International Journal of Innovative Technology and Exploring Engineering
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

International Journal of Innovative Technology and Exploring Engineering
International Journal of Innovative Technology and Exploring Engineering ISSN : 2278 - 3075 Website: www.ijitee.org Volume-1 Issue-5, OCTOBER 2012 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. Ltd. loring Exp En d gin an ee r y in g g lo o n h c e T IjItEe e I n v i t t e E a r X v P N n o L IO a O n T t R A i o V n I I N O G N n IN f a o l l J a o r n u www.ijitee.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. -

What Are Wetlands Threats to Wetlands
What are wetlands Threats to wetlands Wetlands are the ecotones or transitional The trade-off between environmental zones between permanently aquatic and dry protection and development is most acute in terrestrial ecosystems. Ramsar Convention has dynamic and complex ecosystems such as defined wetlands as “areas of marsh, fen, wetlands. Wetlands face a range of anthropogenic peatland or water, whether natural or artificial, threats. The chief indirect drivers of change are permanent or temporary with water that is static human population growth around wetlands or flowing, fresh, brackish or salt, including areas coupled with growing economic and commercial of marine water the depth of which at low tide activities. Major direct threats for inland wetlands does not exceed six meters”. A wide variety of are infrastructure development (dams, dykes, wetlands like marshes, swamps, open water road, residential and commercial buildings), land bodies, mangroves and tidal flats and salt reclamation and over-harvesting. Major indirect marshes etc. exists in our country. ones are aquaculture, agriculture, reduced water flow, depletion of ground and surface water Wetlands are integral to a healthy supplies, introduction of invasive alien species, environment. They help to retain water during and organic and inorganic pollutants. dry periods, thus keeping the water table high and relatively stable. During periods of flooding, In India, momentous losses of wetlands they act to reduce flood levels and to trap have resulted from conversion to industrial, suspended solids and nutrients to the lakes than agricultural and various other developments. if they flow directly into the lakes. Compared to These have caused hydrological perturbations tropical rain forests and coral reefs, wetlands are and its various reverberations, pollution and remarkable in their biological productivity. -

Tamilnadu Transmission Corporation Limited (A Subsidiary of TNEB Ltd)
TamilNadu Transmission Corporation Limited (A Subsidiary of TNEB Ltd) FORMAT-STOA2 APPROVAL FOR SHORT – TERM OPEN ACCESS (Issued by SLDC) Ref : RIPL/PP/STOA/011/19-20 Nodal SLDC SLDC/STOA/TP/4372/2019-2020 Date 21/10/19 Approval No. 1 Customer Application RIPL/PP/STOA/011/19-20 Date 15/10/19 No. 2 Period of Transaction 28/10/2019 to 27/11/2019 3 Nature of customer Thirdparty User 4 Customer Name SRM Medical College Hospital Research center HTSC No. 99094110484 5 Customer EDC Chengalpattu 6 Details of Transaction Party’s to Grid Injecting Entity Drawee Entity Name of the Entity Rajkumar Impex SRM Medical College Hospital Research center Status of Entity Thirdparty Thirdparty User Utility in which it is embedded TANGEDCO TANGEDCO 7 Details of Injecting/Drawee connectivity with Intra-State System Injecting Entity Drawee Entity Name Transmission 110/33 Vagaikulam SS 110/33 Potheri SS of Sub- Distribution N/A N/A Station Voltage Transmission N/A N/A level Distribution 33 11 Name of Licensee(Owner of TANGEDCO TANGEDCO S/S) Intervening Intra-State N/A Licensee Intervening Inter-State N/A Licensee 8 Open Access Granted for: Period Requested Quantum at Injection end Approved Quantum at Injection end (MW) (MW) From To Peak Slots Non-Peak Slots Peak Slots Non-Peak Slots (18:00 to (00:00 to 18:00 & (18:00 to (00:00 to 18:00 & 22:00 22:00) hrs 22:00 to 24:00)hrs 22:00) hrs to 24:00)hrs 28/10/19 27/11/19 0.535 0.535 0.535 0.535 9 Details of Non- Refundable Application Fee made TANTRANSCO collection Instrument Details A/C Head Receipt No. -

Location of BC Gender Full Postal Address with Pincode (Bank Mitr Fixed Bank Mitr Mobile No
Location of BC Gender Full Postal Address with Pincode (Bank Mitr Fixed Bank Mitr Mobile No. ( Photo of Bank Mitr S.No Name Of Bank Name of State Name of District Name of Bank Mitr (BC) (M/F/O) location SSA) 10 Digit). (JPG/PNG format) Longitude Latitude 1 INDIAN BANK TAMILNADU THIRUVALLUR ANBALAGAN K M 9840966378 80.195135 13.069625 2 INDIAN BANK TAMILNADU THIRUVALLUR ARUNA.P F 9841935971 80.270795 13.193283 3 INDIAN BANK TAMILNADU THIRUVALLUR DEVIKALA.G F 9840895756 77.188715 32.239633 NO.378, AMBEDKAR STREET, THIRUMANAM, CHENNAI- 4 INDIAN BANK TAMILNADU THIRUVALLUR ARUNA.M F 9789698809 0.000000 0.000000 72 NO:417,KUPPADUMEDU, SORANACHERI (PO), 5 INDIAN BANK TAMILNADU THIRUVALLUR MEENAKSHI.L F 9962841921 0.000000 0.000000 PATTABIRAN, CHENNAI-600072 NO:3/37,PILLYAR KOVIL ST, METTUPALAYAM, 6 INDIAN BANK TAMILNADU THIRUVALLUR SUBHASHRI.P F 9940387984 80.093004 13.101173 KANNAPALAYAM, CHENNAI - 77 NO:167,BAJANI KOIL ST, 7 INDIAN BANK TAMILNADU THIRUVALLUR VIJAYALAKSHMI.S F VAYALANALLUR (VIL &PO), 9710426314 80.094531 13.047261 CHENNAI-600072 NO:101/1,VINAYAGAR TEMPLE ST, 8 INDIAN BANK TAMILNADU THIRUVALLUR PATCHAYAMMAL.G F PUTHAGARAM, 9380242176 80.193925 13.152552 CHENNAI-99 NO:46,RAMALINGAM NAGAR, 9 INDIAN BANK TAMILNADU THIRUVALLUR MEENAKSHI.P F PUTHAGARAM, 8124968783 80.199109 13.170984 CHENNAI-99 NO:481,GANDHI ST, 10 INDIAN BANK TAMILNADU THIRUVALLUR MAHESWARI.M F KATHIRVEDU, 9941829328 80.199924 13.152287 CHENNAI-66 NO:2/87,ARAYATHMMAN KOIL ST, AZHINJIVAKKAM, 11 INDIAN BANK TAMILNADU THIRUVALLUR SHANTHI.S F 8056098833 80.195964 13.186562 -

International Journal of Innovative Technology and Exploring Engineering
International Journal of Innovative Technology and Exploring Engineering ISSN : 2278 - 3075 Website: www.ijitee.org Volume-4 Issue-5, OCTOBER 2014 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. Ltd. loring Exp En d gin an ee r y in g g lo o n h c e T IjItEe e I n v i t t e E a r X v P N n o L IO a O n T t R A i o V n I I N O G N n IN f a o l l J a o r n u www.ijitee.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. -
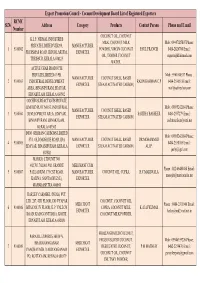
Exporters List
Export Promotion Council - Coconut Development Board List of Registered Exporters RCMC Sl.No Address Category Products Contact Person Phone and E mail Number COCONUT OIL, COCONUT K.L.F. NIRMAL INDUSTRIES MILK, COCONUT MILK Mob : 09447025807 Phone : PRIVATE LIMITED VIII/295, MANUFACTURER 1 9100002 POWDER, VIRGIN COCONUT PAUL FRANCIS 0480-2826704 Email : FR.DISMAS ROAD, IRINJALAKUDA, EXPORTER OIL, TENDER COCONUT [email protected] THRISSUR, KERALA 680125 WATER, ACTIVE CHAR PRODUCTS PRIVATE LIMITED 63/9B, Mob : 9961000337 Phone : MANUFACTURER COCONUT SHELL BASED 2 9100003 INDUSTRIAL DEVELOPMENT RAZIN RAHMAN C.P 0484-2556518 Email : EXPORTER STEAM ACTIVATED CARBON, AREA, BINANIPURAM, EDAYAR, [email protected] ERNAKULAM, KERALA 683502 COCHIN SURFACTANTS PRIVATE LIMITED PLOT NO.63, INDUSTRIAL Mob : 09895242184 Phone : MANUFACTURER COCONUT SHELL BASED 3 9100004 DEVELOPMENT AREA, EDAYAR, SAJITHA BASHEER 0484-2557279 Email : EXPORTER STEAM ACTIVATED CARBON, BINANIPURAM, ERNAKULAM, [email protected] KERALA 683502 INDO GERMAN CARBONS LIMITED Mob : 09895242184 Phone : 57/3, OLD MOSQUE ROAD, IDA MANUFACTURER COCONUT SHELL BASED DR.MOHAMMED 4 9100005 0484-2558105 Email : EDAYAR, BINANIPURAM, KERALA EXPORTER STEAM ACTIVATED CARBON, ALI.P. [email protected] 683502 MARICO LTD UNIT NO. 402,701,702,801,902, GRANDE MERCHANT CUM Phone : 022-66480480 Email : 5 9100007 PALLADIUM, 175 CST ROAD, MANUFACTURER COCONUT OIL, COPRA, H.C MARIWALA [email protected] KALINA, SANTACRUZ (E), EXPORTER MAHARASHTRA 400098 HARLEY CARMBEL (INDIA) PVT. LTD. 287, -

Kancheepuram District Map
KANCHEEPURAM DISTRICT MAP TIRUVALLUR THIRUVALLUR KONDAVAKKAM CHENNAI AYYAPANTHANGAL DISTRICT KANDAMANGALAM CHENNAI THELLIARAGARAM CHENNAI MEVALURCUPPAM MANGADU SRINIVASAPURAM MANGADU T.P KOLATHUVANJERI SENGADU MANNUR KOZHIMANIVAKKAM CHENNAI CHINNA- MOWLIVAKKAM DISTRICT SIVABURAM MALAYAMBAKKAMPANICHERI PARANIPUTHUR VALARPURAM PERIA- ORAGADAMAHADEVINANGALAM PANICHER CHEMBARAMBAKKAM TANK SIKKARAYAPURAM KOVUR GERUGAMBAKKAM KAPPANKOTTUR THANDALAM KOLACHERY KUNNATHUR bit2 KOLAPAKKAM MOONRAM- PICHIVAKKAM THANDALAM KOLAPAKKAM THIRUNAGESWARAM KATTALAI NEMEMLI THANDALAM UDUPPAIR KANDIVAKKAM ELIMIANKDTTUR R.F SIRUKALATHUR KAVANUR RENDANKATTALAI VENKATEPURAM IRUNGATTUKOTTAI THARAPPAKKAM KOTTUR MANANJERI THOLASAPURAM THARVUR KILOY AYAKOLATHUR KUNDRATHUR PURISAI EDAYARPAKKAM KATTRAMBAKKAM GUNAGARABAKKAM ETTIKUTHIMEDU NANDAMBAKKAM KUNDRATHUR PENNALUR SIRUKILOY KANAGAMBAKKAM THANDALAM AKKAMAPURAM MAHADEVIMANGALAM PUDUPPAIR PADICHERY SRIPERUMBUDUR KANNANTHANGAL POONTHANDALAM THIRUMUDIVAKKAM PULLALORE PALLAMBAKKAM SRIPERUMBUDUR AMARAMBEDU R.F ARAKONAM VALATHUR EKANAPURAM PALANTHANDALAM RANIPET NALLUR SINGLEPADI VADAMANGALAM VENGADU NALLUR PADUNALLI PONDAVAKKAM MADURAMANGALAM R.F MOOLAPATTU MADURAMANGALM IRUNBEDU DISTRICT ERUMAYUR KOTTAVAKKAM KODAMANALLUR KANDUR PILLAIPPAKKAM PUDUCHERI SOMANGALAM SOGANDI NAVALUR GOVINDAVADI MANIYATCHI IRUNGULAM KOLATHUR NADUVEERAPPATTU PARANDUR KARUNAGARACHRI PUTHERI THANDALAM MELMADURAMAGALAM MOLASUR NELVOY THIRUMANGALAM KUNDRATHUR UVERI KEERANALLUR NANDIMEDU GOVINDAVADI PARANDUR SIVANKUDAL MAMBAKKAM PONDUR MALAIPPATTU -
Sri Venkateshwara Edu.Trust 30.11.2020
ICICI Bank Limited (Registered Office: ICICI Bank Tower, Near Chakli Circle, Old Padra Road, Vadodara - 390 007, Gujarat) Regional Office: Plot No. 24, Ambattur Industrial Estate, Ambattur, Chennai - 600058. and also having its office at: 3rd Floor, No.1, Cenotaph Road, Teynampet, Chennai - 600 018. SALE NOTICE FOR SALE OF IMMOVABLE PROPERTY E-Auction Sale Notice for Sale of Immovable Assets under the Securitisation and Reconstruction of Financial Assets and Enforcement of Security Interest Act, 2002 read with proviso to Rule 8 (6) of the Security Interest (Enforcement) Rules, 2002 Notice is hereby given to the public in general and in particular to the Borrowers, Mortgagor and Guarantors that the immovable property more fully described in hereunder (“Secured Asset”) is mortgaged in pari-passu basis to ICICI Bank Ltd and UCO Bank Ltd, (“Secured Creditors”), the constructive possession of which has been taken by the Authorised Officer of ICICI Bank Limited, being one of the Secured Creditor, will be sold on “As is where is”, “As is what is”, “Whatever There Is” and “Without Any Recourse” basis on January 12, 2021 for recovery of debts due from M/s.Sri Venkteswara Educational Trust and M/s.Sree Venkateswara Technical Educational Trust(collectively referred to as “the Borrowers”). As per section 13(9) of the SARFAESI act, ICICI Bank Ltd is entitled to conduct auction of the secured asset for recovery of the outstanding dues owed by the Borrowers to the Secured Creditors. The details of the outstanding are as below: S.No Name of the Borrower Secured Creditor Amount Dues in Rs. -

The Chronographic Protocol Abs.Pdf
Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. Deepak Garg Professor, Department of Computer Science and Engineering, Thapar University, Patiala (Punjab), India, Senior Member of IEEE, Secretary of IEEE Computer Society (Delhi Section), Life Member of Computer Society of India (CSI), Indian Society of Technical Education (ISTE), Indian Science Congress Association Kolkata. Dr. Vijay Anant Athavale Director of SVS Group of Institutions, Mawana, Meerut (U.P.) India/ U.P. Technical University, India Dr. T.C. Manjunath Principal & Professor, HKBK College of Engg, Nagawara, Arabic College Road, Bengaluru-560045, Karnataka, India Dr. Kosta Yogeshwar Prasad Director, Technical Campus, Marwadi Education Foundation’s Group of Institutions, Rajkot-Morbi Highway, Gauridad, Rajkot, Gujarat, India Dr. -

International Journal of Innovative Technology and Exploring Engineering
International Journal of Innovative Technology and Exploring Engineering ISSN : 2278 - 3075 Website: www.ijitee.org Volume-6 Issue-4, SEPTEMBER 2016 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. Ltd. loring Exp En d gin an ee r y in g g lo o n h c e T IjItEe e I n v i t t e E a r X v P N n o L IO a O n T t R A i o V n I I N O G N n IN f a o l l J a o r n u www.ijitee.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. -

Kancheepuram
KANCHEEPURAM S.NO ROLL No. NAME OF ADVOCATE ADDRESS NO.46, SANNATHI STREET, UTHIRAMERUR, 1 2678/2014 AARTHI R. KANCHIPURAM DIST - 603 406 NO 21 (OLD NO 28) K.T.S. MANI STREET, 2 322/1975 ABDUL HAKIM R. MAMALLAN NAGAR, KANCHEPUAM - 631502. 35/B, JAWAHARLAL STREET, BIG 3 97/1969 ABDUL RASHID R. KANCHEEPURAM-631502. NO.72, PARUTHIKULAM VILLAGE, 4 2017/2016 ADHAVAN M. THIMMASAMUTHIRAM POST, KANCHEEPURAM DT:631502. NO:178, GANESH UDAYAM, INDIRA AVENUE 5 2006/2007 ADHIL BASHA A. ASHOK NAGAR, KANCHEEPURAM -631502 21, POSTAL COLONY, NEAR POLICE 6 2717/2006 AJITH KUMAR V. QUARTERS, KANCHEEPURAM 631501 385, BAJANAI KOIL STREET 121 KARAI 7 243/2012 ALAGARASU C. VILLAGE KANCHEEPURAM DIST NO.7, C BLOCK, POLICE LINE, PERUMAL ST. 8 3171/2013 ALBIN EDISON C.S. BIG KANCHEEPURAM NO 63, ARULPERUM SELVI STREET, BIG 9 2440/2005 ANANDAN P. KANCHEPURAM HANUMANTHADALAM VILLAGE AND POST, 10 97/1998 ANBALAGAN A. UTHIRAMERUR TALUK, KANCHEEPURAM DT. 603402 NO 22/12, SOUTH MADA ST, LITTLE 11 880/1994 ANBALAGAN R. KANCHIPURAM - 631501. S.NO ROLL No. NAME OF ADVOCATE ADDRESS NO.128, METTU STREET, VATHIYUR VILLAGE, 12 3052/2011 ANBALAGAN S. KANCHIPURAM TALUK & DISTRICT. -631502 CHINNIVAKKAM VILLAGE & POST 13 35/1987 ANBU T. VIA,THENNERI,WALAJABAD, KANCHEEPURAM TALUK-631604 104B/142, KAMATCHI AMMAN SANNATHI ST. 14 2077/2011 ANBUNIDHI K. KANCHIPURAM 631502 NO.93,AMBEDKAR STREET,PERIYAVIPPEDU 15 2422/2016 ANITHA E. VILLAGE,ORAGADAM PO,THIRUPORUR TK,KANCHIPURAM-603109 PLOT NO:35, GANDHI ST SRI MAHALAKSHMI 16 123/2015 ANTONY XAVIER J. NAGAR, KALIYANOOR MOTUR VAIYAVOOR PO KPM DI -631561. NO. -

International Journal of Emerging Science and Engineering (IJESE)
International Journal of Emerging Science and Engineering ISSN : 2319-6378 Website: www.ijese.org Volume-2 Issue-3, January 2014 Published by: Blue Eyes Intelligence Engineering and Sciences Publication Pvt. Ltd. d Enginerin an g ce n ie c S g n i g r e IJESE m E f o l a n r I n u t e o r J E n l X a a t i n o P N L O O TI RI VA NG INNO www.ijese.org Exploring Innovation Editor In Chief Dr. Shiv K Sahu Ph.D. (CSE), M.Tech. (IT, Honors), B.Tech. (IT) Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Dr. Shachi Sahu Ph.D. (Chemistry), M.Sc. (Organic Chemistry) Additional Director, Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., Bhopal(M.P.), India Vice Editor In Chief Dr. Vahid Nourani Professor, Faculty of Civil Engineering, University of Tabriz, Iran Prof.(Dr.) Anuranjan Misra Professor & Head, Computer Science & Engineering and Information Technology & Engineering, Noida International University, Noida (U.P.), India Chief Advisory Board Prof. (Dr.) Hamid Saremi Vice Chancellor of Islamic Azad University of Iran, Quchan Branch, Quchan-Iran Dr. Uma Shanker Professor & Head, Department of Mathematics, CEC, Bilaspur(C.G.), India Dr. Rama Shanker Professor & Head, Department of Statistics, Eritrea Institute of Technology, Asmara, Eritrea Dr. Vinita Kumari Blue Eyes Intelligence Engineering & Sciences Publication Pvt. Ltd., India Dr. Kapil Kumar Bansal Head (Research and Publication), SRM University, Gaziabad (U.P.), India Dr. Deepak Garg Professor, Department of Computer Science and Engineering, Thapar University, Patiala (Punjab), India, Senior Member of IEEE, Secretary of IEEE Computer Society (Delhi Section), Life Member of Computer Society of India (CSI), Indian Society of Technical Education (ISTE), Indian Science Congress Association Kolkata.