Powerbook G4 • Expo – Os
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Administrator's Guide
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release notes, and/or the latest version of the applicable documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/scanmail-for-microsoft- exchange.aspx Trend Micro, the Trend Micro t-ball logo, Apex Central, eManager, and ScanMail are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2020. Trend Micro Incorporated. All rights reserved. Document Part No.: SMEM149028/200709 Release Date: November 2020 Protected by U.S. Patent No.: 5,951,698 This documentation introduces the main features of the product and/or provides installation instructions for a production environment. Read through the documentation before installing or using the product. Detailed information about how to use specific features within the product may be available at the Trend Micro Online Help Center and/or the Trend Micro Knowledge Base. Trend Micro always seeks to improve its documentation. If you have questions, comments, or suggestions about this or any Trend Micro document, please contact us at [email protected]. Evaluate this documentation on the following site: https://www.trendmicro.com/download/documentation/rating.asp Privacy and Personal Data Collection Disclosure Certain features available in Trend Micro products collect and send feedback regarding product usage and detection information to Trend Micro. Some of this data is considered personal in certain jurisdictions and under certain regulations. -

C Powerclmlluling
C PowerClmlluling Everything you need to know about setting up and operating your PowerTower Pro™ system Ma(OS Mac and the Mac OS logo are trademal1<s of Apple Computer, Inc., used under license. Part number 72810 Rev. number 960823 erPro User' ide Part number 72810 Rev. number 960823 Power Computing Corporation © 1996 Power Computing Corporation. All rights reserved. Under copyright laws, this manual may not be copied, in whole or in part, without the written consent of Power Computing. Your rights to the software are governed by the accompanying software license agreement. Power Computing Corporation 2555 North Interstate 35 Round Rock, Texas 78664-2015 (512) 388-6868 Power Computing, the Power Computing logo, PowerTower, and PowerTower Pro are trademarks of Power Computing Corporation. Mac and the Mac as logo are trademarks of Apple Computer, Inc. All other trademarks mentioned are the property of their respective holders. Every effort has been made in this book to distinguish proprietary trademarks from descriptive terms by following the capitalization style used by the manufacturer. Every effort has been made to ensure that the information in this manual is accurate. Power Computing is not responsible for printing or clerical errors. Warranty information about your system may be found beginning on page xv. Other legal notices are found in "Regulatory Information" on page 151. PowerTower Pro User's Guide For Technical Support, Call 1-800-708-6227 Support Information For basic customer and technical support information, as well as product information and other news, visit our Web Site at: http://www.powercc.com Direct or Dealer Support? Customers who purchased systems directly from Power Computing should contact Power Computing for assistance. -

Macworld UK Jul 2001.Pdf
Macworld G4 UPGRADES TAKE YOUR OLD MAC TO 500MHZ JULY 2001 JULY IBOOK TESTED • LCD DISPLAYS • G4 UPGRADE CARDS OS DISPLAYS IBOOK TESTED • LCD • WORD TIPS • PROJECTORS X APPLICATIONS MORE NEWS, MORE REVIEWS White light Apple’s BEST portable yet? New iBook tested OS X software All new applications Flat-panel displays 26 sexy LCD screens tested ALSO INSIDE: Word tips • Flash 5 guide • Improve your info-graphics • Inside Apple’s new shops • Civilization III • FreeHand 10 • Director 8.5 • Projector roundup read me first Simon Jary Wow! Apple’s actually beaten its editor-in-chief own timetable to get Mac OS X pre-installed on all of its new Macs. About time 2.0 t Macworld, we often see amazing technologies even been seen by the secret services of the high-tech demonstrated to us by fire-eyed developers. warring factions of the planet Kabbula. They say “Wow!”; we say “Wow!”; we write Bungie was the worst offender. First there was Oni… A about it; you say “Wow!”. Not long after you’ve “Wow!”. Then there was Halo… “Double Wow!”. Several shown the article to someone else, and they’ve said years after we all first looked forward to pretending to “Wow!”, you start writing in and asking when Wow 1.0 be lithe Japanese urban-shooter girls, Oni finally will be available to buy. Then we realize that what we shipped for the Mac. It’s now at least a couple of years just saw wasn’t anywhere near ready to ship. This is the since we imagined ourselves as body-armoured Halo point at which Wow turns to Oww… space troopers, and still we wait. -

A/UX® 2.0 Release Notes
A/UX® 2.0 Release Notes 031-0117 • APPLE COMPUTER, INC. © 1990, Apple Computer, Inc. All UNIX is a registered trademark of rights reserved. AT&T Information Systems. Portions of this document have been Simultaneously published in the previously copyrighted by AT&T United States and Canada. Information Systems and the Regents of the University of California, and are reproduced with permission. Under the copyright laws, this document may not be copied, in whole or part, without the written consent of Apple. The same proprietary and copyright notices must be afftxed to any permitted copies as were afftxed to the original. Under the law, copying includes translating into another language or format. The Apple logo is a registered trademark of Apple Computer, Inc. Use of the "keyboard" Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple Computer, Inc. 20525 Mariani Ave. Cupertino, California 95014 (408) 996-1010 Apple, the Apple logo, AppleShare, AppleTalk, A/UX, ImageWriter, LaserWriter, LocalTalk, Macintosh, Multifmder, and MacTCP are registered trademarks of Apple Computer, Inc. Apple Desktop Bus, EtherTalk, Finder, and MacX are trademarks of Apple Computer, Inc. Motorola is a registered trademark of Motorola, Inc. POSTSCRIPT is a registered trademark of Adobe Systems, Inc. 031-0117 UMITED WARRANTY ON MEDIA Even though Apple has reviewed this AND REPLACEMENT manual, APPLE MAKES NO WARRANTY OR REPRESENTATION, If you discover physical defects in the EITHER EXPRESS OR IMPLIED, manual or in the media on which a WITH RESPECI' TO THIS MANUAL, software product is distributed, Apple ITS QUAll1Y, ACCURACY, will replace the media or manual at MERCHANTABILITY, OR FITNESS no charge to you provided you return FOR A PARTICULAR PURPOSE. -

Windows X32 Cross Compile Guide
Guide for cross compiling Trezarcoin for windows. By Iwens Fortis Tested on Ubuntu 16.04.2 LTS. • Start on ubuntu your terminal (search for terminal with ubuntu dash top icon left, or press windows key to open dash). • First we need to install the dependencies, for this execute the following cmd’s stated below in the terminal window. The commands to execute are in the grey textboxes. The commands will ask for a password which and u have to confirm some commands with y from yes. Tip transfer the pdf to ubuntu for easy copy and paste. • First update the apt library. sudo apt-get update • Install needed dependencies to install mxe to cross compile Trezarcoin. sudo apt-get install p7zip-full autoconf automake autopoint bash bison bzip2 cmake flex gettext git g++ gperf intltool \ libffi-dev libtool libltdl-dev libssl-dev libxml-parser-perl make openssl patch perl pkg-config python ruby scons sed unzip \ wget xz-utils libtool-bin libgdk-pixbuf2.0-dev g++-multilib libc6-dev-i386 upx -y • We need to get latest mxe from github and compile libraries needed. git clone https://github.com/mxe/mxe.git cd mxe make MXE_TARGETS="i686-w64-mingw32.static" boost make MXE_TARGETS="i686-w64-mingw32.static" qttools make MXE_TARGETS="i686-w64-mingw32.static" miniupnpc • Next we need to compile the recommended Berkeley DB our self cd ~ wget 'http://download.oracle.com/berkeley-db/db-4.8.30.NC.tar.gz' tar zxvf db-4.8.30.NC.tar.gz cd db-4.8.30.NC • Now we will create a bash script for this execute the following commands to create the bash script. -

Infovox Ivox & Visiovoice
Cover by Michele Patterson Masthead Publisher Robert L. Pritchett from MPN, LLC Editor-in-Chief Robert L. Pritchett Editor Mike Hubbartt Assistant Editor Harry (doc) Babad Consultant Ted Bade Advertising and Marketing Director Wayne Lefevre Web Master James Meister Public Relations and Merchandizing Mark Howson Contacts Webmaster at macCompanion dot com Feedback at macCompanion dot com Correspondence 1952 Thayer, Drive, Richland, WA 99352 USA 1-509-210-0217 1-888-684-2161 rpritchett at macCompanion dot com The Macintosh Professional Network Team Harry {doc} Babad Ted Bade Matt Brewer (MacFanatic) Jack Campbell (Guest Author) Ken Crockett (Apple News Now) Kale Feelhaver (AppleMacPunk) Dr. Eric Flescher Eddie Hargreaves Jonathan Hoyle III Mark Howson (The Mac Nurse) Mike Hubbartt Daphne Kalfon (I Love My Mac) Wayne Lefevre Daniel MacKenzie Chris Marshall (My Apple Stuff) Dom McAllister Derek Meier James Meister Michele Patterson David Phillips (Guest Author) Robert Pritchett Leland Scott Dennis Sellers (Macsimum News) Gene Steinberg (The Tech Night Owl) Rick Sutcliffe (The Northern Spy) Tim Verpoorten (Surfbits) Julie M. Willingham Application Service Provider for the macCompanion website: http://www.stephousehosting.com Thanks to Daniel Counsell of Realmac Software Development (http://www.realmacsoftware.com), who graced these pages and our website with newer rating stars. Our special thanks to all those who have allowed us to review their products! In addition, thanks to you, our readers, who make this effort possible. Please support -

Command-Line Guide for Linux, Mac & Windows
Command-line Guide for Linux, Mac & Windows info.nrao.edu /computing/guide/file-access-and-archiving/7zip/7z-7za-command-line-guide See also: File Archiving and Compression, Accessing and Sharing Files, Network Access, Windows Terminal Servers 7-Zip Versions 7-Zip is an Archive and File Management utility available in command-line versions for Linux/Mac, "P7Zip" (7z.exe), as well as for Windows, "7za" (7za.exe). Although its interface is deceptively simple, the command-line versions of 7ZIP are highly customizable archiving programs when used with the command parameters and switchesdescribed below. Windows users who want to use the command-line version should generate a Help Desk ticket to install the standalone 7za.exe version. To begin a session, open a terminal window. Invoke the version of 7Zip you are using by entering " 7z" for P7Zip (7z.exe), or "7za" for 7Zip for Windows (7za.exe) to start either the P7-Zip or 7za application prior to entering commands. Other than this program invocation command, all commands, parameters and switches are identical for all command-line versions. NOTE TO WINDOWS USERS: the following syntax examples begin by invoking the Linux command-line version, "7z". Please change the invocation to "7za" when applying these examples for use in 7-Zip for Windows. Command Line Syntax The general command line syntax begins by invoking the version of 7Zip you are using: "7z" for P7Zip (7z.exe) users or "7za" for 7Zip for Windows (7za.exe) users followed by the command and parameters: "command" "switches" "full_path_archive_name" "full_path_file_name" Eg; 7z a -p 7Zip_Archive Test_file.txt creates a 7z formatted archive named 7Zip_Archive that is protected with a password , then adds a file named test_file.txt to the archive. -
3. PE Portable Executable: a Look
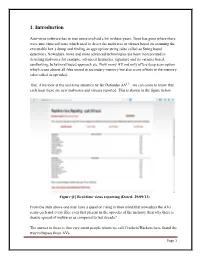
1. Introduction Anti-virus software has in true sense evolved a lot in these years. Time has gone where there were anti-virus software which used to detect the malwares or viruses based on scanning the executable hex`s dump and finding an appropriate string (also called as String based detection). Nowadays, more and more advanced technologies are been incorporated in detecting malwares for example, advanced heuristics, signature and its variants based, sandboxing, behavioral based approach etc. Now many AV not only offers deep scan option which scans almost all files stored in secondary memory but also scans offsets in the memory (also called as opcodes). But, if we look at the real-time statistics by Bit Defender AV[1] , we can come to know that each hour there are new malwares and viruses reported. This is shown in the figure below. Figure [1] Real-time virus reporting (Dated: 29/09/13) From the stats above one may have a question rising in their mind that nowadays the AVs scans each and every files even that present in the opcodes of the memory then why there is drastic spread of malwares as compared to last decade? The answer to these is that very smart people whom we call Crackers/Hackers have found the way to bypass these AVs. Page 1 They know the very detail about how the AV works and which AV have which type of detection capabilities for example if it scans based on string detection or if it scans based on sandboxing approach. We sometimes fail to remember that they (Crackers and Hackers) too have AV scanners from which they may scan their newly developed malware and viruses and can easily spread via plethora of medium, mostly the Internet. -

Introduction to MLAB the Royal Road to Dynamical Simulations
Introduction to MLAB The Royal Road to Dynamical Simulations Revision Date: September 24, 2015 Foster Morrison, author Turtle Hollow Associates, Inc. P.O. Box 3639 Gaithersburg, MD 20885 USA Daniel Kerner, editor Civilized Software, Inc. 12109 Heritage Park Circle Silver Spring, MD 20906 USA Email: [email protected] Web-site: http://www.civilized.com (301) 962-3711 c 1992-2014 Turtle Hollow Associates, Inc. Contents Preface ii 1 BASIC MATHEMATICS AND ITS IMPLEMENTATION IN MLAB 1 1.1 What You Need to Know ................................ 1 1.2 Getting Started with MLAB ............................... 2 1.3 Foundations of Mathematics ............................... 2 1.4 Sets ............................................ 3 1.5 Numbers, Prime, Rational, and Real .......................... 4 1.6 Try Out MLAB ...................................... 6 2 PROGRAMMING IN MLAB 10 2.1 More Numerical Analysis vs. Analysis ......................... 10 2.2 Legendre Polynomials .................................. 11 3 VECTORS AND MATRICES 13 3.1 Vectors .......................................... 13 3.2 Matrices, Linear Algebra, and Modern Algebra .................... 14 3.3 Arrays ........................................... 16 3.4 Functional Analysis .................................... 16 i 4 LINEAR DYNAMIC SYSTEMS AND MODELS 19 4.1 Difference Equations ................................... 19 4.2 Differential Equations .................................. 21 4.3 Generalizations ...................................... 23 5 LINEAR DYNAMIC SYSTEMS WITH INPUTS -

Qualitative and Quantitative Evaluation of Software Packers
Qualitative and Quantitative Evaluation of Software Packers Mar´ıa Bazus,´ Ricardo J. Rodr´ıguez, Jose´ Merseguer « All wrongs reversed [email protected] ¸ @RicardoJRdez ¸ www.ricardojrodriguez.es Department of Computer Science and Systems Engineering University of Zaragoza, Spain December 12, 2015 NoConName 2015 Barcelona (Spain) $whoami Ph.D. on Comp. Sci. (Univ. of Zaragoza, Spain) (2013) Assistant Professor at University of Zaragoza Performance analysis on critical, complex systems Secure Software Engineering Advance malware analysis RFID/NFC Security Not prosecuted ^¨ Speaker at NcN, HackLU, RootedCON, STIC CCN-CERT, HIP, MalCON, HITB. M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 2 / 39 Agenda 1 Introduction 2 Contributions and Related Work 3 Previous Concepts 4 Software Protection Taxonomy 5 Software Packers Under Study 6 Qualitative and Quantitative Evaluation Qualitative Evaluation Quantitative Evaluation 7 Conclusions and Future Work M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 3 / 39 Agenda 1 Introduction 2 Contributions and Related Work 3 Previous Concepts 4 Software Protection Taxonomy 5 Software Packers Under Study 6 Qualitative and Quantitative Evaluation Qualitative Evaluation Quantitative Evaluation 7 Conclusions and Future Work M. Bazus,´ R.J. Rodr´ıguez, J. Merseguer Qualitative and Quantitative Evaluation of Software Packers NcN 2015 4 / 39 RE uses: legitimate and illegitimate X Find software bugs X Get interoperability with legacy systems X Detect malicious software X Detect vulnerabilities to create/spread malware X Obtain (or avoid) software license duplication Introduction (I): Reverse Engineering WTF? To analyse a binary program with machine-code vision Types of analysis: Static analysis( + not executed, * all paths explored) Dynamic analysis( * truly executed, + but just one path explored!) M. -

Chapter 3: System Software
75 System 3 Software When you first buy a computer, it’s the hardware that gets all the attention. But what really makes the Mac what it is—an easy-to-use and highly customizable personal computer—is the system software. The system software creates the desktop, lets you organize your files in folders, and gives you capabilities—such as cutting and pasting text and graphics—that work in virtually any Mac program. In this chapter, we describe the basic components of the Mac system soft- ware. You’ll also find advice on system software installation and modification. 76 Chapter 3: System Software Contributors Contents Sharon Zardetto The Operating System.....................................................77 Aker (SZA) is the chapter editor. System Software ........................................................................77 Updates, Tune-Ups, and Enablers...............................................79 John Kadyk (JK) has been involved with System Installation .....................................................................83 all six editions of this The Installer ...............................................................................85 book. When he’s not working with the Mac, he likes playing music The System Folder ...........................................................88 and biking. The System and Finder Files.......................................................88 Charles Rubin (CR) The Inner Folders .......................................................................90 is a Mac writer who has Extensions..................................................................................92 -

Mac Essentials Organizing SAS Software
Host Systems Getting Organized in Mac OS Rick Asler If you work on just one simple project with SAS MAE is emulation software to run Mac on some software, it may not matter very much how you UNIX systems. It is not the best way to run SAS organize your files. But if you work on a complex software. project or on several projects, your productivity and SAS software requires at least version 7.5 of peace of mind depend on organizing your projects Mac OS. System 7.5 shipped on new computers in effectively. 1994-1995 and can be purchased separately for This paper presents a system for organizing the older computers. A new system version is due in files of SAS projects, taking advantage of the 1996. special features of Mac OS. Then it demonstrates A computer system for running SAS software techniques for automating SAS projects. should also have at least an average-size hard disk and at least 16 megabytes of physical RAM. The Finder is the main application that is always Mac essentials running in Mac OS. It displays disks and files as icons and subdirectories as folders. First, these are some Mac terms and features The system folder is the folder containing the you may need to be aware of to operate SAS System file, Finder, and other Mac OS files. software under Mac OS. The Trash Is a Finder container where deleted Mac, Mac OS, Mac operating system, or Macin files go. You can retrieve them Hyou don't wait too tosh operating system is the distinctive graphical long.