Quantum Bidding in Bridge
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Slam Bidding Lesson
Slam Bidding and Modified Scroll Bids By Neil H. Timm In this Bridge Bit, I explore more fully Slam bidding techniques, some old and some perhaps new. To reach a small slam, the partnership should have roughly thirty-three Bergen points. In addition to a trump fit and count, slams require controls (aces, kings, voids, and singletons). The more controls between the partners, the easier the slam. To evaluate whether or not the partnership has the required controls, one uses cuebids with perhaps the 5NT trump ask bid (Grand Slam Force), and Blackwood Conventions. Blackwood Conventions reveal how many aces and kings, while cuebidding or control showing bids reveal where they reside. To make a slam, one usually requires first-round control in three suits and second round control in the fourth suit. It is possible to make a slam missing two aces, provided the missing ace is opposite a void, and the second missing ace is replaced by or is opposite a second-round control (a king or a singleton). When looking for a possible slam, one often asks the following questions. 1. What cards should my partner have to be able to make a slam? 2. How may I obtain the required information? 3. Are there any bidding techniques or conventions that I can use to obtain the required information? 4. If my partner does not have the required cards for a slam, can I stop short of slam, and if not is the risk of going down worth it? We shall review techniques to help the partnership find the required information for making a slam! However, with some hands one needs only to count points to reach a slam. -

The Eclectic Club
The Eclectic Club Contents Part One The Structure of the Opening Bids Page 3 Part Two Responder’s First Bid 4 The Opening Bid of 1D 4 The Opening Bid of 1H 4 The Opening Bid of 1S 5 The Opening Bid of 1NT 5 Responding in a Minor 7 1NT is Doubled 7 The Rebid of 1NT 8 The Opening Bid of 2C 9 The Opening Bid of 2D 10 The Opening Bid of 2H/2S 11 The Opening Bid of 2NT 14 Part Three Splinters 14 Slam Splinters 14 The Residual Point Count 15 The Gap Between 16 1S 3H 17 Part Four Transfers and Relays 17 Let the Weak Hand Choose Trumps 17 The Competitive Zone 17 Bidding a Passed Hand 18 Transfers in Response to 1H and 1S 18 Transfer Response to 2C 20 The 5-3 Major Fit 21 The Cost of Transfers 21 Responder Makes Two Bids 22 Responder has Hearts 24 The Transfer to Partner’s Suit 25 The Shape Ask 27 Part Five The Control Ask 28 Florentine Blackwood 28 Blackwood with a Minor Suit Agreed 30 Part Six Strong Hands 31 The Opening Bid of 1C 31 Strong Balanced Hands 32 Strong Unbalanced Hands 32 Strong Two Suiters 32 The Golden Negatives 33 Special Positives 33 Opponents Bid over Our 1C 34 R.H.O Bids 35 Our Defence to Their 1C 36 Part Seven More Bidding Techniques 36 Canape in the Majors 36 Sputnik with a One Club System 37 Appendix The Variable Forcing Pass 39 A voyage of Discovery 39 Our Version of V.F.P. -

FOUR ACES Could Have Done More Safely
Number: 214 October 2020 BRIDGEJulian Pottage’s Double Dummy Problem UR ACE FO S ♠ 3 2 ♥ A 3 2 ♦ Q ♣ A Q 6 5 4 3 2 ♠ K Q J 10 9 ♠ 8 7 ♥ N ♥ K Q J 10 W E 9 8 7 ♦ 10 S ♦ K J 9 8 7 6 5 ♣ J 10 9 ♣ K ♠ A 6 5 4 ♥ 6 5 4 ♦ A 4 3 2 ♣ 8 7 Contract 3NT by South Lead: ♠K BRIDGE is ceasing publication. The last issueThe will answer be will benumber published on page 216 4 next - month.December 2020. See page 5 for more information. A Sally Brock Looks At Your Slam Bidding Sally’s Slam Clinic Where did we go wrong? Slam of the month Another regular contributor to these Playing standard Acol, South would This month’s hand was sent in by pages, Alex Mathers, sent in the open 2♣, but whatever system was Roger Harris who played it with his following deal which he bid with played it is likely that he would then partner Alan Patel at the Stratford- his partner playing their version of rebid 2NT showing 23-24 points. It is upon-Avon online bridge club. Benjaminised Acol: normal to play the same system after 2♣/2♦ – negative – 2NT as over an opening 2NT, so I was surprised North Dealer South. Game All. Dealer West. Game All. did not use Stayman. In my view the ♠ A 9 4 ♠ J 9 8 correct Acol sequence is: ♥ K 7 6 ♥ A J 10 6 ♦ 2 ♦ K J 7 2 West North East South ♣ A 9 7 6 4 2 ♣ 8 6 Pass Pass Pass 2♣ ♠ Q 10 8 6 3 ♠ J 7 N ♠ Q 4 3 ♠ 10 7 5 2 Pass 2♦ Pass 2NT ♥ Q 9 ♥ 10 8 5 4 2 W E ♥ 7 4 3 N ♥ 9 8 5 2 Pass 3♣ Pass 3♦ ♦ Q J 10 9 5 ♦ K 8 7 3 S W E ♦ 8 5 4 ♦ Q 9 3 Pass 6NT All Pass ♣ 8 ♣ Q 5 S ♣ Q 10 9 4 ♣ J 5 Once South has shown 23 HCP or so, ♠ K 5 2 ♠ A K 6 North knows the values are there for ♥ A J 3 ♥ K Q slam. -

A Case to CRO About?
A Case to CRO about? Sitting West you hold: and your partner opens 1NT (15-17). You transfer your partner into hearts then bid 2S. Partner now bids 3H showing 3 x hearts and lower point range. You have at least a 6-3 heart fit with a relatively strong hand opposite and you feel that a slam is possible. What do you do bid next? If you use simple Gerber or Blackwood to ask for Aces and Kings, partner tells you that she has two of each. If you use Key Card to ask for controls (the controls are the 4 Aces and the K of trumps), partner tells you that she has two Aces without the QH and two Kings. Do you bid the heart slam? Thoughts: Standard Ace asking bids like Gerber and Blackwood are not that helpful when you have a void since they will not tell you which Aces and Kings partner holds. If, on this board, partner holds the AC and KC opposite your void the slam is unlikely to make. Advanced players can get around this problem by control cue bidding prior to Ace asking. There are augmented versions of Blackwood and Key Card asking which will identify voids but they don’t apply to the situation where the Ace asker has a void herself as in the situation here. If you are missing two Aces which is quite common in Ace asking enquiries, there is a bidding system that can help. It is called CRO and is most effectively used as a 4C asking bid in order to keep the bidding level lower for signoff if slam looks unlikely. -

Polish Standard 2000 ('WJ 2000')
Polish Standard 2000 ('WJ 2000') by Krzysztof Jassem Ó 2000 Translated into English by Daniel J. Neill, June 2003. Distributed with the author's express permission. Publisher: Jarek Zalewski Semata Sp. z o.o. 53-659 Wroclaw ul. Sikorskiego 28/32 tel. (071) 373 55 80, 373 58 81 fax (071) 3735 55 79 Technical editor: Maciek Wreczycki Cover concept: Ula Gardy Reproduction and preparation for press: Semata Sp. z o.o. 53-659 Wroclaw ul. Sikorskiego 28/32 tel. (071) 373 55 80, 373 58 81 fax (071) 3735 55 79 Press: Drukarnia i Oficyna Wydawnicza FORUM 52-016 Wroclaw ul. Rybnicka 2 ISBN 83-914291-1-3 1 PDF byl vytvořen zkušební verzí FinePrint pdfFactory http://www.fineprint.cz Table of Contents TABLE OF CONTENTS ............................................................................................................................. 2 INTRODUCTION ........................................................................................................................................ 4 DEFINITIONS OF SEVERAL BRIDGE TERMS.................................................................................... 4 CHAPTER 1 - "POLISH STANDARD 2000" BASICS............................................................................ 9 THE UNCONTESTED AUCTION ..................................................................................................................... 9 1§ Opening ............................................................................................................................................ 9 1¨ Opening ......................................................................................................................................... -

Four Card Majors: Western Natural Updated
Foreword It is easy to dismiss Marvin French as a crank or a curmudgeon or as the contrarian that he certainly was but this does not do justice to the man’s life. Marvin was Life Master 10231 achieving the rank in 1956, “when it was hard” as he liked to say. This was not a boast, just a fact not well understood by many who started playing later, particularly after the great masterpoint inflation that kicked off shortly into the new millennium. Marvin was a force on the west coast bridge scene. Local San Diego Diamond LM, Anne Terry, never one to withhold an opinion positive or negative, called Marvin the “best of the best.” D22 Director, Ken Monzingo said, “Like him or not, he was a unique man. A leader, not a follower. A brilliant man of honesty and integrity.” Marvin made significant contributions to bridge literature and less known contributions to bidding theory. He was a contributor to Bridge World, Popular Bridge (published in the 1960s and 1970s), and the D22 Contract Bridge Forum, and editor for the latter prior to Joel Hoersch. For many years Marvin maintained his own website where he posted his writings on bridge, blackjack, and literature. His 90 page Squeeze Refresher (For Good Players) is undoubtedly the best reference that is available for free. Sometime in 2011 I got to know Marvin better because we started exchanging e-mail on various bridge topics in part because I had been reading his website and had taken some interest in his discussion of four card vs. -

Minor Suit Openings
Minor Suit Openings Opening the Bidding Suppose you have a good enough hand to open the bidding. Opening bids of 1NT and 1 of a major are very descriptive and give us a good start in the auction, so if you can open 1NT or 1 of a major, you should certainly do that. If you do not have a balanced hand with 15-17 HCP, and you do not have a 5-card major, then you will have to open 1 of a minor. (Sometimes it is correct to open above the 1 level, but these bids have not been covered in class yet, so I will ignore them for now. Also, there is one situation in which you can open 1 of a minor despite having a 5 card major; if you have a longer minor { i.e. 5 spades and 6 diamonds { then you should start with the minor.) But in short, with an opening hand, you should open 1 of a minor if and only if 1NT and 1 of a major are not options. How do you know whether to open 1| or 1}? When we were discussing major suit openings, this was an easy decision: opening 1 of a major promises 5 cards in that major, and you probably don't have two 5 card majors. (If you do have two 5 card majors, you should open 1♠ . As a general rule, whenever you have two 5 card suits, you bid the higher ranking one first. This will allow you to safely bid the lower-ranking suit twice. -

Evolving a Bridge Bidding System Jason R. Woolever
Evolving a Bridge Bidding System by Jason R. Woolever B.S., Massachusetts Institute of Technology (2000) Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Master of Engineering in Electrical Engineering and Computer Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY June 2001 @2001 Jason R. Woolever. All rights reserved. The author hereby grants to M.I.T. permission to reproduce and distribute publicly paper and electronic copies of this thesis BARKER and to grant others the right to do so. MASSOCFT HNOLOGYS JUL 11 2001 LIBRARIES Author ....... ............................ ....... Department of Electrical Engineering and Computer Science May 25, 2001 Certified by ..................................... ,M d .ill Una-May, GReilly Research Scientist ThesisSuyervisor Accepted by........................................ ........... Arthur C. Smith Chairman, Department Committee on Graduate Students 2 3 Evolving a Bridge Bidding System by Jason R. Woolever Submitted to the Department of Electrical Engineering and Computer Science on May 25, 2001, in partial fulfillment of the requirements for the degree of Master of Engineering in Electrical Engineering and Computer Science Abstract In this thesis, I designed and implemented WEBB, a computer program that produces Bridge bidding systems. WEBB uses a genetic algorithm which leverages expert Bridge knowledge to search the space of Bridge bidding systems. One way in which WEBB differs from other (computerized) Bridge programs is that it learns a bidding system rather than, typically, using a statistically-based search of bidding and card play options or using a naive, pre-scripted convention/system. To learn better and better systems, WEBB uses a co-evolutionary approach. -

An Opening Bid of 1NT That Shows a Balanced Hand in the Range of 10-12, 11-14, 12-14, Or 13-15 HCP's (Or Thereabouts) Is Considered a Weak Notrump
Try Something Different....Weak NoTrumps Perhaps? (Part I) An opening bid of 1NT that shows a balanced hand in the range of 10-12, 11-14, 12-14, or 13-15 HCP's (or thereabouts) is considered a Weak Notrump. Generally in the United States and Canada a standard 1NT opening bid shows a balanced hand with a point range of 15 to 17 or 16 to 18 HCP's; thus the term Weak Notrump for a similar hand with fewer values. I am convinced that one of the best ways to learn how to play against weak notrumps is to play them for awhile. Once you get used to them, they aren’t so very difficult to defend or to bid against. Besides playing them is FUN! Jeremy Flint, the late great British bridge player and writer stated, in defense of weak notrumps (they are considered standard in Great Britain): "American writers, nurtured on their standard strong notrumps tend to inform their readers that the weak notrump creates many problems. So it does--for the opposition!" Having played weak notrumps for years I wholeheartedly agree with that assessment. Weak notrumps seem to have several advantages over the strong notrumps: (1) With one bid (the opening bid), the opener gets to show a minimum balanced hand. There is no problem with which "right" suit to open and there is no rebid problem. (2) Because hands that would normally be opened with a 15-17 NT are now opened with one of a minor suit, there is the advantage of permitting the responding hand to bid on poor hands thus enabling the partnership to find a good suit fit that would otherwise have been missed. -

Bernard Magee's Acol Bidding Quiz
Number: 181 UK £3.95 Europe €5.00 January 2018 Bernard Magee’s Acol Bidding Quiz This month we are dealing with hands that have fewer than six points. You are West in the auctions below, BRIDGEplaying ‘Standard Acol’ with a weak no-trump (12-14 points) and four-card majors. 1. Dealer East. Love All. 4. Dealer East. Love All. 7. Dealer East. Game All. 10. Dealer East. Love All. ♠ A 4 3 2 ♠ 9 8 6 ♠ Q 8 7 6 ♠ 8 6 5 ♥ J 7 6 N ♥ 4 2 N ♥ Q J 3 2 N ♥ 7 N ♦ 9 7 6 5 3 W E ♦ 10 9 8 7 6 W E ♦ 4 2 W E ♦ J 7 6 3 2 W E ♣ 2 S ♣ K 4 3 S ♣ 7 6 5 S ♣ 9 8 7 4 S West North East South West North East South West North East South West North East South 1♣ Pass 1♥ 1♠ 2NT Pass 2♣ Pass ? Pass 2♠ Dbl Pass ? 2♦ Pass 2♥ Pass ? ? 2. Dealer East. Love All. 5. Dealer North. Love All. 8. Dealer North. Love All. 11. Dealer East. Love All. ♠ J 4 3 2 ♠ 5 3 2 ♠ 4 3 ♠ Q 7 3 2 ♥ 4 2 N ♥ 4 3 2 N ♥ A 7 6 N ♥ 4 N ♦ A 9 7 3 W E ♦ J 8 7 6 5 W E ♦ 9 8 4 3 W E ♦ K 9 3 2 W E ♣ 6 5 4 S ♣ 4 2 S ♣ 9 7 6 5 S ♣ 9 8 7 4 S West North East South West North East South West North East South West North East South 1♣ Pass 1♥ 1♠ 3♥ 3♣ Dbl Pass 2♣ Pass ? Pass Pass Dbl Pass ? 2♦ Pass 2♠ Pass ? ? 3. -

THE "CHESTER CLUB" BIDDING SYSTEM OUTLINE of The
THE "CHESTER CLUB" BIDDING SYSTEM THE "NOTTINGHAM CLUB" SYSTEM AS DEVELOPED AT THE DEVA BRIDGE CLUB, CHESTER. The Nottingham Club bidding system, developed at the Nottingham Bridge Club, was first published by Marjorie Burns in 1954. It was probably the first British strong 1♣ system and was adopted in a fairly big way by members of the Deva Bridge Club in the late 1950's. At one stage nearly 50% of the club members, including most of the "better" players, were playing "Nottingham". However, in practice, although its basic principle of the strong opening 1♣ with a negative response of 1♦ was found to be a very effective base on which to build an auction, the second and third rebids and responses were not very well systemised and left much room for improvement. To make the system more playable, it has been modified over the years by various Deva club players notably Eric Figgis, David and Barbara Figgis, Dorothy Grunert, Wilf Fearn, Eric and Dorothy Dutton,Frank Dean, and more recently by Jim Stambridge and myself. The earlier modifications were generally added piecemeal as a need was recognised. The latest modifications, some suggested by various Deva players,some borrowed from the Blue Club and some fairly novel, have been incorporated to produce what is now an integrated system whose bids relate logically to one another and often have more extensive and closely defined meanings than hitherto. Sadly, most of the players are no longer with us, and only a small handful of players are left at the Deva who play this system, which, for over 40 years they described as "Nottingham", but which, in fact, bore little resemblance to the original "Nottingham Club". -
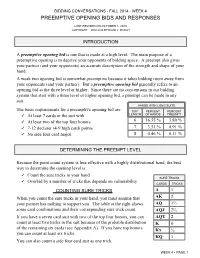
Preemptive Opening Bids and Responses Last Revised on October 1, 2014 Copyright 2010-2014 by David L
BIDDING CONVERSATIONS - FALL 2014 - WEEK 4 PREEMPTIVE OPENING BIDS AND RESPONSES LAST REVISED ON OCTOBER 1, 2014 COPYRIGHT 2010-2014 BY DAVID L. MARCH INTRODUCTION A preemptive opening bid is one that is made at a high level. The main purpose of a preemptive opening is to deprive your opponents of bidding space. A preempt also gives your partner (and your opponents) an accurate description of the strength and shape of your hand. A weak two opening bid is somewhat preemptive because it takes bidding room away from your opponents (and your partner). But a preemptive opening bid generally refers to an opening bid at the three level or higher. Since there are no conventions in our bidding system that start with a three level or higher opening bid, a preempt can be made in any suit. HANDS WITH LONG SUITS The basic requirements for a preemptive opening bid are: SUIT PERCENT PERCENT ✓ At least 7 cards in the suit with LENGTH OF HANDS PREEMPT ✓ At least two of the top four honors 6 16.55 % 3.80 % ✓ 7-12 declarer (4-9 high card) points 7 3.51 % 0.91 % ✓ No side four card major 8 0.46 % 0.11 % DETERMINING THE PREEMPT LEVEL Because the point count system is less effective with a highly distributional hand, the best way to determine the opening level is: ✓ Count the sure tricks in your hand SURE TRICKS ✓ Overbid by a number of tricks that depends on vulnerability CARDS TRICKS COUNTING SURE TRICKS A 1 When you count the sure tricks in your hand, you must assume that AK 2 your partner has nothing to support you.