Adobe Sign Enterprise Overview Security, Compliance, Identity Management, and Document Handling
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Trademark Database for General Distribution
Adobe Trademark List for General Distribution As of May 17, 2021 Please refer to the Permissions and trademark guidelines on our company web site and to the publication Adobe Trademark Guidelines for third parties who license, use or refer to Adobe trademarks for specific information on proper trademark usage. Along with this database (and future updates), they are available from our company web site at: https://www.adobe.com/legal/permissions/trademarks.html Unless you are licensed by Adobe under a specific licensing program agreement or equivalent authorization, use of Adobe logos, such as the Adobe corporate logo or an Adobe product logo, is not allowed. You may qualify for use of certain logos under the programs offered through Partnering with Adobe. Please contact your Adobe representative for applicable guidelines, or learn more about logo usage on our website: https://www.adobe.com/legal/permissions.html Referring to Adobe products Use the full name of the product at its first and most prominent mention (for example, “Adobe Photoshop” in first reference, not “Photoshop”). See the “Preferred use” column below to see how each product should be referenced. Unless specifically noted, abbreviations and acronyms should not be used to refer to Adobe products or trademarks. Attribution statements Marking trademarks with ® or TM symbols is not required, but please include an attribution statement, which may appear in small, but still legible, print, when using any Adobe trademarks in any published materials—typically with other legal lines such as a copyright notice at the end of a document, on the copyright page of a book or manual, or on the legal information page of a website. -

Apttus Adobe Sign Services on Salesforce Spring 2020 Integration Guide
Apttus Adobe Sign Services on Salesforce Spring 2020 Integration Guide Table of Contents About this Guide............................................................................................................................................................................ 3 What's New ...................................................................................................................................................................................... 4 About Apttus Adobe Sign Services ....................................................................................................................................7 Apttus Adobe Sign Integration Life cycle .......................................................................................................................................7 Rebranding ..........................................................................................................................................................................................................7 Key Terminology ..............................................................................................................................................................................................8 Installing Apttus Adobe Sign Services ...........................................................................................................................9 Installing the Apttus Adobe Sign Packages .................................................................................................................................9 -

Adobe Sign Technical Overview White Paper
Adobe Sign Technical Overview White Paper Adobe Sign technical overview Security, compliance, identity management, governance, and document handling Executive summary Adobe Sign is a Document Cloud solution that helps your organization deliver end-to-end digital document experiences with trusted, legal electronic signatures. Use Adobe Sign to easily initiate, sign, track, manage, and archive digital documents from web or mobile apps—or from within enterprise systems. Adobe Sign complies with many regional regulations and industry standards, and is accessible anywhere on any device. A robust cloud-based service, Adobe Sign securely handles large volumes of electronic signature (e-signature) processes, including: Table of contents 1: Executive summary • Managing user identities with capability-based authentication 2: Architecture • Certifying document integrity 4: Identity management 4: Document certifcation • Verifying e-signatures 5: Security • Logging recipient acceptance or acknowledged receipt of documents 8: Compliance • Maintaining audit trails 9: Operations 11: For more information • Integrating with your most valued business applications and enterprise systems Adobe Sign supports both e-signatures and digital signatures. E-signatures are a way to indicate consent or approval on digital documents and forms. E-signatures are legally valid and enforceable in many industrialized nations around the world. A digital signature, by contrast, is a specific implementation of an e-signature that uses a certificate-based digital ID to verify signer identity and binds the signature to the document with encryption. Adobe Sign works with digital IDs stored on smart cards, USB tokens, and cloud-based hardware security modules (HSMs). And it supports open, standards-based signing with digital IDs across desktop, web, and mobile using the Cloud Signature Consortium specification. -
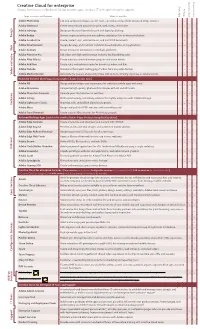
Adobe Creative Cloud for Enterprise Overview
Requires Services New CS6 Since Creative Cloud for enterprise App Single Always have access to the latest Adobe creative apps, services, IT tools and enterprise support Apps All Apps, Services, and Features What it’s used for Adobe Photoshop Edit and composite images, use 3D tools, edit video, and perform advanced image analysis. • • Adobe Illustrator Create vector-based graphics for print, web, video, and mobile. • • Adobe InDesign Design professional layouts for print and digital publishing. • • Adobe Bridge Browse, organize and search your photos and design files in one central place. Design • Adobe Acrobat Pro Create, protect, sign, collaborate on, and print PDF documents. • Adobe Dreamweaver Design, develop, and maintain standards-based websites and applications. • • Web Adobe Animate Create interactive animations for multiple platforms. • • • Adobe Premiere Pro Edit video with high-performance, industry-leading editing suite. • • Adobe After Effects Create industry-standard motion graphics and visual effects. • • Adobe Audition Create, edit, and enhance audio for broadcast, video, and film. • • Adobe Prelude Streamline the import and logging of video, from any video format. • • • Video and audio and Video Adobe Media Encoder Automate the process of encoding video and audio to virtually any video or device format. • Exclusive Creative Cloud Apps (not available in Adobe Creative Suite) Adobe XD Design and prototype user experiences for websites, mobile apps and more. • • • • Adobe Dimension Composite high-quality, photorealistic images with 2D and 3D assets. • • • • Adobe Character Animator Animate your 2D characters in real time. • • Adobe InCopy Professional writing and editing solution that tightly integrates with Adobe InDesign. • • Adobe Lightroom Classic Organize, edit, and publish digital photographs. -
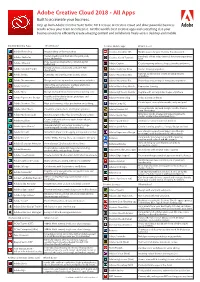
Adobe Creative Cloud 2018 - All Apps Built to Accelerate Your Business
Adobe Creative Cloud 2018 - All Apps Built to accelerate your business. Step up from Adobe Creative Suite to the 2018 release of Creative Cloud and drive powerful business results across your team or enterprise. Get the world’s best creative apps and everything else your business needs to efficiently create amazing content and collaborate freely across desktop and mobile. Creative Desktop Apps What it does? Creative Mobile apps What it does? Adobe Photoshop Image editing and compositing Creative Cloud for iOS Mobile access to your Creative Cloud account Adobe Illustrator Vector graphics and illustration for print, web, Hundreds of free video tutorials for every experience video, and mobile Creative Cloud Tutorials level Page design and layout for print and digital Adobe InDesign publishing Adobe Capture Create inspiring colours, shapes, brushes and more Create, protect, collaborate, and print PDF Adobe Acrobat Pro DC documents Adobe Illustrator Draw Vector drawing anywhere Adobe Bridge Centralize and organize your creative assets Cut out, combine and create amazing images, Adobe Photoshop Mix anywhere. Adobe Dreamweaver Design and develop modern, responsive websites Adobe Photoshop Fix Photoshop retouching for everyone, anywhere Interactive animations for multiple platforms Adobe Animate (formerly Flash Professional) Adobe Photoshop Sketch Expressive drawing Adobe Muse Design and publish websites without writing code Adobe Lightroom Mobile Capture, edit and organize images anywhere Rapidly and iteratively design, prototype, and Adobe -

Adobe 2018 Proxy Statement
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 SCHEDULE 14A Proxy Statement Pursuant to Section 14(a) of the Securities Exchange Act of 1934 (Amendment No.) Filed by the Registrant Filed by a Party other than the Registrant Check the appropriate box: Preliminary Proxy Statement Confidential, for Use of the Commission Only (as permitted by Rule 14a-6(e)(2)) Definitive Proxy Statement Definitive Additional Materials Soliciting Material under §240.14a-12 Adobe Systems Incorporated (Name of Registrant as Specified In Its Charter) (Name of Person(s) Filing Proxy Statement, if other than the Registrant) Payment of Filing Fee (Check the appropriate box): No fee required. Fee computed on table below per Exchange Act Rules 14a-6(i)(1) and 0-11. (1) Title of each class of securities to which transaction applies: (2) Aggregate number of securities to which transaction applies: (3) Per unit price or other underlying value of transaction computed pursuant to Exchange Act Rule 0-11 (set forth the amount on which the filing fee is calculated and state how it was determined): (4) Proposed maximum aggregate value of transaction: (5) Total fee paid: Fee paid previously with preliminary materials. Check box if any part of the fee is offset as provided by Exchange Act Rule 0-11(a)(2) and identify the filing for which the offsetting fee was paid previously. Identify the previous filing by registration statement number, or the Form or Schedule and the date of its filing. (1) Amount Previously Paid: (2) Form, Schedule or Registration Statement No.: (3) Filing Party: (4) Date Filed: Adobe Systems Incorporated 345 Park Avenue San Jose, California 95110 NOTICE OF ANNUAL MEETING OF STOCKHOLDERS To Be Held April 12, 2018 Dear Stockholders: You are cordially invited to attend our 2018 Annual Meeting of Stockholders to be held on Thursday, April 12, 2018 at 9:00 a.m. -
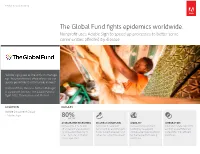
Global Fund Uses Adobe Sign to Speed up Processes to Better Serve
Adobe Customer Story The Global Fund fights epidemics worldwide. Nonprofit uses Adobe Sign to speed up processes to better serve communities affected by disease. “Adobe Sign gives us the tools to manage our documents more efficiently so we can quickly get money to communities in need.” Andrew Tatam, Business Partner Manager, IT Corporate Services, The Global Fund to Fight AIDS, Tuberculosis and Malaria SOLUTION RESULTS Adobe Document Cloud • Adobe Sign 80% LESS TIME ACCELERATED RECRUITING MULTIPLE SIGNATURES MOBILITY INTEGRATION Reduced the time to sign Accelerated document Reduced delays in grant Integrated Adobe Sign with off on recruiting evaluations turnaround by enabling up to funding by developing existing Oracle E-Business by 80%—from five days to 40 concurrent reviewers and mobile-accessible workflows Suite platform for efficient one—for faster staffing of signers for a grant document for the frequently traveling workflows crucial operations workforce Adobe Customer Story The Global Fund to Fight AIDS, Fighting AIDS, tuberculosis, and malaria Tuberculosis and Malaria Every year, governments, private philanthropic foundations, and committed individuals worldwide band Established in 2002 together to fight diseases through the Global Fund to Fight AIDS, Tuberculosis and Malaria. The Global Fund mobilizes around $4 billion a year to deliver life-saving medicine and preventative care to communities Employees: approximately 700 hardest hit by these epidemics. Geneva, Switzerland While some nonprofit organizations focus on developing and implementing their own programs, the www.theglobalfund.org Global Fund offers a simple but fundamentally new philosophy: local communities already know how to best solve the problem. All they need is the resources to fund the fight. -

RSCCD ITS Help Desk – Adobe Sign Usage Guide Updated 08/04/2020
RSCCD ITS Help Desk – Adobe Sign Usage Guide Updated 08/04/2020 Electronic signatures (i.e., e-signatures) are legally binding and can be used to replace handwritten signatures. They can also use more advanced cloud signatures that rely on certificate-based digital IDs to provide stronger signer authentication. With Adobe Sign, recipients can electronically sign documents by typing or drawing their name on their computer or mobile device or uploading an image of their signature. The following document shows how to use Adobe Sign to prepare a document for signatures, and how to electronically sign a document. NOTE: You will need access to the Adobe Creative Cloud in order to use Adobe Sign features. Additionally, a secure certificate based digital ID (or digital signature) for Adobe Sign is tied to your Adobe Creative Cloud account, which is associated with a valid RSCCD email address. NOTE: Login instructions and software installation steps for Adobe Creative Cloud are located here: https://www.rsccd.edu/Departments/Information-Technology-Services/Documents/Adobe-Creative-Cloud-Home-Use-for-Faculty-and-Staff.pdf For further assistance, please contact the RSCCD ITS Help Desk. 714-564-4357 | Ext 44357 | [email protected] | webhelpdesk.rsccd.edu | Mon-Fri, 7:30am-4:30pm 1 | Page RSCCD ITS Help Desk – Adobe Sign Usage Guide Updated 08/04/2020 Contents Prepare document for e-signatures .............................................................................................................................................................................. -

E-Signatures and Sales
Adobe Document Cloud White Paper How IT can enable the business to close deals faster Paper and manual processes grind the sales cycle to a halt. But IT has the power to solve the problem by leveraging Adobe Document Cloud solutions. Table of contents Manual processes impact revenue and productivity 1: Manual processes With all the technology at their disposal today, companies still employ sales processes that involve too much impact revenue and productivity waiting. Sales reps may wait for emails, returned phone calls and various parties to appear in the office. 1: Remove sales Customers may wait for information, documents to arrive or executive approval. A deal that is all but official roadblocks can be in limbo for days or weeks while all parties review and revise agreements, collect signatures and courier 2: Make the organization signed documents back and forth. more nimble 3: Meet security Usually, there isn’t an easy way to know the current status of the contract or find the most recent copy, and objectives time spent finding this information is time the rep isn’t selling. Any errors in agreements caused by manual 4: Enable sales to work processes can set the deal back even further. And sales reps know the danger in delay: If it takes too long, faster—with a solution they may lose the deal. Delays also wreak havoc with sales forecasting, impacting the entire business and a IT can trust 4: Checklist: How company’s ability to compete. to evaluate a digital document But as enormous as the problems may be, there is a simple solution that is easy for IT to implement and easy communications for sales departments to adopt. -

ADOBE PSLT – Adobe Creative Cloud Und Adobe Document Cloud (2016V1.4)
ADOBE PSLT – Adobe Creative Cloud und Adobe Document Cloud (2016v1.4) PRODUKTSPEZIFISCHE LIZENZBEDINGUNGEN FÜR ON-PREMISE SOFTWARE 1. Zugriff von einer Mehrzahl von Benutzern. 1.1 Wird die On-premise Software auf einem Computer, auf dem mehr als ein Benutzer Zugriff hat, auf einer pro Benutzer Basis (per-User) lizenziert, darf die Anzahl der potentiellen Benutzer (nicht die Anzahl der gleichzeitigen Benutzer) die gemäß dem Bestelldokument erworbene Anzahl an Lizenzen der On-premise Software nicht übersteigen. 1.2 Der Kunde darf die On-premise Software nicht für Tätigkeiten verwenden, die nicht von einem Einzelbenutzer initiiert werden (z. B. automatische Serververarbeitung). 2. Aktivierung; Gleichzeitige Nutzung. Lizenziert der Kunde die On-premise Software auf einer pro Benutzer Basis darf jeder Benutzer die On-premise Software auf bis zu zwei Computern aktivieren, die der direkten Kontrolle des Kunden unterliegen. Der Kunde darf die On-premise Software jedoch nicht gleichzeitig auf diesen beiden Computern verwenden. Lizenziert der Kunde die On-premise Software auf einer pro Computer Basis, darf der Kunde die On-premise Software nur auf einem Computer installieren. 3. Updates. Der Kunde ist im Rahmen seiner Nutzung der On-Premise Software damit einverstanden, dass die On-premise Software von Zeit zu Zeit automatisch neue Softwarestände installiert. 4. Inhaltsdateien. Der Kunde darf die von Adobe bereitgestellten „Inhaltsdateien“ (z.B. Stockfotos und Klänge) wiedergeben, bearbeiten, vervielfältigen und verbreiten. Er darf diese Inhaltsdateien jedoch nicht einzeln vertreiben und hat keinen Anspruch auf Markenrechte an derartigen Inhaltsdateien oder Ableitungen davon. 5. Eingebettete Materialien. Der Kunde darf die ihm mit der On-premise Software bereitgestellte Software (etwa Runtimes, Add-ins und andere Bestandteile, die etwa als Teil einer Applikation zum Ablauf auf dem Apple iOS oder Android™ Betriebssystem entwickelt wurden) als vollständig integrierten Teil einer Entwicklerapplikation, elektronische Dokumente oder Inhalte vertreiben. -

SIGNING” WITHOUT SIGNING What Estate Planners Should Know About the Federal E-Sign Act and the Texas Uniform Electronic Transactions Act
“SIGNING” WITHOUT SIGNING What Estate Planners Should Know About the Federal E-Sign Act and The Texas Uniform Electronic Transactions Act WILLIAM D. PARGAMAN, Austin Saunders, Norval, Pargaman & Atkins State Bar of Texas 28TH ANNUAL ESTATE PLANNING & PROBATE DRAFTING COURSE October 26-27, 2017 Houston CHAPTER 14 © 2017, William D. Pargaman, All Rights Reserved 10/16/2017 3:09 PM WILLIAM D. (BILL) PARGAMAN SAUNDERS, NORVAL, PARGAMAN&ATKINS, LLP 2630 Exposition Boulevard, Suite 203 Austin, Texas 78703-1763 512.617.7328 (direct) ∞ 512.472.7790 (fax) [email protected] ∞ www.snpalaw.com Legal Experience Bill Pargaman has been a partner in the Austin law firm of Saunders, Norval, Pargaman & Atkins since July of 2012. He has been certified as a specialist in Estate Planning and Probate Law by the Texas Board of Legal Specialization (since 1986) and has been a Fellow in the American College of Trust and Estate Counsel (since 1994). He is very active in the Real Estate, Probate and Trust Law Section of the State Bar of Texas, having served as REPTL’s Chair for the 2015-2016 bar year, as chair of its Estate and Trust Legislative Affairs Committee for the 2009, 2011, and 2013 legislative sessions, and as a Council member and chair of REPTL’s Trusts Committee from 2004 to 2008. Bill’s practice involves the preparation of wills, trusts and other estate planning documents, charitable planning, and estate administration and alternatives to administration. He advises clients on the organization and maintenance of business entities such as corporations, partnerships, and limited liability entities. He represents nonprofit entities with respect to issues involving charitable trusts and endowments. -

Adobe Annual Report 2020
Adobe Annual Report 2020 Form 10-K (NASDAQ:ADBE) Published: January 21st, 2020 PDF generated by stocklight.com UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 _____________________________ FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended November 29, 2019 or ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number: 0-15175 ADOBE INC. (Exact name of registrant as specified in its charter) _____________________________ Delaware 77-0019522 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 345 Park Avenue, San Jose, California 95110-2704 (Address of principal executive offices) (408) 536-6000 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Trading Symbol Name of Each Exchange on Which Registered Common Stock, $0.0001 par value per share ADBE NASDAQ Securities registered pursuant to Section 12(g) of the Act: None _____________________________ Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes ☐ No ☒ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days.