Debug Register Rootkits a Study of Malicious Use of the IA-32 Debug Registers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

6.4.0-0 Release of SIMP, Which Is Compatible with Centos and Red Hat Enterprise Linux (RHEL)
SIMP Documentation THE SIMP TEAM Sep 16, 2020 Contents 1 Level of Knowledge 3 1.1 Quick Start................................................4 1.2 Changelogs................................................4 1.3 SIMP Getting Started Guide....................................... 64 1.4 SIMP User Guide............................................ 81 1.5 Contributing to SIMP.......................................... 228 1.6 SIMP Security Concepts......................................... 263 1.7 SIMP Security Control Mapping..................................... 282 1.8 Vulnerability Supplement........................................ 642 1.9 Help................................................... 644 1.10 License.................................................. 652 1.11 Contact.................................................. 652 1.12 Glossary of Terms............................................ 652 Index 669 i ii SIMP Documentation This is the documentation for the 6.4.0-0 release of SIMP, which is compatible with CentOS and Red Hat Enterprise Linux (RHEL). This guide will walk a user through the process of installing and managing a SIMP system. It also provides a mapping of security features to security requirements, which can be used to document a system’s security conformance. Warning: Be EXTREMELY CAREFUL when performing copy/paste operations from this document! Different web browsers and operating systems may substitute incompatible quotes and/or line endings in your files. The System Integrity Management Platform (SIMP) is an Open Source -

Securing Debian Manual
Securing Debian Manual Javier Fernández-Sanguino Peña <[email protected]> ‘Authors’ on this page Version: 3.13, Sun, 30 Jan 2011 19:58:16 +0000 Abstract This document describes security in the Debian project and in the Debian operating system. Starting with the process of securing and hardening the default Debian GNU/Linux distribu- tion installation, it also covers some of the common tasks to set up a secure network environ- ment using Debian GNU/Linux, gives additional information on the security tools available and talks about how security is enforced in Debian by the security and audit team. Copyright Notice Copyright © 2002-2007 Javier Fernández-Sanguino Peña Copyright © 2001 Alexander Reelsen, Javier Fernández-Sanguino Peña Copyright © 2000 Alexander Reelsen Some sections are copyright © their respective authors, for details please refer to ‘Credits and thanks!’ on page 28. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU General Public License, Version 2 (http://www.gnu.org/licenses/ old-licenses/gpl-2.0.html) or any later version (http://www.gnu.org/copyleft/ gpl.html) published by the Free Software Foundation. It is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY. Permission is granted to make and distribute verbatim copies of this document provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this document under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. -

Nelson Murilo
#! /bin/sh # -*- Shell-script -*- # $Id: chkrootkit, v 0.44 2004/09/01 CHKROOTKIT_VERSION='0.44' # Authors: Nelson Murilo <nelson@pa ngeia.com.br> (main author) and # Klaus Steding-Jessen <[email protected]> # # (C)1997-2004 Nelson Murilo, Pangeia Informatica, AMS Foun dation and others. # All rights reserved ### workaround for some Bourne shell implementations unalias login > /dev/null 2>&1 unalias ls > /dev/null 2>&1 unalias netstat > /dev/null 2>&1 unalias ps > /dev/null 2>&1 unalias dirname > /dev/null 2>&1 # Native commands TROJAN="amd basename biff chfn chsh cron date du dirname echo egrep env find \ fingerd gpm grep hdparm su ifconfig inetd inetdconf identd init killall \ ldsopreload login ls lsof mail mingetty netstat named passwd pidof pop2 pop3 \ ps pstree rpcinfo rlogind rshd slogin sendmail sshd syslogd tar tcpd \ tcpdump top telnetd timed traceroute vdir w write" # Tools TOOLS="aliens asp bindshell lkm r exedcs sniffer w55808 wted scalper slapper z2" # Return Codes INFECTED=0 NOT_INFECTED=1 NOT_TESTED=2 NOT_FOUND=3 INFECTED_BUT_DISABL ED=4 # Many trojaned commands have this label GENERIC_ROOTKIT_LABEL="^/bin/.*sh$|bash|elite$|vejeta|\.ark" ######################### ############################################# # tools functions # # 55808.A Worm # w55808 (){ W55808_FILES="${ROOTDIR}tmp/.../a ${RO OTDIR}tmp/.../r" STATUS=0 for i in ${W55808_FILES}; do if [ -f ${i} ]; then STATUS=1 fi done if [ ${STATUS} -eq 1 ] ;then echo "Warn ing: Possible 55808 Worm installed" else if [ "${QUIET}" != "t" ]; then echo "not infected"; fi return -

Hack Proofing Sun Solaris 8.Pdf
158_hack_sun_FC 11/11/01 2:46 PM Page 1 1 YEAR UPGRADE BUYER PROTECTION PLAN ™ Protect Your Solaris Network from Attack • Complete Coverage of Solaris 8 C2 and Trusted Solaris 8 • Hundreds of Damage & Defense,Tools & Traps, and Notes from the Underground Sidebars, Security Alerts, and FAQs • Step-by-Step Instructions for Making the Most of Solaris 8 Security Enhancements Wyman Miles Ed Mitchell F. William Lynch Randy Cook Technical Editor From the authors of the bestsellingbes-selling HACK PROOFING™ YOUR NETWORK 158_HPsun_FM 10/5/01 5:07 PM Page i [email protected] With more than 1,500,000 copies of our MCSE, MCSD, CompTIA, and Cisco study guides in print, we continue to look for ways we can better serve the information needs of our readers. One way we do that is by listening. Readers like yourself have been telling us they want an Internet-based ser- vice that would extend and enhance the value of our books. Based on reader feedback and our own strategic plan, we have created a Web site that we hope will exceed your expectations. [email protected] is an interactive treasure trove of useful infor- mation focusing on our book topics and related technologies. The site offers the following features: I One-year warranty against content obsolescence due to vendor product upgrades. You can access online updates for any affected chapters. I “Ask the Author”™ customer query forms that enable you to post questions to our authors and editors. I Exclusive monthly mailings in which our experts provide answers to reader queries and clear explanations of complex material. -

A Freebsd 4.8-RELEASE Operating System Security Checklist
A FreeBSD 4.8-RELEASE Security Checklist 页码,1/14 A FreeBSD 4.8-RELEASE Operating System Security Checklist Support the BSD projects by getting a subscription to one or more of the family: FreeBSD, OpenBSD, NetBSD and Darwin Updated: June 12, 2003 Location: http://www.sddi.net/FBSDSecCheckList.html Location of the checklist version: http://www.sddi.net/FBSDSecCheckListaslist.html This document is also available in Portuguese, translated by someone or something that didn't notify me, but is still much appreciated. Assuming it's accurate, of course. If you are part of an institution or business, and you found this document useful, consider paying a fee to assist us in producing more documents and keeping this one up-to-date. You can use Paypal and send to the account of [email protected]. Location: http://www.traduzweb.com.br/scripts/tws.dll/ingport?p=kounen&lg=in_pt&url=http%3A% 2F%2Fwww.sddi.net%2FFBSDSecCheckList.html%23Installation Please note that I haven't spent much time recently on the document, but I do plan to expand and revise. As 5.0 is not meant for production, I will at least wait for 5.1 to be out for a while before I approach locking down FreeBSD 5.x. This document is intended to be a working checklist of security settings implemented on FreeBSD servers version 4.8-RELEASE. There are a number of well-written and often brilliant documents providing overviews, how-to's and faqs on FreeBSD security for the practical systems administrator, but there is no to-the-point, checklist that can be a tool for each time a server is built. -

Métodos Para Detecção Local De Rootkits E Módulos De Kernel Maliciosos Em Sistemas Unix
MÉTODOS PARA DETECÇÃO LOCAL DE ROOTKITS E MÓDULOS DE KERNEL MALICIOSOS EM SISTEMAS UNIX Nelson Murilo Klaus Steding-Jessen Pangéia Informática NIC BR Security Office SRTS 701, 70 cj E, sala 304 Rua Hum, 45 Caixa Postal 6146 70340-902 Brasília-DF 13083-970 Campinas-SP [email protected] [email protected] RESUMO Rootkits são ferramentas utilizadas com freqüência por invasores para ocultar sua presença em máquinas comprometidas, fazendo parte inclusive de alguns Worms e ferramentas de DDoS. Uma invasão pode passar meses sem ser descoberta graças a essas ferramentas. Além das versões tradicionais, rootkits vem sendo imple- mentados também sob a forma de módulos de kernel (LKMs), dificultando a sua detecção. Este artigo descreve o funcionamento desses dois tipos de rootkit, alguns métodos para sua detecção em sistemas Unix e uma ferramenta de código aberto, implementada pelos autores, para detecção automatizada de rootkits. ABSTRACT Rootkits are a very popular technique among intruders to hide themselves in compromised machines. Some rootkits are also used by Worms and DDoS tools. An intrusion can remain undetected for months when such a tool is used by an attacker. Rootkits are also being implemented as Loadable Kernel Modules (LKMs), making them much harder to detect. This paper describes the traditional as well as the LKM-based rootkit and presents some rootkit detection methods for Unix machines. This paper also presents an open source tool, developed by the authors, to detect rootkits. 1 INTRODUÇÃO evolução dos rootkits, seguido da descrição dos com- ponentes e funcionamento dos rootkits tradicionais e Com a popularização de ferramentas de ataque au- também dos implementados sob a forma de LKMs. -
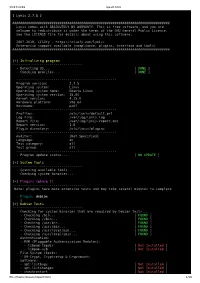
Lynis Report of Ubuntu 18.04
10/17/2019 report.html [ Lynis 2.7.5 ] ################################################################################ Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under the terms of the GNU General Public License. See the LICENSE file for details about using this software. 2007-2019, CISOfy - https://cisofy.com/lynis/ Enterprise support available (compliance, plugins, interface and tools) ################################################################################ [+] Initializing program ------------------------------------ - Detecting OS... [ DONE ] - Checking profiles... [ DONE ] --------------------------------------------------- Program version: 2.7.5 Operating system: Linux Operating system name: Ubuntu Linux Operating system version: 18.04 Kernel version: 4.15.0 Hardware platform: x86_64 Hostname: pc07 --------------------------------------------------- Profiles: /etc/lynis/default.prf Log file: /var/log/lynis.log Report file: /var/log/lynis-report.dat Report version: 1.0 Plugin directory: /etc/lynis/plugins --------------------------------------------------- Auditor: [Not Specified] Language: en Test category: all Test group: all --------------------------------------------------- - Program update status... [ NO UPDATE ] [+] System Tools ------------------------------------ - Scanning available tools... - Checking system binaries... [+] Plugins (phase 1) ------------------------------------ Note: plugins have more extensive tests and may take several minutes to complete -

Malware Forensics Field Guide for Linux Systems: Digital Forensics
Chapter 3 Postmortem Forensics Discovering and Extracting Malware and Associated Artifacts from Linux Systems Solutions in this Chapter • Linux Forensic Analysis Overview • Malware Discovery and Extraction from a Linux System • Examine Linux File System • Examine Linux Configuration Files • Keyword Searching • Forensic Reconstruction of Compromised Linux Systems • Advanced Malware Discovery and Extraction from a Linux System INTRODUCTION If live system analysis can be considered surgery, forensic examination of Linux systems can be considered an autopsy of a computer impacted by mal- ware. Trace evidence relating to a particular piece of malware may be found in various locations on the hard drive of a compromised host, including files, configuration entries, records in system logs, and associated date stamps. Foren- sic examination of such trace evidence on a Linux system is an important part of analyzing malicious code, providing context and additional information that help us address important questions about a malware incident, including how malware was placed on the system, what it did, and what remote systems were involved. This chapter provides a repeatable approach to conducting forensic examinations in malware incidents, increasing the consistency across mul- tiple computers, and enabling others to evaluate the process and results. Employing this approach, with a measure of critical thinking on the part of a digital investigator, can uncover information necessary to discover how malware was placed on the system (a.k.a. the intrusion vector), to determine Malware Forensics Field Guide for Linux Systems. http://dx.doi.org/10.1016/B978-1-59749-470-0.00003-6 Copyright © 2014 Elsevier Inc. All rights reserved. -

Geek Guide > Self-Audit
GEEK GUIDE SELF-AUDIT: CHECKING ASSUMPTIONS AT THE DOOR Table of Contents About the Sponsor .......................................................... 4 Introduction .................................................................... 5 Two Steps Necessary for Security ................................. 7 Verify Configurations ...................................................... 9 Assume Security Has Been Compromised .................. 10 Tools to Scan for Malware ............................................ 11 rkhunter �������������������������������������������������������������������������������������������������12 chkrootkit ����������������������������������������������������������������������������������������������13 LMD�������������������������������������������������������������������������������������������������������14 lynis �������������������������������������������������������������������������������������������������������19 Checking for Stealth Ports ........................................... 22 lsof ��������������������������������������������������������������������������������������������������������23 unhide ���������������������������������������������������������������������������������������������������24 Rootkits ......................................................................... 25 Conclusion .................................................................... 27 GREG BLEDSOE is VP of Operations at Personal, Inc. (http://www.personal.com). He is CEH and CPT certified and has 20 years of hard-fought experience -

How to Securely Isolate and Execute Lynis from Kali Linux
How to securely isolate and execute Lynis from Kali Linux Version 0.1, Last Updated: 11 Oct 2020 Table of Contents 1. Introduction . 1 2. Requirements. 3 2.1. Writing Conventions . 3 2.2. VirtualBox . 3 2.2.1. Clean VirtualBox Networking. 3 2.2.2. Add VirtualBox Networking . 4 2.3. Vagrant. 5 2.4. Kali Linux and Damn Vulnerable Web Application (DVWA) . 5 2.4.1. Vagrantfile . 5 2.4.2. bootstrap.sh . 8 3. Lynis. 12 3.1. Lynis output on Kali Linux VM . 14 3.2. Lynis Output on RHEL 7 VM . 25 3.3. Running Lynis on a Remote Server . 35 4. Conclusion . 36 5. Appendix . 37 1. Introduction The motivation behind this paper is to explore using the tool Lynis that comes with Kali Linux. What is this tool: "Lynis is an open source security auditing tool. Its main goal is to audit and harden Unix and Linux based systems. It scans the system by performing many security control checks. Examples include searching for installed software and determine possible configuration flaws. Many tests are part of common security guidelines and standards, with on top additional security tests. After the scan a report will be displayed with all discovered findings. To provide you with initial guidance, a link is shared to the related Lynis control." source: Kali Linux "Since Lynis is flexible, it is used for several different purposes. Typical use cases for Lynis include: - Security auditing - Compliance testing (e.g. PCI, HIPAA, SOx) - Penetration testing - Vulnerability detection - System hardening " source: Lynis What does Lynus run on? "Lynis runs on almost all UNIX-based systems and versions, including: - AIX - FreeBSD - HP-UX - Linux - macOS - NetBSD - NixOS - OpenBSD - Solaris - and others It even runs on systems like the Raspberry Pi, IoT devices, and QNAP storage devices." source: Lynis "Lynis scanning is modular and opportunistic. -

Methods for Detecting Kernel Rootkits
University of Louisville ThinkIR: The University of Louisville's Institutional Repository Electronic Theses and Dissertations 12-2007 Methods for detecting kernel rootkits. Douglas Ray Wampler University of Louisville Follow this and additional works at: https://ir.library.louisville.edu/etd Recommended Citation Wampler, Douglas Ray, "Methods for detecting kernel rootkits." (2007). Electronic Theses and Dissertations. Paper 1507. https://doi.org/10.18297/etd/1507 This Doctoral Dissertation is brought to you for free and open access by ThinkIR: The University of Louisville's Institutional Repository. It has been accepted for inclusion in Electronic Theses and Dissertations by an authorized administrator of ThinkIR: The University of Louisville's Institutional Repository. This title appears here courtesy of the author, who has retained all other copyrights. For more information, please contact [email protected]. METHODS FOR DETECTING KERNEL ROOTKITS By Douglas Ray Wampler B.S., Indiana State University, 1994 M.S. Ball State University, 2003 A Dissertation Submited to the Faculty of the Graduate School of the University of Louisville In Partial Fulfillment of the Requirements For the Degree of Doctor of Philsophy Department of Computer Engineering and Computer Science University of Louisville Louisville, Kentucky December 2007 Copyright 2007 by Douglas Ray Wampler All rights reserved METHODS FOR DETECTING KERNEL ROOTKTIS By Douglas Ray Wampler B.S. Indiana State University, 1994 M.S., Ball State University, 2003 A Dissertation Approved on November 12, 2007 By the following Dissertation Committee: ________________________________________ James H. Graham, Dissertation Director ________________________________________ DarJen Chang ________________________________________ Gail W. Depuy ________________________________________ Adel S. Elmaghraby ________________________________________ Mehmed M. Kantardzic ii DEDICATION This dissertation is dedicated to my parents, Mr.