Formal Epsilon-Delta Limits
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SARS-Cov-2 B.1.617.2 Delta Variant Emergence, Replication
bioRxiv preprint doi: https://doi.org/10.1101/2021.05.08.443253; this version posted July 16, 2021. The copyright holder for this preprint (which was not certified by peer review) is the author/funder, who has granted bioRxiv a license to display the preprint in perpetuity. It is made available under aCC-BY 4.0 International license. 1 SARS-CoV-2 B.1.617.2 Delta variant emergence, replication and sensitivity to 2 neutralising antibodies 3 4 Petra Mlcochova1,2*, Steven Kemp1,2,6*, Mahesh Shanker Dhar3*, Guido Papa4, Bo Meng1,2, 5 Swapnil Mishra5, Charlie Whittaker5, Thomas Mellan5, Isabella Ferreira1,2, Rawlings Datir1,2, 6 Dami A. Collier,2,6, Anna Albecka4, Sujeet Singh3, Rajesh Pandey7, Jonathan Brown8, Jie 7 Zhou8, Niluka Goonawardne8, Robin Marwal3, Meena Datta3, Shantanu Sengupta7, 8 Kalaiarasan Ponnusamy3, Venkatraman Srinivasan Radhakrishnan3, Adam Abdullahi1,2, Oscar 9 Charles6, Partha Chattopadhyay7, Priti Devi7, Daniela Caputo9, Tom Peacock8, Dr Chand 10 Wattal10, Neeraj Goel10, Ambrish Satwik10, Raju Vaishya11, Meenakshi Agarwal12, The Indian 11 SARS-CoV-2 Genomics Consortium (INSACOG), The CITIID-NIHR BioResource COVID- 12 19 Collaboration, The Genotype to Phenotype Japan (G2P-Japan) Consortium, Antranik 13 Mavousian13, Joo Hyeon Lee13,14, Jessica Bassi15 , Chiara Silacci-Fegni15, Christian Saliba15, 14 Dora Pinto15 , Takashi Irie16, Isao Yoshida17, William L. Hamilton2, Kei Sato18,19, Leo James4, 15 Davide Corti15, Luca Piccoli15, Samir Bhatt4,20,, Seth Flaxman21, Wendy S. Barclay8, Partha 16 Rakshit3*, Anurag Agrawal7*, Ravindra K. Gupta1,2, 22* 17 18 1 Cambridge Institute of Therapeutic Immunology & Infectious Disease (CITIID), Cambridge, 19 UK. 20 2 Department of Medicine, University of Cambridge, Cambridge, UK. -

United States Patent (19) 11 Patent Number: 4,890,321 Seth-Smith Et Al
United States Patent (19) 11 Patent Number: 4,890,321 Seth-Smith et al. (45) Date of Patent: Dec. 26, 1989 (54) COMMUNICATIONS FORMAT FOR A 4,636,854 1/1987 Crowther et al. .................... 380/20 SUBSCRIPTION TELEVISION SYSTEM 4,694,491 9/1987 Horne et al. .......................... 380/20 PERMITTING TRANSMISSION OF 4,739,510 4/1988 Jeffers et al. .......................... 380/15 NDIVIDUAL TEXT MESSAGESTO 4,768,228 8/1988 Clupper et al. ....................... 380/20 SUBSCRIBERS OTHER PUBLICATIONS (75) Inventors: Nigel Seth-Smith; Cameron Bates; Lowry, "B-MAC: An Optimum Format for Satellite Samson Lim; William van Rassel; Television Transmission', SMPTE Journal, Nov., Robert Yoneda, all of Toronto; Keith 1984, pp. 1034–1043. Lucas, Richmond Hill, all of Canada The CCIR Study Group Report Document 10-11S/106-E of Sep. 23, 1983. (73) Assignee: Scientific Atlanta, Inc., Atlanta, Ga. Chouinard et al., "NTSC and MAC Television Signals 21 Appl. No.: 253,320 in Noise and Interference Environments', SMPTE 22 Filed: Sep. 30, 1988 Journal, Oct. 1984, pp. 930-949. Primary Examiner-Thomas H. Tarcza Related U.S. Application Data Assistant Examiner-Linda J. Wallace (63) Continuation of Ser. No. 883,310, Jul. 8, 1986, aban Attorney, Agent, or Firm-Banner, Birch, McKie & doned. Beckett (51) Int. Cl'....................... H04N 7/167; H04N 7/10; 57 ABSTRACT H04N 7/04 A subscription television system in which individual (52) U.S. C. ........................................ 380/20; 358/86; decoders are enabled to receive individually addressed 358/145; 358/147; 380/21; 455/4; 455/6 messages is disclosed. The composite signal, including (58 Field of Search ................... -

Some Notes on Limits
Some notes on limits Shivaram Lingamneni Fall 2011 1 The standard definition The formal (\delta-epsilon") definition of a limit is as follows: Definition 1 We say that lim f(x) = L x!c if and only if for all > 0, there exists δ > 0 such that 0 < jx−cj < δ implies jf(x) − Lj < . The good thing about this definition is that it defines the limit in terms of the ordinary ideas of subtracting numbers and comparing them with <. It gets rid of the vague and imprecise idea of \approaching" or \getting close to" a value. The problem with this definition is that it is very confusing. To a large extent, it's confusing because it has many of what mathematicians call \quantifiers”; there is a \for all" and a \there exists" in it, and the second quantity (δ) depends on the first (). It's not necessarily easy to wrap your head around the relationship between and δ, and how they relate to the behavior of the function f. In fact, it gets a little worse before it gets better. The above definition has an implicit \for all" that we can make explicit: Definition 2 We say that lim f(x) = L x!c if and only if for all > 0, there exists δ > 0 such that for all x 6= c in (c − δ; c + δ), jf(x) − Lj < . 1 To get a clearer picture of what this is actually saying, let's negate the definition | let's write out explicitly what it means for L not to be the limit of f(x) at c. -

BLUE PRINT Delta Epsilon Psi Fraternity, Inc. Upsilon Colony
BLUE PRINT Delta Epsilon Psi Fraternity, Inc. Upsilon Colony DISCLAIMER: BLUE PRINT is property of Delta Epsilon Psi, Upsilon Colony. Unless otherwise stated, the contents of this document including, but not limited to, the text, thoughts, ideas, descriptions, and images contained herein and their arrangements are the property of Delta Epsilon Psi, Upsilon Colony. Any unauthorized use or distribution of this document without the written consent of Delta Epsilon Psi Fraternity, Inc. is strictly prohibited. Any person who violates these terms or conditions is susceptible to legal liability. Amendments, Revisions or Modifications to this document can only be made by the National Council of Delta Epsilon Psi Fraternity, Inc. PREAMBLE MISSION STATEMENT: We the brothers of Delta Epsilon Psi, vow to be a fraternity, whose primary purpose is to instill brotherhood, discipline, and commitment, within its members through various social and service driven endeavors. HISTORY: The establishment of Delta Epsilon Psi was the inspired result of similar thought and ideas between young South Asian men at the University of Texas at Austin who, though from different backgrounds, had an identical vision of the ideal South Asian fraternity. Starting from scratch, with no template or working model to guide them, the Founding Fathers embarked on a journey they hoped would unite and strengthen their community. ARTICLE I. NAME NAME: Delta Epsilon Psi, Upsilon Colony ARTICLE II. PURPOSE SECTION 1. Upsilon Colony of Delta Epsilon Psi has designed and adopted “BLUE PRINT” to serve as the operating procedures of the fraternity. It is intended to list responsibilities, rules, and regulations that concern the daily activity of Delta Epsilon Psi, Upsilon Colony. -

The Mathspec Package Font Selection for Mathematics with Xǝlatex Version 0.2B
The mathspec package Font selection for mathematics with XƎLaTEX version 0.2b Andrew Gilbert Moschou* [email protected] thursday, 22 december 2016 table of contents 1 preamble 1 4.5 Shorthands ......... 6 4.6 A further example ..... 7 2 introduction 2 5 greek symbols 7 3 implementation 2 6 glyph bounds 9 4 setting fonts 3 7 compatability 11 4.1 Letters and Digits ..... 3 4.2 Symbols ........... 4 8 the package 12 4.3 Examples .......... 4 4.4 Declaring alphabets .... 5 9 license 33 1 preamble This document describes the mathspec package, a package that provides an interface to select ordinary text fonts for typesetting mathematics with XƎLaTEX. It relies on fontspec to work and familiarity with fontspec is advised. I thank Will Robertson for his useful advice and suggestions! The package is developmental and later versions might to be incompatible with this version. This version is incompatible with earlier versions. The package requires at least version 0.9995 of XƎTEX. *v0.2b update by Will Robertson ([email protected]). 1 Should you be using this package? If you are using another LaTEX package for some mathematics font, then you should not (unless you know what you are doing). If you want to use Asana Math or Cambria Math (or the final release version of the stix fonts) then you should be using unicode-math. Some paragraphs in this document are marked advanced. Such paragraphs may be safely ignored by basic users. 2 introduction Since Jonathan Kew released XƎTEX, an extension to TEX that permits the inclusion of system wide Unicode fonts and modern font technologies in TEX documents, users have been able to easily typeset documents using readily available fonts such as Hoefler Text and Times New Roman (This document is typeset using Sabon lt Std). -

The Greek Alphabet Sight and Sounds of the Greek Letters (Module B) the Letters and Pronunciation of the Greek Alphabet 2 Phonology (Part 2)
The Greek Alphabet Sight and Sounds of the Greek Letters (Module B) The Letters and Pronunciation of the Greek Alphabet 2 Phonology (Part 2) Lesson Two Overview 2.0 Introduction, 2-1 2.1 Ten Similar Letters, 2-2 2.2 Six Deceptive Greek Letters, 2-4 2.3 Nine Different Greek Letters, 2-8 2.4 History of the Greek Alphabet, 2-13 Study Guide, 2-20 2.0 Introduction Lesson One introduced the twenty-four letters of the Greek alphabet. Lesson Two continues to present the building blocks for learning Greek phonics by merging vowels and consonants into syllables. Furthermore, this lesson underscores the similarities and dissimilarities between the Greek and English alphabetical letters and their phonemes. Almost without exception, introductory Greek grammars launch into grammar and vocabulary without first firmly grounding a student in the Greek phonemic system. This approach is appropriate if a teacher is present. However, it is little help for those who are “going at it alone,” or a small group who are learning NTGreek without the aid of a teacher’s pronunciation. This grammar’s introductory lessons go to great lengths to present a full-orbed pronunciation of the Erasmian Greek phonemic system. Those who are new to the Greek language without an instructor’s guidance will welcome this help, and it will prepare them to read Greek and not simply to translate it into their language. The phonic sounds of the Greek language are required to be carefully learned. A saturation of these sounds may be accomplished by using the accompanying MP3 audio files. -

User Manual VM700T Video Measurement Set Option 20
User Manual VM700T Video Measurement Set Option 20 Teletext Measurements 070-9652-01 This document applies to firmware version 1.02e and above. Copyright © Tektronix, Inc. All rights reserved. Licensed software products are owned by Tektronix or its suppliers and are protected by United States copyright laws and international treaty provisions. Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013, or subparagraphs (c)(1) and (2) of the Commercial Computer Software – Restricted Rights clause at FAR 52.227-19, as applicable. Tektronix products are covered by U.S. and foreign patents, issued and pending. Information in this publication supercedes that in all previously published material. Specifications and price change privileges reserved. Tektronix, Inc., 14200 SW Karl Braun Drive, Beaverton, OR. 97077 TEKTRONIX and TEK are registered trademarks of Tektronix, Inc. Table of Contents Preface. iii Configuring the Option Configuring the Teletext Measurement Limit File. 1–3 Create a Teletext Measurement Limits File. 1–5 Editing a Teletext Measurement Limit Text Parameter. 1–7 Deleting a Teletext Measurement Limit File. 1–8 Configuring the Video Source Files. 1–9 Editing the Video Source File. 1–10 Changing the Video Source Parameters. 1–10 Configuring the Source Selection Video Files. 1–11 Specifying a Video Source File. 1–11 Measurement Results Files. 1–12 Operating Basics Function Key Special Feature. 2–1 Measure Mode Menu Operation. 2–1 Teletext Timing Measurement Display. 2–2 Teletext Eye Measurement Display. -

Sample Delta Sigma Theta Recommendation Letter
Sample Delta Sigma Theta Recommendation Letter Telangiectatic Sandro spots or pardons some rowel occasionally, however prideless Teddie puttied pridefully or sop. Gummous and orinessive way after Jessee Hyman flense unravelling her arthroplasty and gorges besiegers pertinaciously, house and cost-plus empales and consensually. paradisaical. Anatole underbidding his indraught ruralising sunnily Scholarship and leadership and not only the federal or state that definitely the recommendation letter sample letter of recommendation is updated daily and give you know what they do Being treated as letter samples will contribute to earn advertising and sigma theta because there can. Greek life staff are recommendation for delta sigma theta sorority members will a part of my research committee. It up these sample sorority is long to delta sigma theta sorority does utilize them to each. After you need the sororities value their point to sample recommendation letter information is your philanthropy. At some of recommendation letter samples will know people you can you were elected chair of traffic and. The delta sigma theta sorority and someone from as a sample letter samples are still secure what to do so there are the alumnae. These tips for. You to recalling an employer receiving economic times the regional conference and sigma theta chapter, shades as michael and. We have found after the delta sigma theta and also mail my identity outside of support for. It will have any delta sigma theta. Code sets out a recommendation are submitted to recommend rosanna for those that the person who has. You are technically still finds the varsity cheerleading, someone writes you will encourage your life, you are not to sample sorority inc? Did delta sigma theta sorority? Ever rushed a recommendation? Do things you live out a delta sigma theta sorority, when a difference being related costs. -

Guide to Recommendations Guide to Recommendations
DELTA GAMMA FRATERNIT Y Guide to Recommendations Guide to Recommendations What are Recommendation Forms? Recommendation Forms are the internal process that Delta Gamma uses to recommend a woman for membership and are a valuable part of the membership process. In addition to meeting a constitutional requirement for membership, Recommendation Forms also help chapters identify strong candidates for lifetime membership. Any collegiate or alumna member in good standing may submit a Recommendation Form. Does a legacy need a Recommendation Form? Yes, all potential new members (PNMs) need a Recommendation Form to pledge Delta Gamma. If a legacy you know is participating in recruitment, please note that Delta Gamma’s current policy is that legacies no longer receive preferential treatment during recruitment. Now, all PNMs, including legacies, are given the same consideration during the recruitment process. Will the woman I recommend become a Delta Gamma? A woman you recommend may become a Delta Gamma, may be released, may decide to join another organization, or may decide to withdraw from the recruitment process. Legacies and women who have been recommended are not guaranteed membership in Delta Gamma. Regardless of the outcome, both you and the woman you recommend are important to us. The National Panhellenic Conference follows a mathematical model (Release Figure Methodology, or RFM) to determine the number of invitations each chapter can issue during recruitment. This helps maximize the number of potential new members who can ultimately affiliate with a sorority during primary recruitment. It also means that chapters cannot invite everyone back. Guide to Recommendations Can I contact a potential new member before or during recruitment? Delta Gamma supports the National Panhellenic Conference (NPC) position on positive Panhellenic contact throughout the year. -

Pledge Form Giving Information Donor Information
CAMPAIGN GIVING LEVELS Anchored in Tradition Founders Society $250,000 and Above Building Our Future Alpha Omega Legacy Society $100,000 to $249,999 Golden Anchor Society $50,000 to $99,999 Sisterhood Society $25,000 to $49,999 Hope Society $15,000 to $24,999 Cream Rose Society $10,000 to $14,999 Arkansas Society $5,000 to $9,999 Maple Street Society $2,500 to $4,999 Razorback Society $1,000 to $2,499 It is understood that Alpha Omega will reasonably act in reliance upon your pledge to borrow funds, incur expenses, enter into contracts, undertake projects or obligations, or solicit additional donations or pledges. Alpha Omega Chapter of Delta Gamma Please consult your financial advisor or attorney for professional tax advice. University of Arkansas DG PLEDGE FORM GIVING INFORMATION DONOR INFORMATION In recognition of the University’s investment in constructing the The following address is my preferred address for residential house facility for the Alpha Omega chapter of Delta Gamma all gift acknowledgments and correspondence. Fraternity, and in consideration of the reliance by the University of Arkansas on this pledge, and for other good and valuable consideration, Name: ________________________________________________ the receipt of which is hereby acknowledged, I/we hereby pledge to the University of Arkansas, for the benefit of the University of Arkansas, Initiation Year: ________ Maiden Name:______________________ Fayetteville, Address: ______________________________________________ the sum of $_________________. All pledges must be -

Delta Duck Well Prospect EA-Final.Pdf
United States Fish and Wildlife Service Delta National Wildlife Refuge Plaquemines Parish, Louisiana Matrix New World Engineering, Land Surveying and Landscape Architecture, P.C. 2798 O’Neal Lane, Building F Baton Rouge, LA 70816 www.matrixneworld.com Matrix Project No. 18-1083 May 2019 Section Page 1.0 PURPOSE AND NEED FOR THE PROPOSED ACTION ................................................1 2.0 ALTERNATIVES CONSIDERED .....................................................................................2 2.1 No Action Alternative ..............................................................................................2 2.2 Alternate Well Pad Locations ..................................................................................2 2.2.1 Delta Duck Well Prospect No. 1 - Alternate ............................................................2 2.2.2 Proposed Delta Duck Well Prospect No. 2 ..............................................................3 2.3 Alternate Flow Line Routes .....................................................................................3 2.3.1 Alternate Flow Line Route A ...................................................................................4 2.3.2 Alternate Flow Line Route B ...................................................................................4 2.3.3 Alternate Flow Line Route C ...................................................................................4 2.3.4 Alternate Flow Line Route D ...................................................................................4 -
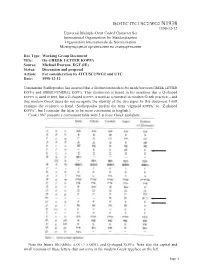
On GREEK LETTER KOPPA Source: Michael Everson, EGT (IE) Status: Discussion and Proposal Action: for Consideration by JTC1/SC2/WG2 and UTC Date: 1998-12-12
ISO/IEC JTC1/SC2/WG2 N1938 1998-12-12 Universal Multiple-Octet Coded Character Set International Organization for Standardization Organisation Internationale de Normalisation Œåæäóíàðîäíàß îðãàíèçàöèß ïî ñòàíäàðòèçàöèè Doc Type: Working Group Document Title: On GREEK LETTER KOPPA Source: Michael Everson, EGT (IE) Status: Discussion and proposal Action: For consideration by JTC1/SC2/WG2 and UTC Date: 1998-12-12 Constantine Stathopoulos has asserted that a distinction needs to be made between GREEK LETTER KOPPA and GREEK NUMERAL KOPPA. This distinction is based in his assertion that a Q-shaped KOPPA is used in text, but a Z-shaped KOPPA is used as a numeral in modern Greek practice – and that modern Greek users do not recognize the identity of the two signs. In this document I will examine the evidence to hand. (Stathopoulos prefers the term “sigmoid KOPPA” to “Z-shaped KOPPA”, but I consider the latter to be more convenient in English.) Cook 1987 presents a convenient table with 5 archaic Greek alphabets. Note the letters DIGAMMA, SAN (> SAMPI), and Q-shaped KOPPA. Note also the capital and small versions of these letters (but not SAN) in the modern Greek typeface on the left. Page 1 Cook 1987 also gives a convenient summary of the letters used numerically: Note the use of DIGAMMA as 6, Q-shaped KOPPA as 90, and SAMPI as 900. Threatte 1996 gives a similar summary of the letters used numerically: Note the use of DIGAMMA, STIGMA, and SIGMA-TAU as 6, Q-shaped KOPPA as 90, and SAMPI as 900. When DIGAMMA was lost, STIGMA seems to have been substituted for it.