Applications That Facilitate Teamwork
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Parental Control – Whatsapp
Parental controls guide WhatsApp privacy guide Parental Controls information Type of guide Social media privacy guides Features and Benefits WhatsApp privacy settings allow you to restrict who can see your child’s messages and location. There are also ways to block delete or report users on the platform. Please note, WhatsApp new privacy policy has come into effect starting May 15. What specific content can I restrict? Chatting Downloading file sharing Location sharing Privacy Privacy and identity theft What do I need? A WhatsApp account WhatsApp privacy guide Step by step guide 1 Control who sees your information You can set your last seen, profile photo and/or status to the following options: Everyone, My Contacts and Nobody: 1. Open WhatsApp and go to your Settings, tap Account, then tap Privacy. 2. Next, tap your selected option, then choose from either option: ‘Everyone’, ‘My Contacts’ or ‘Nobody’. 3. The changes will be applied automatically. 1 WhatsApp privacy guide 2 3 WhatsApp privacy guide Step by step guide 2 How to block contacts You can stop receiving messages, calls and status updates from certain contacts by blocking them. Open WhatsApp, choose the person you want to block either by searching or scrolling through your chat list. 2. Tap on their name, then scroll down and tap Block Contact. 1 2 WhatsApp privacy guide WhatsApp privacy guide Step by step guide 3 How to report contacts 1. Open WhatsApp, choose the person you want to report either by searching or scrolling through your chat list. 2. Tap on their name, then scroll down and tap Report or Report and Block Contact. -

Enterprise Edition
Secure Communication. Simplified. SAFECHATS Problem Most companies use popular insecure email and ⛔ messaging services to communicate confidential information P The information flow within the Company is ⛔ disorganized Metadata is exposed and available to third-party ⛔ services SAFECHATS Introducing SAFECHATS Ultra-secure communication solution P Designed with security in mind SAFECHATS Why SAFECHATS? ✔ Information is always end-to-end encrypted by default P ✔ All-in-one communication suite: • Text messaging (one-on-one and group chats) • Voice calls • File transfers (no size and file type limits) SAFECHATS How does SAFECHATS solve the problem? ✔ Customizable white label solution ✔ Integrates with existing softwareP infrastructure ✔ Enterprise-wide account and contact list management, supervised audited chats for compliance SAFECHATS What makes SAFECHATS different? ✔ Your own isolated cloud environment or on-premise deployment P ✔ Customizable solution allows to be compliant with internal corporate security policies ✔ No access to your phone number and contact list SAFECHATS Screenshot Protection ✔ Notifications on iOS P ✔ DRM protection on Android SAFECHATS Identity Verification ✔ Protection from man-in-the-middle attacksP ✔ SMP Protocol SAFECHATS Privacy Features ✔ Show / hide messages and files P ✔ Recall messages and files ✔ Self-destructing messages and files SAFECHATS Additional Protection ✔ History retention control P ✔ Application lock: • PIN-code • Pattern-lock on Android devices • Touch ID on iOS devices SAFECHATS How does SAFECHATS -

How Secure Is Textsecure?
How Secure is TextSecure? Tilman Frosch∗y, Christian Mainkay, Christoph Badery, Florian Bergsmay,Jorg¨ Schwenky, Thorsten Holzy ∗G DATA Advanced Analytics GmbH firstname.lastname @gdata.de f g yHorst Gortz¨ Institute for IT-Security Ruhr University Bochum firstname.lastname @rub.de f g Abstract—Instant Messaging has gained popularity by users without providing any kind of authentication. Today, many for both private and business communication as low-cost clients implement only client-to-server encryption via TLS, short message replacement on mobile devices. However, until although security mechanisms like Off the Record (OTR) recently, most mobile messaging apps did not protect confi- communication [3] or SCIMP [4] providing end-to-end con- dentiality or integrity of the messages. fidentiality and integrity are available. Press releases about mass surveillance performed by intelli- With the advent of smartphones, low-cost short-message gence services such as NSA and GCHQ motivated many people alternatives that use the data channel to communicate, to use alternative messaging solutions to preserve the security gained popularity. However, in the context of mobile ap- and privacy of their communication on the Internet. Initially plications, the assumption of classical instant messaging, fueled by Facebook’s acquisition of the hugely popular mobile for instance, that both parties are online at the time the messaging app WHATSAPP, alternatives claiming to provide conversation takes place, is no longer necessarily valid. secure communication experienced a significant increase of new Instead, the mobile context requires solutions that allow for users. asynchronous communication, where a party may be offline A messaging app that claims to provide secure instant for a prolonged time. -

Ethics of Facebook: Analyzing the Social Network and Global Leader
Ethics of Facebook: Analyzing the Social Network and Global Leader A Thesis Submitted to the Faculty of the School of Engineering and Applied Science University of Virginia • Charlottesville, Virginia In Partial Fulfillment of the Requirements of the Degree Bachelor of Science, School of Engineering Selwyn Hector Spring 2020 On my honor as a University Student, I have neither given nor received unauthorized aid on this assignment as defined by the Honor Guidelines for Thesis-Related Assignments Signature __________________________________________ Date __________ Selwyn Hector Approved __________________________________________ Date __________ Michael Gorman, Department of Engineering and Society Ethics of Facebook: Analyzing the Social Network and Global Leader Introduction As computing technology has grown, the internet and computers have become an essential part of people’s daily lives. According to data from the US Census, 81% of United States homes had a computer with internet access in 2016 and 76% of households had at least 1 one smartphone. Facebook is one of the internet’s largest services with 1.59 billion daily active 2 users and 2.41 billion monthly active users as of June 2019. Facebook’s massive user base gives it a platform to influence many parts of the world. Facebook began as a platform for connecting college students but now is a behemoth in entertainment, news, advertising, and more. Small decisions in how content is prioritized and what content is allowed to be posted have consequences across many cultures. This enormous power makes Facebook not only a social network that connects friends but a global leader that shapes the future. Unfortunately, the platform has been at the center of many controversies related to user 3,4 privacy, misinformation, and hate speech. -

What Is Whatsapp? Whatsapp Is a Mobile Phone Application That Allows Users to Send Messages to Individuals and Groups, As Well As Share Images and Documents
What is WhatsApp? WhatsApp is a mobile phone application that allows users to send messages to individuals and groups, as well as share images and documents. WhatsApp is a useful tool when you want to communicate with a group—such as all the nurses on your unit. It is less cumbersome than starting a texting group using everyone’s personal mobile phone. How to set up WhatsApp on your mobile phone Go to the App Store for your iPhone or Open Google Play on your Android Install “WhatsApp” Once you have the App on your phone: Go to “Settings” and add a photo and a status message (optional) The App will draw from directly your contacts in your phone and identified people who have WhatsApp How to set up a group chat Open WhatsApp On the bottom of the screen there are options to make calls, send texts etc. Click on the Chat Bubble which will take you to the screen where you message with your contacts From here there are two ways of creating a new group: Click on NEW GROUP on the top right of your screen This will take you to your contact list. Type a name in the search bar at top, or go down the list and tap everyone you would like in the group (a little blue check will show up next to their name). Click NEXT The next page is where you can give your group a name, and add a picture that represents the group (optional) SECOND WAY TO CREATE A GROUP CHAT: Back on the main chat page, you can click on the icon of a note being written all the way at the top right of the page Which will take to the next page offering you the option of creating a new group. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Portable Wi-Fi Calling and Interactive Voice Response System
www.ijemr.net ISSN (ONLINE): 2250-0758, ISSN (PRINT): 2394-6962 Volume-7, Issue-1, January-February 2017 International Journal of Engineering and Management Research Page Number: 384-386 Portable Wi-Fi Calling and Interactive Voice Response System Ruchi W. Kasare1, Pooja K. Muneshwar2, Nikhil D. Tembhekar3, Prof. V. P. Yadav4, Prof. J. V. Shriral5 1,2,3,4,5Department of Computer Science and Engineering, Priyadarshani College of Engineering and Research, Nagpur University, Maharashtra, INDIA ABSTRACT Wireless IP-PBX utilizes WIFI technology for Implementation of a VoIP telephony system using communication, the same wireless infrastructure used for an IP Telephony solution in the organization as IVR. A new your corporate network. Just as we use mobiles and technology VoIP or Internet Telephony means that your laptops within this wireless infrastructure to gain access voice is carried over the IP network, otherwise known as to information, now we can use wireless IP phones the Internet. Voice which is an analog signal, is converted system as this system uses the telephony function to digital data, which is then disassembled and transmitted through the Internet or Internet to be recovered back to an directly into an already existing data network. This analog signal an the other using an IP Telephony solution provides an advantage that voice and data network can which is an Linux base system. be used together using single system. One of the major This service can be properly managed and advantages of the IP-PBX wireless phone is that you can deployed over a network with less stress and expenses. -

National Security Agency | Cybersecurity Information Selecting
National Security Agency | Cybersecurity Information Selecting and Safely Using Collaboration Services for Telework - UPDATE Summary During a global pandemic or other crisis contingency scenarios, many United States Government (USG) personnel must operate from home while continuing to perform critical national functions and support continuity of government services. With limited access to government furnished equipment (GFE) such as laptops and secure smartphones, the use of (not typically approved) commercial collaboration services on personal devices for limited government official use becomes necessary and unavoidable. We define collaboration services as those capabilities that allow the workforce to communicate via internet-enabled text, voice, and video, and can include the sharing of files and other mission content. Collaboration can occur between two people or widened to include a large group to support mission needs. This document provides a snapshot of best practices and criteria based on capabilities available at the time of publication and was coordinated with the Department of Homeland Security (DHS), which has released similar guidance: “Cybersecurity Recommendations for Federal Agencies Using Video Conferencing” [1] and “Guidance for Securing Video Conferencing” [2]. This NSA publication is designed to provide simple and actionable considerations for individual government users. The intent of this document is not meant to be exhaustive or based on formal testing, but rather be responsive to a growing demand amongst the federal government to allow its workforce to operate remotely using personal devices when deemed to be in the best interests of the health and welfare of its workforce and the nation. Recommendations in this document are likely to change as collaboration services evolve and also address known vulnerabilities and threats. -
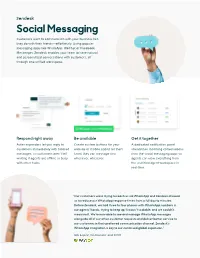
Social Messaging Customers Want to Communicate with Your Business Like They Do with Their Friends—Effortlessly
Social Messaging Customers want to communicate with your business like they do with their friends—effortlessly. Using popular messaging apps like WhatsApp, WeChat or Facebook Messenger, Zendesk enables your team to have natural and personalized conversations with customers, all through one unified workspace. Respond right away Be available Get it together Auto-responders let you reply to Create custom buttons for your A dedicated notification panel customers immediately with tailored website or mobile app to let them streamlines incoming conversations messages, so customers aren’t left know they can message you from the social messaging apps so waiting if agents are offline or busy whenever, wherever. agents can view everything from with other tasks. the a unified agent workspace in real-time. “Our customers were trying to reach us via WhatsApp and Zendesk allowed us to reduce our WhatsApp response times from a full day to minutes. Before Zendesk, we had three to four phones with WhatsApp numbers in our agents’ hands, trying to keep up. It wasn’t scalable, and we couldn’t measure it. We’re now able to see and manage WhatsApp messages alongside all of our other customer requests and deliver better service to our customers in their preferred communication channel. Zendesk’s WhatsApp integration is key to our continued global expansion.” Gib Lopez, Co-founder and COO Build meaningful Make it easy for your An effortless addition relationships agents Connect quickly and easily, Connect with customers on their Manage interactions across enabling your teams to up their preferred messaging apps. channels using a single, agent productivity using their existing workspace. -

The Leading Secure Communication & Collaboration Platform
pro The Leading Secure Communication & Collaboration Platform Security Wickr Pro is a user-friendly collaboration platform built with security first. Whether you are messaging, on a call, holding video conferences, file sharing, or using any of our other features, your communications are completely protected by our uncompromised, advanced security protocols. Compliance Wickr Pro allows you to secure all of your communications while still remaining compliant with industry regulations. You are in charge of what information is kept and what is automatically deleted with our expiration and burn-on-read timers. As you collaborate within Wickr, your communications and your customers’ data can remain secure. Control Wickr Pro gives you full administrative control over your network. Our security measures are customizable to your needs, so you can decide who has access to what data, set up security protocols, and be alerted if someone is out of network. "Given the multitude of attacks and access to communications solutions, enterprises need to deploy, manage and have flexible administrative controls to not only secure sensitive communications, but follow best practices for retaining information as required. Wickr is the only product that offers this through strong encryption, deployment options and selective controls." Joe Sullivan Former CSO of Facebook, Uber, and Cloudfare pro Features & Capabilities 1:1 and Group Audio and Video Screen Sharing and File Sharing and Messaging Calling Broadcasting Saving Create secure rooms with Conference with up -

Battery and Data Drain of Over-The-Top Applications on Low-End Smartphones
CORE Metadata, citation and similar papers at core.ac.uk Provided by University of the Western Cape Research Repository IST-Africa 2018 Conference Proceedings Paul Cunningham and Miriam Cunningham (Eds) IIMC International Information Management Corporation, 2018 ISBN: 978-1-905824-59-5 Battery and Data Drain of Over-The-Top Applications on Low-end Smartphones Shree Om1, William D. Tucker2 University of the Western Cape, Robert Sobukwe Road, Cape Town, 7535, South Africa1,2 Tel: +27 21 959 3010, Fax: +27 21 959 1274, Email: [email protected] 1, [email protected] 2 Abstract: Low-end smartphones with sub $50 price tags provide affordable device ownership to low-income populations. However, their limited capacity, when combined with the need for multimodal connectivity, raises usage concerns in rural off-grid regions. Some off-grid regions in sub-Saharan Africa provide recharge facilities using solar power and charge money for the service. Adding data bundle costs to frequent recharge costs, affordability of low-end smartphones becomes questionable in such areas. Community-controlled solar-powered wireless mesh network models with Session Initiation Protocol capability could alleviate the network usage cost conundrum and consume less power in low-end smartphones with the usage of WiFi. This paper reports on investigations that reveal usage of WiFi consumes less battery than 3G, 2G and Bluetooth. In addition, we feel that lowering recharge costs also requires battery consumption knowledge of the over- the-top applications. Using automated voice calls, this paper reports on battery and data consumption by multiple popular social media applications using one type of low-end smartphone. -

Conversational Commerce on Instant Messaging Apps
CONVERSATIONAL COMMERCE ON INSTANT MESSAGING APPS WHITEPAPER Table of Content Summary 3 Key Takeaways 3 What is Conversational Commerce? 3 Rise of Instant Messaging Apps 3 Industry Landscape 4 Solution & Benefits 4 Conclusion 5 References 5 Author 6 Abstract Today consumers are spending most of their time on instant messaging apps such as WhatsApp, Facebook Messenger, WeChat, etc. These apps provide a great opportunity for brands to connect intimately with consumers and establish it as an alternate channel for shopping. By facilitating AI-powered chatbots on messaging apps helps brands resolve customer queries and enable purchasing & sales requests. Also, it can be a key source for personalized shopping. Chatbots automates customer conversations and helps in building a strong relationship with them. Key takeaways. Conversational commerce current Popular use cases that can be 1 trends and future scope 4 implemented on instant messaging platforms – Conversational Ordering, customer support, and personalized Instant Messaging Apps – Overview, selling 2 platforms, geography-wise usage, customer journey, and brand Tech Mahindra capabilities and interaction 5 partner ecosystem - integrated commerce solution on instant Scope for Retail and CG Industry, messaging apps. 3 Industry examples, consumer preferences What is Conversational Commerce? Rise of Instant Messaging Apps Conversational commerce is the intersection of Instant messaging apps are the preferred means of messaging apps (Facebook Messenger, WhatsApp, communication worldwide, there are over 2 billion Instagram, WeChat) or voice-assisted apps (Alexa, users on WhatsApp, 900 million active users on Google Home, Amazon Echo) with shopping. It uses Facebook Messenger, and 700 million users on AI-based chatbots in interacting with customers and WeChat worldwide.