Social Media, Elections, and Democracy in West Africa
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

World Bank Document
Document of The World Bank Public Disclosure Authorized Report No: ICR3058 IMPLEMENTATION COMPLETION AND RESULTS REPORT (IDA-41640 P100785) ON A Public Disclosure Authorized CREDIT IN THE AMOUNT OF SDR 30.90 MILLION (US$46.65 MILLION EQUIVALENT) TO THE FEDERAL REPUBLIC OF NIGERIA IN SUPPORT OF THE SECOND PHASE OF WEST AND CENTRAL AFRICA AIR TRANSPORT SAFETY AND SECURITY Public Disclosure Authorized PROGRAM March 28, 2014 Transport Sector Country Department AFCW2 Africa Region Public Disclosure Authorized CURRENCY EQUIVALENTS (Exchange Rate Effective May 31, 2013) Currency Unit = Nigerian Naira (NGN) SDR 1.00 = US$1.50 US$1.00 = NGN 158.80 FISCAL YEAR January 1 – December 31 ABBREVIATIONS AND ACRONYMS AFTN Aeronautical Fixed Telecommunication Network APL Adaptable Program Lending ATN Air Telecommunications Network BAG Banjul Accord Group BAGASOO Banjul Accord Group Safety Oversight Organization CAA Civil Aviation Authority CCTV Closed Circuit Television CPS Country Partnership Strategy DME Distance Measuring Equipment ECOWAS Economic Community of Western African States ERGP Economic Reform and Governance Project ESIA Environmental and Social Impact Assessment ESMF Environmental and Social Management Framework ESMP Environmental and Social Management Plan FAA Federal Aviation Administration (United States) FAAN Federal Airports Authority of Nigeria FM Financial Management FMA Federal Ministry of Aviation FMOF Federal Ministry of Finance FMOT Federal Ministry of Transportation FMR Financial Management Report GDP Gross Domestic Product GON -
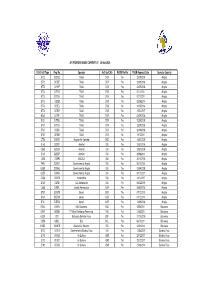
Amended Master AFI RVSM Height Monitoring 26 Aug 2020.Xlsx
AFI RVSM DATABASE CURRENT AT 26 Aug 2020 ICAO Acft Type Reg. No. Operator Acft Op ICAO RVSM Yes/No RVSM Approval Date Operator Country B772 D2TED TAAG DTA Yes 23/09/2008 Angola B772 D2TEE TAAG DTA Yes 23/09/2008 Angola B772 D2TEF TAAG DTA Yes 23/09/2008 Angola B773 D2TEG TAAG DTA Yes 01/11/2011 Angola B773 D2TEH TAAG DTA Yes 01/11/2011 Angola B773 D2TEI TAAG DTA Yes 25/06/2014 Angola B773 D2TEJ TAAG DTA Yes 10/05/2016 Angola B773 D2TEK TAAG DTA Yes 15/02/2017 Angola B737 D2TBF TAAG DTA Yes 23/09/2008 Angola B737 D2TBG TAAG DTA Yes 23/09/2008 Angola B737 D2TBH TAAG DTA Yes 23/09/2008 Angola B737 D2TBJ TAAG DTA Yes 23/09/2008 Angola B737 D2TBK TAAG DTA Yes 19/12/2011 Angola C750 D2EZR Angolan Air Operator DCD Yes 18/02/2009 Angola E145 D2FDF AeroJet IGA Yes 23/07/2018 Angola C560 D2EBA AeroJet IGA Yes 29/07/2009 Angola E145 D2EBP AeroJet IGA Yes 29/08/2013 Angola C550 D2EPI EMCICA IGA Yes 30/11/2016 Angola F900 D2ANT Government of Angola IGA Yes 05/11/2014 Angola GLEX D2ANG Government of Angola IGA Yes 23/04/2008 Angola GLEX D2ANH Government of Angola IGA Yes 04/12/2017 Angola C550 D2GES Humbertico IGA Yes 19/12/2017 Angola E135 D2FIA SJL Aeronautica IGA Yes 08/02/2019 Angola C680 D2EPL Socolil-Aeronautica SOR Yes 28/03/2018 Angola B737 D2EWS Sonair SOR Yes 07/12/2010 Angola B737 D2EVW Sonair SOR Yes 07/12/2010 Angola B721 D2ESU Sonair SOR Yes 13/09/2006 Angola BE40 A2WIN NAC Botswana NAC Yes 29/04/2011 Botswana BE40 A2DBK FT Meat Packaging Processing IGA Yes 13/05/2011 Botswana GLEX OK1 Botswana Defence Force BDF Yes 21/10/2009 Botswana C550 A2BCL BCL BCL Yes 06/10/2011 Botswana H25B A2MCB Kalahari Air Services IGA Yes 23/01/2013 Botswana B722 XTBFA Government of Burkina Faso IGA Yes 12/04/2007 Burkina Faso E170 XTABS Air Burkina VBW Yes 29/12/2017 Burkina Faso E170 XTABT Air Burkina VBW Yes 29/12/2017 Burkina Faso E190 XTABV Air Burkina VBW Yes 27/06/2019 Burkina Faso E190 XTABY Air Burkina VBW Yes 27/06/2019 Burkina Faso E190 XTABZ Air Burkina VBW Yes 27/06/2019 Burkina Faso B752 D4CBP TACV. -

ATPI NL Advisory 2020 / 26 MAR
ATPI NL Advisory 2020 / 26 MAR ATPI Alerts Travel Restrictions per Country due to Coronavirus (COVID-19) Dear Valued Client, Countries all over the world are implementing travel bans and restrictions in an effort to limit the spread of the COVID pandemic outbreak. Below you may find the most recent bans in short. Note that unexpected travel cancellations are taking place and airlines status may change at any given time without prior notice. The enlisted information are based on the officially announced governmental travel restrictions and quarantine measures. To receive up to date travel information 24/7, we highly suggest that you also enroll to ATPI Alerts (more info on subscription details at the end of the text). Below is a summary of the latest updates, please be aware it is not a complete overview of all current travel bans and restrictions. EUROPEAN COUNTRIES: 1. UK: London: London City Airport to close until end of April because of COVID-19. They will suspend all commercial and private flights from Wednesday evening, 25th March until the end of April following Britain's order that people should stay at home and stop travelling. 2. UK: the UK government advised to close all UK hotels. ATPI would recommend the traveller calls ahead on the day of arrival to check the hotel is still open. 3. France: Paris Orly: is to close from midnight on March 31, operator Aéroports de Paris has confirmed. Orly’s few remaining flights will be transferred to Paris CDG – the capital’s main airport. 4. France: Metro, bus and tram services in Paris will be severely restricted from Thursday onwards because of COVID-19. -

Fatigue Occurrence, Perception, Knowledge and the Utilization of Its Coping Mechanisms by Commercial Aircrew in Nigeria
FATIGUE OCCURRENCE, PERCEPTION, KNOWLEDGE AND THE UTILIZATION OF ITS COPING MECHANISMS BY COMMERCIAL AIRCREW IN NIGERIA SUBMITTED BY DR OSAGIE KENNETH COLE DEPARTMENT OF COMMUNITY HEALTH AND PRIMARY CARE ,LAGOS UNIVERSITY TEACHING HOSPITAL,IDI-ARABA LAGOS TO THE NATIONAL POSTGRADUATE MEDICAL COLLEGE OF NIGERIA IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE AWARD OF THE FINAL FELLOWSHIP OF THE FACULTY OF PUBLIC HEALTH (FMCPH). NOVEMBER 2012 DECLARATION I hereby declare that this Research work titled “FATIGUE OCCURRENCE, PERCEPTION, KNOWLEDGE AND THE UTILIZATION OF ITS COPING MECHANISMS BY COMMERCIAL AIRCREW IN NIGERIA” is my original work and was done by me under appropriate supervision, and any assistance given has been duly acknowledged. I also declare that this dissertation has not been submitted anywhere else in part or in full for any other examination. ……………………………………….. ……………………….. Dr Osagie Kenneth Cole Date Department of Community Health and primary care , Lagos University Teaching Hospital Idi Araba ,Lagos state ii CERTIFICATION I hereby certify that this study titled “FATIGUE OCCURRENCE, PERCEPTION, KNOWLEDGE AND THE UTILIZATION OF ITS COPING MECHANISMS BY COMMERCIAL AIRCREW IN NIGERIA” was carried out by Dr Osagie Kenneth Cole under my direct supervision and to the best of my knowledge has not been submitted for any other examination or for publication in any journal. Prof A T Onajole …………………………….… (MPH,FMCPH) Signature and date Department of Community Health Lagos University Teaching Hospital Idi-Araba, Lagos Dr K A Odeyemi ………………………………… (MPH,FMCPH) Signature and date Head of Department, Department of Community Health Lagos University Teaching Hospital Idi-Araba, Lagos iii ACKNOWLEDGEMENTS I wish to most sincerely thank the Almighty God who strengthened me, gave exceedingly abundant grace and opened unbelievable windows of opportunity to make this project a reality. -

Aircraft Accident Report Dana/2012/06/03/F
v AIRCRAFT ACCIDENT REPORT DANA/2012/06/03/F Accident Investigation Bureau Report on the Accident to DANA AIRLINES NIGERIA LIMITED Boeing MD-83 aircraft with registration 5N-RAM which occurred at Iju-Ishaga Area of Lagos State, Nigeria On 3rd June 2012 Published by Accident Investigation Bureau, of Nigeria Aircraft Accident Report DANA/2012/06/03/F 5N-RAM This Report is produced by the Accident Investigation Bureau (AIB), Murtala Muhammed International Airport, Ikeja, Lagos. The Report is based upon the investigation carried out by Accident Investigation Bureau, in accordance with Annex 13 to the Convention on International Civil Aviation, Nigerian Civil Aviation Act 2006, and Civil Aviation (Investigation of Air Accidents and Incidents) Regulations. It is not the purpose of aircraft accident/serious incident investigations to apportion blame or liability. Readers are advised that Accident Investigation Bureau investigates for the sole purpose of enhancing aviation safety. Consequently, Accident Investigation Bureau reports are confined to matters of safety significance and should not be used for any other purpose. As the Bureau believes that safety information is of great value if it is passed on for the use of others, readers are encouraged to copy or reprint for further distribution, acknowledging Accident Investigation Bureau, Nigeria as the source. Recommendations in this report are addressed to the regulatory Authorities of the state (NCAA). It is for this authority to ensure enforcement. © Copyright: Accident Investigation Bureau, Nigeria Printed in Nigeria for the Accident Investigation Bureau (AIB) ii Aircraft Accident Report DANA/2012/06/03/F 5N-RAM TABLE OF CONTENTS GLOSSARY OF ABBREVIATIONS USED IN THIS REPORT ......................... -

Causal Factors of Flight Delay in Nigerian Airport: a Case Study of Murtala Muhammed International Airport
Bangladesh Journal of Multidisciplinary Scientific Research; Vol. 1, No. 2 ISSN 2687-850X E-ISSN 2687-8518 July-September; 2019 Published by Centre for Research on Islamic Banking & Finance and Business Causal Factors of Flight Delay in Nigerian Airport: A Case Study of Murtala Muhammed International Airport Ayo-Agunbiade Oluwafisayo T. Department of Transport Management Technology Federal University of Technology Akure, Nigeria E-mail: [email protected] Stephens Mobolaji S. Department of Transport Management Technology Federal University of Technology Akure, Nigeria E-mail: [email protected] Abstract Delay is a prominent event mostly experienced at the airport by both airline and passengers. Globally delay is permitted at 15mins later than the scheduled time. Assessing the level of delay in the airport is a major criterion for measuring airport performance. Aircraft not adhering to schedule flight results in increased airport congestion, cancellation flight and flight delay. This study made use of primary data through well-structured questionnaires to obtain information from selected NAMA Staff at the Murtala Muhammed International Airport (MMIA). Operational delay report for a month and Airlines flight were examined for two months under the MMA2 to know the deviation of scheduled flight time from actual flight time. Descriptive Analysis, Wilcoxon Rank test, Factor Analysis and Step Wise Regression were the statistical tools deployed for this research. Findings showed that on a monthly base, 63% of the domestic traffic flows are delayed. Some factors responsible for delay were considered: aircraft damage, bad weather, aircraft maintenance, VIP movement and fueling are the major factor responsible for delay of aircraft Movement. -

Significant Variables Currently Influencing Air Travelers' Preference for Domestic Airlines in Nigeria
“Significant variables currently influencing air travelers’ preference for domestic airlines in Nigeria” Ben Sidiq AUTHORS Mobolaji Stephens Wilfred Ukpere Ben Sidiq, Mobolaji Stephens and Wilfred Ukpere (2020). Significant variables ARTICLE INFO currently influencing air travelers’ preference for domestic airlines in Nigeria. Tourism and Travelling, 3(1), 16-24. doi:10.21511/tt.3(1).2021.03 DOI http://dx.doi.org/10.21511/tt.3(1).2021.03 RELEASED ON Thursday, 19 August 2021 RECEIVED ON Wednesday, 23 June 2021 ACCEPTED ON Friday, 13 August 2021 LICENSE This work is licensed under a Creative Commons Attribution 4.0 International License JOURNAL "Tourism and Travelling" ISSN PRINT 2544-2295 ISSN ONLINE 2616-5090 PUBLISHER LLC “Consulting Publishing Company “Business Perspectives” FOUNDER Sp. z o.o. Kozmenko Science Publishing NUMBER OF REFERENCES NUMBER OF FIGURES NUMBER OF TABLES 18 0 5 © The author(s) 2021. This publication is an open access article. businessperspectives.org Tourism and Travelling, Volume 3, Issue 1, 2021 Sidiq Ben (Nigeria), Mobolaji Stephens (Nigeria), Wilfred Ukpere (South Africa) Significant variables BUSINESS PERSPECTIVES currently influencing air LLC “СPС “Business Perspectives” Hryhorii Skovoroda lane, 10, travelers’ preference for Sumy, 40022, Ukraine www.businessperspectives.org domestic airlines in Nigeria Abstract In recent years domestic airlines are improving their services, and the major airlines in Nigeria are ahead of others based on superior strategies; in fact, some airlines are not fully utilized, which affects their profitability, while others are highly utilized. Market dynamics and regulatory forces are the key variables that influence airline attributes, features, and developments, but this is most evident where each airline competes for passengers despite the different route choices and airports of departure. -

Dealing with Air Carrier Liability and Related Matters: Practical Perspectives
DEALING WITH AIR CARRIER LIABILITY AND RELATED MATTERS: PRACTICAL PERSPECTIVES Professor Fabian Ajogwu, SAN, FCIArb A paper prepared by Professor Fabian Ajogwu, SAN, FCIArb and presented at the Nigeria Civil Aviation Authority Seminar on Aviation at Sheraton Hotel and Towers, Ikeja, Lagos, on Wednesday July 2, 2014 Dealing with Air Carrier Liability and Related Matters: Practical Perspectives It is a privilege to be invited to speak at this INTRODUCTION seminar on the subject of Dealing with The issue of Air Carrier liability arises from Air Carrier Liability and Related Matters various circumstances. In a situation where organised by the Nigerian Civil Aviation there is an accident occasioning death or injury Authority (NCAA) with the assistance of the or where there is a loss of baggage or cargo, the Socio Economic Rights Initiative (SERI). I liability of the Air Carrier can arise. Nigeria as would like to share with you my thoughts on a country has witnessed several mishaps as it a subject, whose importance has been brought relates to aircraft accidents. Incidents of loss to the front burner as it rightfully should. It of baggage or cargo have arisen from several is the subject of understanding the practical occasions not only in Nigeria but the World perspectives to the concept of air carrier over. Where liability against the Air Carrier is liability and the legal framework for this special proved, the issue of compensation will arise and class of contractual relationship. this can lead to either a negotiated settlement This discussion is segmented into six parts, with the parties involved, or litigating the namely — dispute where amicable resolution of the disputes fail. -

Early Signs of a Turnaround
COVERSTORY BY HAROLD O. DEMUREN International audits stimulate Nigerian airline development and public-private partnerships to continue rehabilitating infrastructure. Early Signs of Turnaround hen people look at the skies Nigerian airlines with modern aircraft flight frequencies to an ever-expanding over Nigeria today, they are supplementing strong established number of domestic, regional and see a very different envi- carriers that are rapidly renewing their international destinations. ronment compared with fleets. Many more aircraft coming into The dramatic turnaround (Table 1, p. Wwhat we had just a few years ago. New the country are providing increased 20) is the result of a deliberate policy of 18 | FLIGHT SAFETY FOUNDATION | AEROSAFETYWORLD | MAY 2009 COVERSTORY the federal government of Nigeria that followed the Accident Investigation Bureau (AIB) of the demise of Nigeria Airways in 2003 and came Nigeria as an autonomous agency. The AIB in the aftermath of tragic accidents in the coun- is now an independent accident investigator try (ASW, 10/06, p. 29). In November 2006, a in compliance with ICAO Annex 13, Aircraft new Civil Aviation Act became law, establishing Accident and Incident Investigation. the Nigerian Civil Aviation Authority (NCAA) The importance to Nigeria of autonomy Nigerian Authority Civil Aviation as an autonomous safety regulator. Autonomy for the NCAA and ratification of the ICAO for the NCAA effectively protects it from politi- Convention on International Interests in Mobile cal interference, enabling it to act without fear or Equipment — also known as the Cape Town favor, and provides for effective safety oversight Convention — cannot be overstated.2 Because of the aviation industry in Nigeria. -

Appraisal Ofpassenger Satisfaction with Air Transportation Servicesat the Domestic Terminals of Murtalamuhammed Airport, Lagos
American Journal of Social Science Research Vol. 3, No. 5, 2017, pp. 25-34 http://www.aiscience.org/journal/ajssr ISSN: 2381-7712 (Print); ISSN: 2381-7720 (Online) Appraisal ofPassenger Satisfaction with Air Transportation Servicesat the Domestic Terminals of MurtalaMuhammed Airport, Lagos Samuel Sunday Eleboda * Department of Administration and Management, College of Business and Social Sciences, Crawford University, Faith City, Nigeria Abstract Service expectationis widely recognized as a key influencer ofcustomer/passenger satisfaction and the formation of customers’ future purchase intentions which have implications for the firm’s bottom lines. Despite this fact, previous studies have largely focused on funding and its utilization in the air transportation sub-sector, coupled with recent and past operational challenges faced by airline operators, and the fear of air transportation by many Nigerians due to previous air crashes, there is the need to gauge the current level of passenger satisfaction vis-à-vis their service expectations as a means towards better performance. This study therefore investigatedthe current level of passenger satisfaction and the impact of expectation on satisfaction. Primary data were used for the study. These were collected through the adaptation of the SERVQUAL instrument. From the targeted population of 302,869 passengers, multi-stage sampling technique was used to select 268 passengers of airlines operating atdomestic terminals of the Murtala Mohammed Airport, Lagos. Of the 268 copies of the questionnaire distributed, 232 (86.6%) were retrieved. Data collected were analyzed using tables, frequencies, percentages, and multiple regression. The study found that that the industry as a whole has 82.61% satisfied passengers, though with varying degrees of satisfaction, while individual airlines ranked as follow: Medview airline, Aero Contractor, Dana Air, Azman Air, Arik Air, Air Peace, First Nation, and Overland. -

Niger Ia Aviatio N Fact Sheet
Nigeria Aviation Fact Sheet United States Embassy in Nigeria Recent Developments International Aviation Industry The aviation industry has grown rapidly in recent Airbus predicted that Lagos would become an years and become heavily indebted because of "airline megacity" and transport 10,000 long-haul losses caused by low fares, high interest rates, and rising fuel costs. passengers per day within the next twenty years. There are 74 services per week from Western Total Passenger Traffic Europe to Nigeria. (in millions) 13 The United Kingdom is Nigeria's largest aviation market and home to a large Diaspora community. 12 11 Virgin Atlantic has an effective pricing strategy, transit visa, and chauffeur services. 10 9 Foreign Carriers’ Nigerian Market Share 8 (weekly flight frequencies) 7 2003 2004 2005 2006 2007 2008 2009 Airlines 2000 2002 2004 2006 2007 Four major accidents in 2005-2006 led to the British 10 10 12 12 14 adoption of the Nigerian Civil Aviation Act and Airways International Civil Aviation Organization (ICAO) Universal Safety Oversight Audit KLM 5 6 10 13 13 Program (USOAP) in 2006 and the achievement of Federation Aviation Administration Category Lufthansa 3 3 7 10 9 1 flight safety status in 2010. Air France 3 4 7 9 10 Major Airports and Their Conditions State Lagos Abuja Virgin 3 3 4 7 7 Size Inadequate Adequate Atlantic Physical Condition Poor Average There are 21 flights per week from the Gulf region Use of technology Low Low to Nigeria. Regional Trends High Traffic Low Traffic Nigeria has no direct links to the growing markets Minister of Aviation Stella Oduah-Ogiemwonyi of Asia. -

Four Airports Ppp Nigeria
FOUR AIRPORTS PPP NIGERIA PROJECT DESCRIPTION PROJECT SUMMARY THE FEDERAL MINISTRY OF TRANSPORTATION IS ASSESSING THE FEASIBILITY OF PUBLIC PRIVATE PARTNERSHIPS (PPP) FOR THE AIRPORTS OF ABUJA, LAGOS, KANO AND PORT HARCOURT LEVERAGE PRIVATE SECTOR PARTICIPATION AND FOREIGN INVESTMENT TO ACHIEVE THE UPGRADE AND DEVELOPMENT OF NEW INFRASTRUCTURE AT THE AIRPORTS IN THE FASTEST AND MOST COST-EFFECTIVE MANNER. KANO 0.5 MPPA ABUJA 4.2 MPPA LAGOS 6.7 MPPA PORT HARCOURT 1.1 MPPA FOUR AIRPORTS PPP Page 2 NIGERIA TRAFFIC OVERVIEW THE NIGERIAN AVIATION INDUSTRY HAS BEEN FACING MAJOR CHALLENGES DUE TO HIGH FUEL PRICES, LIMITED ACCESS TO FOREIGN CURRENCIES, AS WELL AS LOW AIRCRAFT UTILISATION AND HIGH MAINTENANCE COSTS TOTAL PASSENGERS LAGOS, PORT HARCOURT, ABUJA, KANO • With 6.7 million passengers, Lagos Domestic International Total Growth Murtala Muhammed 14.0 40% International Airport is Nigeria’s 35% largest airport, 12.0 followed by Abuja 30% Nnamdi Azikiwe International Airport 10.0 25% (4.2m). 20% • Despite the 8.0 country’s higher GDP 15% per capita, 6.0 Nigeria’s 10% propensity to fly is Total Growth Total relatively low 4.0 5% compared to other Total Passengers, Passengers, MillionsTotal African countries. 0% 2.0 • Route network out of -5% the four airports is dominated by 0.0 -10% domestic services 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 operated by Arik Air, PASSENGERS, M 6.7 9.0 10.2 11.8 12.6 12.2 12.8 13.3 12.6 12.4 Dana Air, Air Peace etc. Foreign airlines mostly focus on economic MMA2 Failure Issues trade links, diaspora and Hajj markets.