Automated Malware Analysis Report for Setup.Exe
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft and Cray to Unveil $25,000 Windows-Based Supercomputer
AAll About Microsoft: l lCodeTracker A monthly look at Microsoft’s codenames and what they Areveal about the direction of the company. b o u t M i c r o s o f t : All About Microsoft CodeTracker Keeping track of Microsoft's myriad codenames is an (almost) full-time occupation. I know, as I spend a lot of my work hours tracking down the latest names in the hopes of being able to better keep tabs on what's coming next from the Redmondians. Each month, I'll be releasing an updated, downloadable version of the CodeTracker. I'll add new codenames -- arranged in alphabetical order by codename -- of forthcoming Microsoft products and technologies. I also will note timing changes (date slips, the release of a new test build, the disappearance of a planned deliverable) for entries that are already part of the Tracker. Once Microsoft releases the final version of a product or technology I've been tracking, I will remove it from the Tracker. In that way, the CodeTracker will remain focused on futures. (An aside about the Tracker: A question mark in place of an entry means I have insufficient information to hazard even an educated guess about a particular category.) If you have suggested new entries or corrections to existing ones, please drop me an e-mail at mjf at microsofttracker dot com. Thanks! Mary Jo Foley, Editor, ZDNet's "All About Microsoft" blog This Month's Theme: Big iron needs love, too If you went by nothing but blog and publication headlines, you might think mobile phones and slates are where all the innovation is these days. -

Discovery Attender User Guide
Welcome Sherpa Software's Discovery Attender is a software tool designed to automate the search and collection of electronically stored information across a variety of platforms. This dynamic solution sits behind the firewall and enables in-house talent to identify and gather responsive information in a timely, defensible manner. The Discovery Attender interface is designed to be intuitive and user friendly. The Welcome Screen (above) serves as the gateway to the product. From here you can directly open the PreSearch Tool or create a project. A project serves as a repository for a collection - related searches and associated result sets. Once a new pro- ject is created, the MAIN CONSOLE acts as the central hub to allow you to control the creation, processing, and organization of searches. From here, you can access a Search Wizard which guides you through the step-by- step process of creating a new search. The MAIN CONSOLE also provides access to the Result Management features to view, organize, export and report on the messages, attachments and files that are found during your custom searches. Where to Begin To effectively filter and produce data with Discovery Attender, you must first create a project . Once a project is created, follow the steps below to begin the process: Step Action Description 1 Create and Run A Search A setup wizard leads you through the process of selecting locations and criteria to include in your search. Once started, the chosen data stores are scanned to find items (called results) that match the selected criteria. Information and metadata from these results are stored in the search data- bases. -

Software License Agreement (EULA)
Third-party Computer Software AutoVu™ ALPR cameras • angular-animate (https://docs.angularjs.org/api/ngAnimate) licensed under the terms of the MIT License (https://github.com/angular/angular.js/blob/master/LICENSE). © 2010-2016 Google, Inc. http://angularjs.org • angular-base64 (https://github.com/ninjatronic/angular-base64) licensed under the terms of the MIT License (https://github.com/ninjatronic/angular-base64/blob/master/LICENSE). © 2010 Nick Galbreath © 2013 Pete Martin • angular-translate (https://github.com/angular-translate/angular-translate) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • angular-translate-handler-log (https://github.com/angular-translate/bower-angular-translate-handler-log) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • angular-translate-loader-static-files (https://github.com/angular-translate/bower-angular-translate-loader-static-files) licensed under the terms of the MIT License (https://github.com/angular-translate/angular-translate/blob/master/LICENSE). © 2014 [email protected] • Angular Google Maps (http://angular-ui.github.io/angular-google-maps/#!/) licensed under the terms of the MIT License (https://opensource.org/licenses/MIT). © 2013-2016 angular-google-maps • AngularJS (http://angularjs.org/) licensed under the terms of the MIT License (https://github.com/angular/angular.js/blob/master/LICENSE). © 2010-2016 Google, Inc. http://angularjs.org • AngularUI Bootstrap (http://angular-ui.github.io/bootstrap/) licensed under the terms of the MIT License (https://github.com/angular- ui/bootstrap/blob/master/LICENSE). -

Focus Type Applies To
Focus Type Applies To All Power Tools All All Power Tools Team Foundation Server All Templates Team Foundation Server All Integration Provider Team Foundation Server All Power Tools Team Foundation Server All Power Tools Team Foundation Server All Integration Provider Team Foundation Server Architecture Power Tools Visual Studio Architecture Power Tools Visual Studio Architecture Templates Visual Studio Architecture Integration Provider Oracle Architecture Templates Expression Builds Power Tools Team Foundation Server Builds Integration Provider Visual Studio Builds Power Tools Team Foundation Server Builds Templates Team Foundation Server Builds Power Tools Team Foundation Server Builds Power Tools Team Foundation Server Builds Power Tools Team Foundation Server Coding Power Tools Visual Studio Coding Integration Provider Visual Studio Coding Azure Integration Visual Studio Coding Integration Provider Dynamics CRM Coding Documentation Visual Studio Coding Integration Provider Visual Studio Coding Templates Visual Studio Coding Documentation Visual Studio Coding Templates SharePoint Coding Templates SharePoint Coding Integration Provider Visual Studio Coding Integration Provider Visual Studio Coding Templates SharePoint Coding Power Tools Visual Studio Coding Power Tools Visual Studio Coding Templates SharePoint Coding Templates Visual Studio Coding Templates Visual Studio Coding Templates Visual Studio Coding Power Tools Visual Studio Coding Integration Provider SharePoint Coding Templates Visual Studio Coding Templates SharePoint Coding -

Introducing Microsoft SQL Server 2014 Technical Overview
Introducing Windows 8.1 for IT Professionals Introducing Introducing Windows 8.1 for IT Professionals Get a head start evaluating Windows 8.1—with early technical Note insights from award-winning journalist and Windows expert Ed This title is also available as a free Bott. This guide introduces new features and capabilities, providing eBook from Microsoft at: a practical, high-level overview for IT professionals ready to begin http://aka.ms/mspressfree deployment planning now. About the Author Preview new features and enhanced capabilities, Ed Bott is an award-winning journalist including: known to millions of readers through two decades of writing for leading • The Windows 8.1 user experience industry publications and more than 25 • Deployment tools and technologies books on Microsoft Office and Windows, • Security features including Windows 7 Inside Out and • Internet Explorer 11 Microsoft Office Inside Out: 2013 Edition. • Delivering Windows Store apps • Recovery options • Networking and remote access • Virtualization Introducing • Windows RT 8.1 • Managing mobile devices Also see Microsoft SQL Server 2014 Windows 8.1 Administration Microsoft Office Pocket Consultant Inside Out Essentials & Configuration 2013 Edition ISBN: 9780735682658 ISBN: 9780735669062 Storage, Security, & Networking Technical Overview ISBN: 9780735682610 U.S.A. $9.99 Canada $10.99 [Recommended] n Operating Systems/Windows Celebrating 30 years! ROSS MISTRY STACIA MISNER PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2014 by Microsoft Corporation All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. -

Meridium V3.6X Open Source Licenses (PDF Format)
Open Source Components Component Version License License Link Usage Home Page .NET Zip Library Unspecified SharpZipLib GPL License (GPL w/exception) http://www.icsharpcode.net/opensource/sharpziplib/ Dynamic Library http://dotnetziplib.codeplex.com/ 32feet.NET Unspecified Microsoft Public License http://opensource.org/licenses/MS-PL File + Dynamic Library http://32feet.codeplex.com AjaxControlToolkit Unspecified Microsoft Public License http://opensource.org/licenses/MS-PL Dynamic Library http://ajaxcontroltoolkit.codeplex.com/ Android - platform - external - okhttp 4.3_r1 Apache License 2.0 http://www.apache.org/licenses/LICENSE-2.0.html File http://developer.android.com/index.html angleproject Unspecified BSD 3-clause "New" or "Revised" License http://opensource.org/licenses/BSD-3-Clause Dynamic Library http://code.google.com/p/angleproject/ Apache Lucene - Lucene.Net 3.0.3-RC2 Apache License 2.0 http://www.apache.org/licenses/LICENSE-2.0.html Dynamic Library http://lucenenet.apache.org/ AttributeRouting (ASP.NET Web API) 3.5.6 MIT License http://www.opensource.org/licenses/mit-license.php File http://www.nuget.org/packages/AttributeRouting.WebApi AttributeRouting (Self-hosted Web API) 3.5.6 MIT License http://www.opensource.org/licenses/mit-license.php File http://www.nuget.org/packages/AttributeRouting.WebApi.Hosted AttributeRouting.Core 3.5.6 MIT License http://www.opensource.org/licenses/mit-license.php Component http://www.nuget.org/packages/AttributeRouting.Core AttributeRouting.Core.Http 3.5.6 MIT License http://www.opensource.org/licenses/mit-license.php -

NET Technology Guide for Business Applications // 1
.NET Technology Guide for Business Applications Professional Cesar de la Torre David Carmona Visit us today at microsoftpressstore.com • Hundreds of titles available – Books, eBooks, and online resources from industry experts • Free U.S. shipping • eBooks in multiple formats – Read on your computer, tablet, mobile device, or e-reader • Print & eBook Best Value Packs • eBook Deal of the Week – Save up to 60% on featured titles • Newsletter and special offers – Be the first to hear about new releases, specials, and more • Register your book – Get additional benefits Hear about it first. Get the latest news from Microsoft Press sent to your inbox. • New and upcoming books • Special offers • Free eBooks • How-to articles Sign up today at MicrosoftPressStore.com/Newsletters Wait, there’s more... Find more great content and resources in the Microsoft Press Guided Tours app. The Microsoft Press Guided Tours app provides insightful tours by Microsoft Press authors of new and evolving Microsoft technologies. • Share text, code, illustrations, videos, and links with peers and friends • Create and manage highlights and notes • View resources and download code samples • Tag resources as favorites or to read later • Watch explanatory videos • Copy complete code listings and scripts Download from Windows Store Free ebooks From technical overviews to drilldowns on special topics, get free ebooks from Microsoft Press at: www.microsoftvirtualacademy.com/ebooks Download your free ebooks in PDF, EPUB, and/or Mobi for Kindle formats. Look for other great resources at Microsoft Virtual Academy, where you can learn new skills and help advance your career with free Microsoft training delivered by experts. -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -

The Work of Microsoft Research Connections in the Region
• To tell you more about Microsoft Research Connections • Global • EMEA • PhD Programme • Other engagements • • • Microsoft Research Connections Work broadly with the academic and research community to speed research, improve education, foster innovation and improve lives around the world. Accelerate university Support university research and research through education through collaborative technology partnerships investments Inspire the next Drive awareness generation of of Microsoft researchers and contributions scientists to research Engagement and Collaboration Focus Core Computer Natural User Earth Education and Health and Science Interface Energy Scholarly Wellbeing Environment Communication Research Accelerators Global Partnerships People • • • • • • • • • • • • • • Investment Focus Education & Earth, Energy, Health & Computer Science Scholarly and Environment Wellbeing Communication Programming, Natural User WW Telescope, Academic Search, MS Biology Tools, Mobile Interfaces Climate Change Digital Humanities, Foundation & Tools Earth Sciences Publishing Judith Bishop Kris Tolle Dan Fay Lee Dirks Simon Mercer Regional Outreach/Engagements EMEA: Fabrizio Gagliardi LATAM: Jaime Puente India: Vidya Natampally Asia: Lolan Song America/Aus/NZ: Harold Javid Engineering High-quality and high-impact software release and community adoption Derick Campbell CMIC EMIC ILDC • • . New member of MSR family • • • . Telecoms, Security, Online services and Entertainment Microsoft Confidential Regional Collaborations at Joint Institutes INRIA, FRANCE -
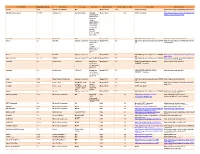
Third Party Version
Third Party Name Third Party Version Manufacturer License Type Comments Merge Product Merge Product Versions License details Software source autofac 3.5.2 Autofac Contributors MIT Merge Cardio 10.2 SOUP repository https://www.nuget.org/packages/Autofac/3.5 .2 Gibraltar Loupe Agent 2.5.2.815 eSymmetrix Gibraltor EULA Gibraltar Merge Cardio 10.2 SOUP repository https://my.gibraltarsoftware.com/Support/Gi Loupe Agent braltar_2_5_2_815_Download will be used within the Cardio Application to view events and metrics so you can resolve support issues quickly and easily. Modernizr 2.8.3 Modernizr MIT Merge Cadio 6.0 http://modernizr.com/license/ http://modernizr.com/download/ drools 2.1 Red Hat Apache License 2.0 it is a very old Merge PACS 7.0 http://www.apache.org/licenses/LICENSE- http://mvnrepository.com/artifact/drools/dro version of 2.0 ols-spring/2.1 drools. Current version is 6.2 and license type is changed too drools 6.3 Red Hat Apache License 2.0 Merge PACS 7.1 http://www.apache.org/licenses/LICENSE- https://github.com/droolsjbpm/drools/releases/ta 2.0 g/6.3.0.Final HornetQ 2.2.13 v2.2..13 JBOSS Apache License 2.0 part of JBOSS Merge PACS 7.0 http://www.apache.org/licenses/LICENSE- http://mvnrepository.com/artifact/org.hornet 2.0 q/hornetq-core/2.2.13.Final jcalendar 1.0 toedter.com LGPL v2.1 MergePacs Merge PACS 7.0 GNU LESSER GENERAL PUBLIC http://toedter.com/jcalendar/ server uses LICENSE Version 2. v1, and viewer uses v1.3. -

Tutorials for Project on Building a Business Analytic Model Using Data Warehouse and OLAP Cubes
Cleveland State University Tutorials for Project on Building a Business Analytic Model Using Data Warehouse and OLAP Cubes Sunnie S. Chung Cleveland State University 14 Sunnie S Chung Phase 1: Preparation of Labs/Project 1. Downloads and Installations 1. Visual Studio 2012/2014 or higher 2. SQL Server 2012/2014 or higher 3. Microsoft SQL Server Data Tools - Business Intelligence for Visual Studio 2012/2014 or higher 4. Adventure Works (Data Warehouse) for SQL Server 2012/2014 For download and installation instructions: Downloading and Installation Guides and Set up Instructions are available on the class webpage. You can access each class webpage from my webpage: http://grail.csuohio.edu/~sschung/ Or https://msdn.microsoft.com/en-US/library/jj856966(v=sql.120).aspx After successful installations, 1. Open Visual Studio 2. File -> New Project 3. You should see following BI add-ons which lets you create Data mining projects. a. Analysis Service b. Integration Service c. Reporting Service Sunnie S Chung PHASE 2: Downloading and Setting up a Sample Database/DW Adventure Works 2012 (or 2014) Data Warehouse for SQL Server 2012/2014 1. Go to Microsoft CodePlex site: 2. For Adventure Works DW Databases – 2012 http://msftdbprodsamples.codeplex.com/ 3. For Adventure Works DW Databases – 2014 http://msftdbprodsamples.codeplex.com/releases/ 4. Download Adventure Works DW Databases – 2012 or higher Choose Either 2012 SQL Server DW 2012/2014 or 2012 SQL Server OLAP 2012/2014 Sunnie S Chung 5. Restore database in SQL Server 2012/2014. 6. There are two -

Automating Problem Analysis and Triage Sasha Goldshtein @Goldshtn Production Debugging
Automating Problem Analysis and Triage Sasha Goldshtein @goldshtn Production Debugging Requirements Limitations • Obtain actionable • Can’t install Visual information about Studio crashes and errors • Can’t suspend • Obtain accurate production servers performance • Can’t run intrusive information tools In the DevOps Process… Automatic build (CI) Automatic Automatic deployment remediation (CD) Automatic Automatic error triage monitoring and analysis Dump Files Dump Files • A user dump is a snapshot of a running process • A kernel dump is a snapshot of the entire system • Dump files are useful for post-mortem diagnostics and for production debugging • Anytime you can’t attach and start live debugging, a dump might help Limitations of Dump Files • A dump file is a static snapshot • You can’t debug a dump, just analyze it • Sometimes a repro is required (or more than one repro) • Sometimes several dumps must be compared Taxonomy of Dumps • Crash dumps are dumps generated when an application crashes • Hang dumps are dumps generated on-demand at a specific moment • These are just names; the contents of the dump files are the same! Generating a Hang Dump • Task Manager, right- click and choose “Create Dump File” • Creates a dump in %LOCALAPPDATA%\Te mp Procdump • Sysinternals utility for creating dumps • Examples: Procdump -ma app.exe app.dmp Procdump -ma -h app.exe hang.dmp Procdump -ma -e app.exe crash.dmp Procdump -ma -c 90 app.exe cpu.dmp Procdump -m 1000 -n 5 -s 600 -ma app.exe Windows Error Reporting • WER can create dumps automatically