9781119588054.Index.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bostonbarjournal
January/February 2009 BostonBarA Publication of the Boston Bar Association Journal Web 2.0 and the Lost Generation Web 2.0: What’s Evidence Between “Friends”? Q W The New E-Discovery Frontier — Seeking Facts in the Web 2.0 World (and Other Miscellany) do you E Twitter? Massachusetts Adopts Comprehensive Information Security Regulations updated 3 minutes ago Law Firm Added You as a Friend What Happens When the College Rumor Mill Goes Online? R 77º The Future of Online THIS AGREE- Networking MENT (hereinafter referred to as the “Agreement”) made and entered into this ____________ day of Y tweet! T Boston Bar Journal • January/February 2009 1 Boston Bar Journal Volume 53, Number 1 January/February 2009 Contents President’s Page 2 Officers of the Boston Bar Association President, Kathy B. Weinman President-Elect, John J. Regan BBJ Editorial Policy 3 Vice President, Donald R. Frederico Treasurer, Lisa C. Goodheart Secretary, James D. Smeallie Departments Members of the Council Opening Statement 4 Lisa M. Cukier Damon P. Hart Edward Notis-McConarty Paul T. Dacier Christine Hughes Maureen A. O’Rourke Web 2.0 and the Lost Generation Anthony M. Doniger Julia Huston Laura S. Peabody Bruce E. Falby Kimberly Y. Jones Mala M. Rafik By Donald R. Frederico George P. Field Wayne M. Kennard Rebecca B. Ransom Laurie Flynn Grace H. Lee Douglas B. Rosner First Principles 5 Lawrence M. Friedman James D. Masterman Charles E. Walker, Jr. Elizabeth Shea Fries Wm. Shaw McDermott Mark J. Warner Web 2.0: What’s Evidence Randy M. Gioia Between “Friends”? Past Presidents By Seth P. -

Revista Comunicação E Sociedade, Vol. 25
Comunicação e Sociedade, vol. 25, 2014, pp. 252 – 266 The (non)regulation of the blogosphere: the ethics of online debate Elsa Costa e Silva [email protected] Centro de Estudos de Comunicação e Sociedade, Universidade do Minho, Instituto de Ciências Sociais, 4710-057 Braga, Portugal Abstract New technologies have enabled innovative possibilities of communication, but have also imposed new upon matters of ethics, particularly in regards to platforms such as blogs. This ar- ticle builds upon the reflections and experiences on this issue, in an attempt to map and analyse the ethical questions underlying the Portuguese blogosphere. In order to reflect on the possibil- ity and opportunity to create a code of ethics for bloggers, attention is permanently paid to the political blogosphere. Keywords Code of conduct; values; political blogs; freedom of expression 1. Introduction The debate about ethics in communication (a theme that is perhaps as old as the first reflections on the human ability to interact with others) remains extremely dynamic in contemporary societies, fuelled by innovative technological capabilities that bring new challenges to this endless questioning. Ethics is a construction whose pillars oscillate between different perspectives (Fidalgo, 2007), ranging from a greater primacy of the freedom of the ‘I’, to a primacy of the collective responsibility, from the justification by the norms (to do that which is correct) to the justification by the purposes (the good to be achieved). Values and rules underlie ethics, providing a standard for human behaviour and forms of procedure. It is never a finished process, but the result of ongoing tensions and negotiations between interested members of the community (Christofoletti, 2011). -

What Is a Website Content Management System?
A GUIDE TO WEBSITE CONTENT MANAGEMENT CHOICES FOR YOUR BUSINESS Comparing SquareSpace, Wordpress, and HubSpot Website Management Systems A Guide To Website Content Management Choices For Your Business | 1 WHAT IS A WEBSITE CONTENT MANAGEMENT SYSTEM? A website content management system (CMS) allows you to make changes to your website without learning any website code. This software system provides website authoring, collaboration, and administration tools designed to allow users with little knowledge of web programming or markup languages to create and manage website content with relative ease. Website content management systems are web applications that are purchased through a monthly subscription and built when a website is initially created (they can’t be added after the fact). Bottom Line: Website CMS software allows you to control your website, making changes when needed without incurring costly maintenance contracts. A Guide To Website Content Management Choices For Your Business | 2 WE JUST BUILT A NEW WEBSITE A FEW YEARS AGO, WHY IS IT ALREADY OUT OF DATE? When you launched your last website, it was a big success. Over the years your once clear and easy to understand homepage has become a cluttered mess. Photos show former employees and never mind what the website looks like on the latest technology. A firm is hired and the cycle repeats itself. If this sounds familiar, that’s because most businesses redesign their website every 3-5 years. What if there was a way to break this endless cycle and actually show a consistent return on your website investment? That’s exactly what the latest website content management software systems deliver. -

3.3.5.Haulath.Pdf
CONTENTS SL. PAGE NO. ARTICLE NO 1 DATA PRE-PROCESSING FOR EFFECTIVE INTRUSION DETECTION RIYAD AM 5 2. AN ENHANCED AUTHENTICATION SYSTEM USING MULTIMODAL BIOMETRICS MOHAMED BASHEER. K.P DR.T. ABDUL RAZAK 9 6. GRADIENT FEATURE EXTRACTION USING FOR MALAYALAM PALM LEAF DOCUMENT IMAGEGEENA K.P 19 7. INTERNET ADDICTION JESNA K 23 8. VANETS AND ITS APPLICATION: PRESENT AND FUTURE.JISHA K 26 9. DISTRIBUTED OPERATING SYSTEM AND AMOEBAKHAIRUNNISA K 30 5. INDIVIDUAL SOCIAL MEDIA USAGE POLICY: ORGANIZATION INFORMATION SECURITY THROUGH DATA MINING REJEESH.E1, MOHAMED JAMSHAD K2, ANUPAMA M3 34 3. APPLICATION OF DATA MINING TECHNIQUES ON NETWORK SECURITY O.JAMSHEELA 38 4. SECURITY PRIVACY AND TRUST IN SOCIAL MEDIAMS HAULATH K 43 10. SECURITY AND PRIVACY ISSUES AND SOLUTIONS FOR WIRELESS SYSTEM NETWORKS (WSN) AND RFID RESHMA M SHABEER THIRUVAKALATHIL 45 11. ARTIFICIAL INTELLIGENCE IN CYBER DEFENSESHAMEE AKTHAR. K. ASKARALI. K.T 51 SECURITY PRIVACY AND TRUST IN SOCIAL MEDIA Haulath K, Assistant professor, Department of Computer Science, EMEA College, Kondotty. [email protected] Abstract— Channels social interactions using 2. Social Blogs extremely accessible and scalable publishing A blog (a truncation of the expression weblog) is a methods over the internet. Connecting individuals, discussion or informational site published on communities, organization. Exchange of idea Sharing the World Wide Web consisting of discrete entries message and collaboration through security privacy (“posts”) typically displayed in reverse chronological and trust. order (the most recent post appears first). Until 2009, Classification of Social Media blogs were usually the work of a single individual, occasionally of a small group, and often covered a 1. -
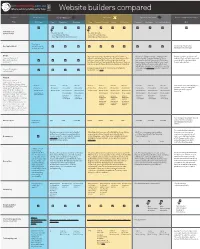
Website Builders Compared
Website builders compared Service WordPress.org WordPress.com Wix.com Squarespace.com Hire a designer/developer Plan N/A (free) Free Premium Business Free Connect Domain Combo Unlimited Personal Business Online Store Basic N/A O X O O X O O O O O O O Your choice of domain name? No, your domain No, your domain name will look like this: name will look like this: www. tigersnetball.wordpress. com www. tigersnetball.wix. com Third party. Hosting included? You will need to O O O O O O O O O O Third party. You or your arrange yourself. developer can arrange it. Design Once you've chosen a template, you can't change it Almost all of Squarespace's templates are A good designer/developer will Free and "premium" without rebuilding the whole site. All templates are free, picture-heavy. To make the best of them, help you flesh out your ideas and themes/templates O O O O but some have certain features (e.g. hotel booking you need to start with good-quality images. come up with a design unique availalbe? functions) that can't be used with the Free plan; they can Squarespace templates tend to have a look to your organisation. only be used with Connect Domain, Combo or Unlimited. and feel that particularly suits artists and arts groups - browse the templates, even the To see some examples of community-oriented Wix business ones click here and you'll see what Themes/templates O X O O templates, click here. we mean. customisable? Support Wordpress support consist of online forums, Q&As, tutorials, videos and so on, all written by the "Wordpress - Website - Website - Website - Website - Website - Website - Website - Website - Website - Website - Website This varies from one company to community". -

Handbook for Bloggers and Cyber-Dissidents
HANDBOOK FOR BLOGGERS AND CYBER-DISSIDENTS REPORTERS WITHOUT BORDERS MARCH 2008 Файл загружен с http://www.ifap.ru HANDBOOK FOR BLOGGERS AND CYBER-DISSIDENTS CONTENTS © 2008 Reporters Without Borders 04 BLOGGERS, A NEW SOURCE OF NEWS Clothilde Le Coz 07 WHAT’S A BLOG ? LeMondedublog.com 08 THE LANGUAGE OF BLOGGING LeMondedublog.com 10 CHOOSING THE BEST TOOL Cyril Fiévet, Marc-Olivier Peyer and LeMondedublog.com 16 HOW TO SET UP AND RUN A BLOG The Wordpress system 22 WHAT ETHICS SHOULD BLOGUEURS HAVE ? Dan Gillmor 26 GETTING YOUR BLOG PICKED UP BY SEARCH-ENGINES Olivier Andrieu 32 WHAT REALLY MAKES A BLOG SHINE ? Mark Glaser 36 P ERSONAL ACCOUNTS • SWITZERLAND: “” Picidae 40 • EGYPT: “When the line between journalist and activist disappears” Wael Abbas 43 • THAILAND : “The Web was not designed for bloggers” Jotman 46 HOW TO BLOG ANONYMOUSLY WITH WORDPRESS AND TOR Ethan Zuckerman 54 TECHNICAL WAYS TO GET ROUND CENSORSHIP Nart Villeneuve 71 ENS URING YOUR E-MAIL IS TRULY PRIVATE Ludovic Pierrat 75 TH E 2008 GOLDEN SCISSORS OF CYBER-CENSORSHIP Clothilde Le Coz 3 I REPORTERS WITHOUT BORDERS INTRODUCTION BLOGGERS, A NEW SOURCE OF NEWS By Clothilde Le Coz B loggers cause anxiety. Governments are wary of these men and women, who are posting news, without being professional journalists. Worse, bloggers sometimes raise sensitive issues which the media, now known as "tradition- al", do not dare cover. Blogs have in some countries become a source of news in their own right. Nearly 120,000 blogs are created every day. Certainly the blogosphere is not just adorned by gems of courage and truth. -

How Indirect Intermediaries Shape Online Speech
Mitchell 1 Anna Mitchell Professor Nate Persily INTLPOL 323 December 16, 2018 Hidden Censors: How Indirect Intermediaries Shape Online Speech 1. Introduction “Literally, I woke up in a bad mood and decided someone shouldn’t be allowed on the internet. No one should have that power.” After a whirlwind five days of social media protests and internal tension, Matthew Prince, the CEO of Cloudflare, an Internet-services company, decided to terminate its contract with The Daily Stormer. The Internet’s most popular neo-Nazi website had vanished from the Web.1 Cloudflare’s content distribution network (CDN), improving the Stormer’s performance and protecting it from distributed denial of service (DDoS) attacks, had allowed the site to stay afloat for months or years. But that changed in 2017 during a period of tense racial relations in the United States. From August 11 to 12, the Daily Stormer helped organize the white supremacist Unite the Right rally in Charlottesville, Virginia. Soon after, it published articles calling murdered protestor Heather Heyer a “sloppy lard ass” and labeling her death an accidental heart attack.2 Reaction was swift. The next day, activist Amy Suskind tagged web hosting service GoDaddy in a Twitter post: “@GoDaddy you host The Daily Stormer - they posted this on their site. Please retweet if you think this hate should be taken down & banned.”3 Within 24 hours, GoDaddy responded by withdrawing hosting services. When the Stormer tried to switch to Google, it soon followed suit.4 Zoho refused to provide email service,5 and Twitter shut down Mitchell 2 associated accounts.6 With multiple major companies withdrawing services, it became increasingly difficult for the Stormer to host and propagate content. -

FOR THERAPISTS and COACHES LAUNCHING a SQUARESPACE WEBSITE Copyright Stuff
The Getting Started Guide FOR THERAPISTS AND COACHES LAUNCHING A SQUARESPACE WEBSITE Copyright Stuff Copyright © 2021 by Emily Whitish. All rights reserved. You are welcome to print a copy of this document for your personal use. Other than that, no part of this publication may be reproduced, stored, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, without the prior written permission of the author. Requests to the author and publisher for permission should be addressed to the following email: [email protected]. Limitation of liability/disclaimer of warranty: While the publisher and author have used their best efforts in preparing this guide and workbook, they make no representations or warranties with respect to the accuracy or completeness of the contents of this document and specifically disclaim any implied warranties of merchantability or fitness for particular purpose. No warranty may be created or extended by sales representatives, promoters, or written sales materials. The advice and strategies contained herein may not be suitable for your situation. You should consult with a professional where appropriate. Neither the publisher nor author shall be liable for any loss of profit or any other commercial damages, including but not limited to special, incidental, consequential, or other damages. How to Take Ownership of Your Website Once you have paid for your website, I will transfer ownership of the website to you and Squarespace will send you an email notification. You will click the link on the email to be taken to Squarespace where you will create an account. Once you have an account, you can accept the “Administrator” privileges on your site and it will show up on your dashboard. -

Social Media Identity Deception Detection: a Survey
Social Media Identity Deception Detection: A Survey AHMED ALHARBI, HAI DONG, XUN YI, ZAHIR TARI, and IBRAHIM KHALIL, School of Computing Technologies, RMIT University, Australia Social media have been growing rapidly and become essential elements of many people’s lives. Meanwhile, social media have also come to be a popular source for identity deception. Many social media identity deception cases have arisen over the past few years. Recent studies have been conducted to prevent and detect identity deception. This survey analyses various identity deception attacks, which can be categorized into fake profile, identity theft and identity cloning. This survey provides a detailed review of social media identity deception detection techniques. It also identifies primary research challenges and issues in the existing detection techniques. This article is expected to benefit both researchers and social media providers. CCS Concepts: • Security and privacy ! Social engineering attacks; Social network security and privacy. Additional Key Words and Phrases: identity deception, fake profile, Sybil, sockpuppet, social botnet, identity theft, identity cloning, detection techniques ACM Reference Format: Ahmed Alharbi, Hai Dong, Xun Yi, Zahir Tari, and Ibrahim Khalil. 2021. Social Media Identity Deception Detection: A Survey . ACM Comput. Surv. 37, 4, Article 111 (January 2021), 35 pages. https://doi.org/10.1145/ 1122445.1122456 1 INTRODUCTION Social media are web-based communication tools that facilitate people with creating customized user profiles to interact and share information with each other. Social media have been growing rapidly in the last two decades and have become an integral part of many people’s lives. Users in various social media platforms totalled almost 3.8 billion at the start of 2020, with a total growth of 321 million worldwide in the past 12 months1. -

Annex 1 Namecheap Contact Information
Annex 1 Namecheap contact information NameCheap, Inc. 4600 East Washington Street Suite 33 Phoenix AZ 85034 United States +1 3234480232 These IRP proceedings are followed up internally at Namecheap by: − Mr. Owen Smigelski, Contact Information Redacted All notifications in these IRP proceedings can be made to Namecheap’s counsel: − Mr. Flip Petillion, [email protected] − Mr. Jan Janssen, jjanssen@petillion law. About Namecheap Our Story and M ss on Namecheap Com 24/02/2020 11 40 Payment Options We use cookies to understand how you use our site and to improve your overall experience. This includes personalizing content and advertising. By › More Information ✓ Accept continuing to use our site, you accept our use of cookies, revised Privacy Policy, Terms of Service and Cookie Policy. https //www namecheap com/about/ Page 4 of 4 Namecheap Phoen x AZ 22/02/2020 09 47 CHANNELS MORE INC. SUBSCRIBE FOLLOW INC. STARTUP EVENTS GROW NEWSLETTERS LEAD MAGAZINE INNOVATE BRANDVIEW MAGAZINE TECHNOLOGY PODCASTS DIGITAL EDITION MONEY SUBSCRIBE INC. 5000 VIDEO © 2018 Manuseto VenturesHelp Center Advertise Privacy Sitemap https //www nc com/prof e/namecheap Page 2 of 2 Annex 2 Proposed Renewa of org Reg stry Agreement CANN 23/02/2020 16 13 Proposed Renewal of .org Registry Agreement Open Date Close Date Staff Report Due 18 Mar 2019 23:59 UTC 29 Apr 2019 23:59 UTC 3 Jun 2019 23:59 UTC ! ! ! Comments Closed Report of Public Comments (https://www.icann.org/en/system/files/files/report- comments-org-renewal-03jun19-en.pdf) Follow Updates (/users/sign_up? View Comments document_id=13925&following=true) (https://mm.icann.org/pipermail/comments- org-renewal-18mar19) Origina!ng Organiza!on Brief Overview Global Domains Division Purpose: The purpose of this public comment proceeding is to obtain community input on the proposed .org renewal Staff Contact agreement (herein referred to as ".org renewal agreement"). -

Blog Rules: a Business Guide to Managing Policy, Public Relations, and Legal Issues Has You Covered
Other Books by Nancy Flynn Instant Messaging Rules: A Business Guide to Managing Policies, Security, and Legal Issues for Safe IM Communication, Nancy Flynn, (AMACOM) E-Mail Rules: A Business Guide to Managing Policies, Security, and Legal Issues for E-Mail and Digital Communication, Nancy Flynn and Randolph Kahn, Esq., (AMACOM) The ePolicy Handbook: Designing and Implementing Effective E-Mail, Internet, and Software Policies, Nancy Flynn (AMACOM) Writing Effective E-Mail: Improving Your Electronic Communication, Nancy Flynn and Tom Flynn (Crisp) E-Mail Management, Nancy Flynn (Thomson Learning) ................. 15888$ $$FM 05-19-06 09:29:45 PS PAGE i This page intentionally left blank Blog Rules A Business Guide to Managing Policy, Public Relations, and Legal Issues Nancy Flynn American Management Association New York • Atlanta • Brussels • Chicago • Mexico City • San Francisco Shanghai • Tokyo • Toronto • Washington, D. C. ................. 15888$ $$FM 05-19-06 09:29:45 PS PAGE iii Special discounts on bulk quantities of AMACOM books are available to corporations, professional associations, and other organizations. For details, contact Special Sales Department, AMACOM, a division of American Management Association, 1601 Broadway, New York, NY 10019. Tel.: 212-903-8316. Fax: 212-903-8083. Web site: www.amacombooks.org This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold with the understanding that the publisher is not engaged in rendering legal, accounting, or other professional service. If legal advice or other expert assistance is required, the services of a competent professional person should be sought. Although this book is designed to provide accurate and authoritative information in regard to the subject matter covered, it is sold with the understanding that the publisher and author are not engaged in rendering legal, regulatory, technology, or other professional service. -

SOCIAL MEDIA USE and MISUSE: a GUIDE for PSYCHIATRISTS the Content of This Booklet (“Content”) Is for Informational Purposes Only
SOCIAL MEDIA USE AND MISUSE: A GUIDE FOR PSYCHIATRISTS The content of this booklet (“Content”) is for informational purposes only. The Content is not intended to be a substitute for professional legal advice or judgment, or for other professional advice. Always seek the advice of your attorney with any questions you may have regarding the Content. Never disregard professional legal advice or delay in seeking it because of the Content. ©2015 Professional Risk Management Services, Inc. (PRMS). All rights reserved. Social Media Use and Misuse: A Guide for Psychiatrists PRMS 3 Introduction 4 Websites 5 Facebook 7 LinkedIn 10 Doximity, Sermo and Other Medically-Oriented 10 Social Networking Communities Blogging 11 Twitter 14 Listservs 15 Social Media in the Medical Office 16 Managing Your Online Reputation – Yes You Do Have One 19 Asking Patients to Rate You 20 Googling Patients 20 Physicians and Social Media – Further Guidance 22 Conclusion 23 Glossary 24 Social Media Use and Misuse: A Guide for Psychiatrists PRMS 4 INTRODUCTION The way patients seek out healthcare information is changing. Whereas once patients would pick up the phone and call their doctors, today’s patients are more likely to look to the Internet for information. Psychiatrists are taking note of this change and are looking for guidance on using technology to enhance physician-patient communication and to provide patients with accurate and reliable information. Many are also recognizing that in order to be found by prospective patients, they need an online presence and are exploring options for achieving this. To help in this endeavor, in the following pages we will discuss various forms of social media and ways in which they may be used by you, in your practice, and in your care of patients.