Implementing Microsoft Hyper-V on IBM System X and IBM Bladecenter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Para-Virtualization
Large-Scale Data & Systems Group Virtualization Jana Giceva [email protected] PeterDepartment R. Pietzuch of Computing Imperial College London [email protected]://lsds.doc.ic.ac.uk Fall 2018 Intro to Virtualization 2 Why do we need virtualizaton? • Recall previous lecture… 3 What is virtualization? • Broadly speaking… Virtualization: simulate or emulate a function of a resource (object) in software, identical to that of the physical one. Abstraction to make software look and behave like hardware. • Recall – virtual memory • Computer software gains access to more memory than it is physically installed, via the background swapping of data to disk storage. • Similarly, virtualization techniques can be applied to other IT infrastructure layers, including networks, storage, laptop or server hardware, OSs and applications. 4 Virtual infrastructure • Allows multiple VMs with different OSs and applications to run in isolation, side by side on the same physical machine. • VMs can be provisioned to any system. • Machine independence of OS and applications. • Can manage an application and its OS as a unit, encapsulating them in a single VM. src: VMWare whitepaper -- Virtualization 5 Properties of Virtual Machines • Key properties of VMs: • 1. Partitioning – Run multiple OS on one physical machine – Divide system resources between VMs • 2. Isolation – Provide fault and security isolation at the hardware level – Preserve performance with advanced resource controls • 3. Encapsulation – Save the entire state of a VM to files – Move and copy VMs as easily as copying and moving files • 4. Hardware independence – Provision or migrate any VM to any physical server 6 Virtualization – Definitions and Terms Virtual Machine (VM): a tightly isolated software container with an operating system (OS) and an application inside. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Network Virtualization for Open Cloud
Πανεπιστήμιο Δυτικής Αττικής Τμήμα Μηχανικών Πληροφορικής και Υπολογιστών ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ της ΣΟΥΒΑΛΙΩΤΗ ΜΑΡΙΑΣ Επιβλέπων Καθηγητής: Ξυδάς Ιωάννης Επίκουρος Καθηγητής ΠΑ.Δ.Α. Αθήνα, Σεπτέμβριος, 2018 Περιεχόμενα Περίληψη ...............................................................................................................................................9 Αbstract...................................................................................................................................................9 Ευχαριστίες.............................................................................................................................................10 ΚΕΦΑΛΑΙΟ 1 – Εισαγωγή ..................................................................................................................11 1.1. Περίληψη Κεφαλαίου..................................................................................................................11 1.2. Virtualization ...............................................................................................................................11 1.2.1. Hypervisor – Virtual Machine Manager................................................................................12 1.2.1.1. Ενσωματωμένοι Hypervisors.........................................................................................13 1.2.2. Network Virtualization..........................................................................................................13 1.2.2.1. Συνδυασμοί Network Virtualization...............................................................................14 -

Microsoft Service Pack & Security Bulletin Support
Microsoft Service Pack & Security Bulletin Support ReadMe Revision History Date Revised Changes Made March 23, 2020 March 2020 Microsoft Security Update Contents What’s New? . 1 Microsoft Security Bulletins . 2 Current Microsoft Security Bulletin Status . 2 Enabling Windows Updates on Avid Systems . 6 Using a Microsoft WSUS Server for distributing Windows Updates. 7 Historical List of Microsoft Security Bulletin Exceptions . 7 What’s New? For March security bulletins, see “Current Microsoft Security Bulletin Status” on page 2. The section on “Notification Regarding the January 2020 Windows Updates” on page 3 has been updated to include information on MediaCentral Asset Management and MediaCentral Newsroom Management. See also http://avid.force.com/pkb/articles/en_US/Troubleshooting/en239659. Microsoft Security Bulletins Microsoft Security Bulletins Install Windows Security Patches and Service Packs. To download patches, run Windows Update. By default Avid supports all Windows Service Packs and security patches (sometimes referred to as “hot fixes”) which apply to the environments in which Avid products are deployed. We refer to them as Windows Updates in this document. Customers can schedule the download and installation of Windows Updates whenever they are available and make sense in their production environment. Avid tests the updates within several days of their availability. However, customers do not have to wait for the testing to be complete before installing the updates. Our current testing methodology is to utilize Windows Update on a representative sample of Avid products upon notification of new Security Bulletin availability by Microsoft. These systems are updated and observed while under test. Once the test period has completed (approx. -

Manage Your Virtual Environments with Virtual Machine Manager 2008
Virtualisation In this article, I will examine VMM 2008 The red box on the upper-left represents At a glance: and the new features it brings to IT adminis- the Virtual Machine Manager 2008 server Support for VMware VMs trators. I’ll then look at the requirements and service. Above it are the different interfaces Windows PowerShell- based scripting and the steps involved with a VMM installation. into the service: the Administrator Console, automation Finally, I’ll take a closer look at how to use the Windows PowerShell interface, and the Consolidated, centralised some of the new features of VMM 2008. management Installation procedures An introduction to Virtual Machine There are significantly Manager 2008 System Center Virtual Machine Manager more interfaces to 2008 is a standalone application that provides centralised, enterprise-class management of the VMM system in virtual machines running under Microsoft Virtual Server 2005 R2 SP1, Windows Serv- VMM 2008 er 2008 Hyper-V, Microsoft Hyper-V Server Manage your virtual 2008 and VMware Infrastructure 3 (ESX/ ESXi) servers. Together with other System Self-Service Web Portal with delegated user Center products, VMM provides end-to-end access. Windows PowerShell forms the basis physical and virtual infrastructure manage- for all access to the VMM server. The VMM environments with ment. Figure 1 shows the architectural lay- Admin Console is built entirely on Win- out of Virtual Machine Manager. dows PowerShell, so you can simply create As those familiar with VMM 2007 will Windows PowerShell scripts that the VMM note, there are significantly more interfaces server service runs. Thus, the public API for Virtual Machine to the VMM system in VMM 2008 (see Fig- VMM 2008 is Windows PowerShell, and any ure 1). -
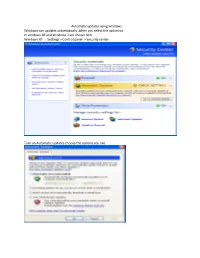
Automatic Updates Using Windows Windows Can Updates Automatically ,When You Select the Option On
Automatic updates using windows Windows can updates automatically ,when you select the option on. In windows XP and Windows 7 are shown here Windows XP : Settings > Control panel > Security center Turn on Automatic updates choose the options you like. In windows 7: Control panel > System and security So how can do all users let updates on system. By default, Windows only allows users with administrator user accounts to install updates. To allow all users to install updates, follow these steps: Click to open Windows Update. In the left pane, click Change settings. Do one of the following: To allow standard users to install updates, select the Allow all users to install updates on this computer check box. To prevent standard users from installing updates, clear the Allow all users to install updates on this computer check box. If you use automatic updating for Important or Recommended updates, those updates are installed regardless of whether the current user is an administrator or not. Different types of updates Updates are classified as Important, Recommended, Optional, and Featured. Important updates offer significant benefits, such as improved security, privacy, and reliability. They should be installed as they become available, and can be installed automatically with Windows Update. Recommended updates address non-critical problems or help enhance your computing experience. While these updates do not address fundamental issues with your computer or Windows software, they can offer meaningful improvements. These can be installed automatically. Optional updates can include updates, drivers, or new software from Microsoft to enhance your computing experience. You can only install these manually. -

Windows Server, System Center, and Forefront Pricing and Licensing Guide
1 Comprehensive Resource for Licensing and Pricing Windows Server, System Center, and Forefront Licensing Guide Table of Contents What’s New in This Guide 2 Windows Server 2008 R2 Offerings 2 Windows Server 2008 R2 Licensing 5 General Windows Server Licensing Construct 5 Windows Server 2008 R2 Foundation 6 Windows Server 2008 R2 Standard 6 Windows Server 2008 R2 Enterprise 7 Windows Server 2008 R2 Datacenter 9 Windows Server 2008 R2 for Itanium-Based Systems 9 Windows Web Server 2008 R2 10 Windows HPC Server 2008 R2 10 Windows Server 2008 Client Access Licensing: Decision Trees, Types, and Modes 12 Remote Desktop Services Licensing Requirements 14 External Connector License Requirements for Windows Server 2008 15 Virtual Desktop Infrastructure Suites Licensing 16 System Center Offerings 18 System Center Licensing 19 General System Center Licensing Construct 19 System Center Server Management for Enterprise 20 System Center Client Management for Enterprise 24 System Center Server and Client Management for Midmarket 25 Enrollment for Core Infrastructure Licensing 26 Core Infrastructure Server Suites 27 Program Requirements 27 ECI Migration Paths 28 Pricing Tables and SKUs 30 Windows Server 30 System Center 34 Best Practices and Resources 35 Windows Server Licensing Scenarios 35 Windows Server Upgrade and Downgrade Options 37 Tracking Windows Server Licenses 40 Forefront 2010 Overview 43 Forefront 2010 Offerings 43 FF 2010 Management Product Offerings 43 Forefront 2010 Protection & Access Product Offerings 43 Forefront 2010 Licensing Overview -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Vmware Converter Enterprise-Class Migration Tool for Converting Physical Machines, Virtual Machines Or Other Third-Party Image Formats to Vmware Virtual Machines
PRODUCT DATASHEET VMware Converter Enterprise-class migration tool for converting physical machines, virtual machines or other third-party image formats to VMware virtual machines What Is VMware Converter? How Does VMware Converter Work? VMware® Converter is a highly robust and scalable enterprise-class VMware Converter is managed through a simple, task based UI that migration tool that reduces the time that IT managers spend convert- enables customers to convert physical machines, other VMware ing physical machines to VMware virtual machines. Using a snapshot- product formats or other third-party formats to VMware virtual based cloning mechanism that is extremely fast and reliable, VMware machines in three easy steps: Converter enables remote conversions without disrupting the source • Step 1: Specify the source physical server, virtual machine or third- server during the conversion process. party format to convert. VMware Converter provides a full range of physical-to-virtual and • Step 2: Specify the destination format, virtual machine name, and virtual-to-virtual conversions, allowing users to: location for the new virtual machine to be created. • Convert physical machines running Windows operating systems 1 to • Step 3: Automate the virtual machine creation and conversion pro- VMware virtual machines cess with VMware Converter. • Import older VMware virtual machine formats to new VMware virtual machine formats What are Benefits and Applications of VMware • Convert third-party formats such as Symantec Backup Exec System Converter? Recovery (formerly Symantec LiveState Recovery) and Microsoft Vir- tual Server/Virtual PC to VMware virtual machines Customers often want to convert a large number of physical servers to VMware virtual machines, for example, during a server consoli- • Populate new virtual machine environments quickly from large direc- dation project. -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

Vmware Converter User's Manual: Vmware Converter 3
VMware Converter User’s Manual VMware Converter 3 VMware Converter User’s Manual VMware Converter User’s Manual Version: 3.0.2 Revision: 20071018 Item: VMC-ENG-Q407-281 You can find the most up-to-date technical documentation on our Web site at http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] © 2006-2007 VMware, Inc. All rights reserved. Protected by one or more of U.S. Patent Nos. 6,397,242, 6,496,847, 6,704,925, 6,711,672, 6,725,289, 6,735,601, 6,785,886, 6,789,156, 6,795,966, 6,880,022, 6,944,699, 6,961,806, 6,961,941, 7,069,413, 7,082,598, 7,089,377, 7,111,086, 7,111,145, 7,117,481, 7,149,843, 7,155,558, 7,222,221, 7,260,815, 7,260,820, and 7,269,683; patents pending. VMware, the VMware “boxes” logo and design, Virtual SMP and VMotion are registered trademarks or trademarks of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents Preface 7 1 Introduction to VMware Converter 9 Migration with VMware Converter 9 VMware Converter Editions 10 Cloning and System Reconfiguration of Physical Machines 10 Hot and Cold Cloning 11 Local and Remote Cloning 11 Example of Remote Hot Cloning 11 Example of Local Cold Cloning 13 Cloning Modes 14 Volume‐Based Cloning 14 Disk‐Based Cloning 15 Migrating Existing Virtual Machines