End-To-End Detection of Caller ID Spoofing Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Data Communications Glossary of Terms
DOCUMENT RESUME ED 108 612 IR 002 1 -27 AUTHOR Teplitzky, Frank TITLE A'Data Communications Glossary of Terms. INSTITUTION Southwest Regional Laboratory for Educational Research, and Development, Los Alamitos, Calif. REPORT NO SWRL-TN-5-72-09 PUB DATE' 28 Feb 72 NOTE 18p. -EDRS TRICE MF-$0.76 HC-$1.5e PLUS ,POSTAGE DESCRIPTORS Computer Science; Data Processing; *Glossaries; *Media Technology; Programing Languages; *Reference Materials; Research Tools; *Telecommunication ' ABSTRACT General and specialized terms developed in data communications in recent years are listed al abetically and defined. The list is said to be more representative thaexhaustive and is ' intended for use as a reference source. Approximately 140 terms are included. (Author/SK) Gjr ,r ************************************************************A******** Doduments acquired byERIC inclUde =many informal unpublis4e& * * materials not available from other sources. ERIC makes every effort * *.to obtain the best copy c.vpilable. nevertheless, items of marginal * * reproducibility are often enCountered and this,affects the quality * * of the microfiche =and hardcopy reproductionsERIC makes available 4` * =via= the, ERIC Document Re -prod_ uc =tion= Service,(EDRS). EDRS= is not * responsible for the quality of the original document. Reproductions * * supplied =by EDRS are the best that can be made -from= =the original. * ********************************************************************** C I. SOUTHWEST REGIONAL LABORATORY TECHNICAL NOTE DATE: Febr-uary 28, 1972 NO: TN -

Federal Register/Vol. 85, No. 77/Tuesday, April 21, 2020/Rules
Federal Register / Vol. 85, No. 77 / Tuesday, April 21, 2020 / Rules and Regulations 22029 and-comment requirements of the FEDERAL COMMUNICATIONS Synopsis Administrative Procedure Act, see 5 COMMISSION I. Introduction U.S.C. 553(b)(A). 7. Implementation. As a temporary 47 CFR Part 64 1. Each day, Americans receive transition measure, for 90 days after millions of unwanted phone calls. One source indicates that Americans publication of this document in the [WC Docket Nos. 17–97, 20–67; FCC 20– received over 58 billion such calls in Federal Register, U.S. Bank will 42; FRS 16631] continue to process payments to P.O. 2019 alone. These include ‘‘spoofed’’ Box 979088. After that date, forfeiture Call Authentication Trust Anchor; calls whereby the caller falsifies caller payments must be made in accordance Implementation of TRACED Act— ID information that appears on a with the procedures set forth in each Knowledge of Customers by Entities recipient’s phone to deceive them into forfeiture order and on the With Access to Numbering Resources thinking the call is from someone they Commission’s website, www.fcc.gov/ know or can trust. Spoofing has legal licensing-databases/fees. For now, such AGENCY: Federal Communications and illegal uses. For example, medical payments will be made through the Fee Commission. professionals calling patients from their Filer Online System (Fee Filer), mobile phones often legally spoof the accessible at https://www.fcc.gov/ ACTION: Final rule. outgoing phone number to be the office licensing-databases/fees/fee-filer. As we phone number for privacy reasons, and assess and implement U.S. -

The Information Act the Numbering Crisis in World Zone 1
The Information Act Brian Hayes Annan, Octopus, 1990 The Numbering Crisis in World Zone 1 i carcity is no stranger in this land of I ten-digit numbers are possible telephone or a ladder without rungs—I couldn't .plenty. From time to time it seems I numbers. Indeed, more than 90 percent fathom the use of it. Then my grand • we are running out of fuel, out of wa of them are unacceptable for one reason mother demonstrated. She picked up the ter, out of housing, out of wilderness, out or another. A telephone number is not receiver and said, "Jenny, get me Mrs. of ozone, out of places to put the rubbish, just an arbitrary sequence of digits, like Wilson, please. Thank you, dear." out of all the stuff we need to make more the serial number on a ticket stub; it has My grandmother's telephone was al rubbish. But who could have guessed, as a surprising amount of structure in it. As a ready quite an anachronism when I first the millennium trundles on to its close, matter of fact, the set of all valid North saw it in the 1950s. Automatic switching that we would be running out of num American telephone numbers constitutes gear—allowing the customer to make a bers? That was one resource everyone a formal language, analogous to a com connection without the help of an opera thought was infinite. puter programming language. When you tor—had been placed in service as early as The numbers in short supply are tele dial a telephone, you are programming 1892. -

Direct Distance Dialing
Chapter 8 Direct Distance Dialing Direct distance dialing of calls nationwide by customers required a major investment in development by the Bell System. Automatic alternate rout ing was incorporated into a multilevel hierarchy of switching centers, and a routing plan was developed to allow efficient choice of routes to a toll office in the region of the called telephone. No. 4 crossbar was adapted in several versions to take on the added functions of accepting more dialed digits from customers and of performing more code conversions or translations. The card translator solved the problem of handling the large amounts of infor mation required to service calls nationwide, and the crossbar tandem sys tem, despite its 2-wire design, was modified extensively for toll service and gave a good account of itself, with 213 toll systems in place by 1968. Crossbar tandem was, in addition, the first host system for centralized automatic message accounting, another important ingredient in making DDD available to all customers, regardless of the type of local office serving them. Selected No. 5 crossbar systems were modified, beginning in 1967, to inaugurate customer-dialing of calls overseas. I. NATIONWIDE PLANNING Initially, much of the equipment used by operators to complete toll calls was of the step-by-step variety, since this system was most suitable for the smaller-size trunk groups and was available, having been developed before World War II (see Chapter 3, section VI). Later, when there was a greater concentration of toll facilities, the No. 4 crossbar was available and was indeed adapted for the larger cities with five post-war installations in New York, Chicago, Boston, Cleveland, and Oakland (see Chapter 4, section III and Chapter 6, section 3.1). -
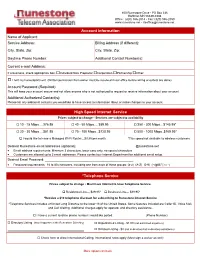
Account Information High Speed Internet Service *Telephone
100 Runestone Drive • PO Box 336 Hoffman MN 56339-0336 Office: (320) 986-2013 • Fax: (320) 986-2050 www.runestone.net • [email protected] Account Information Name of Applicant: Service Address: Billing Address (if different): City, State, Zip: City, State, Zip: Daytime Phone Number: Additional Contact Number(s): Current e-mail Address: If a business, check appropriate box: Individual/Sole Proprietor Corporation Partnership Other:_________________ I rent my home/apartment (Written permission from owner must be received in our office before wiring or outlets are done) Account Password (Required): This will keep your account secure and not allow anyone who is not authorized to request or receive information about your account Additional Authorized Contact(s): Please list any additional contacts you would like to have access to information about or make changes to your account High Speed Internet Service Prices subject to change • Services are subject to availability 10 - 15 Mbps….$76.95 40 - 50 Mbps.... $89.95 250 - 300 Mbps…$145.95* 20 - 30 Mbps….$81.95 75 - 100 Mbps...$120.95 500 - 1000 Mbps..$169.95* I would like to lease a Managed Wi-Fi Router…$3.95 per month *This speed not available to wireless customers Desired Runestone email addresses (optional): _______________________________ @runestone.net Email address requirements: Minimum 3 characters, lower case only, no special characters Customers are allowed up to 5 email addresses. Please contact our Internet Department for additional email setup. Desired Email Password: ______________________________________________________ Password requirements: 16 to 80 characters, including one from each of these groups: (a-z) (A-Z) (0-9) (~@#$*( ) = -) *Telephone Service Prices subject to change • Must have Internet to have Telephone Service. -

Managing Unsolicited Communication Leveraging STIR/SHAKEN and Blockchain
Managing Unsolicited Communication Leveraging STIR/SHAKEN and Blockchain Tech Mahindra and IBM POV STIR/SHAKEN BLOCKCHAIN POV 1 Table of Contents Introduction 3 STIR/SHAKEN Framework 3 Secured Telephony Identity Revisited (STIR) 3 Signature-based Handling of Asserted information using toKENs (SHAKEN) 4 How do STIR/SHAKEN work in a telecom network? 4 Limitations of STIR/SHAKEN Framework 5 How is India resolving the Great '1 Bn Subscriber Problem" by adopting Blockchain? 5 Benefits of DLT UCC Solution 6 Architecture for implementation of UCC ecosystem based on DLT 6 Ledgers for DLT UCC Solution 7 Performance of the DLT UCC Solution 8 Platform To Curb RoboCalls and Caller ID Spoofing for US Operators: 8 A Use Case for Integration of DLT UCC Solution with the STIR/SHAKEN framework 8 Call flow with integrated STIR/SHAKEN and DLT UCC Solution 9 Why the IBM Blockchain Platform for the DLT? 10 Conclusion 10 STIR/SHAKEN BLOCKCHAIN POV 2 Introduction The Federal Trade Commission (FTC) is a bipartisan federal agency with a dual mission to protect consumers and promote competition. Federal Communications Commission (FCC) regulates interstate and international communications by radio, television, wire, satellite, and cable in all 50 states. The District of Columbia and US territories regularly cite “unwanted and illegal robocalls" as their top complaint category. The FTC got more than 1.9 million complaints filed in the first five months of 2017 and around 5.3 million in 2016. The FCC has stated that it gets more than 200,000 complaints about unwanted telemarketing calls each year. The consumers are increasingly the targets of unsolicited and often fraudulent robocalls, which are enabled by caller ID spoofing. -

Henning Schulzrinne FCC 7/16/14 ITIF 2
7/16/14 ITIF 1 TECHNOLOGY TRANSITION: NUMBERING Henning Schulzrinne FCC 7/16/14 ITIF 2 Overview • Technology transition overview • The role of telephone numbers • The future of telephone numbers 7/16/14 ITIF 3 Technology Transitions application TDM voice VoIP (incl. VoLTE) transport network TDM circuits & IP packets analog fiber physical coax copper twisted-pair layer wireless copper twisted-pair (and combinations) 7/16/14 ITIF 4 The universe of IP transitions cable video PSTN satellite video numbers 911 7/16/14 ITIF 5 The three transitions From to motivation issues Copper fiber capacity competition maintenance cost (“unbundled network elements”) Wired wireless mobility capacity cost in rural areas quality Circuits packets flexibility line power (IP) cost per bit VoIP, VoLTE 7/16/14 ITIF 6 Dividing the problem space universal reach power intra network reliability consumer protection Tech transition interconnection inter network 911 numbering 7/16/14 ITIF 7 Interstate switched access minutes 7/16/14 ITIF 8 Lines are disappearing, but maintenance costs are constant 100 JSI Capital Advisors projection 80 voice only (DSL: 20 M) 60 40 20 Residential 0 Business per-line monthly maintenance $2.72 $17.57 cost voice revenue/line: dis $50 7/16/14 ITIF 9 Switches are ageing 1979 Nortel DMS-100 http://www.phworld.org/switch/ntess.htm 7/16/14 ITIF 10 Engines for tech transition • Consumer-induced • Landline cellular • uneven by geography, income, ethnicity • but decreasing rate • why do household keep or abandon landlines? • ILEC DSL cable company -

GAO-20-153, Fake Caller ID Schemes
United States Government Accountability Office Report to Congressional Committees December 2019 FAKE CALLER ID SCHEMES Information on Federal Agencies’ Efforts to Enforce Laws, Educate the Public, and Support Technical Initiatives GAO-20-153 December 2019 FAKE CALLER ID SCHEMES Information on Federal Agencies’ Efforts to Enforce Laws, Educate the Public, and Support Technical Initiatives Highlights of GAO-20-153, a report to congressional committees Why GAO Did This Study What GAO Found Unwanted phone calls, which may also Transmitting fake caller ID information with a phone call, also referred to as involve spoofing, consistently rank “spoofing,” is in many cases illegal—and is used in schemes to obtain money among the top consumer complaints to and personal information or generate telemarketing leads. Complaints submitted FCC and FTC. In recent years, to the Federal Communications Commission (FCC) and the Federal Trade consumers have lost millions of Commission (FTC), both of which work to protect consumers from spoofing, dollars—and been deceived into suggest that spoofing is a growing issue. providing financial or other sensitive information or purchasing falsely FCC, FTC, and the Department of Justice (DOJ) identified 62 enforcement cases advertised products—due to schemes they have brought since 2006 involving spoofing. Enforcement can be using these calls. FCC, FTC, and DOJ challenging, as it can be difficult to identify the source of spoofed calls, and have efforts aimed at combatting the scammers may be based overseas. Nevertheless, GAO found that the agencies fraudulent use of caller ID spoofing. prioritize their spoofing-related enforcement actions based in part on the level of harm perpetrated against the public and generally follow key practices identified Recently enacted federal legislation included a statutory provision for GAO by GAO for effective collaboration. -

Feature Document International Direct Distance Dialing (Iddd) No. 3 Electronic Switching System
BELL SYSTEM PRACTICES SECTION 233-190-503 AT&TCo SPCS Issue 1, March 1980 FEATURE DOCUMENT INTERNATIONAL DIRECT DISTANCE DIALING (IDDD) NO. 3 ELECTRONIC SWITCHING SYSTEM CONTENTS PAGE CONTENTS PAGE 9. INSTALLATION/ADDITION/DELETION .. dd INTRODUCTION ........ 3 10. HARDWARE REQUIREMENTS 2. oe we) (6d 1. GENERAL INFORMATION ..... 3 11. SOFTWARE REQUIREMENTS woe ew we UT 2. DEFINITION eee ee ee 3 12. DATA ASSIGNMENTS AND RECORDS . DESCRIPTION ........ 3 13. TESTING woe ee we ee wwe Cd 3. USER OPERATION woe ee ee 3 14. OTHER PLANNING TOPICS re 4. SYSTEM OPERATION , oe ee ee 4 ADMINISTRATION ...... 12 CHARACTERISTICS - ee ee 15. MEASUREMENTS se ew we ew wee) CT 5. FEATURE ASSIGNMENT woe ee 9 16. CHARGING woe ee ew ww ew OT 6. LIMITATIONS woe ee ee ww we) (10 7. INTERACTIONS woe oe ee ew ee 0 SUPPLEMENTARY INFORMATION 12 8. RESTRICTION CAPABILITY ~ ee ew. 7 17. GLOSSARY woe ew we ww we) Od INCORPORATION INTO SYSTEM 11 18. REFERENCES woe ee we we ww NOTICE Not for use or disclosure outside the Bell System except under written agreement Printed in U.S.A. Page 1 SECTION 233-190-503 Figures Tables CONTENTS PAGE CONTENTS PAGE 1. IDDD Flowchart 5 A. Country Codes and National Numbers 4 2. IDDD Translator 7 B. Summary of Outpulsing to TSPS . 10 C. Frequencies for MF Pulsing (in Hertz) 10 Page 2 ISS 1, SECTION 233-190-503 INTRODUCTION When 01 is followed by a “0” (representing an international 0- call), the call is intended for the 1. GENERAL INFORMATION overseas operator. A_ station-to-station call is identified by the prefix “011.” When the prefix 1.01 This document describes the International “01” is followed by the first digit of the country Direct Distance Dialing (IDDD) feature for code (representing an international 0+ call), the the No. -

April 13, 2021 TLP: WHITE Report: 2021041313000
Health Sector Cybersecurity Coordination Center (HC3) Analyst Note April 13, 2021 TLP: WHITE Report: 2021041313000 Vishing and Phishing Campaigns Targeting the HPH Sector Executive Summary In late March 2021, security researchers revealed details of a malicious campaign targeting the healthcare and public health (HPH) sector by leveraging call centers to distribute malware to its targets. Numerous campaigns in the past year have successfully leveraged voice-changing software, Voice over IP (VoIP) software, caller ID spoofing, and social engineering techniques to obtain sensitive information or install malware on targeted systems. HC3 assesses that these trends will continue due to previous successful exploitation. Report HC3 has observed numerous phishing and vishing campaigns in the last year, with an uptick of recent activity targeting the HPH sector. Voice phishing, also known as vishing, is the practice of eliciting information or attempting to influence action via the telephone. Threat actors often leverage VoIP services to conduct social engineering attacks. These attacks enable hackers to appear to be originating from a trusted telephone number by spoofing the caller ID. Attackers may even leverage voice-changing software to further convince victims and obscure their identity. The objectives of these attacks are to obtain sensitive information or distribute malware. Some relevant threat activity observed by the HC3 over the past year includes the following: • In April 2021, the Molerats cyberespionage group was discovered using voice-changing software to pose as women when social engineering its targets to install malware. This group is also believed to hack VoIP systems which could allow them to appear to be coming from a trusted phone number. -

March 10, 2020 FACT SHEET* Mandating STIR/SHAKEN And
March 10, 2020 FACT SHEET* Mandating STIR/SHAKEN and Proposing Additional Measures to Combat Illegal Spoofing Report and Order and Further Notice of Proposed Rulemaking – WC Docket Nos. 17-97, 20-67 Background: Each day, Americans receive millions of unwanted phone calls, including calls that “spoof” or falsify caller ID information with a malicious intent. These spoofed calls are not simply an annoyance—they result in billions of dollars lost to fraud, degrade consumer confidence in the voice network, and harm public safety. This Report and Order and Further Notice of Proposed Rulemaking would take a critical step in the Commission’s multi-pronged approach to ending illegal caller ID spoofing by requiring voice service providers to implement caller ID authentication technology. Known as STIR/SHAKEN, this technology enables voice service providers to verify that the caller ID information transmitted with a particular call matches the caller’s number—and provides valuable information to detect illegally spoofed calls. Widespread implementation of STIR/SHAKEN will reduce the effectiveness of illegal spoofing, allow law enforcement to identify bad actors more easily, and help voice service providers identify calls with illegally spoofed caller ID information before those calls reach their subscribers. Most importantly, it will help restore Americans’ trust in the voice network, which has been eroded by the prevalence of illegal caller ID spoofing. What the Order Would Do: • Require originating and terminating voice service providers to implement the STIR/SHAKEN caller ID authentication framework in the Internet Protocol (IP) portions of their networks by June 30, 2021, a deadline that is consistent with the TRACED Act, which was recently passed by Congress. -

September 9, 2020 FACT SHEET* Promoting Caller ID Authentication
September 9, 2020 FACT SHEET* Promoting Caller ID Authentication to Combat Illegal Robocalls: Further Implementation of the TRACED Act Second Report and Order – WC Docket No. 17-97 Background: Each day, Americans receive millions of unwanted phone calls, including calls that falsify caller ID information with malicious intent, resulting in billions of dollars lost to fraud, the degradation of consumer confidence in the voice network, and harm to public safety. Caller ID authentication technology enables voice service providers to verify that the caller ID information transmitted with a particular call matches the caller’s number—and provides valuable information to detect illegally spoofed calls. The STIR/SHAKEN framework is an industry-standard caller ID authentication solution that operates solely on Internet Protocol (IP) networks. The Commission’s March Report and Order and Further Notice of Proposed Rulemaking in this proceeding required all voice service providers to implement STIR/SHAKEN in the IP portions of their networks by June 30, 2021, consistent with the recently-enacted TRACED Act. This Second Report and Order would continue the FCC’s work to implement the TRACED Act and promote the deployment of caller ID authentication technology. What the Second Report and Order Would Do: • Require voice service providers to either upgrade their non-IP networks to IP and implement STIR/SHAKEN, or work to develop a non-IP caller ID authentication solution. • Establish extensions of the June 30, 2021 caller ID authentication implementation deadline for small voice service providers, voice service providers that are currently incapable of obtaining a “certificate” necessary to implement STIR/SHAKEN, services scheduled for discontinuance, and non-IP networks.