Relationship Between Product Quality and Customer Satisfaction Albert Vitales Cruz Walden University
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Quantitative Study of Advanced Encryption Standard Performance
United States Military Academy USMA Digital Commons West Point ETD 12-2018 A Quantitative Study of Advanced Encryption Standard Performance as it Relates to Cryptographic Attack Feasibility Daniel Hawthorne United States Military Academy, [email protected] Follow this and additional works at: https://digitalcommons.usmalibrary.org/faculty_etd Part of the Information Security Commons Recommended Citation Hawthorne, Daniel, "A Quantitative Study of Advanced Encryption Standard Performance as it Relates to Cryptographic Attack Feasibility" (2018). West Point ETD. 9. https://digitalcommons.usmalibrary.org/faculty_etd/9 This Doctoral Dissertation is brought to you for free and open access by USMA Digital Commons. It has been accepted for inclusion in West Point ETD by an authorized administrator of USMA Digital Commons. For more information, please contact [email protected]. A QUANTITATIVE STUDY OF ADVANCED ENCRYPTION STANDARD PERFORMANCE AS IT RELATES TO CRYPTOGRAPHIC ATTACK FEASIBILITY A Dissertation Presented in Partial Fulfillment of the Requirements for the Degree of Doctor of Computer Science By Daniel Stephen Hawthorne Colorado Technical University December, 2018 Committee Dr. Richard Livingood, Ph.D., Chair Dr. Kelly Hughes, DCS, Committee Member Dr. James O. Webb, Ph.D., Committee Member December 17, 2018 © Daniel Stephen Hawthorne, 2018 1 Abstract The advanced encryption standard (AES) is the premier symmetric key cryptosystem in use today. Given its prevalence, the security provided by AES is of utmost importance. Technology is advancing at an incredible rate, in both capability and popularity, much faster than its rate of advancement in the late 1990s when AES was selected as the replacement standard for DES. Although the literature surrounding AES is robust, most studies fall into either theoretical or practical yet infeasible. -
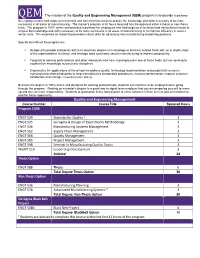
QEM the Mission of the Quality and Engineering Management
QEM The mission of the Quality and Engineering Management (QEM) program is to provide a pathway for employees who hold degrees in technical and non-technical areas to acquire the knowledge and skills necessary to be more successful in all areas of manufacturing. The master’s program is 30 hours long and has the option of either a thesis or non-thesis track. The program is 100% online and provides a pathway for employees who hold degrees in technical and nontechnical areas to acquire the knowledge and skills necessary to be more successful in all areas of manufacturing or to improve efficiency in service sector units. The emphasis on leadership provides critical skills for advancing into manufacturing leadership positions. Specific benefits of the program are: Designed to provide individuals with baccalaureate degrees in technology or business related fields with an in-depth study of the organizational, technical, and strategic tools commonly used in manufacturing to improve productivity Targeted to working professionals and other individuals who have a background in one of these fields, but are seeking to expand their knowledge across these disciplines Emphasizes the applications of these tools to address quality, technology implementation and productivity issues in manufacturing related industries to help manufacturers standardize procedures, measure performance, improve customer satisfaction and manage resources more wisely Because the degree is 100% online and designed for working professionals, students can continue to be employed while going through the program. Working on a master’s degree is a great way to signal to an employer that you are preparing yourself to move up and take on more responsibility. -

KLEIN: a New Family of Lightweight Block Ciphers
KLEIN: A New Family of Lightweight Block Ciphers Zheng Gong1, Svetla Nikova1;2 and Yee Wei Law3 1Faculty of EWI, University of Twente, The Netherlands fz.gong, [email protected] 2 Dept. ESAT/SCD-COSIC, Katholieke Universiteit Leuven, Belgium 3 Department of EEE, The University of Melbourne, Australia [email protected] Abstract Resource-efficient cryptographic primitives become fundamental for realizing both security and efficiency in embedded systems like RFID tags and sensor nodes. Among those primitives, lightweight block cipher plays a major role as a building block for security protocols. In this paper, we describe a new family of lightweight block ciphers named KLEIN, which is designed for resource-constrained devices such as wireless sensors and RFID tags. Compared to the related proposals, KLEIN has ad- vantage in the software performance on legacy sensor platforms, while its hardware implementation can be compact as well. Key words. Block cipher, Wireless sensor network, Low-resource implementation. 1 Introduction With the development of wireless communication and embedded systems, we become increasingly de- pendent on the so called pervasive computing; examples are smart cards, RFID tags, and sensor nodes that are used for public transport, pay TV systems, smart electricity meters, anti-counterfeiting, etc. Among those applications, wireless sensor networks (WSNs) have attracted more and more attention since their promising applications, such as environment monitoring, military scouting and healthcare. On resource-limited devices the choice of security algorithms should be very careful by consideration of the implementation costs. Symmetric-key algorithms, especially block ciphers, still play an important role for the security of the embedded systems. -

Performance and Energy Efficiency of Block Ciphers in Personal Digital Assistants
Performance and Energy Efficiency of Block Ciphers in Personal Digital Assistants Creighton T. R. Hager, Scott F. Midkiff, Jung-Min Park, Thomas L. Martin Bradley Department of Electrical and Computer Engineering Virginia Polytechnic Institute and State University Blacksburg, Virginia 24061 USA {chager, midkiff, jungmin, tlmartin} @ vt.edu Abstract algorithms may consume more energy and drain the PDA battery faster than using less secure algorithms. Due to Encryption algorithms can be used to help secure the processing requirements and the limited computing wireless communications, but securing data also power in many PDAs, using strong cryptographic consumes resources. The goal of this research is to algorithms may also significantly increase the delay provide users or system developers of personal digital between data transmissions. Thus, users and, perhaps assistants and applications with the associated time and more importantly, software and system designers need to energy costs of using specific encryption algorithms. be aware of the benefits and costs of using various Four block ciphers (RC2, Blowfish, XTEA, and AES) were encryption algorithms. considered. The experiments included encryption and This research answers questions regarding energy decryption tasks with different cipher and file size consumption and execution time for various encryption combinations. The resource impact of the block ciphers algorithms executing on a PDA platform with the goal of were evaluated using the latency, throughput, energy- helping software and system developers design more latency product, and throughput/energy ratio metrics. effective applications and systems and of allowing end We found that RC2 encrypts faster and uses less users to better utilize the capabilities of PDA devices. -

A Novel and Highly Efficient AES Implementation Robust Against Differential Power Analysis Massoud Masoumi K
A Novel and Highly Efficient AES Implementation Robust against Differential Power Analysis Massoud Masoumi K. N. Toosi University of Tech., Tehran, Iran [email protected] ABSTRACT been proposed. Unfortunately, most of these techniques are Developed by Paul Kocher, Joshua Jaffe, and Benjamin Jun inefficient or costly or vulnerable to higher-order attacks in 1999, Differential Power Analysis (DPA) represents a [6]. They include randomized clocks, memory unique and powerful cryptanalysis technique. Insight into encryption/decryption schemes [7], power consumption the encryption and decryption behavior of a cryptographic randomization [8], and decorrelating the external power device can be determined by examining its electrical power supply from the internal power consumed by the chip. signature. This paper describes a novel approach for Moreover, the use of different hardware logic, such as implementation of the AES algorithm which provides a complementary logic, sense amplifier based logic (SABL), significantly improved strength against differential power and asynchronous logic [9, 10] have been also proposed. analysis with a minimal additional hardware overhead. Our Some of these techniques require about twice as much area method is based on randomization in composite field and will consume twice as much power as an arithmetic which entails an area penalty of only 7% while implementation that is not protected against power attacks. does not decrease the working frequency, does not alter the For example, the technique proposed in [10] adds area 3 algorithm and keeps perfect compatibility with the times and reduces throughput by a factor of 4. Another published standard. The efficiency of the proposed method is masking which involves ensuring the attacker technique was verified by practical results obtained from cannot predict any full registers in the system without real implementation on a Xilinx Spartan-II FPGA. -

Development of the Advanced Encryption Standard
Volume 126, Article No. 126024 (2021) https://doi.org/10.6028/jres.126.024 Journal of Research of the National Institute of Standards and Technology Development of the Advanced Encryption Standard Miles E. Smid Formerly: Computer Security Division, National Institute of Standards and Technology, Gaithersburg, MD 20899, USA [email protected] Strong cryptographic algorithms are essential for the protection of stored and transmitted data throughout the world. This publication discusses the development of Federal Information Processing Standards Publication (FIPS) 197, which specifies a cryptographic algorithm known as the Advanced Encryption Standard (AES). The AES was the result of a cooperative multiyear effort involving the U.S. government, industry, and the academic community. Several difficult problems that had to be resolved during the standard’s development are discussed, and the eventual solutions are presented. The author writes from his viewpoint as former leader of the Security Technology Group and later as acting director of the Computer Security Division at the National Institute of Standards and Technology, where he was responsible for the AES development. Key words: Advanced Encryption Standard (AES); consensus process; cryptography; Data Encryption Standard (DES); security requirements, SKIPJACK. Accepted: June 18, 2021 Published: August 16, 2021; Current Version: August 23, 2021 This article was sponsored by James Foti, Computer Security Division, Information Technology Laboratory, National Institute of Standards and Technology (NIST). The views expressed represent those of the author and not necessarily those of NIST. https://doi.org/10.6028/jres.126.024 1. Introduction In the late 1990s, the National Institute of Standards and Technology (NIST) was about to decide if it was going to specify a new cryptographic algorithm standard for the protection of U.S. -

Defining the Quality of Business Processes
Defining the Quality of Business Processes Robert Heinrich1 and Barbara Paech2 Abstract: Business process models are used to gain a joint understanding of complex processes. Often they are applied in change projects where either the supporting IT or the processes themselves or both are to be improved. So it is an important question to assess the quality of the modeled business processes. However, so far there is no standard definition of the quality of a business process. Furthermore, business process models are not tuned to capture quality aspects. The goal of our work is to collect important quality characteristics and attributes of processes and to enhance business process modeling languages with means to express these attributes. This paper is a first step in this direction. We define a first set of quality characteristics, attributes and measures for these attributes in a business process. As an example we evaluate how well these measures can be expressed in a BPMN model. 1Introduction Business process models aim at providing a joint understanding of business processes. Therefore, they typically cover information about structure and behavior like description of activities or decisions within the process. But they do not aim at providing quality information. Quality information, for example, is information about the reliability or the usability of a business process. That information is of high interest for organizations because business process models are often used in change projects where either the supporting IT or the processes themselves or both are to be enhanced. Furthermore, the quality of a business process highly affects the success of an organization. -

The Importance of Sample Size in Marine Megafauna Tagging Studies
Ecological Applications, 0(0), 2019, e01947 © 2019 by the Ecological Society of America The importance of sample size in marine megafauna tagging studies 1,17 2 3 4 5 6 6 A. M. M. SEQUEIRA, M. R. HEUPEL, M.-A. LEA, V. M. EGUILUZ, C. M. DUARTE, M. G. MEEKAN, M. THUMS, 7 8 9 6 4 10 H. J. CALICH, R. H. CARMICHAEL, D. P. COSTA, L. C. FERREIRA, J. F ERNANDEZ -GRACIA, R. HARCOURT, 11 10 10,12 13,14 15 16 A.-L. HARRISON, I. JONSEN, C. R. MCMAHON, D. W. SIMS, R. P. WILSON, AND G. C. HAYS 1IOMRC and The University of Western Australia Oceans Institute, School of Biological Sciences, University of Western Australia, 35 Stirling Highway, Crawley, Western Australia 6009 Australia 2Australian Institute of Marine Science, PMB No 3, Townsville, Queensland 4810 Australia 3Institute for Marine and Antarctic Studies, University of Tasmania, 20 Castray Esplanade, Hobart, Tasmania 7000 Australia 4Instituto de Fısica Interdisciplinar y Sistemas Complejos IFISC (CSIC – UIB), E-07122 Palma de Mallorca, Spain 5Red Sea Research Centre (RSRC), King Abdullah University of Science and Technology, Thuwal 23955-6900 Saudi Arabia 6Australian Institute of Marine Science, Indian Ocean Marine Research Centre (M096), University of Western Australia, 35 Stirling Highway, Crawley, Western Australia 6009 Australia 7IOMRC and The University of Western Australia Oceans Institute, Oceans Graduate School, University of Western Australia, 35 Stirling Highway, Crawley, Western Australia 6009 Australia 8Dauphin Island Sea Lab and University of South Alabama, 101 Bienville Boulevard, Dauphin Island, Alabama 36528 USA 9Department of Ecology and Evolutionary Biology, University of California, Santa Cruz, California 95060 USA 10Department of Biological Sciences, Macquarie University, Sydney, New South Wales 2109 Australia 11Migratory Bird Center, Smithsonian Conservation Biology Institute, National Zoological Park, PO Box 37012 MRC 5503 MBC, Washington, D.C. -

State of the Art in Lightweight Symmetric Cryptography
State of the Art in Lightweight Symmetric Cryptography Alex Biryukov1 and Léo Perrin2 1 SnT, CSC, University of Luxembourg, [email protected] 2 SnT, University of Luxembourg, [email protected] Abstract. Lightweight cryptography has been one of the “hot topics” in symmetric cryptography in the recent years. A huge number of lightweight algorithms have been published, standardized and/or used in commercial products. In this paper, we discuss the different implementation constraints that a “lightweight” algorithm is usually designed to satisfy. We also present an extensive survey of all lightweight symmetric primitives we are aware of. It covers designs from the academic community, from government agencies and proprietary algorithms which were reverse-engineered or leaked. Relevant national (nist...) and international (iso/iec...) standards are listed. We then discuss some trends we identified in the design of lightweight algorithms, namely the designers’ preference for arx-based and bitsliced-S-Box-based designs and simple key schedules. Finally, we argue that lightweight cryptography is too large a field and that it should be split into two related but distinct areas: ultra-lightweight and IoT cryptography. The former deals only with the smallest of devices for which a lower security level may be justified by the very harsh design constraints. The latter corresponds to low-power embedded processors for which the Aes and modern hash function are costly but which have to provide a high level security due to their greater connectivity. Keywords: Lightweight cryptography · Ultra-Lightweight · IoT · Internet of Things · SoK · Survey · Standards · Industry 1 Introduction The Internet of Things (IoT) is one of the foremost buzzwords in computer science and information technology at the time of writing. -

The Effects of Simplifying Assumptions in Power Analysis
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Public Access Theses and Dissertations from Education and Human Sciences, College of the College of Education and Human Sciences (CEHS) 4-2011 The Effects of Simplifying Assumptions in Power Analysis Kevin A. Kupzyk University of Nebraska-Lincoln, [email protected] Follow this and additional works at: https://digitalcommons.unl.edu/cehsdiss Part of the Educational Psychology Commons Kupzyk, Kevin A., "The Effects of Simplifying Assumptions in Power Analysis" (2011). Public Access Theses and Dissertations from the College of Education and Human Sciences. 106. https://digitalcommons.unl.edu/cehsdiss/106 This Article is brought to you for free and open access by the Education and Human Sciences, College of (CEHS) at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in Public Access Theses and Dissertations from the College of Education and Human Sciences by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Kupzyk - i THE EFFECTS OF SIMPLIFYING ASSUMPTIONS IN POWER ANALYSIS by Kevin A. Kupzyk A DISSERTATION Presented to the Faculty of The Graduate College at the University of Nebraska In Partial Fulfillment of Requirements For the Degree of Doctor of Philosophy Major: Psychological Studies in Education Under the Supervision of Professor James A. Bovaird Lincoln, Nebraska April, 2011 Kupzyk - i THE EFFECTS OF SIMPLIFYING ASSUMPTIONS IN POWER ANALYSIS Kevin A. Kupzyk, Ph.D. University of Nebraska, 2011 Adviser: James A. Bovaird In experimental research, planning studies that have sufficient probability of detecting important effects is critical. Carrying out an experiment with an inadequate sample size may result in the inability to observe the effect of interest, wasting the resources spent on an experiment. -

Quality Management
DEPARTMENT OF HEALTH AND HUMAN SERVICES ENTERPRISE PERFORMANCE LIFE CYCLE FRAMEWORK <OPDIV Logo> PPPRRRAAACCCTTTIIICCCEEESSS GGGUUUIIIDDDEEE QUALITY MANAGEMENT Issue Date: <mm/dd/yyyy> Revision Date: <mm/dd/yyyy> Document Purpose This Practices Guides is a brief document that provides an overview describing the best practices, activities, attributes, and related templates, tools, information, and key terminology of industry-leading project management practices and their accompanying project management templates. This guide is focused on practices that should be applied to ensure the project will satisfy business needs, objectives, and requirements. Background The Department of Health and Human Services (HHS) Enterprise Performance Life Cycle (EPLC) is a framework to enhance Information Technology (IT) governance through rigorous application of sound investment and project management principles and industry’s best practices. The EPLC provides the context for the governance process and describes interdependencies between its project management, investment management, and capital planning components. The Quality Management Plan is an important component of a Project Management Plan deliverable. The discipline of quality management complements project management with its focus on customer satisfaction, prevention of defects over inspection, management responsibility, and continuous improvement. Practice Overview Project Managers should assume responsibility for the development of quality policies for the project and the coordination of related activities, in compliance with any organizational and/or regulatory standards. A Quality Management Plan documents this information and describes the authorities, policies, tools and techniques that are specific to ensuring project excellence, reducing cost and eliminating unnecessary corrections and/or changes. It is important to note that the concept of quality does not necessarily require perfection. -

DES and Differential Power Analysis, the Duplication Method
DES and Differential Power Analysis The “Duplication” Method? Louis Goubin, Jacques Patarin Bull SmartCards and Terminals 68, route de Versailles - BP45 78431 Louveciennes Cedex - France {L.Goubin, J.Patarin}@frlv.bull.fr Abstract. Paul Kocher recently developped attacks based on the elec- tric consumption of chips that perform cryptographic computations. A- mong those attacks, the “Differential Power Analysis” (DPA) is probably one of the most impressive and most difficult to avoid. In this paper, we present several ideas to resist this type of attack, and in particular we develop one of them which leads, interestingly, to rather precise mathematical analysis. Thus we show that it is possible to build an implementation that is provably DPA-resistant, in a “local” and re- stricted way (i.e. when – given a chip with a fixed key – the attacker only tries to detect predictable local deviations in the differentials of mean curves). We also briefly discuss some more general attacks, that are sometimes efficient whereas the “original” DPA fails. Many measures of consumption have been done on real chips to test the ideas presented in this paper, and some of the obtained curves are printed here. Note: An extended version of this paper can be obtained from the authors. 1 Introduction This paper is about a way of securing a cryptographic algorithm that makes use of a secret key. More precisely, the goal consists in building an implementation of the algorithm that is not vulnerable to a certain type of physical attacks – so-called “Differential Power Analysis”. These DPA attacks belong to a general family of attacks that look for infor- mation about the secret key by studying the electric consumption of the elec- tronic device during the execution of the computation.