Supporting Protocols and Framing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

XEP-0347: Internet of Things - Discovery
XEP-0347: Internet of Things - Discovery Peter Waher mailto:peterwaher@hotmail:com xmpp:peter:waher@jabber:org http://www:linkedin:com/in/peterwaher Ronny Klauck mailto:rklauck@informatik:tu-cottbus:de xmpp:TBD http://www-rnks:informatik:tu-cottbus:de/~rklauck 2018-11-03 Version 0.5.1 Status Type Short Name Deferred Standards Track iot-discovery This specification describes an architecture based on the XMPP protocol whereby Things can be in- stalled and safely discovered by their owners and connected into networks of Things. Legal Copyright This XMPP Extension Protocol is copyright © 1999 – 2020 by the XMPP Standards Foundation (XSF). Permissions Permission is hereby granted, free of charge, to any person obtaining a copy of this specification (the ”Specification”), to make use of the Specification without restriction, including without limitation the rights to implement the Specification in a software program, deploy the Specification in a network service, and copy, modify, merge, publish, translate, distribute, sublicense, or sell copies of the Specifi- cation, and to permit persons to whom the Specification is furnished to do so, subject to the condition that the foregoing copyright notice and this permission notice shall be included in all copies or sub- stantial portions of the Specification. Unless separate permission is granted, modified works that are redistributed shall not contain misleading information regarding the authors, title, number, or pub- lisher of the Specification, and shall not claim endorsement of the modified works by the authors, any organization or project to which the authors belong, or the XMPP Standards Foundation. Warranty ## NOTE WELL: This Specification is provided on an ”AS IS” BASIS, WITHOUT WARRANTIES OR CONDI- TIONS OF ANY KIND, express or implied, including, without limitation, any warranties or conditions of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A PARTICULAR PURPOSE. -

Well Known TCP and UDP Ports Used by Apple Software Products
Well known TCP and UDP ports used by Apple Languages English software products Symptoms Learn more about TCP and UDP ports used by Apple products, such as OS X, OS X Server, Apple Remote Desktop, and iCloud. Many of these are referred to as "well known" industry standard ports. Resolution About this table The Service or Protocol Name column lists services registered with the Internet Assigned Numbers Authority (http://www.iana.org/), except where noted as "unregistered use." The names of Apple products that use these services or protocols appear in the Used By/Additional Information column. The RFC column lists the number of the Request For Comment document that defines the particular service or protocol, which may be used for reference. RFC documents are maintained by RFC Editor (http://www.rfc- editor.org/). If multiple RFCs define a protocol, there may only be one listed here. This article is updated periodically and contains information that is available at time of publication. This document is intended as a quick reference and should not be regarded as comprehensive. Apple products listed in the table are the most commonly used examples, not a comprehensive list. For more information, review the Notes below the table. Tip: Some services may use two or more ports. It is recommend that once you've found an instance of a product in this list, search on the name (Command-F) and then repeat (Command-G) to locate all occurrences of the product. For example, VPN service may use up to four diferent ports: 500, 1701, 1723, and 4500. -

Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS
DEVICES AND COMMUNICATION BUSES FOR DEVICES NETWORK– Lesson-13: INTERNET ENABLED SYSTEMS NETWORK PROTOCOLS Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 1 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Communication to other system on the Internet. Use html (hyper text markup language) or MIME (Multipurpose Internet Mail Extension) type files Use TCP (transport control protocol) or UDP (user datagram protocol) as transport layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 2 Raj Kamal, Publs.: McGraw-Hill Education Internet enabled embedded system Addressed by an IP address Use IP (internet protocol) at network layer protocol Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 3 Raj Kamal, Publs.: McGraw-Hill Education MIME Format to enable attachment of multiple types of files txt (text file) doc (MSOFFICE Word document file) gif (graphic image format file) jpg (jpg format image file) wav format voice or music file Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 4 Raj Kamal, Publs.: McGraw-Hill Education A system at one IP address Communication with other system at another IP address using the physical connections on the Internet and routers Since Internet is global network, the system connects to remotely as well as short range located system. Chapter-5 L13: "Embedded Systems - Architecture, Programming and Design", 2015 5 Raj Kamal, Publs.: McGraw-Hill Education -

951 John Gilmore (Sun Microsystems) September 1985
Network Working Group Bill Croft (Stanford University) Request for Comments: 951 John Gilmore (Sun Microsystems) September 1985 BOOTSTRAP PROTOCOL (BOOTP) 1. Status of this Memo This RFC suggests a proposed protocol for the ARPA-Internet community, and requests discussion and suggestions for improvements. Distribution of this memo is unlimited. 2. Overview This RFC describes an IP/UDP bootstrap protocol (BOOTP) which allows a diskless client machine to discover its own IP address, the address of a server host, and the name of a file to be loaded into memory and executed. The bootstrap operation can be thought of as consisting of TWO PHASES. This RFC describes the first phase, which could be labeled 'address determination and bootfile selection'. After this address and filename information is obtained, control passes to the second phase of the bootstrap where a file transfer occurs. The file transfer will typically use the TFTP protocol [9], since it is intended that both phases reside in PROM on the client. However BOOTP could also work with other protocols such as SFTP [3] or FTP [6]. We suggest that the client's PROM software provide a way to do a complete bootstrap without 'user' interaction. This is the type of boot that would occur during an unattended power-up. A mechanism should be provided for the user to manually supply the necessary address and filename information to bypass the BOOTP protocol and enter the file transfer phase directly. If non-volatile storage is available, we suggest keeping default settings there and bypassing the BOOTP protocol unless these settings cause the file transfer phase to fail. -

Optional Interniche Protocol Modules for Nichelite For
fåíÉêkáÅÜÉ=qÉÅÜåçäçÖáÉëI=fåÅK bãÄÉÇÇÉÇ=mêçíçÅçä=péÉÅá~äáëíë ïïïKáåáÅÜÉKÅçã Available from NXP : Optional InterNiche Protocol Modules for InterNiche Technologies and NXP have collaborated to NicheLite for LPC provide an OEM version of InterNiche’s NicheLite™ InterNiche’s optional protocol modules have been optimized for the LPC developed from the ground up to address the needs of low architecture. NicheLite for LPC provides the functionality of cost embedded systems. The result is a modular solution NicheLite and is RFC compliant. that is functionally comprehensive, requiring minimal system and memory requirements, and is tuned for both Key Features portability and performance. • Transmission Control Protocol (TCP) supporting InterNiche's lightweight API, and a Zero-Copy option NicheStack™ SNMP(v1, v2c or v3) are fully compliant agent • Internet Protocol (IPv4), without implementations enabling industry standard device fragmentation and reassembly monitoring with SNMP management workstations. The • User Datagram Protocol (UDP) • Address Resolution Protocol (ARP) complete SDK includes a MIB Compiler tool. • Internet Control Message Protocol (ICMP) NicheStack HTTPServer™ is an innovative robust embedded • Dynamic Host Configuration Protocol (DHCP) Client web server that has been designed specifically to optimize • Name Service (DNS) Client size, performance and support for dynamic data displays • Bootstrap Protocol (BOOTP) • Trivial File Transfer Protocol (TFTP), and important security features. client and server • Ping Protocol Options: A variety of optional protocols support • NicheTool ™ solutions for specific applications including Point to Point • NicheFile ™ VFS • Single Ethernet interface Protocol (PPP), PPPoE, Telnet, FTP, SMTP and POP3. • No "GPL Contamination" Includes two operating systems Options • SuperLoop : a very fast, do-forever loop running various tasks and Email applications in a run-to-completion FTP model. -

IP Host Configuration IK2218/EP2120
IP Host Configuration IK2218/EP2120 Markus Hidell, [email protected] KTH School of ICT Acknowledgements • The presentation builds upon material from - Previous slides by Markus Hidell, Björn Knutsson and Peter Sjödin - Computer Networking: A Top Down Approach, 5th ed. Jim Kurose, Keith Ross. Addison-Wesley. - TCP/IP Protocol Suite, 4th ed, Behrouz Foruzan. McGraw-Hill. 2 Outline • Introduction • Automating IP Configuration • Stateful configuration - DHCP • Stateless configuration – SLAAC • Further reading 3 Basic Question • IP (Internet Protocol): - what packets look like and how to interpret IP addresses • Routing protocols: - calculate paths through the network • DNS (Domain Name System): - how to translate between names and IP addresses But how do we get an IP address for a network interface? 4 Manual IP Address Configuration • System administrator: - Manually select an IP address from currently unassigned addresses in the subnet - Assign to host machine - Manually edit configuration file on host machine • Statically assigned address - require work to change address • What if... - Sysadmin forgets to mark address as assigned? - Subnet changes address? Manual IP address configuration is not a practical solution 5 IP Configuration Information • Just IP address is not enough information for hosts - Need to know subnet mask for local traffic • CIDR notation: 10.1.1.0/24 - Need to know IP address of gateway for non-local traffic • Gateway: the router that connects our subnet to the Internet (default gateway) • What else might we want to tell -

Bootstrap Protocol, BOOTP, Is the Recommended Way to Establish Communications from the Host to the Printer in an Internet Protocol Environment
BOOTP Bootstrap protocol, BOOTP, is the recommended way to establish communications from the host to the printer in an internet protocol environment. BOOTP obtains booting data from the bootptab file. With the proper information stored in the bootptab file, the printer can find its own name and IP address and boot from the network without any intervention, even for a first time boot. 1. Verify that the bootpd and bootptab files are in the correct directories: UNIX: /etc or /usr/etc directory OS/2: \TCPIP\ETC (for bootptab) and \TCPIP\BIN (for bootpd) LAN Server: MPTN\ETC (for bootptab) and \MPTN\BIN (for bootpd) Type: ls bootp* 2. Edit the hosts file to add the printer internet addresses and names: 128.07.60.30 P340-mktg 128.07.60.31 P340-sales For OS/2, use the TCP/IP Configuration Notebook under the Services tab to add the printer internet addresses and names. 3. Some UNIX hosts may require an explicit update to the arp table to add the new entries. This command is host-specific; check your host documentation for details. arp -s ether P340-mktg 08:00:11:01:00:45 arp -s ether P340-sales 08:00:11:01:00:46 The ether switch indicates that you are providing an Ethernet address. 4. Set up the bootptab file. 5. Start or restart the inetd or bootpd daemon. For OS/2 Warp, LAN Server 4.0, and UNIX, use the bootpd daemon. Here is a sample bootptab file; check your host system documentation to see which fields your implementation of BOOTP supports. -

Kenneth Brennan ISC330 Lab 1 How Many Packets (Frames)
Kenneth Brennan ISC330 Lab 1 How many packets (frames) are there in this capture? 499 Choose the first frame in the top pane. Expand the Internet Protocol triangle of this frame in the middle pane. What are the source and destination addresses of this packet? 10.1.6.18 10.1.3.143 To what entities do these numbers refer? IP addresses Expand the Transmission Control Protocol triangle of the packet. What are the source and destination ports of this packet? i. 1720 ii. 32803 To what entities do these numbers refer? iii. Port numbers Note that wireshark is smart enough to "know" which ports are typically used by internet applications. what service is the host at IP 10.1.3.143 trying to access on the host with IP 10.1.6.18? [hint] Telephone call Read this discussion excerpted from here and answer the questions that follow as best you can. H.323 uses a single fixed TCP port (1720) to start a call using the H.225 protocol (defined by H.323 suite) for call control. Once that protocol is complete, it then uses a dynamic TCP port for the H.245 protocol (also defined by the H.323 suite) for capabilities exchange (caps exchange) and channel control. Finally, it opens up two dynamic UDP ports for each type of media that was negotiated for the call (audio, video, far-end camera control, etc.). This first port carries the RTP protocol data (defined by the H.225 specification) and the second one carries the RTCP data (defined by the H.225 specification). -

Network Protocols and Service
UNIT 2 NETWORK PROTOCOLS AND SERVICE 1 SYLLABUS 2.1 Dynamic Host Control Protocol(DHCP): DHCP Origins :ARP,RARP,BOOTP DHCP Objectives, IP Address assignments, DHCP Architecture. 2.2 Introduction to Domain Name Systems (DNS) DNS Objectives Domain Naming, Top Lavel Domains, Second Level Domains, Sub- domains DNS Functions, Resource Records, DNS Name Resolution, Resolves, DNS Requests, Root Name Servers, Resolving a Domain Name, DNS Name Registration 2.3 Network Printing Concepts Locally Connected Print Devices, Setting up local Print Devices, Shared Print Devices, Sharing Locally Attached Print Devices, 2 Describe Windows Network Printing and Add print Wizard. 2.1 DHCP ORIGINS: ADDRESS RESOLUTION PROTOCOL(ARP) . Address Resolution Protocol (ARP) is a protocol for mapping an Internet Protocol address (IP address) to a physical machine address that is recognized in the local network. ARP stands for Address Resolution Protocol. When you try to ping an IP address on your local network, say 192.168.1.1, your system has to turn the IP address 192.168.1.1 into a MAC address. This involves using ARP to resolve the address, hence its name. Systems keep an ARP look-up table where they store information about what IP addresses are associated with what MAC addresses. 3 ARP CONT… . When trying to send a packet to an IP address, the system will first consult this table to see if it already knows the MAC address. If there is a value cached, ARP is not used. If the IP address is not found in the ARP table, the system will then send a broadcast packet to the network using the ARP protocol to ask "who has 192.168.1.1". -

Bootp and DHCP
BootP and DHCP Flexible and Scalable Host Configuration (C) Herbert Haas 2005/03/11 1 Shortcomings of RARP Reverse Address Resolution Protocol Only IP Address distribution No subnet mask Using hardware address for identification New methods needed: BOOTP, DHCP (C) Herbert Haas 2005/03/11 2 RARP was one of the first protocols which offers automatically an IP Address to a new connected client. But RARP is an old protocol with many disadvantages. It can only distribute an IP Address without a subnet mask. RARP uses the hardware address for identification. This make it impossible to connect new clients to the network without some administrative work. 2 Bootstrap Protocol (BOOTP) A static solution with many parameters 3 Goal Clients request IP address and other parameters from server Subnet mask, configuration filename, ... IP addresses are predefined in a list Fixed mapping MAC address IP address Defined in RFC 951 and RFC 1048 (C) Herbert Haas 2005/03/11 4 The Bootstrap Protocol can offer many important parameters to the client. The most important parameters are the subnet mask and the configuration filename. With the configuration filename it is possible to connect a no-disk client. Also BOOTP uses a fixed mapping via hardware address (Ethernet Mac Address). 4 Bootstrap Eth2 DA = FFFF.FFFF.FFFF DA = 255.255.255.255 IP SA = 0.0.0.0 DPort = 67 UDP SPort = 68 Request-ID = 77 B Client IP = 0.0.0.0 O MAC = A O Your IP = ? T BOOTP Server IP = ? P Server Image File = ? Here is MAC A, I need an IP address, and something to boot! TFTP BOOTP Client Server (C) Herbert Haas 2005/03/11 5 In the picture above you see the classic bootstrap principle. -

Network Protocols Handbook
Third Edition Network Protocols TCP/IP Ethernet ATM Handbook Frame Relay WAN LAN MAN WLAN SS7/C7 VOIP Security VPN SAN VLAN IEEE IETF ISO Javvin Technologies,ITU-T Inc. ANSI Cisco IBM Apple Microsoft Novell I Table of Contents Table of Contents Network Communication Architecture and Protocols•••••••••••••••••••••••••••••••••••••••••••••1 OSI Network Architecture 7 Layers Model•••••••••••••••••••••••••••••••••••••••••••••••••••••••••2 TCP/IP Four Layers Archiitecture Model••••••••••••••••••••••••••••••••••••••••••••••••••••••••••5 Other Network Architecture Models: IBM SNA•••••••••••••••••••••••••••••••••••••••••••••••••7 Network Protocols: Definition and Overview•••••••••••••••••••••••••••••••••••••••••••••••••••••9 Protocols Guide••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••11 TCP/IP Protocols••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••11 Application Layer Protocols••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••13 BOOTP: Bootstrap Protocol•••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••13 DCAP: Data Link Switching Client Access Protocol••••••••••••••••••••••••••••••••••••••••••••••••••••••14 DHCP: Dynamic Host Configuration Protocol•••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••15 DNS: Domain Name System (Service) Protocol•••••••••••••••••••••••••••••••••••••••••••••••••••••••••••16 FTP: File Transfer Protocol••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••••17 -
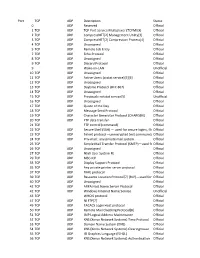
Official 2 TCP UDP Compr
Port TCP UDP Description Status 0 UDP Reserved Official 1 TCP UDP TCP Port Service Multiplexer (TCPMUX) Official 2 TCP UDP CompressNET[2] Management Utility[3] Official 3 TCP UDP CompressNET[2] Compression Process[4] Official 4 TCP UDP Unassigned Official 5 TCP UDP Remote Job Entry Official 7 TCP UDP Echo Protocol Official 8 TCP UDP Unassigned Official 9 TCP UDP Discard Protocol Official 9 UDP Wake-on-LAN Unofficial 10 TCP UDP Unassigned Official 11 TCP UDP Active Users (systat service)[5][6] Official 12 TCP UDP Unassigned Official 13 TCP UDP Daytime Protocol (RFC 867) Official 14 TCP UDP Unassigned Official 15 TCP UDP Previously netstat service[5] Unofficial 16 TCP UDP Unassigned Official 17 TCP UDP Quote of the Day Official 18 TCP UDP Message Send Protocol Official 19 TCP UDP Character Generator Protocol (CHARGEN) Official 20 TCP UDP FTP data transfer Official 21 TCP FTP control (command) Official 22 TCP UDP Secure Shell (SSH) — used for secure logins, file Officialtransfers (scp, sftp) and port forwarding 23 TCP UDP Telnet protocol—unencrypted text communicationsOfficial 24 TCP UDP Priv-mail : any private mail system. Official 25 TCP Simple Mail Transfer Protocol (SMTP)—used forOfficial e-mail routing between mail servers 26 TCP UDP Unassigned Official 27 TCP UDP NSW User System FE Official 29 TCP UDP MSG ICP Official 33 TCP UDP Display Support Protocol Official 35 TCP UDP Any private printer server protocol Official 37 TCP UDP TIME protocol Official 39 TCP UDP Resource Location Protocol*7+ (RLP)—used for determiningOfficial the location