Criminal Justice M01dels: an Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Channel Lineup
Channel Lineup HD HD HD HD HD BASIC DIGITAL CONTINUED DIGITAL PLUS ON DEMAND PREMIUM ABC (WSB) 2 801 Includes Basic and Digital. Video On Demand 949-999 Additional monthly subscription may be required. FOX Sports 2 140 890 AntennaTV (WATL) 784 American Heroes Channel 157 Cinemax 216 215 / 910 / 831 FOX Sports South 23 836 Bounce (WSB) 793 BET Jams 161 MUSIC CHANNELS FOX Sports Southeast 25 835 Cinemáx 219 Buzzr (WAGA) 782 BET Soul 172 Adult Alternative 611 Freeform 42 853 5StarMax 220 CBS (WGCL) 12 804 Big Ten Network 142 750 Alt Country / Americana 620 FX 71 805 ActionMax 221 225 / 912 Coweta County Schools 7 Big Ten Network 2 749 Alternative Rock Classics 610 FX Movies 76 861 MoreMax 217 224 / 911 COZI TV (WGCL) 788 Boomerang 128 Bluegrass 621 FXX 66 891 MovieMax 223 FOX (WAGA) 5 802 CMT Music 171 Broadway 638 Golf Channel 27 818 OuterMax 222 GPB Create (WGTV) 791 CNN Español 150 Chamber Music 639 Great American Country 78 865 ThrillerMax 218 GPB Knowledge (WGTV) 792 Destination America 158 Classic Masters 637 Hallmark Channel 73 855 Flix 272 GRIT (WGCL) 789 Discovery Español 159 Classic RnB & Soul 602 HGTV 43 838 HBO 201 200 / 900 HSN 16 806 Discovery Family 155 Classic Rock 606 History Channel 49 812 HBO 2 202 207 / 901 ION Television (WPXA) 18 871 Discovery Life Channel 141 Country Classics 619 HLN 55 872 HBO Comedy 206 JusticeTV (WXIA) 786 Disney Junior 129 896 Dance Clubbin’ 603 IFC 102 892 HBO Family 204 208 / 902 LAFF (WSB) 790 Disney XD 131 851 Easy Listening 629 Inspirational Network 96 HBO Signature 203 209 / 903 Movies! (WAGA) -

PATIENT GUIDE FREE! Take This Key Information for Your Stay Copy Home with You
PATIENT GUIDE FREE! Take This Key Information For Your Stay Copy Home With You PATIENT STORY BEATING BREAST CANCER The Power of Love Brought to you by: We’re taking quality care to new heights #1 Large Hospital in Georgia for 3 of the past 4 years – Georgia Trend magazine Ranked among the Top 100 U.S. Hospitals for Medical Excellence In Hospital Care for 3 of the past 4 years – Care Chex® Rating System Named to the 100 Great Community Hospitals list for 2016 – Becker’s Hospital Review At WellStar West Georgia Medical Center, we believe in life well lived. While we are proud to be recognized for our longstand- ing commitment to delivering quality care to our patients, it’s even more rewarding to us that you have access to exceptional healthcare right here at home. That means less time on the road and more time living life to the fullest. We believe in life well-lived. WellStar West Georgia Medical Center 1514 Vernon Road To learn more and find a physician, LaGrange, Georgia 30240 visit wellstar.org/wgmc 706.882.1411 WEST GEORGIA HEALTH FOUNDATION West Georgia Health Foundation the name and address of the center must house all cancer raises money for facility person we should notify. services under one roof. Cancer enhancements, technology Community Cancer Center navigators, genetics counseling, additions and service expansions WGMC has provided quality a resource center and support at WellStar West Georgia cancer care for generations and groups also will be housed here. Medical Center. Created in is investing in oncology staff, Donations for this project are tax 2004, our first campaign raised advanced technologies and deductible and will be matched $5.1 million for an expanded lifesaving treatments to better by Callaway Foundation, Inc. -

All Full-Power Television Stations by Dma, Indicating Those Terminating Analog Service Before Or on February 17, 2009
ALL FULL-POWER TELEVISION STATIONS BY DMA, INDICATING THOSE TERMINATING ANALOG SERVICE BEFORE OR ON FEBRUARY 17, 2009. (As of 2/20/09) NITE HARD NITE LITE SHIP PRE ON DMA CITY ST NETWORK CALLSIGN LITE PLUS WVR 2/17 2/17 LICENSEE ABILENE-SWEETWATER ABILENE TX NBC KRBC-TV MISSION BROADCASTING, INC. ABILENE-SWEETWATER ABILENE TX CBS KTAB-TV NEXSTAR BROADCASTING, INC. ABILENE-SWEETWATER ABILENE TX FOX KXVA X SAGE BROADCASTING CORPORATION ABILENE-SWEETWATER SNYDER TX N/A KPCB X PRIME TIME CHRISTIAN BROADCASTING, INC ABILENE-SWEETWATER SWEETWATER TX ABC/CW (DIGITALKTXS-TV ONLY) BLUESTONE LICENSE HOLDINGS INC. ALBANY ALBANY GA NBC WALB WALB LICENSE SUBSIDIARY, LLC ALBANY ALBANY GA FOX WFXL BARRINGTON ALBANY LICENSE LLC ALBANY CORDELE GA IND WSST-TV SUNBELT-SOUTH TELECOMMUNICATIONS LTD ALBANY DAWSON GA PBS WACS-TV X GEORGIA PUBLIC TELECOMMUNICATIONS COMMISSION ALBANY PELHAM GA PBS WABW-TV X GEORGIA PUBLIC TELECOMMUNICATIONS COMMISSION ALBANY VALDOSTA GA CBS WSWG X GRAY TELEVISION LICENSEE, LLC ALBANY-SCHENECTADY-TROY ADAMS MA ABC WCDC-TV YOUNG BROADCASTING OF ALBANY, INC. ALBANY-SCHENECTADY-TROY ALBANY NY NBC WNYT WNYT-TV, LLC ALBANY-SCHENECTADY-TROY ALBANY NY ABC WTEN YOUNG BROADCASTING OF ALBANY, INC. ALBANY-SCHENECTADY-TROY ALBANY NY FOX WXXA-TV NEWPORT TELEVISION LICENSE LLC ALBANY-SCHENECTADY-TROY AMSTERDAM NY N/A WYPX PAXSON ALBANY LICENSE, INC. ALBANY-SCHENECTADY-TROY PITTSFIELD MA MYTV WNYA VENTURE TECHNOLOGIES GROUP, LLC ALBANY-SCHENECTADY-TROY SCHENECTADY NY CW WCWN FREEDOM BROADCASTING OF NEW YORK LICENSEE, L.L.C. ALBANY-SCHENECTADY-TROY SCHENECTADY NY PBS WMHT WMHT EDUCATIONAL TELECOMMUNICATIONS ALBANY-SCHENECTADY-TROY SCHENECTADY NY CBS WRGB FREEDOM BROADCASTING OF NEW YORK LICENSEE, L.L.C. -
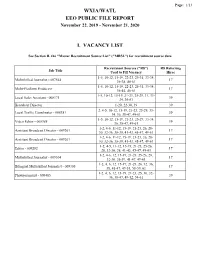
Wxia/Watl Eeo Public File Report I. Vacancy List
Page: 1/13 WXIA/WATL EEO PUBLIC FILE REPORT November 22, 2019 - November 21, 2020 I. VACANCY LIST See Section II, the "Master Recruitment Source List" ("MRSL") for recruitment source data Recruitment Sources ("RS") RS Referring Job Title Used to Fill Vacancy Hiree 1-5, 10-12, 15-19, 22-23, 25-31, 33-34, Multiskilled Journalist - 007544 17 36-38, 40-61 1-5, 10-12, 15-19, 22-23, 25-31, 33-34, Multi-Platform Producevr 17 36-44, 46-61 1-5, 10-12, 15-19, 21-23, 25-29, 31, 33- Local Sales Assistant - 008171 39 34, 36-61 Broadcast Director 1-20, 22-30, 39 39 2, 4-5, 10-12, 15-19, 21-23, 25-29, 33- Local Traffic Coordinator - 008381 39 34, 36, 38-47, 49-61 1-5, 10-12, 15-19, 21-23, 25-29, 33-34, Video Editor - 008385 39 36, 38-47, 49-61 1-2, 4-6, 11-12, 15-19, 21-23, 26, 28- Assistant Broadcast Director - 009261 17 30, 32-36, 38-39, 41-43, 45-47, 49-61 1-2, 4-6, 11-12, 15-19, 21-23, 26, 28- Assistant Broadcast Director - 009261 17 30, 32-36, 38-39, 41-43, 45-47, 49-61 1-2, 4-5, 11-12, 15-19, 21-23, 25-26, Editor - 009282 17 28, 32-36, 38, 41-43, 45-47, 49-61 1-2, 4-6, 12, 15-19, 21-23, 25-26, 28, Multiskilled Journalist - 009304 17 32-36, 38-39, 41-47, 49-61 1-2, 4, 6, 12, 15-19, 21-23, 26, 32, 36, Bilingual Multiskilled Journalist - 009305 17 38, 41-47, 49-55, 58-59, 61 1-2, 4, 6, 12, 15-19, 21-23, 25, 30, 32- Photojournalist - 009485 39 36, 38-47, 49-52, 54-61 Page: 2/13 WXIA/WATL EEO PUBLIC FILE REPORT November 22, 2019 - November 21, 2020 II. -

PUBLIC NOTICE News Media Information 202 / 418-0500 Fax-On-Demand 202 / 418-2830 Federal Communications Commission TTY 202 / 418-2555 445 12Th St., S.W
PUBLIC NOTICE News media information 202 / 418-0500 Fax-On-Demand 202 / 418-2830 Federal Communications Commission TTY 202 / 418-2555 445 12th St., S.W. Internet: http://www.fcc.gov ftp.fcc.gov Washington, D.C. 20554 REPORT NO: 1366 MEDIA BUREAU REGISTRATIONS August 6, 2003 This Public Notice has been generated by the Media Bureau’s from the Cable Operations & Licensing Systems (COALS). This Public Notice is intended to list newly registered Community Unit Identification (CUID) Numbers. This Public Notice lists those filings processed by the Media Bureau as registrations pursuant to §76.1801 of the Commission's Rules. Should any of these registrations contain a request for special relief, such waiver requests will be handled separately through the special relief process. Furthermore, parties seeking special relief are advised that such requests must be initiated through the special relief provisions of §76.7 of the Rules. Files containing these registrations can be reviewed in the Commissions Reference Information Center, CY-Level, 445 12th Street, SW Washington, DC 20554. It is requested that all responses or statements refer to the FCC assigned Community Unit Identification (CUID) Number; e.g., AL0075. For further information about this Public Notice contact the Media Bureau at (202) 418-7000. REPORT NO: 1366 MEDIA BUREAU REGISTRATIONS August 6, 2003 CUID CODE COMMUNITY COUNTY COMMUNITY TYPE LEGAL NAME CALL SIGNS CORRECTION GA1059 BETWEEN WALTON INCOR TOWN MONROE GEORGIA WSB WATER LIGHT AND GAS WHSG COMMISSION WUVG WATL WAGA WTBS WPBA -

Atlanta Broadcast Television Channel Line-Up
ATLANTA BROADCAST TELEVISION CHANNEL LINE-UP Display RF ChannelP.S.I.P. ID Network/Programming Broadcasting Antenna Tower Location City Of License (if not Atlanta) 2.1 39.1 WSB-HD ABC Freedom Parkway Atlanta, GA 2.2 39.2 WSB-SD Me TV Freedom Parkway Atlanta, GA 4 x WUVM-LP Azteca America North Druid Hills Atlanta, GA 5.1 27.3 WAGA-HD FOX North Druid Hills Atlanta, GA 7.1 7.3 WCIQ-DT PBS (Alabama Public Television) Mt. Cheaha, AL Cheaha Mountain, AL 7.2 7.4 WCIQ-D1 PBS World Mt. Cheaha, AL Cheaha Mountain, AL 7.3 7.5 WCIQ-D2 Create TV Mt. Cheaha, AL Cheaha Mountain, AL 8.1 8.1 GPB HD PBS (Georgia Public Broadcasting) Stone Mountain Athens/Atlanta, GA 8.2 8.2 Kids PBS Kids Stone Mountain Athens/Atlanta, GA 8.3 8.3 Knowled PBS World / GPB Knowledge Stone Mountain Athens/Atlanta, GA 11.1 10.3 WXIA-TV NBC Arizona Avenue Atlanta, GA 11.2 10,4 WXIA-WX 11Alive WIZtv powered by Accuweather Arizona Avenue Atlanta, GA 14.1 51.3 ION Ion Bear Mountain Rome, GA 14.2 51.4 qubo Qubo Bear Mountain Rome, GA 14.3 51.5 IONLife Ion Life Bear Mountain Rome, GA 14.4 51.6 ShopTV ShopTV (Infomercials) Bear Mountain Rome, GA 16.1 16.1 WYGA-LD N/A (Color Bars) Inman Park/Reynoldstown Atlanta, GA 16.2 16.2 SBN Sonlife Broadcasting Network Inman Park/Reynoldstown Atlanta, GA 16.3 16.3 PunchTV Punch TV Network Inman Park/Reynoldstown Atlanta, GA 16.4 16.4 WYGA-LD N/A (Color Bars) Inman Park/Reynoldstown Atlanta, GA 16.5 16.5 PeaceTV Peace TV (Islamic) Inman Park/Reynoldstown Atlanta, GA 16.6 16.6 M Canal N/A (Color Bars) Inman Park/Reynoldstown Atlanta, GA 17.1 20.3 WPCH-DT Peachtree TV North Druid Hills Atlanta, GA 18.1 33.1 WNGH-DT PBS (Georgia Public Broadcasting) Chatsworth, GA Chatsworth/Dalton, GA 18.2 33.2 Kids PBS Kids Chatsworth, GA Chatsworth/Dalton, GA 18.3 33.3 Knowled PBS World / GPB Knowledge Chatsworth, GA Chatsworth/Dalton, GA 22.1 22.1 WSKC-CD Fuxion TV (African/Caribbean) Satelite Blvd. -

Weathernation TV Partners with 11ALIVE WXIA to Provide Innovative, Accurate, 24/7 Weather Reporting to Atlanta TV Viewers
WeatherNation TV Partners with 11ALIVE WXIA to Provide Innovative, Accurate, 24/7 Weather Reporting to Atlanta TV Viewers WeatherNation TV and 11ALIVE Offer Atlanta Viewers In-depth Coverage on WXIA’s Digital Channel 11.2, Comcast Channel 211 and Charter Channel 84 ATLANTA – Oct. 1 2013 – Today, WeatherNation TV, Inc., announced its partnership with 11ALIVE WXIA to broadcast 24/7 weather news on Atlanta’s digital TV channel 11.2, on Comcast Channel 211, and on Charter Cable 84 serving the Atlanta market. WeatherNation TV currently operates in cities across America, including Chicago, Boston, Minneapolis, Seattle and Denver and is expanding its reach rapidly. WeatherNation TV affords viewers reliable and current local, regional and national weather news all day, every day. “We are thrilled to be partnering with 11ALIVE in Atlanta – one of our largest partnerships to date and in a top 10 media market,” said Michael Norton, president of WeatherNation TV. “With this collaboration, more than 6 million people in the Atlanta area will have access to our accurate, 24/7, real time local and national TV weather reporting from an expanded team of top- notch meteorologists.” “We love that the Atlanta community will now be able to have a live weather channel 24/7 with local updates every five minutes,” said John Deushane, president and general manager of 11ALIVE. “WeatherNation brings world-class technology and additional professional talent that will provide more of the quality weather coverage viewers have come to expect from the Networks of 11ALIVE.” “We are excited to be partnering with WeatherNation to provide 24/7 continuous weather coverage on our digital channel 11.2,” said Mike Francis, Chief Meteorologist for WXIA. -

WSB-2 (ABC) 2 CNNI (CNN International) 205
Sattec Inc. 719 W. Lanier Ave. Suite B Fayetteville, GA 30214 404-396-8998 (Direct) AT&T U-Verse Channel Line Up 404-935-6171 (Office) Trust only the Pro with your TV! WSB-2 (ABC) 2 CNNI (CNN International) 205 Planet Green 465 WUVM-4 (AZTECA) 4 FOX News Channel 210 Discovery Fit & Health 466 WAGA-5 (FOX) 5 Fox Business Network 211 ION Life 468 Atlanta Interfaith Broadcasters 6 MSNBC 215 Wealth TV 470 WGTV-8 (PBS) 8 CNBC 216 tvMall 471 QVC 10 CNBC World 217 SWRV 501 WXIA-11 (NBC) 11 Bloomberg Television 222 MTV (Music Television) 502 Home Shopping Network (HSN) 12 The Weather Channel 225 MTV2 504 WPXA-14 (ION) 14 BUY TV 228 Tr3s 506 WPCH-17 (IND) 17 C-SPAN 230 MTV Jams 508 WKTB-LD-47 (TEL) 18 C-SPAN2 231 MTV Hits 509 WPBA-30 (PBS) 30 C-SPAN3 232 mtvU 510 WUVG-34 (UNI) 34 ABC News Now 243 Centric 515 WATL-36 (MY NETWORK TV) 36 BuyIt2 247 BET Gospel 516 As Seen On TV 37 TLC 250 VH1 518 WGCL-46 (CBS) 46 Animal Planet 252 VH1 Classic 520 WATC-57 (IND) 57 Travel Channel 254 VH1 Soul 522 WHSG-63 (TBN) 63 History 256 CMT (Country Music Television) 525 WUPA-69 (CW) 69 H2 257 CMT Pure Country 527 Valu TV 82 Science 258 Great American Country (GAC) 529 AT&T U-verse Shopping 1 84 Military Channel 259 fuse 535 U-verse Message Channel 93 Investigation Discovery 260 FUEL TV 536 AT&T U-verse Front Row 100 NASA TV 264 TBN - Trinity Broadcasting Network 560 AT&T Pay Per View Schedule 101 National Geographic Channel 265 Eternal Word Television Network (EWTN) 562 TNT (Turner Network TV) 108 Nat Geo WILD 266 Daystar 563 TNT (Turner Network TV) - West 109 BIO 272 INSP (Inspiration Network) 564 TBS 112 Military History Channel 276 The Church Channel 565 TBS - West 113 AT&T U-verse Buzz 300 FamilyNet 566 Smithsonian Channel 118 Disney Channel 302 BYU 567 Discovery Channel 120 Disney XD 304 JCTV 570 USA Network 124 Nickelodeon 314 The Word Network 575 FX Network 128 Nick2 316 World Harvest Television 578 A&E 132 Nicktoons 318 FAITH 580 E! Entertainment TV 134 Nick Jr. -

TV Station WAGA • Analog Channel 5, DTV Channel 27 • Atlanta, GA Expected Operation on June 13: Licensed
TV Station WAGA • Analog Channel 5, DTV Channel 27 • Atlanta, GA Expected Operation on June 13: Licensed Digital License (solid): 1000 kW ERP at 332 m HAAT, Network: Fox vs. Analog (dashed): 100 kW ERP at 328 m HAAT, Network: Fox Market: Atlanta, GA TN-4 Marion Bradley Cherokee Clay Macon Hamilton Polk Pickens TN-3 NORTH NC-11 AL-5 Dade Catoosa Towns Fannin Jackson Rabun Murray Union Dalton Oconee Whitfield Walker Gilmer SC-3 GA-9 Habersham AL-4 White Lumpkin Stephens DeKalb Gordon Fort Payne Chattooga Pickens Dawson Hall Banks Franklin Hart Gainesville Rome Bartow Forsyth Floyd Cherokee GA-10 Cherokee GA-6 Jackson Madison Elbert GA-11 Acworth Etowah Polk Barrow Clarke Cobb Lawrenceville Athens Paulding GwinnettGA-7 Oglethorpe Calhoun Haralson A5 D27 Walton Oconee Wilkes Atlanta GA-4 Douglas GA-5 DeKalb Rockdale Cleburne Fulton Covington Carrollton Clayton Morgan Greene Carroll GA-13 Newton Taliaferro Fayette Henry Peachtree City Coweta Jasper Clay Heard Putnam Randolph Spalding Butts Hancock GA-3 GA-12 Meriwether Pike Lamar Milledgeville LaGrange Baldwin Troup Monroe Jones Tallapoosa Washington Chambers Upson AL-3 Macon Bibb GA-8 Wilkinson Harris Talbot Crawford Opelika GA-2 Twiggs Taylor Lee Peach Laurens 2009 Hammett & Edison,Muscogee Inc. Houston 10MI 0 10 20 30 40 50 100 80 60 40 20 0 KM 20 Coverage gained after DTV transition Analog service 4,596,045 persons Digital service 4,723,912 No symbol = no change in coverage Analog loss 23,867 Coverage lost but still served by same network Digital gain 151,734 Coverage lost and no other service by same network Net gain 127,867 BLCDT-20060728AEL Map set 1 WAGA Digital License TV Station WAGA • Analog Channel 5, DTV Channel 27 • Atlanta, GA Approved Post-Transition Operation: Licensed Digital License (solid): 1000 kW ERP at 332 m HAAT, Network: Fox vs. -

Download Annual Report
Trusted Voices Delivering Results 2020 ANNUAL REPORT A TEGNA Key Financial Metrics 2020 Results $2.9B $1.3B Total Revenue Subscription Revenue 28% growth 28% growth compared to 2019 compared to 2019 33% growth 53% growth compared to 2018 compared to 2018 $446M $483M $1B Political Revenue GAAP Net Income in Adjusted EBITDA* 91% growth 69% growth 45% growth compared to 2018 compared to 2019 compared to 2019 19% growth 31% growth compared to 2018 compared to 2018 * “Adjusted EBITDA,” a non-GAAP measure, is defined as net income attributable to the Company before (1) net loss attributable to redeemable noncontrolling interest, (2) income taxes, (3) interest expense, (4) equity income in unconsolidated investments, net, (5) other non-operating items, net, (6) workforce restructuring expense, (7) M&A due diligence costs, (8) acquisition-related costs, (9) advisory fees related to activism defense, (10) spectrum repacking reimbursements and other, net, (11) depreciation and (12) amortization. Superior 2- and 3-Year TSR1 Since Becoming a Pure-Play Broadcasting Company 33.5% 2-Year (2019-2020) 21.4% 3-Year 5.5% (2018-2020) TEGNA 2.3% Peer Median 0 5 10 15 20 25 30 35 1 Total shareholder return includes impact of stock price performance and reinvested dividends. Peer set is E.W. Scripps, Gray TV, Meredith, Nexstar and Sinclair. Five Pillars of Value Creation Driving Strong Growth Aggressive, yet Commitment to disciplined pursuit Growth strong free cash Best-in-class of accretive M&A, through organic Maintain a strong flow generation operator including adjacent innovation, such balance sheet and optimized businesses and as Premion capital allocation technologies process 2021 Annual Guidance Subscription Revenue Growth +Mid to High-Teens percent Non-GAAP Corporate Expense $44 - $48 million Depreciation $62 - $66 million Amortization $60 - $65 million Interest Expense $187 - $192 million Capital Expenditures $64 - $69 million Including Non-Recurring Capital Expenditures $20 - $22 million Effective Tax Rate 24.0 – 25.0% Net Leverage Ratio Mid 3x Free Cash Flow as a % of est. -

Technical Summary WPXH-TV Hoover, Alabama Channel 33 300 Kw 318.4
Technical Summary WPXH-TV Hoover, Alabama Channel 33 300 kW 318.4 (HAAT) ION Media License Company, LLC (“ION”) licensee of television station WPXH-TV, Facility ID 73312, Hoover, Alabama (the “Station”) hereby amends its pending construction permit application seeking authority to relocate its transmitter from the currently authorized site to a site that will accommodate post-repack operations (FCC LMS File No. 0000034874). This application is necessary because ION does not have access to its current tower for post-repack operations. Following the Commission’s assignment of post-repack facilities to WPXH-TV, ION was unable to reach accommodation with the tower landlord that would permit the station to continue operating from its current site. This forced ION to identify a new site for the station’s post-repack operations. Before selecting the proposed tower site, ION performed a comprehensive analysis of available tower sites in the Birmingham market. In the immediate vicinity of the current tower site, ION’s market analysis found no acceptable alternatives that would provide equivalent interference-free coverage as compared to the Station’s pre-auction or authorized post-auction facilities. ION determined that the proposed site would provide the best option due to its structural capability and coverage performance, with minimal or no interference to other full- power broadcast stations. The new tower is located 55 kilometers to the southwest of the current site. Accordingly, the Station’s proposed noise limited service contour (“NLSC”) will shift to the southwest, resulting in some areas of service gain and loss. Figure 1 shows the loss area and the stations predicted to serve the loss areas using the Commission’s standard prediction methodology. -

2 2.1 Wsb Escape 2.2 Wsb Laff 2.3 Tbs 3.1 Tnt 4.1 Waga-Tv Fox-5 5.1 Waga-Movies!
WSB-TV ABC -2 2.1 CCTV4 16.5 WSB- BOUNCE 2.2 NTD 16.6 WSB- Dabl 2.3 Estrella 16.8 TBS 3.1 PEACHTREE TV 17.1 TNT 4.1 GAME SHOW NETWORK 18.1 WAGA-TV FOX-5 5.1 OWN 19.1 WAGA-MOVIES! 5.2 ANIMAL PLANET 20.1 WAGA-BUZZER 5.3 FOOD 21.1 WAGA-theGrio 5.4 E! Entertainment 22.1 WAGA-DECADES 5.5 LIFETIME 23.2 FREEFORM 6.1 FX 24.1 BET 7.1 The LEARNING CHANNEL 25.1 WGTV- GPB-8 8.1 WMRE 26.1 WGTV-CREATE 8.2 TV GUIDE 27.1 UNIVESAL KIDS 8.3 EDUNET 28.1 CheddarU 9.1 EDUNET 28.2 MTV LIVE 10.1 EDUNET 28.3 WXIA NBC-11 11.1 EDUNET 28.4 WXIA-TRUE CRIME 11.3 TRAVEL 29.1 WXIA- QUEST 11.4 WPBA PBA-30 30.1 VH1 12.1 THE WEATHER CHANNEL 31.1 MTV 13.1 ME TV -Atlanta 32.1 WPXA- ION-14 14.1 HEROES & ICONS -WGTA 32.2 WPXA- COURT TV 14.2 USA 33.1 WPXA-LAFF 14.3 WUVG UNIVISION-34 34.1 WPXA-/MYSTREY 14.4 Paramount 35.1 WPXA-DEFY 14.5 WATL My-36 36.1 WPXA-TRUE REAL 14.6 WATL-this 36.2 HGTV 15.1 WATL ANTENNA TV 36.3 WUVM-LP AZTECA 16.1 ESPN 37.1 WKTB TELEMUNDO 16.2 ESPN2 38.1 WKTB-KBS 16.3 ESPN NEWS 39.1 TVK 16.4 ESPN U 40.1 A&E 41.1 HALLMARK 43.1 WUPA-FAVE TV 69.5 COMEDY CENTRAL 44.1 WUPA-CHARGE 69.6 INDEPENDENT FILM CHANNEL 45.1 WE 70.1 WGCL CBS-46 46.1 FYI 71.1 WGCL -COZI 46.2 SEC NETWORK 72.1 WGCL-GRIT 46.3 Bally SPORTS SOUTH 73.2 BLOOMBERG TV 47.1 Bally SPORTS SOUTHEAST 74.1 MSNBC 48.1 GOLF 75.1 FOX NEWS 49.1 SEC FHDA 76.1 CNN HLN 50.1 FS1 78.1 CNN 51.1 NBC SPORTS 79.1 CNBC 52.1 NFL 80.1 FOX BUSINESS 53.1 CBS SPORTS NETWORK 81.1 CSPAN 54.1 FXX 82.1 CSPAN2 55.1 INVESTIGATION DISCOVERY 83.1 CSPAN3 56.1 SCIENCE 84.1 HISTORY 57.1 OXYGEN 85.1 BRAVO 58.1 UP 86.1 AMERICAN MOVIE