Frequently Asked Questions Frequently Asked Questions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The NT Insider May-June 2016
; The commandments of x64 assembly: ; ; 1. Thou Shalt Not Write Inline Assembly ; 2. Thou Shalt Generate Unwind Data ; 3. Thou Shalt Comment Each Line of Assembly ; include macamd64.inc ; ; External C function to read an article ; ; NTSTATUS ; TheNTInsiderReadSingleArticle( ; PCHAR ArticleDescription, ; ULONG_PTR PageNumber, ; ); ; EXTERN TheNTInsiderReadSingleArticle:PROC .DATA PeterPontificates BYTE "COMPUTER SCIENCE EDUCATION? (YUP, STILL SUCKS)", 0 NewWaysToConnect BYTE "INTRODUCTION TO SIMPLE PERIPHERAL BUS DEVICES AND DRIVERS", 0 TipsForUsingIoTargets BYTE "A FEW RULES TO MAKE YOUR USE OF I/O TARGETS SIMPLE", 0 TodayInDriverSigning BYTE "COLOR ME CONFUSED (STILL. AGAIN.)", 0 AnalystsPerspective BYTE "MY DRIVER PASSES DRIVER VERIFIER! (OR DOES IT…)", 0 ByeByeCoInstallers BYTE "SURPRISE? NEW VERSIONS OF WDF NO LONGER SUPPORTED DOWNLEVEL", 0 .CODE NESTED_ENTRY TheNTInsiderReadEntireIssue, _TEXT save_reg rcx, 8h ; Home RCX save_reg rdx, 10h ; Home RDX save_reg r8, 18h ; Home R8 save_reg r9, 20h ; Home R9 alloc_stack 20h ; Make home space for TheNTInsiderReadSingleArticle END_PROLOGUE ; We are done manipulating the stack, so emit the ; appropriate unwind stuff lea rcx, [PeterPontificates] ; We're about to read the first article mov rdx, 4 ; Put page number in RDX. I realize this comment ; isn't useful, but I'm supposed to comment every ; line... call TheNTInsiderReadSingleArticle ; Read the article! test eax, eax ; Returns an NTSTATUS, so check SF js Exit ; If it's set there's an error and we need to leave lea rcx, [NewWaysToConnect] ; Time for the second article! mov rdx, 6 ; Do what I did last time call TheNTInsiderReadSingleArticle ; Read the next article! test eax, eax ; Testin'... js Exit ; And jumpin'... A publication of OSR Open Systems Resources, Inc. Resources, Systems Open OSR of A publication lea rcx, [TipsForUsingIoTargts] ; Let's read another article! mov rdx, 8 ; TODO: Learn to write a MASM loop.. -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -

1 Table of Contents List of Figures
Table of Contents List of Figures ..................................................................................................................... 4 List of Tables ...................................................................................................................... 5 Chapter 1: Introduction....................................................................................................... 6 1.1 Introduction....................................................................................................................6 1.2 Problem Statement .......................................................................................................12 1.3 Thesis Objective...........................................................................................................12 1.4 Thesis Organization.....................................................................................................14 Chapter 2: Intrusion Detection.......................................................................................... 15 2.1 Introduction..................................................................................................................15 2.2 What is an IDS .............................................................................................................15 2.2.1 The Basic Concepts of Intrusion Detection......................................................16 2.2.2 A Generic Intrusion-Detection System.............................................................17 2.2.3 Characteristics of -
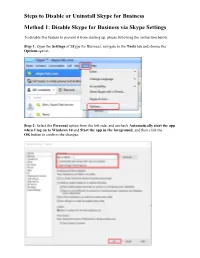
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Blackbaud CRM Security Guide
Security Guide 11/10/2014 Blackbaud Direct Marketing 4.0 Security UK ©2014 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying, recording, storage in an information retrieval system, or oth- erwise, without the prior written permission of Blackbaud, Inc. The information in this manual has been carefully checked and is believed to be accurate. Blackbaud, Inc., assumes no responsibility for any inaccuracies, errors, or omissions in this manual. In no event will Blackbaud, Inc., be liable for direct, indirect, special, incidental, or consequential damages resulting from any defect or omission in this manual, even if advised of the possibility of damages. In the interest of continuing product development, Blackbaud, Inc., reserves the right to make improvements in this manual and the products it describes at any time, without notice or obligation. All Blackbaud product names appearing herein are trademarks or registered trademarks of Blackbaud, Inc. All other products and company names mentioned herein are trademarks of their respective holder. Security-2014 Contents CONTENTS I SECURITY 1 Fundamentals of Security 1 APPLICATION USERS 3 Search for Users 3 Application User Records 4 Add an Application User 4 Edit Users 5 Delete Users 6 Grant/Revoke Users Administrator Rights 6 Run the Program as a Selected User 6 Organisational Unit Record 7 Application Users Page 8 Manage System Roles of an Application User 8 Add System Roles -
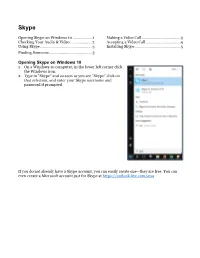
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -
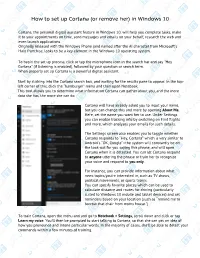
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Metasys Server Installation and Upgrade Instructions Code No
Metasys Server Installation and Upgrade Instructions Code No. LIT-12012162 Software Release 10.0 Issued April 15, 2019 Welcome.....................................................................................................................................3 Getting Started...........................................................................................................................3 Summary of Changes.........................................................................................................................4 Prerequisite Software Checklist for Installation and Upgrade.......................................................4 Recommended OS and SQL Server Combinations.........................................................................7 Upgrade Pre-Work Checklist..............................................................................................................8 Metasys Server Installation.....................................................................................................10 Installing Unified Metasys Server on Desktop Computer.............................................................10 Installing Unified Metasys Server on Server Computer................................................................12 Installing Unified Metasys Server and SCT on Desktop Computer.............................................14 Installing Unified Metasys Server and SCT on Server Computer................................................17 Installing a Split Metasys Server and SCT.....................................................................................20 -

Lesson 14: Creating and Managing Active Directory Users and Computers
Lesson 14: Creating and Managing Active Directory Users and Computers MOAC 70-410: Installing and Configuring Windows Server 2012 Overview • Exam Objective 5.2: Create and Manage Active Directory Users and Computers • Creating User Objects • Creating Computer Objects • Managing Active Directory Objects © 2013 John Wiley & Sons, Inc. 2 Creating User Objects Lesson 14: Creating and Managing Active Directory Users and Computers © 2013 John Wiley & Sons, Inc. 3 Creating User Objects • The user account is the primary method for authentication on a network. • Usernames and passwords are validated at log on by comparing entered information to the information stored in the AD DS database. © 2013 John Wiley & Sons, Inc. 4 Types of Users • Local users: These accounts can only access resources on the local computer and are stored in the local Security Account Manager (SAM) database on the computer where they reside. • Domain users: These accounts can access AD DS or network-based resources, such as shared folders and printers. o Account information for these users is stored in the AD DS database and replicated to all domain controllers within the same domain. © 2013 John Wiley & Sons, Inc. 5 Built-In User Accounts Administrator and Guest • On a member server or standalone server: The built-in local Administrator account has full control of all files as well as complete management permissions for the local computer. • On a domain controller: The built-in Administrator account created in Active Directory has full control of the domain in which it was created. The Administrator account cannot be deleted, but it can be renamed. © 2013 John Wiley & Sons, Inc. -

The 12 Essential Tasks of Active Directory Domain Services
WHITE PAPER ACTIVE DIRECTORY DOMAIN SERVICES The 12 Essential Tasks of Active Directory Domain Services Using the right tools and processes helps reduce administrative overhead and ensures directory service is always available By Nelson Ruest and Danielle Ruest Sponsored by WHITE PAPER ACTIVE DIRECTORY DOMAIN SERVICES ABSTRACT Active Directory Domain Services (AD DS) administration and management includes Sponsored by 12 major tasks. These tasks cover a wide breadth of business needs and are not all performed solely by AD DS administrators. In fact, administrators can and should delegate several tasks to other members of their technical community, technicians, help desk personnel, even users such as team managers and administrative assistants. While delegation is a way to reduce the amount of work administrators have to do when managing AD DS infrastructures, it really only addresses one or two of the 12 tasks, for example, user and group administration as well as end point device administration. The other ten tasks can be staggering in nature—security, networked service administration, OU-Specific Management, Group Policy Object management and many more—and because of this can take up inordinate amounts of time. You can rely on Microsoft’s built-in tools to reduce some of this workload, but are the native tools enough? Perhaps it’s time to reduce AD DS administration overhead by automating most tasks and tightening internal security. Address this by first, determining what the twelve essential labors of Active Directory are and then, see how you can reduce AD DS workloads through the implementation of proper management and administration tools. -

Inside Windows 10 - an Early Look at Microsoft’S Newest Operating System Volume 1 - by Onuora Amobi
0 www.windows10update.com – Comprehensive Windows 10 News Copyright Notice INSIDE WINDOWS 10 - AN EARLY LOOK AT MICROSOFT’S NEWEST OPERATING SYSTEM VOLUME 1 - BY ONUORA AMOBI ©2015 Nnigma Inc. All rights reserved. Any unauthorized use, sharing, reproduction or distribution of these materials by any means, electronic, mechanical, or otherwise is strictly prohibited. No portion of these materials may be reproduced in any manner whatsoever, without the express written consent of the Publisher or Author. Published under the Copyright Laws of The United States of America by: Nnigma Inc. 3579 East Foothill Blvd, Suite #254 Pasadena, CA 91107 www.Nnigma.com i www.windows10update.com – Comprehensive Windows 10 News Legal Notice While all attempts have been made to verify information provided in this publication, neither the author nor the publisher assumes any responsibility for errors, omissions or contradictory interpretation of the subject matter herein. This publication is not intended to be used as a source of binding technical, technological, legal or accounting advice. Please remember that the information contained may be subject to varying state and/or local laws or regulations that may apply to the user’s particular practice. The purchaser or reader of this publication assumes responsibility for the use of these materials and information. Adherence to all applicable laws and regulations, both federal, state, and local, governing professional licensing, business practices, advertising and any other aspects of doing business in the US or any other jurisdiction is the sole responsibility of the purchaser or reader. Nnigma Inc. assumes no responsibility or liability whatsoever on behalf of any purchaser or reader of these materials.