Wireless Routers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
View Your World Anywhere……Anytime!
View Your World Anywhere……Anytime! Camera Installation for PC with Windows XP, Windows 7, Windows 8/ 8.1 Camera Installation for Mac with Airport Extreme and Time Capsule Note: Proceed to the Quick Guide for iPhone, iPad iOS device and Android OS Smartphone, Tablet. 1 Introduction ----------------------------------------------------------------------------------------------------------------3 Pre-requisites and Initial Connection--------------------------------------------------------------------------------- 5 PC Quick start-------------------------------------------------------------------------------------------------------------- 6 Install “Camera Setup” and “Camera Live” Utilities on a PC------------------------------------------------------7 Install “Camera Live” Utility & Multiple Cameras viewing on a PC--------------------------------------------10 Mac Quick start------------------------------------------------------------------------------------------------------------15 Apple Airport Remote Access Setup----------------------------------------------------------------------------------19 Wi-Fi Wireless Setup for PC and Mac-------------------------------------------------------------------------------- 22 Wi-Fi Troubleshooting--------------------------------------------------------------------------------------------------- 26 Is the Remote Access Setup already done? ----------------------------------------------------------------------- 27 Enabling UPNP for Automatic Remote Access Setup ------------------------------------------------------------ -

Wireless-G Broadband Router WIRELESS User Guide
GHz 2,4802.11g Wireless-G Broadband Router WIRELESS User Guide Model No. WRT54G (EU/LA) Wireless-G Broadband Router Copyright and Trademarks Specifications are subject to change without notice. Linksys is a registered trademark or trademark of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries. Copyright © 2006 Cisco Systems, Inc. All rights reserved. Other brands and product names are trademarks or registered trademarks of their respective holders. How to Use This User Guide This User Guide has been designed to make understanding networking with the Wireless-G Broadband Router easier than ever. Look for the following items when reading this User Guide: This checkmark means there is a note of interest and is something you should pay special attention to while using the Wireless-G Broadband Router. This exclamation point means there is a caution or warning and is something that could damage your property or the Wireless-G Broadband Router. This question mark provides you with a reminder about something you might need to do while using the Wireless-G Broadband Router. In addition to these symbols, there are definitions for technical terms that are presented like this: word: definition. Also, each figure (diagram, screenshot, or other image) is provided with a figure number and description, like this: Figure 0-1: Sample Figure Description Figure numbers and descriptions can also be found in the “List of Figures” section in the “Table of Contents”. WRT54GV7-EU-UG-60307 BW Wireless-G Broadband Router Table of -

User Guide Linksys EA-Series Contents
SMART Wi-Fi Router AC900, EA6200 User Guide Linksys EA-Series Contents Contents Product Overview Using an External Drive EA6200 . .1 Overview. .18 Wall-mounting placement 4 How to attach a USB drive . .18 How to use secured folder access . 19 Setting Up: Basics How to set up authorized users and shared folders 19 How to access shared folders 20 How to create a home network. .5 How to set up your router as a media server . 21 What is a network? 5 How to connect your UPnP device to the media server 22 How to set up a home network 5 How to remotely access storage . 22 Where to find more help . .5 How to install your router . .6 How to configure your router. .7 Setting Up: Advanced How to connect to Linksys Smart Wi-Fi 7 How to manually set up your router. .24 How to connect directly to your router 8 How to manually set up your Internet connection 24 How to improve your wireless connection speed 8 How to change your network’s name and password 9 How to associate a router with your Linksys Smart Wi-Fi account 25 How to change your router’s local access password 9 How to get the most out of your dual-band router . 26 How to change your router’s time zone 10 How to control access to your network. .27 How to test your Internet connection speed . 10 How to improve security using the built-in firewall 29 How to connect devices to your network . 11 How to set up the DHCP server on your router . -

Wireless Router User Manual Models 525459, 525466, 525480
WIRELESS ROUTER USER MANUAL MODELS 525459, 525466, 525480 1200AC Model 505480 150N Model 505459 300N Model 505466 MH-525459/525466/525480-UM-0713-01 Thank you for purchasing this Manhattan® Wireless Router: Model 525459 (150N 4-Port), Model 525466 (300N 4-Port) or Model 525480 (1200AC 4-Port). The latest in wireless networking, these Wireless Routers serve multiple purposes — an access point for your wireless network, a four-port router for hard-wiring Ethernet devices — and bring it all together so that the devices can access a high-speed Internet connection. Detailed instructions in this user manual make installation reasonably quick and simple so you’ll soon be enjoying the benefits of these and more popular features: • Network link speed of up to 150 Mbps for Model 525459, 300 Mbps for Model 525466 and 867 Mbps for Model 525480 (at 5 GHz) • Supports WMM function to meet the multimedia data bandwidth requirement • Supports Wi-Fi Protected Setup (WPS) • Supports WEP and WPA/WPA2 (TKIP and AES) data encryption • Auto MDI/MDI-X support • DHCP server assigns IP addresses for all LAN users • DHCP server supports static lease management • Supports virtual server, port forwarding and DMZ (demilitarized zone) • Supports DDNS (dynamic DNS) • Supports UPnP (Universal Plug and Play) • Integrated anti-DOS firewall • QoS (Quality of Service) bandwidth management • VPN Passthrough • Easy installation through Web-based user interface • Three-Year Warranty Package Contents • Wireless 150N 4-Port Router, Wireless 300N 4-Port Router or Wireless 1200AC Router • Quick install guide, plus user manual on CD • Power adapter • Ethernet Cat5 RJ45 cable: 1.0 m (3 ft.) NOTE: Some screen images have been modified to fit the format of this manual. -

Openwrt Docs Documentation Release
Openwrt docs Documentation Release People on the internet Nov 12, 2017 Contents 1 Why use LEDE? 3 2 Download LEDE 5 3 LEDE wants you! 7 4 Contents 9 4.1 LEDE Project Information........................................9 4.2 LEDE Documentation.......................................... 14 5 Endorsements 31 i ii Openwrt docs Documentation, Release The LEDE Project (“Linux Embedded Development Environment”) is a Linux operating system based on OpenWrt. It is a complete replacement for the vendor-supplied firmware of a wide range of wireless routers and non-network devices. See the Table of Hardware for supported devices. For more information about LEDE Project organization, see the About LEDE page. Contents 1 Openwrt docs Documentation, Release 2 Contents CHAPTER 1 Why use LEDE? People install LEDE because they believe it works better than the stock firmware from their vendor. They find it is more stable, offers more features, is more secure and has better support. • Extensibility: LEDE provides many capabilities found only in high-end devices. Its 3000+ application packages are standardized, so you can easily replicate the same setup on any supported device, including two (or even five) year old routers. More about extensibility... • Security: LEDE’s standard installation is secure by default, with Wi-Fi disabled, no poor passwords or back- doors. LEDE’s software components are kept up-to-date, so vulnerabilities get closed shortly after they are discovered. More about security... • Performance and Stability: LEDE firmware is made of standardized modules used in all supported devices. This means each module will likely receive more testing and bug fixing than stock firmware which can be tweaked for each product line and never touched again. -

Wireless Router Quick Reference Booklet Thank You for Choosing Wightman Internet
Wightman Telecom Wireless Router Quick Reference Booklet Thank you for choosing Wightman Internet. The information in this booklet will guide you through the process of connecting to the internet with your Wightman wireless router. To see the full manufacturer’s guide, please visit Wightman.ca/support/internet For technical support, please call 1-877-327-4440. 2 Introduction 2 TABLE OF CONTENTS 3 Wightman Wireless Connection Details 4 Installation 6 Hardware Setup 6 Back Panel 6 Power On 6 Reset Button 7 Ethernet (LAN) Ports 7 Front Panel 7 Wifi Switch 8 WPS Button 8 LED Indicators 8 Computer Connection 9 IP Configuration 9 Windows XP Instructions 9 Windows 8.x, 7, and Vista Instructions 10 Wireless Router Connection 10 Web User Interface 10 Default Settings 10 Login Procedure 11 Frequently Asked Questions 12 3 WIGHTMAN WIRELESS CONNECTION DETAILS Please write down your SSID and passcode information in the space below. You will need this information for your wireless connections. Please have this information ready if calling in to our technical support group. Wifi Access (see image below) Wireless Router SSID : _______________________ Wireless key (passcode): _______________________________ Example of Router Label (found on top of router) SSID wightman9E1Z PASSCODE 8E858F9E1Z LOGIN URL http://192.168.1.1/ USERNAME user PASSWORD useradmin1 WIRELESS ROUTER ACCESS This section describes how to access the device via the web user interface (WUI) using an Internet browser such as Internet Explorer (version 5.0 and later). This is only required to adjust or configure the optional functionality of the wireless router. Default Settings The factory default settings of this device are summarized below. -

Wireless LAN Networking White Paper
Wireless LAN Networking White Paper Introduction • Roaming capability is desired; e.g., maintaining connectivity from almost anywhere inside a Wireless technology has helped to simplify home or business networking by enabling multiple computer • Network access is desired outdoors; e.g., users to simultaneously share resources outside a home or office building in a home or business without additional or intrusive wiring. These resources might include a broadband Internet connection, network Wireless LANs in the Office printers, data files, and even streaming audio and video. This kind of resource sharing has An 802.11 network is the ideal solution for a become more prevalent as computer users network administrator in many respects. No have changed their habits from using single, longer is it a requirement that every workstation stand-alone computers to working on networks and conference room be wired up to hubs and with multiple computers, each with potentially switches with cables in hard-to-reach areas. different operating systems and varying Wireless networking allows for impromptu peripheral hardware. U.S. Robotics wireless meetings in cafeterias, hallways, courtyards, networking products offer a variety of solutions or wherever inspiration strikes while providing to seamlessly integrate computers, peripherals, real-time LAN connectivity for business and data. applications such as sending e-mail, working on spreadsheets on shared drives, and Wireless networking enables the same capabilities conducting market research. and comparable speeds of a wired 10BASE-T network without the difficulties associated with laying wire, drilling into walls, or stringing Wireless LANs in the Home Ethernet cables throughout an office building Wireless networking has become commonplace, or home. -

Low-Cost On-Board Linux, Vision, Wi-Fi, and More for the Roomba Robotics Base
Low-cost On-board Linux, Vision, Wi-Fi, and more for the Roomba Robotics Base Tod E. Kurt ThingM Design 1126 Palm Terrace Pasadena, CA 91104 [email protected] Abstract Roomba-related requirements are single serial port and a The Roomba has become a rugged yet inexpensive small form-factor. peripheral robotics platform. Remotely controlling it with a desktop PC is well understood, but limits the utility as a research robot. By providing a capable on-board intelligence, the Roomba can be made autonomous and enable the installation of additional senses and actuators. With the addition of a sub-$100 wireless router, the Roomba can cut the tether and have an on-board embedded Linux system with built-in Wi-Fi and USB. The addition of USB allows the use of a wide-range of additional peripherals supported by Linux such as cameras, flash memory, and other science payloads. Figure 1 Capabilities of three common wireless routers. Motivation for Autonomous Roombas The iRobot Roomba Open Interface (ROI) [1] is a simple serial protocol that turns the robotic vacuum cleaner into a controllable robot base with basic sensors. The release of the protocol specification in late 2005 created an explosion of robotics experimentation accessible to anyone with a Roomba [2]. The physical interface of the ROI is RS-232- like asynchronous serial, which can be converted to true RS-232 via a serial tether [3] or accessed via a Bluetooth adapter [4]. The logical interface is based on a data format of 57.6 kbps, 8N1, with a command structure consisting of one to five byte commands used to interrogate and actuate the Roomba’s capabilities. -

Linksys X1000 I N300 Wireless Router with ADSL2+ Modem
Linksys X1000 I N300 Wireless Router with ADSL2+ Modem Create a wireless home network suitable for your DSL or cable broadband connection. Ideal for: • Sharing Internet access, surfing the web, emailing and printing wirelessly • Connecting multiple devices • Connecting to a DSL connection or cable modem Key features: • All-in-one device - functions as a wireless ADSL2+ modem router or a wireless router • Wireless-N router with wireless transfer speeds up to 300 Mbps • Reliable range with MIMO antenna technology • Three Ethernet ports for connecting wired devices Packaging Icons Packaging Icons Speed SpeedBoost Speed SpeedBoost Band Ports Band Ports Dual-Band USB Port Dual-Band USB Port N Wireless-N UPnP Media Server Packaging Icons N Wireless-N UPnP Media Server Broad Compatibility Easy Setup Packaging Icons Speed SpeedBoost Broad Compatibility Easy Setup HD/3D Ready QualitySpeed of Service SpeedBoost PackaBagindng Icons Ports HD/3D Ready Quality of Service Parental Controls IPv6BandLinksys Enabled X1000Ports I N300 Wireless Router with ADSL2+ Modem SpeedDual-Band SpeedBoUSB Portost Parental Controls IPv6 Enabled Advanced Security WiDualrele-Bassnd House USB Port BaWindreless-N PUPnPorts Media Server Packaging Icons N Advanced Security Wireless House Maximum Range DSL Built-inWireless-N DSL Modem UPnP Media Server DualBroad-Ba Cndompatibility USBEasy PSetuort p N Speed SpeedBoost Built-in DSL modem MQuickaximum Rang toe installDSL Built-in DSL Modem Directly connects you to the internet wirelessly —no separate DSL Linksys Connect helps you set up your wireless network in a few Wi Protected Setup Multi-portBroad Compatib connect.ility Easy Setup modem required. The Linksys X1000 can also act as a wirelessWiHD/3Dreless-N R eady UPnPQuality M oedf Siae rvSeicerver Band Ports easy steps on a Windows or Mac computer. -

Networking Types of Wireless Networks Introduction
Networking Types of Wireless Networks Introduction Community Wireless Networks can be designed in Reading through this material should take about many ways. To help you understand these 30 to 45 minutes. Working through the activities, different methods for designing networks, this or diving deeper into the subject with a group may document covers the basics of what different take longer. devices do in wireless networks, and how they can be used in different configurations. Using the MATERIALS + SUPPLIES NEEDED knowledge and activities in this document, you - The Worksheet and Solution decks - printed out can work with others to design the wireless on 8½ by 11" or A4 paper. Available on the network that works best for your community. Construction Kit website. - Pens or colored markers Reading and working through Learn Wireless - A surface to work on Basics before this document will help you with some of the concepts used in designing wireless networks. It provides some necessary background information for this document. A Build-It-Ourselves Guide to Wireless Mesh Networks 2 UNIT: NETWORKING MODULE: TYPES OF WIRELESS NETWORKS Wireless Device Roles There are three major “modes” a Wi-Fi device can use. These modes define the role a Wi-Fi device has in the network, and networks must be built out of combinations of devices operating in these different modes. How the devices are configured depends on the types of connections you want to use between parts of the network. In discussing these modes and the examples below, several types of devices are used. In addition to the phones, tablets, and laptops you use in accessing a network, routers make up the hardware that runs the network. -

User Guide 802.11Ac Wave 2 Router Model RAC2V1S
User Guide 802.11ac Wave 2 Router Model RAC2V1S Trademarks Sagemcom and the Sagemcom logo are trademarks or registered trademarks of Sagemcom Broadband SAS or its subsidiaries in the United States or other countries. All other company or product names mentioned herein are trademarks or registered trademarks of their respective companies. Copyright © 2014 by Sagemcom Broadband SAS. All rights reserved. Rights of modifications reserved. This publication may not be reproduced, in whole or in part, without prior expressed written permission of Sagemcom Broadband SAS. Issued by Sagemcom Broadband SAS Sagemcom 250, route de l'Empereur - 92848 RUEIL MALMAISON CEDEX FRANCE i Table of Contents Trademarks........................................................................................................................................................ i Chapter 1: Product Overview ..................................................................................... 1 Package Contents .......................................................................................................................................... 2 Hardware Overview ....................................................................................................................................... 2 Labels ............................................................................................................................................................. 5 Router Positioning .....................................................................................................................................6 -
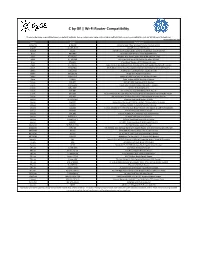
C by GE | Wi-Fi Router Compatibility
C by GE | Wi-Fi Router Compatibility These routers are compatible based on default settings. Some routers may have customizable settings that cause incompatibility, such as WPA3 security features. Updated May 26, 2020 Vendor Model Description Actiontec GT84WN Actiontec 300 Mbps Wireless-N ADSL Modem Router AmpliFI Afi-INS-R-US AmpliFi Instant WiFi Router ASRock G10us ASRock G10 AC2600 Gigabit Gaming Router (802.11 a/b/g/n/ac) Asus RT-N66U Dual Band 3x3 Wireless-N900 Gigabit Router ASUS RT-ARCH17 Wireless Dual Band Gigabit Router Wireless-AC1700 ASUS RT-AC1200 802.11ac Dual-band USB Router Wireless-AC1200 Asus RT-N65U Dual Band Wireless-N750 Wireless Router ASUS RT-ARCH13 ASUS RT-ACRH13 Dual-Band 2x2 AC1300 Wifi 4-port Gigabit Router with USB 3.0 ASUS RT-AC68U ASUS Whole Home Dual-Band AiMesh Router (AC1900) for Mesh Wifi System Belkin F91124V1 AC1900 Wi-Fi Dual-Band AC+ Gigabit Router Belkin F9K1001V5 N150 Wi-Fi Router Dual Band Belkin F9K1113v5 Belkin AC1200 Dual Band AC Wireless Router Cisco E2100L Cisco-Linksys E1000 Wireless-N Router D-Link DIR-879 GXO AC1900 Dual Band Wi-Fi Router D-Link COVR-3902 D-Link Covr AC3900 Whole Home Wi-Fi System D-Link DGL-4500 Xtreme N Gaming Router D-Link DIR-882 D-Link EXO AC2600 MU-MIMO Wi-Fi Router D-Link DIR-826L D-Link Wireless AC 1200 Mbps Home Cloud App-Enabled Dual-Band Gigabit Router D-Link DIR-869 D-Link EXO AC1750 Dual-Band Wi-Fi Performance Wireless Router LB-Link BL-W1210M Wireless Dual Band Router AC1200 Linksys EA8300 Linksys Max-Stream AC2200 MU-MIMO Tri-Band Wireless Router Linksys EA9200