protection level than other to protect particular data item If you use the same data (values), the worst app is your max protection level equals the minimum (worst) Valuable data is not only credentials, location, passport and bank data Valuable data is main data of app, like pics of Instagram, chats of Viber UNDERSTANDING DATA PROTECTION OVER DIFFERENT APPS. NETWORK DATA ITEMS Travel Data, Location Data, User Profile Data Uber Taxi, No Protection Yandex Meridian, Taxi Cris Taxi SSL Pinning Bucuresti, Taxi apps (RU) UNDERSTANDING DATA PROTECTION OVER DIFFERENT APPS. NETWORK DATA ITEMS Any data MITM with crafted cert (trust British to root certs) Airways, and Android Anywayanyday, Sberbank SSL Pinning Delta, Aeroflot, and iOS Sberbank ‘British Airways for iOS & Android’ have all data SSL Pinned, except booking data that MITMed with preinstalled/crafted CERT MOBILE PROTECTION & ISSUES 1. -

FAQ Aircraft
FAQ Aircraft How do I control Tello? You can control Tello directly via Tello app or with a supported Bluetooth remote controller connected to the Tello app. Supported devices iOS: Requires iOS 9.0 or later. Compatible with iPhone 5s, iPhone SE, iPhone 6, iPhone 6 Plus, iPhone 6s, iPhone 6s Plus, iPhone 7, iPhone 7 Plus, iPhone 8, iPhone 8 Plus, iPhone X, iPad mini 4 and iPad mini 4 Wi-Fi + Cellular. Android: Android version 4.4.0 or later. Compatible with Samsung S7, Samsung S6 edge, Samsung S5, Samsung Galaxy note 4, Samsung Galaxy note 3, Huawei Honor 8, Huawei Honor 9, Huawei P8 Max, Huawei P10, Huawei Honor V8, Huawei P9, Huawei nova2, Xiaomi 6, Xiaomi Note3, Redmi 4A, OnePlus5, vivoX6, Google Pixel1 XL, Google Pixel2. *Support for additional devices available as testing and development continues. For the latest information, please refer to the official Tello website. *Not available for Android tablets. What kind of interesting things can Tello do during flight? Tello can perform eight different flips, fly up and down from your hand in Bounce mode, or automatically record short videos with EZ Shots. Can Tello fly indoors? Yes, Tello is safe to fly indoors. Tello can also fly outdoors, but it is only recommended to do so in windless conditions. Is Tello waterproof? No. Camera What does Tello's camera feature? Tello's camera is capable of capturing photos and recording videos. With EZ Shots, users can fly in three specific patterns while recording short videos. Where are my captured photos and video saved? How can I export them? Photos and video will save to your smartphone.