University of Piraeus – Department of Informatics Master Program in «Informatics»
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Openvms: an Introduction
The Operating System Handbook or, Fake Your Way Through Minis and Mainframes by Bob DuCharme VMS Table of Contents Chapter 7 OpenVMS: An Introduction.............................................................................. 7.1 History..........................................................................................................................2 7.1.1 Today........................................................................................................................3 7.1.1.1 Popular VMS Software..........................................................................................4 7.1.2 VMS, DCL................................................................................................................4 Chapter 8 Getting Started with OpenVMS........................................................................ 8.1 Starting Up...................................................................................................................7 8.1.1 Finishing Your VMS Session...................................................................................7 8.1.1.1 Reconnecting..........................................................................................................7 8.1.2 Entering Commands..................................................................................................8 8.1.2.1 Retrieving Previous Commands............................................................................9 8.1.2.2 Aborting Screen Output.........................................................................................9 -

MS-DOS Basics.Pdf
MS-DOS Basics The Command Prompt When you first turn on your computer, you will see some cryptic information flash by. MS-DOS displays this information to let you know how it is configuring your computer. You can ignore it for now. When the information stops scrolling past, you'll see the following: C:\> This is called the command prompt or DOS prompt. The flashing underscore next to the command prompt is called the cursor. The cursor shows where the command you type will appear. Type the following command at the command prompt: ver The following message appears on your screen: MS-DOS version 6.22 Viewing the Contents of a Directory To view the contents of a directory 1. Type the following at the command prompt: dir A list similar to the following appears: Changing Directories To change from the root directory to the WINDOWS directory To change directories, you will use the cd command. The cd command stands for "change directory." 1. Type the following at the command prompt: cd windows The command prompt changes. It should now look like the following: C:\WINDOWS> Next, you will use the dir command to view a list of the files in the DOS directory. Viewing the Contents of WINDOWS Directory To view a list of the files in the WINDOWS directory 1. Type the following at the command prompt: dir Changing Back to the Root Directory To change to the root directory 1. Type the following at the command prompt: cd \ Note that the slash you type in this command is a backslash (\), not a forward slash (/). -

MS-DOS Lecture
MS-DOS 2017 University of Babylon College of Engineering Electrical Department Learning Basics of MS-DOS Assis. Lec. Abeer Abd Alhameed | 1 MS-DOS 2017 Outcomes: By the end of this lecture, students are able to: Define the MS-DOS system Log in MS-DOS commands system Display MS-DOS information on your computer Type basic commands of MS-DOS system (view directory contents, change directory, make directory) Assis. Lec. Abeer Abd Alhameed | 2 MS-DOS 2017 Learning of MS-DOS Basics: Definition - What does Microsoft Disk Operating System (MS- DOS) mean? The Microsoft Disk Operating System (MS-DOS) is an operating system developed for PCs (personal computers) with x86 microprocessors. It was the first widely-installed operating system in personal computers. It is a command-line-based system, where all commands are entered in text form and there is no graphical user interface. The Command Prompt: When you first turn on your computer, you will see some information flash by. MS-DOS displays this information to let you know how it is configuring your computer. You can ignore it for now. When the information stops scrolling past, you'll see the following: C:\> This is called the command prompt or DOS prompt. The flashing underscore next to the command prompt is called the cursor. The cursor shows where the command you type will appear. Typing a Command: This section explains how to type a command at the command prompt and demonstrates the "Bad command or file name" message. • To type a command at the command prompt 1. Type the following at the command prompt (you can type the command in either uppercase or lowercase letters): nul If you make a typing mistake, press the BACKSPACE key to erase the mistake, and then try again. -

CS 103 Lab 1 - Linux and Virtual Machines
CS 103 Lab 1 - Linux and Virtual Machines 1 Introduction In this lab you will login to your Linux VM and write your first C/C++ program, compile it, and then execute it. 2 What you will learn In this lab you will learn the basic commands and navigation of Linux/Unix, its file system, the GNU C/C++ compiler and a few basic applications such as Gedit. Important: The Linux operating system and environment shares a vast majority of commands and methods with Unix. 3 Background Information and Notes 3.1 Software to Install on your PC Start by following the course virtual machine installation instructions found at the link below. http://cs103.usc.edu/tools-and-links/installing-course-vm/ Below is a list of recommended software you should install that will be helpful over multiple courses in CS and EE. These tools allow you to access remote servers, run GUI apps on those servers, and transfer files between your PC and those servers. For Windows: FileZilla FTP – Available from : https://software.usc.edu/index.aspx XWin-32 – Available from : https://software.usc.edu/index.aspx PuTTY – Available from : https://software.usc.edu/index.aspx For Mac: X Server: http://developer.apple.com/opensource/tools/runningx11.html Fetch FTP – Available from : https://software.usc.edu/index.aspx Reference: http://www.usc.edu/its/unix/ Last Revised: 8/29/2014 1 CS 103 Lab 1 - Linux and Virtual Machines 3.2 Getting Started with Unix1 and Accessing your Account Solaris vs. Unix vs. Linux UNIX was developed by AT&T Bell Labs in 1969. -

How to Load Vista Or Windows 7 Onto a Bootable Thumb Drive
STAR Watch Statewide Technology Assistance Resources Project A publication of the Western New York Law Center,Inc. Volume 15 Issue 5 Sept-Oct 2011 How to Load Vista or Windows 7 onto a Bootable Thumb Drive Ever since the capacity of USB thumb more robust. What happens when a drives rose into the multi-gigabyte range, DVD gets scratched? computer geeks have been trying to use them to create bootable devices that • Some of the latest computers don’t could be used in an emergency to boot have DVD drives, but they do have a up a failed computer. It was a wonderful USB port. idea, except for one detail: The driver • It takes less time to re-install needed to read the Windows install files Windows from a thumb drive could not be accessed. With the release of Vista and Windows 7 operating Find yourself a suitable thumb drive. It systems, the drivers needed to read the might be possible to shoehorn the files have been made more accessible. It Windows software onto a 4GB thumb is now possible to create a bootable drive, but that would leave no room for thumb drive that can be used to boot up anything else (It might be nice to have a computer and install Windows. copies of the install programs for things like printer drivers or other software that So, what is the big deal? Isn’t a DVD good enough? For many people, a DVD is quite adequate. Just store it in a safe In this issue… place and pull it out when it is needed. -

Linux File System and Linux Commands
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity with the Linux file system, file permissions, and a base set of Linux commands. In this activity, you will study how the Linux file system is organized and practice utilizing common Linux commands. Objectives • Describe the purpose of the /bin, /sbin, /etc, /var/log, /home, /proc, /root, /dev, /tmp, and /lib directories. • Describe the purpose of the /etc/shadow and /etc/passwd files. • Utilize a common set of Linux commands including ls, cat, and find. • Understand and manipulate file permissions, including rwx, binary and octal formats. • Change the group and owner of a file. Materials • Windows computer with access to an account with administrative rights The Air Force Cyber College thanks the Advanced Cyber Engineering program at the Air Force Research Laboratory in Rome, NY, for providing the information to assist in educating the general Air Force on the technical aspects of cyberspace. • VirtualBox • Ubuntu OS .iso File Assumptions • The provided instructions were tested on an Ubuntu 15.10 image running on a Windows 8 physical machine. Instructions may vary for other OS. • The student has administrative access to their system and possesses the right to install programs. • The student’s computer has Internet access. 2. Directories / The / directory or root directory is the mother of all Linux directories, containing all of the other directories and files. From a terminal users can type cd/ to move to the root directory. -

Jailbreak Ios 12.1.1 As a Case Study
OPEN ACCESS Ind. Journal on Computing ISSN 2460-9056 Vol. 4, Issue. 2, Sept 2019. pp. 205-218 socj.telkomuniversity.ac.id/indojc doi:10.21108/indojc.2019.4.2.349 Digital Forensic Analysis on iDevice: Jailbreak iOS 12.1.1 as a Case Study Amin Aenurahman Ali 1, Niken Dwi Wahyu Cahyani 2, Erwid Musthofa Jadied 3 1,2,3 Informatics, School of Computing, Telkom University Jl. Telekomunikasi No. 1 Terusan Buah Batu, Bandung, Indonesia 1 [email protected] 2 [email protected] 3 [email protected] Abstract Jailbreak has an issue in data alteration, as it modifies file(s) in the device to allow user to extract more data than without jailbreaking. This issue raises controversy of the use of jailbreaking in digital forensic investigation, as data integrity is a prominent requirement in a court proceeding. This study aims to analyze the process of jailbreak, what is actually done by the jailbreak code in a device, and what data is actually modified by the jailbreak code. By using the latest version of iOS system, this study uses the voucher_swap exploit as a representation of semi-tethered jailbreaking method to investigate the effects of jailbreak on data integrity on a idevice. The investigation is conducted based on to what extent data can be extracted from the jailbreak device, hash value comparison of the data, and source code analysis to scrutinize the effect of jailbreak to the system and user data inside the device. Results of this study suggest that jailbreak is acceptable to prepare idevice in digital forensic investigations to acquire more data, as it maintains the integrity of user data. -

Apple File System Reference
Apple File System Reference Developer Contents About Apple File System 7 General-Purpose Types 9 paddr_t .................................................. 9 prange_t ................................................. 9 uuid_t ................................................... 9 Objects 10 obj_phys_t ................................................ 10 Supporting Data Types ........................................... 11 Object Identifier Constants ......................................... 12 Object Type Masks ............................................. 13 Object Types ................................................ 14 Object Type Flags .............................................. 20 EFI Jumpstart 22 Booting from an Apple File System Partition ................................. 22 nx_efi_jumpstart_t ........................................... 24 Partition UUIDs ............................................... 25 Container 26 Mounting an Apple File System Partition ................................... 26 nx_superblock_t ............................................. 27 Container Flags ............................................... 36 Optional Container Feature Flags ...................................... 37 Read-Only Compatible Container Feature Flags ............................... 38 Incompatible Container Feature Flags .................................... 38 Block and Container Sizes .......................................... 39 nx_counter_id_t ............................................. 39 checkpoint_mapping_t ........................................ -

File Systems
File Systems CS 4410 Operating Systems [R. Agarwal, L. Alvisi, A. Bracy, M. George, E. Sirer, R. Van Renesse] The abstraction stack I/O systems are accessed Application through a series of layered Library abstractions File System File System API Block Cache& Performance Block Device Interface Device DriverDevice Access Memory-mapped I/O, DMA, Interrupts Physical Device The Block Cache Application Library • a cache for the disk File System File System API • caches recently read blocks Block Cache& Performance • buffers recently written blocks • serves as synchronization point Block Device Interface (ensures a block is only fetched Device DriverDevice Access once) Memory-mapped I/O, DMA, Interrupts Physical Device More Layers (not a 4410 focus) • allows data to be read or Application written in fixed-sized blocks Library • uniform interface to disparate devices File System File System API • translate between OS Block Cache& Performance abstractions and hw-specific Block Device Interface details of I/O devices Device DriverDevice Access • Control registers, bulk data Memory-mapped I/O, transfer, OS notifications DMA, Interrupts Physical Device Where shall we store our data? Process Memory? (why is this a bad idea?) 5 File Systems 101 Long-term Information Storage Needs • large amounts of information • information must survive processes • need concurrent access by multiple processes Solution: the File System Abstraction • Presents applications w/ persistent, named data • Two main components: • Files • Directories 6 The File Abstraction • File: a named collection of data • has two parts • data – what a user or application puts in it - array of untyped bytes • metadata – information added and managed by the OS - size, owner, security info, modification time 7 First things first: Name the File! 1. -
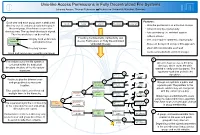
Unix-Like Access Permissions in Fully Decentralized File Systems Johanna Amann, Thomas Fuhrmann Technische Universität München, Germany
Unix-like Access Permissions in Fully Decentralized File Systems Johanna Amann, Thomas Fuhrmann Technische Universität München, Germany 1 Each user and each group owns a dedicated Features: / (root) home amann Documents poster.pdf directory tree. It contains all data belonging to - Unix-like permissions on untrusted storage the user/group. A hash-tree secures the - enforced only by cryptography directory tree. The top-level directory is signed. - fork consistency i.e. resistent against Thus the whole tree can be verified. rollback attacks Providing Confidentiality, Authenticity, and 28876FF... Integrity hash of directory - fast, only requires symmetric cryptography superuser and subdirectories Access Permissions on Fully Decentralized Version: 10 Untrusted Storage - ACLs can be layered on top of this approach, Directory version albeit with considerable overhead - works on block/chunk oriented storage Hash and version are signed by user/group 2 5 The visible root of the file system is All users have access to the keys contained within the dedicated directory, which stores the data directory structure of the file-system needed to verify user signatures. The superuser. superuser hash tree protects the 2 837561A... 1B05524... signatures. 3 / home Redirects glue the different user- 6 and group directory structures 28876FF... 1 Groups are split into a public and B55A142... 7B3220A... superuser together. home amann a private part. The pointers to the Version: 10 private subdirectory are encrypted Files and directories are referenced FAD2452... with the current group key. 7A35209... 5 B70462F... A22A182... 3 multiple times in the hierarchy. amann .users amann Documents Version: 5 Group keys are distributed to users using the subset difference algorithm. -

Joseph Migga Kizza Fourth Edition
Computer Communications and Networks Joseph Migga Kizza Guide to Computer Network Security Fourth Edition Computer Communications and Networks Series editor A.J. Sammes Centre for Forensic Computing Cranfield University, Shrivenham Campus Swindon, UK The Computer Communications and Networks series is a range of textbooks, monographs and handbooks. It sets out to provide students, researchers, and nonspecialists alike with a sure grounding in current knowledge, together with comprehensible access to the latest developments in computer communications and networking. Emphasis is placed on clear and explanatory styles that support a tutorial approach, so that even the most complex of topics is presented in a lucid and intelligible manner. More information about this series at http://www.springer.com/series/4198 Joseph Migga Kizza Guide to Computer Network Security Fourth Edition Joseph Migga Kizza University of Tennessee Chattanooga, TN, USA ISSN 1617-7975 ISSN 2197-8433 (electronic) Computer Communications and Networks ISBN 978-3-319-55605-5 ISBN 978-3-319-55606-2 (eBook) DOI 10.1007/978-3-319-55606-2 Library of Congress Control Number: 2017939601 # Springer-Verlag London 2009, 2013, 2015 # Springer International Publishing AG 2017 This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. -

Kobold: Evaluating Decentralized Access Control for Remote NSXPC Methods on Ios
Kobold: Evaluating Decentralized Access Control for Remote NSXPC Methods on iOS Luke Deshotels Costin Carabas, Jordan Beichler North Carolina State University, University POLITEHNICA of Bucharest North Carolina State University Samsung Research America [email protected] [email protected] [email protected] Razvan˘ Deaconescu William Enck University POLITEHNICA of Bucharest North Carolina State University [email protected] [email protected] Abstract—Apple uses several access control mechanisms to posed to other applications. However, several features (e.g., prevent third party applications from directly accessing secu- dynamic dispatching for method calls) make data flow rity sensitive resources, including sandboxing and file access analysis less practical for iOS binaries. To the best of our control. However, third party applications may also indirectly access these resources using inter-process communication (IPC) knowledge, there exists no systematic enumeration of iOS with system daemons. If these daemons fail to properly enforce remote methods accessible to third party applications. The access control on IPC, confused deputy vulnerabilities may closest related work is existing IPC fuzzers for iOS [2], result. Identifying such vulnerabilities begins with an enumer- [22], [30] that probe for code flaws such as type confusion ation of all IPC services accessible to third party applications. or dereferencing vulnerabilities, which can be exploited However, the IPC interfaces and their corresponding access control policies are unknown and must be reverse engineered at to obtain arbitrary code execution. However, these fuzzers a large scale. In this paper, we present the Kobold framework do not attempt to enumerate remote methods or identify to study NSXPC-based system services using a combination confused deputy vulnerabilities.