Computing Winning Strategies for Poset Games
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![On Variations of Nim and Chomp Arxiv:1705.06774V1 [Math.CO] 18](https://docslib.b-cdn.net/cover/3174/on-variations-of-nim-and-chomp-arxiv-1705-06774v1-math-co-18-43174.webp)
On Variations of Nim and Chomp Arxiv:1705.06774V1 [Math.CO] 18
On Variations of Nim and Chomp June Ahn Benjamin Chen Richard Chen Ezra Erives Jeremy Fleming Michael Gerovitch Tejas Gopalakrishna Tanya Khovanova Neil Malur Nastia Polina Poonam Sahoo Abstract We study two variations of Nim and Chomp which we call Mono- tonic Nim and Diet Chomp. In Monotonic Nim the moves are the same as in Nim, but the positions are non-decreasing numbers as in Chomp. Diet-Chomp is a variation of Chomp, where the total number of squares removed is limited. 1 Introduction We study finite impartial games with two players where the same moves are available to both players. Players alternate moves. In a normal play, the person who does not have a move loses. In a misère play, the person who makes the last move loses. A P-position is a position from which the previous player wins, assuming perfect play. We can observe that all terminal positions are P-positions. An N-position is a position from which the next player wins given perfect play. When we play we want to end our move with a P-position and want to see arXiv:1705.06774v1 [math.CO] 18 May 2017 an N-position before our move. Every impartial game is equivalent to a Nim heap of a certain size. Thus, every game can be assigned a non-negative integer, called a nimber, nim- value, or a Grundy number. The game of Nim is played on several heaps of tokens. A move consists of taking some tokens from one of the heaps. The game of Chomp is played on a rectangular m by n chocolate bar with grid lines dividing the bar into mn squares. -

Blue-Red Hackenbush
Basic rules Two players: Blue and Red. Perfect information. Players move alternately. First player unable to move loses. The game must terminate. Mathematical Games – p. 1 Outcomes (assuming perfect play) Blue wins (whoever moves first): G > 0 Red wins (whoever moves first): G < 0 Mover loses: G = 0 Mover wins: G0 Mathematical Games – p. 2 Two elegant classes of games number game: always disadvantageous to move (so never G0) impartial game: same moves always available to each player Mathematical Games – p. 3 Blue-Red Hackenbush ground prototypical number game: Blue-Red Hackenbush: A player removes one edge of his or her color. Any edges not connected to the ground are also removed. First person unable to move loses. Mathematical Games – p. 4 An example Mathematical Games – p. 5 A Hackenbush sum Let G be a Blue-Red Hackenbush position (or any game). Recall: Blue wins: G > 0 Red wins: G < 0 Mover loses: G = 0 G H G + H Mathematical Games – p. 6 A Hackenbush value value (to Blue): 3 1 3 −2 −3 sum: 2 (Blue is two moves ahead), G> 0 3 2 −2 −2 −1 sum: 0 (mover loses), G= 0 Mathematical Games – p. 7 1/2 value = ? G clearly >0: Blue wins mover loses! x + x - 1 = 0, so x = 1/2 Blue is 1/2 move ahead in G. Mathematical Games – p. 8 Another position What about ? Mathematical Games – p. 9 Another position What about ? Clearly G< 0. Mathematical Games – p. 9 −13/8 8x + 13 = 0 (mover loses!) x = -13/8 Mathematical Games – p. -

Combinatorial Game Theory
Combinatorial Game Theory Aaron N. Siegel Graduate Studies MR1EXLIQEXMGW Volume 146 %QIVMGER1EXLIQEXMGEP7SGMIX] Combinatorial Game Theory https://doi.org/10.1090//gsm/146 Combinatorial Game Theory Aaron N. Siegel Graduate Studies in Mathematics Volume 146 American Mathematical Society Providence, Rhode Island EDITORIAL COMMITTEE David Cox (Chair) Daniel S. Freed Rafe Mazzeo Gigliola Staffilani 2010 Mathematics Subject Classification. Primary 91A46. For additional information and updates on this book, visit www.ams.org/bookpages/gsm-146 Library of Congress Cataloging-in-Publication Data Siegel, Aaron N., 1977– Combinatorial game theory / Aaron N. Siegel. pages cm. — (Graduate studies in mathematics ; volume 146) Includes bibliographical references and index. ISBN 978-0-8218-5190-6 (alk. paper) 1. Game theory. 2. Combinatorial analysis. I. Title. QA269.S5735 2013 519.3—dc23 2012043675 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. Republication, systematic copying, or multiple reproduction of any material in this publication is permitted only under license from the American Mathematical Society. Requests for such permission should be addressed to the Acquisitions Department, American Mathematical Society, 201 Charles Street, Providence, Rhode Island 02904-2294 USA. Requests can also be made by e-mail to [email protected]. c 2013 by the American Mathematical Society. All rights reserved. The American Mathematical Society retains all rights except those granted to the United States Government. -

Flipping the Winner of a Poset Game Adam O
Illinois Mathematics and Science Academy DigitalCommons@IMSA Published Student Papers Student Works 1-1-2011 Flipping the winner of a poset game Adam O. Kalinich '12 Illinois Mathematics and Science Academy Follow this and additional works at: http://digitalcommons.imsa.edu/published_student_papers Part of the Mathematics Commons, and the Theory and Algorithms Commons Recommended Citation Kalinich, Adam O. (2011). Flipping the winner of a poset game. Information Processing Letters, 112 (2012), 86-89. This Article is brought to you for free and open access by the Student Works at DigitalCommons@IMSA. It has been accepted for inclusion in Published Student Papers by an authorized administrator of DigitalCommons@IMSA. For more information, please contact [email protected], [email protected]. Flipping the winner of a poset game Adam O. Kalinich Illinois Math and Science Academy, 1500 Sullivan Road, Aurora, IL 60506, United States ARTICLE INFO ABSTRACT Article history: Partially-ordered set games, also called poset games, are a class of two-player Received 4 May 2011 combinatorial games. The playing field consists of a set of elements, some of which are Received in revised form 30 September 2011 greater than other elements. Two players take turns removing an element and all elements Accepted 30 September 2011 greater than it, and whoever takes the last element wins. Examples of poset games include Available online 15 October 2011 Nim and Chomp. We investigate the complexity of computing which player of a poset Communicated by J. Torán game has a winning strategy. We give an inductive procedure that modifies poset games to change the nim-value which informally captures the winning strategies in the game. -

Crash Course on Combinatorial Game Theory
CRASH COURSE ON COMBINATORIAL GAME THEORY ALFONSO GRACIA{SAZ Disclaimer: These notes are a sketch of the lectures delivered at Mathcamp 2009 containing only the definitions and main results. The lectures also included moti- vation, exercises, additional explanations, and an opportunity for the students to discover the patterns by themselves, which is always more enjoyable than merely reading these notes. 1. The games we will analyze We will study combinatorial games. These are games: • with two players, who take turns moving, • with complete information (for example, there are no cards hidden in your hand that only you can see), • deterministic (for example, no dice or flipped coins), • guaranteed to finish in a finite amount of time, • without loops, ties, or draws, • where the first player who cannot move loses. In this course, we will specifically concentrate on impartial combinatorial games. Those are combinatorial games in which the legal moves for both players are the same. 2. Nim Rules of nim: • We play with various piles of beans. • On their turn, a player removes one or more beans from the same pile. • Final position: no beans left. Notation: • A P-position is a \previous player win", e.g. (0,0,0), (1,1,0). • An N-position is a \next player win", e.g. (1,0,0), (2,1,0). We win by always moving onto P-positions. Definition. Given two natural numbers a and b, their nim-sum, written a ⊕ b, is calculated as follows: • write a and b in binary, • \add them without carrying", i.e., for each position digit, 0 ⊕ 0 = 1 ⊕ 1 = 0, 0 ⊕ 1 = 1 ⊕ 0 = 1. -

Octal Games on Graphs
Octal Games on Graphs Laurent Beaudou1, Pierre Coupechoux2, Antoine Dailly3, Sylvain Gravier4, Julien Moncel2, Aline Parreau3, Éric Sopena5 1LIMOS, Clermont-Ferrand 2LAAS, Toulouse 3LIRIS, Lyon 4Institut Fourier, Grenoble 5LaBRI, Bordeaux This work is part of the ANR GAG (Graphs and Games). Games And Graphs CGTC 2017 1/19 I kayles is 0.137 I cram on a single row is 0.07 I The James Bond Game is 0.007 I impartial games; I played on heaps of counters; I whose rules are defined by an octal code. Examples I nim is 0.3333. Octal games Definition Octal games are: 2/19 I kayles is 0.137 I cram on a single row is 0.07 I The James Bond Game is 0.007 Examples I nim is 0.3333. Octal games Definition Octal games are: I impartial games; I played on heaps of counters; I whose rules are defined by an octal code. 2/19 I kayles is 0.137 I cram on a single row is 0.07 I The James Bond Game is 0.007 Octal games Definition Octal games are: I impartial games; I played on heaps of counters; I whose rules are defined by an octal code. Examples I nim is 0.3333. 2/19 I cram on a single row is 0.07 I The James Bond Game is 0.007 Octal games Definition Octal games are: I impartial games; I played on heaps of counters; I whose rules are defined by an octal code. Examples I nim is 0.3333. I kayles is 0.137 2/19 I cram on a single row is 0.07 I The James Bond Game is 0.007 Octal games Definition Octal games are: I impartial games; I played on heaps of counters; I whose rules are defined by an octal code. -

Combinatorial Game Complexity: an Introduction with Poset Games
Combinatorial Game Complexity: An Introduction with Poset Games Stephen A. Fenner∗ John Rogersy Abstract Poset games have been the object of mathematical study for over a century, but little has been written on the computational complexity of determining important properties of these games. In this introduction we develop the fundamentals of combinatorial game theory and focus for the most part on poset games, of which Nim is perhaps the best- known example. We present the complexity results known to date, some discovered very recently. 1 Introduction Combinatorial games have long been studied (see [5, 1], for example) but the record of results on the complexity of questions arising from these games is rather spotty. Our goal in this introduction is to present several results— some old, some new—addressing the complexity of the fundamental problem given an instance of a combinatorial game: Determine which player has a winning strategy. A secondary, related problem is Find a winning strategy for one or the other player, or just find a winning first move, if there is one. arXiv:1505.07416v2 [cs.CC] 24 Jun 2015 The former is a decision problem and the latter a search problem. In some cases, the search problem clearly reduces to the decision problem, i.e., having a solution for the decision problem provides a solution to the search problem. In other cases this is not at all clear, and it may depend on the class of games you are allowed to query. ∗University of South Carolina, Computer Science and Engineering Department. Tech- nical report number CSE-TR-2015-001. -
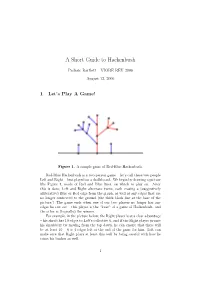
A Short Guide to Hackenbush
A Short Guide to Hackenbush Padraic Bartlett – VIGRE REU 2006 August 12, 2006 1 Let’s Play A Game! Figure 1. A sample game of Red-Blue Hackenbush. Red-Blue Hackenbush is a two-person game – let’s call these two people Left and Right – best played on a chalkboard. We begin by drawing a picture like Figure 1, made of Red and Blue lines, on which to play on. After this is done, Left and Right alternate turns, each erasing a (suggestively alliterative) Blue or Red edge from the graph, as well as any edges that are no longer connected to the ground (the thick black line at the base of the picture.) The game ends when one of our two players no longer has any edges he can cut – this player is the “loser” of a game of Hackenbush, and the other is (logically) the winner. For example, in the picture below, the Right player is at a clear advantage – his shrub has 10 edges to Left’s collective 6, and if the Right player prunes his shrubbery by moving from the top down, he can ensure that there will be at least 10 − 6 = 4 edges left at the end of the game for him. Left can make sure that Right plays at least this well by being careful with how he trims his bushes as well. 1 Figure 2. A shrubbery! But what about a slightly less clear-cut picture? In Figure 3, both players have completely identical plants to prune, so who wins? Well: if Left starts, he will have to cut some edge of his picture. -

Chomp on Partially Ordered Sets a Focused Introduction to Combinatorial Game Theory
Chomp on Partially Ordered Sets A Focused Introduction to Combinatorial Game Theory Alexander Clow August 13, 2020 A.Clow August 13, 2020 1 / 12 What is a Combinatorial Game? Partisan vs. Impartial Definition of a combinatorial game1 No Chance Perfect Information Games as Sets of Moves 1Winning ways for your mathematical plays[1] A.Clow August 13, 2020 2 / 12 Examples of Partisan Games A.Clow August 13, 2020 3 / 12 Examples of Impartial Games The Game of Nim th Let there be n 2 N0 piles with xi 2 N stones in the i pile. On their turn a player can remove any amount of stones from a single pile that they wish. The player who takes removes the final stone from the board is the winner. Who wins (x,x) Nim? Is a winner guaranteed? Who wins (3,2,1) Nim? Is a winner guaranteed? A.Clow August 13, 2020 4 / 12 Examples of Impartial Games Poset Chomp Poset Chomp Let (X ; ≤) = P be a partially ordered set. Each turn a player can chose any x 2 X and then remove all x0 2 P such that x ≤ x0. The first player to have no move on their turn loses. Why is Poset Chomp interesting?2 2Computing Winning Strategies for Poset Games[4],A curious nim-type game[2] A.Clow August 13, 2020 5 / 12 Examples of Poset Chomp 3 4 (1) ◦ ◦ (2) ◦ ◦ (3) ◦ (4) ◦ Z D O c O O ◦ ◦ ::: ◦ ◦ ◦ O ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦ 3Transfinite chomp[3] 4A curious nim-type game[2] A.Clow August 13, 2020 6 / 12 Impartial Combinatorial Games Who wins and how? Zermelo's Theorem5 Theorem If both player play ideally combinatorial games have a set winner and loser or the game will draw. -

Daisies, Kayles, Sibert-Conway and the Decomposition in Miske Octal
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Theoretical Computer Science 96 (1992) 361-388 361 Elsevier Mathematical Games Daisies, Kayles, and the Sibert-Conway decomposition in miske octal games Thane E. Plambeck Compuler Science Department, Stanford University, StanJord, Cal@nia 94305, USA Communicated by R.K. Guy Received November 1990 Revised June 1991 Abstract Plambeck, T.E., Daisies, Kayles, and the Sibert-Conway decomposition in misere octal games, Theoretical Computer Science 96 (1992) 361-388. Sibert and Conway [to appear] have solved a long-standing open problem in combinatorial game theory by giving an efficient algorithm for the winning misere play of Kay/es, an impartial two-player game of complete information first described over 75 years ago by Dudeney (1910) and Loyd (1914). Here, we extend the SiberttConway method to construct a similar winning strategy for the game of Daisies (octal code 4.7) and then more generally solve all misere play finite octal games with at most 3 code digits and period two nim sequence * 1, * 2, * 1, * 2, 1. Introduction She Loves Me, She Loves Me Not is a two-player game that can be played with one or more daisies, such as portrayed in Fig. 1. To play the game, the two players take turns pulling one petal off a daisy. In normal play, the player taking the last petal is defined to be the winner. Theorem 1.1 is not difficult to prove. Theorem 1.1. In normal play of the game She Loves Me, She Loves Me Not, a position is a win for the jrst player if and only zifit contains an odd number of petals. -

Game Theory Basics
Game Theory Basics Bernhard von Stengel Department of Mathematics, London School of Economics, Houghton St, London WC2A 2AE, United Kingdom email: [email protected] February 15, 2011 ii The material in this book has been adapted and developed from material originally produced for the BSc Mathematics and Economics by distance learning offered by the University of London External Programme (www.londonexternal.ac.uk). I am grateful to George Zouros for his valuable comments, and to Rahul Savani for his continuing interest in this project, his thorough reading of earlier drafts, and the fun we have in joint research and writing on game theory. Preface Game theory is the formal study of conflict and cooperation. It is concerned with situa- tions where “players” interact, so that it matters to each player what the other players do. Game theory provides mathematical tools to model, structure and analyse such interac- tive scenarios. The players may be, for example, competing firms, political voters, mating animals, or buyers and sellers on the internet. The language and concepts of game theory are widely used in economics, political science, biology, and computer science, to name just a few disciplines. Game theory helps to understand effects of interaction that seem puzzling at first. For example, the famous “prisoners’ dilemma” explains why fishers can exhaust their resources by over-fishing: they hurt themselves collectively, but each fisher on his own cannot really change this and still profits by fishing as much as possible. Other insights come from the way of looking at interactive situations. Game theory treats players equally and recommends to each player how to play well, given what the other players do. -

Games from Basic Data Structures
Games from Basic Data Structures Mara Bovee Kyle Burke University of New England Plymouth State University [email protected] [email protected] Craig Tennenhouse University of New England [email protected] January 12, 2018 Abstract In this paper, we consider combinatorial game rulesets based on data structures normally covered in an undergraduate Computer Science Data Structures course: arrays, stacks, queues, priority queues, sets, linked lists, and binary trees. We describe many rulesets as well as computational and mathemat- ical properties about them. Two of the rulesets, Tower Nim and Myopic Col, are new. We show polynomial-time solutions to Tower Nim and to Myopic Col on paths. 1 Introduction 1.1 Notation • For an integer x we will use x− to denote an integer less than or equal to x, and x+ an integer at least as large as x. • We use the ⊕ operator to refer to the bitwise binary XOR operation. For example, 3 ⊕ 5 = 6. • Other notation common to combinatorial game theory is mentioned below. 1.2 Combinatorial Game Theory Two-player games with alternating turns, perfect information, and no random elements are known as combi- natorial games. Combinatorial Game Theory concerns determining which of the players has a winning move from any position (game state). Some important considerations here follow. arXiv:1605.06327v1 [cs.DS] 20 May 2016 • This paper only considers games under normal play conditions, meaning that the last player to make a move wins. (If a player can’t make a legal move on their turn, they lose.) • The sum of two game positions is also a game where a legal move consists of moving on one of the two position summands.